Develop a Project Plan
Project planning overview
identifies the works must be done.
break the work down to make it easy to manage.
once have tasks list, then decide:
- Who?
- Estimated time?
- Estimated cost?
Project Plan
- Used over the course of the project
- Directs people's tasks
- Tracks project's progression
- Aids in course corrections
- Communicates progress with stakeholders
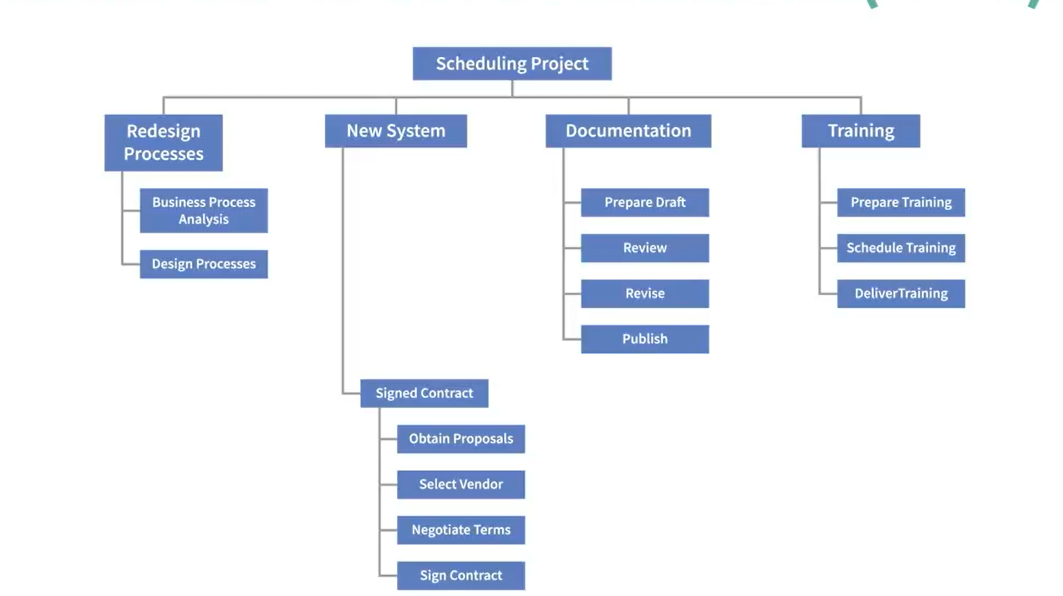
Work Breakdown Structure(WBS)
- Easier to estimate time and cost.
- Easier to assign work.
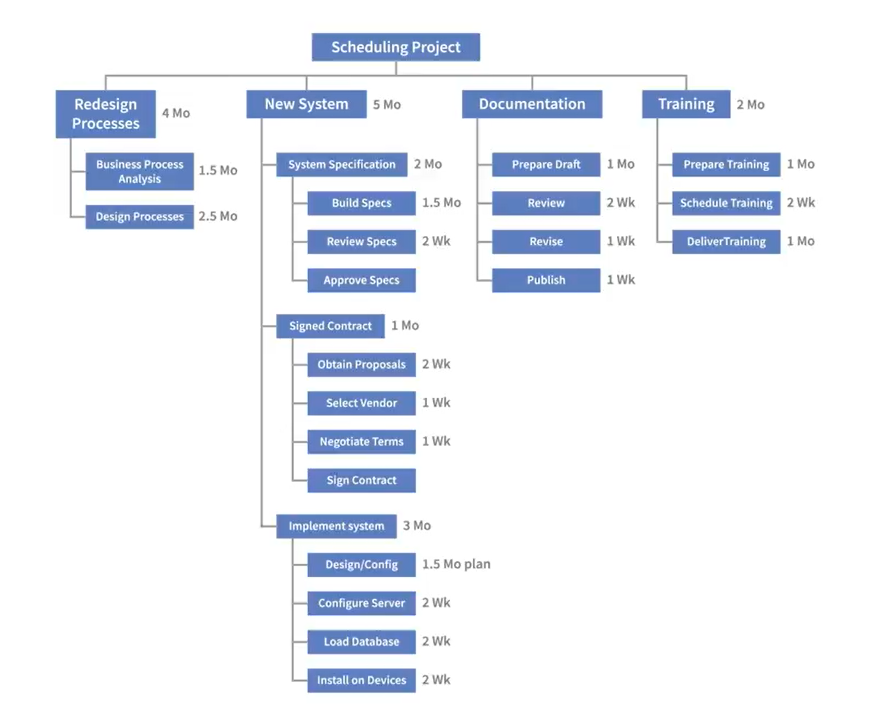
- WBS(two type of tasks)
- Summary tasks
- Higher-level tasks in WBS
- The quantity of levels depends on project complexity
- Work packages
- Lowest level in WBS
- Summary tasks
Build a work Breakdown structure
Work Packages
- Break down in eight-to-eighty-hour tasks
- Match to frequency of status reports
Determining Breakdowns
- Time and cost are easy to estimate
- Status is easy to measure
- Task durations are shorter than reporting periods
- Details are manageable
How to create work packages
- Defining work packages
- Create work package documents
Level of Detail
- Familiarity of work
- Experience of the team member
Cho3-work package solution.pdf
Estimate time and cost
- Core planning team
- Team members
Time Estimates
Parametric Model
Calculate work and cost based on a measured unit.
Delphi Technique
For large project, Top-Down estimate works well.
How to choose the best estimate
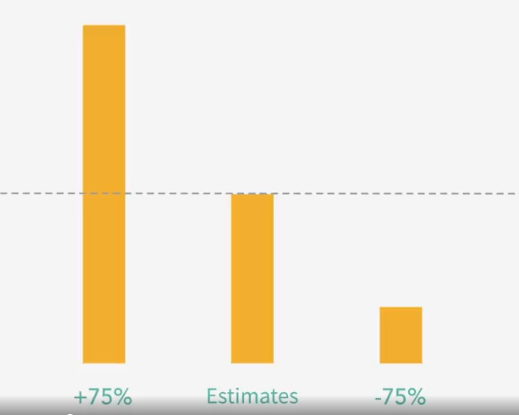
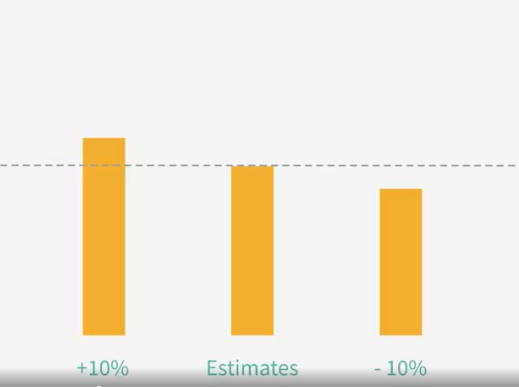
Choosing Estimate Values
Adjust your Estimate
- A highter value increases the chance of success
- A lower value decreases the chance of success
Choose the estimate with an acceptable probability of success
Ch03 -Best Estimate.pdf
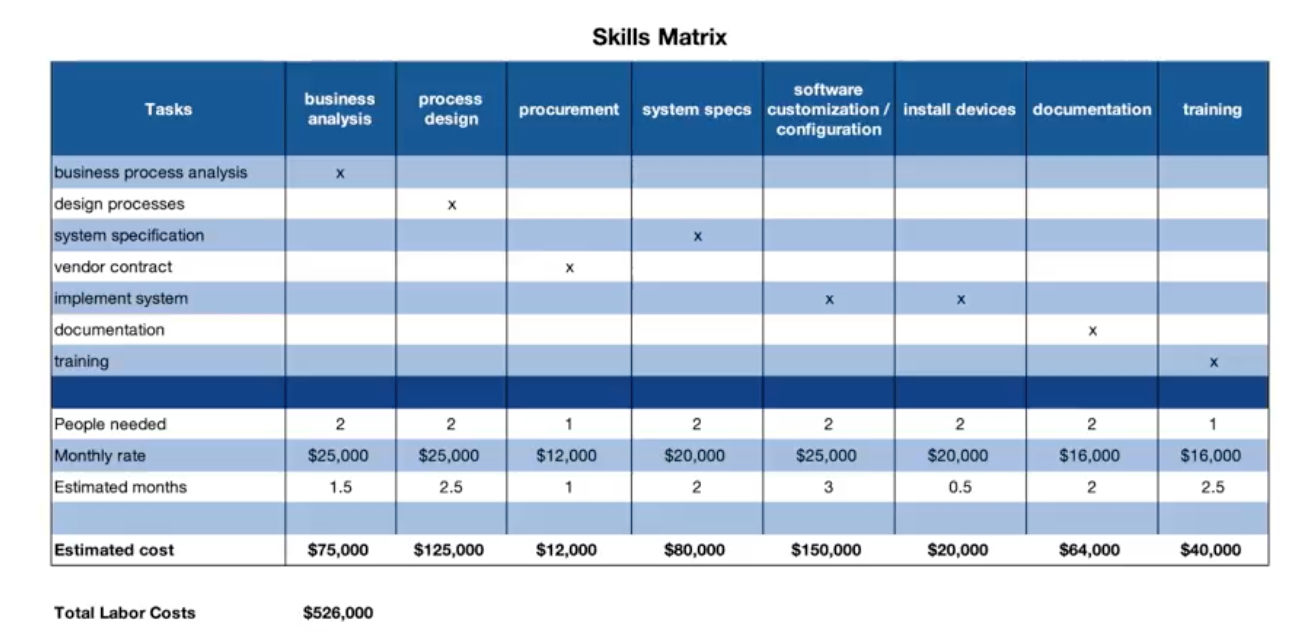
Create a resource management plan
- Roles
- Responsibilities
- Reporting structure
- Skills
- Staffing
RICA
- Responsible for doing
- Needs to be Informed
- Consult before a decision
- Accountable for decisions and delegatioins
Staffing Plan
- Identify sources for resources
- When are they needed
- Training requirements
- Resource processes
Ch03 - Responsibility_Matrix.xlsx
Build a project schedule
- Put tasks in sequential order
- Estimate the time each task will take.
- Assign tasks to project team members
- Calculate task duration
- Account for deadlines and other constrains.

Develop a project budget
- Labor
- Vendors
- Contractors
- Employees
- System
- Other(travel)
- Contingency
- Total
Burdened Cost
For Employees
- Salary
- Benefits
Time-Based Resources
- Rental equipment
- Leased office space
Materials
- Equipment being installed
- Construction materials
- Consumable goods
Ancillary
- Travel
- Training
- Fees
Assign resources and other costs to the tasks in your project schedule.
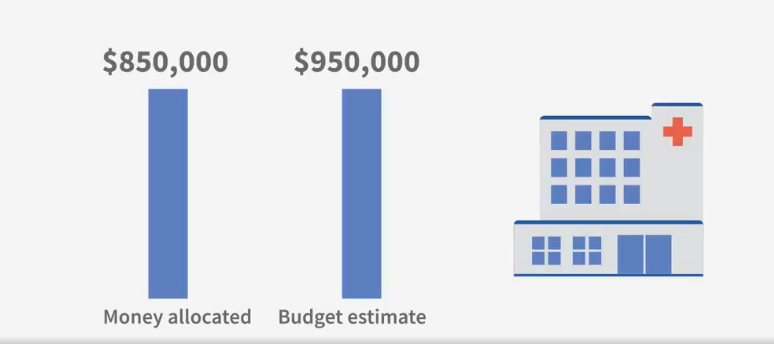
Money Allocated
If estimate is high:
- Eliminate nonessential expenses
- Use less expensive resources
- Cut scope
Hospital Scheduling Project
Ch03- Best Estimate.pdf
Identify risks
Known Unknows
- Weather delays
- Unavailable resources
- Technology
- Time Zone
- relationship
- deliverables
- limited options
- Unknown unknows
- unforeseeable events
- contingency funds (应急费用)
Project Budget/Schedule
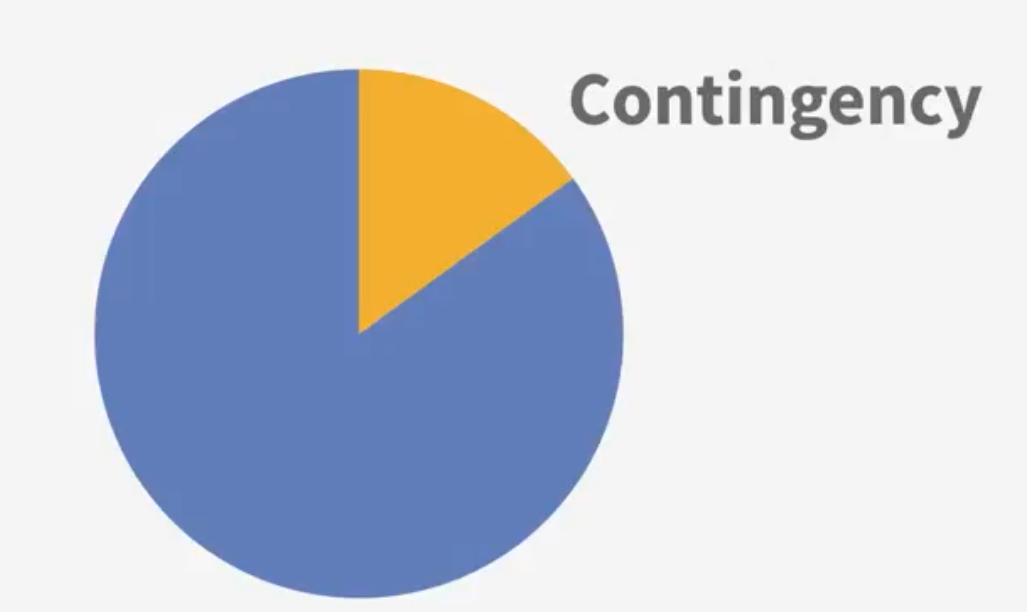
some 15% according to experience, and depends on situation
Ch03-Risk Information Form Template.docx
create rish information sheet
Create a risk management plan
Evaluate Rish
- How likely?
- How serious?
| Probability | 1 low | 3 medium | 5 high |
| Impact | 1 low | 3 medium | 5 high |
- Unlikely and not serious
1 x 1 = 1 - Medium likely and serious
3 x 3 = 9 - Very likely and serious
5 x 5 = 25
Avoid Rish
- Changing project scope
Mitigate Rish
- Reducing impact
Transfer Risk
- Handing risk to someone else
- Your response to the risk should reflect the impact of the risk.
- Review and update the risk management plan regularly
Ch03 - Risk log template.xlsx
Set up a communication plan
- identify your audiences(who should know)
- Who, What, How
- Who - management
- What - objective
- How - Project plan, Status reports, Expenditures, Closeout report
- Who - Sponsor
- What - Objective
- How - Weekly 1:1
- Who - Functional managers
- What - Skill sets, Milestones, Constraints, Schedules
- How - Bi-weekly email
- Who - Team
- What - Assignments, Upcoming tasks, Changes, Best Practices
- How - Weekly emails
- Who - management
Communication Distribution
- Frequency
- Fromat (face to face, email)
Develop a quality plan
Quality
- Meeting customer's requirements on time and within budget
- Conforming deliverables to specifications
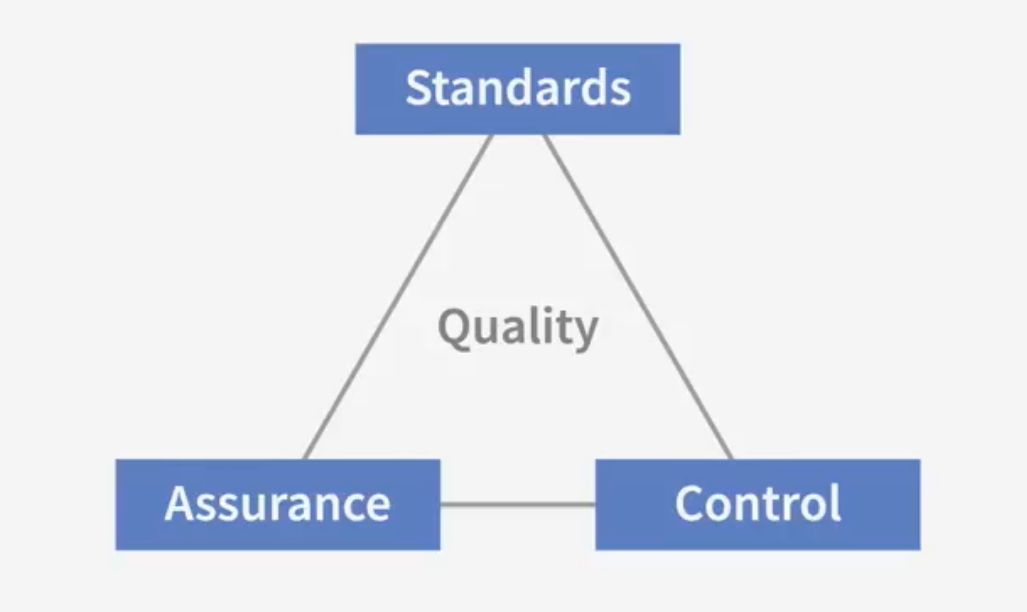
- Quality Standard(can't be lower)
- Longer scheduling Increased cost(can't be higher)
Quality Assurance Plan
Processes needed to meet quality standards
Quality Control
Measure and monitor quality of final deliverables
- Acceptance test
- Inspection
- Peer review
- Walk-through
- Audit
Tools for quality improvement
Cost-Effective Diagrams(Fish-bone diagrams)
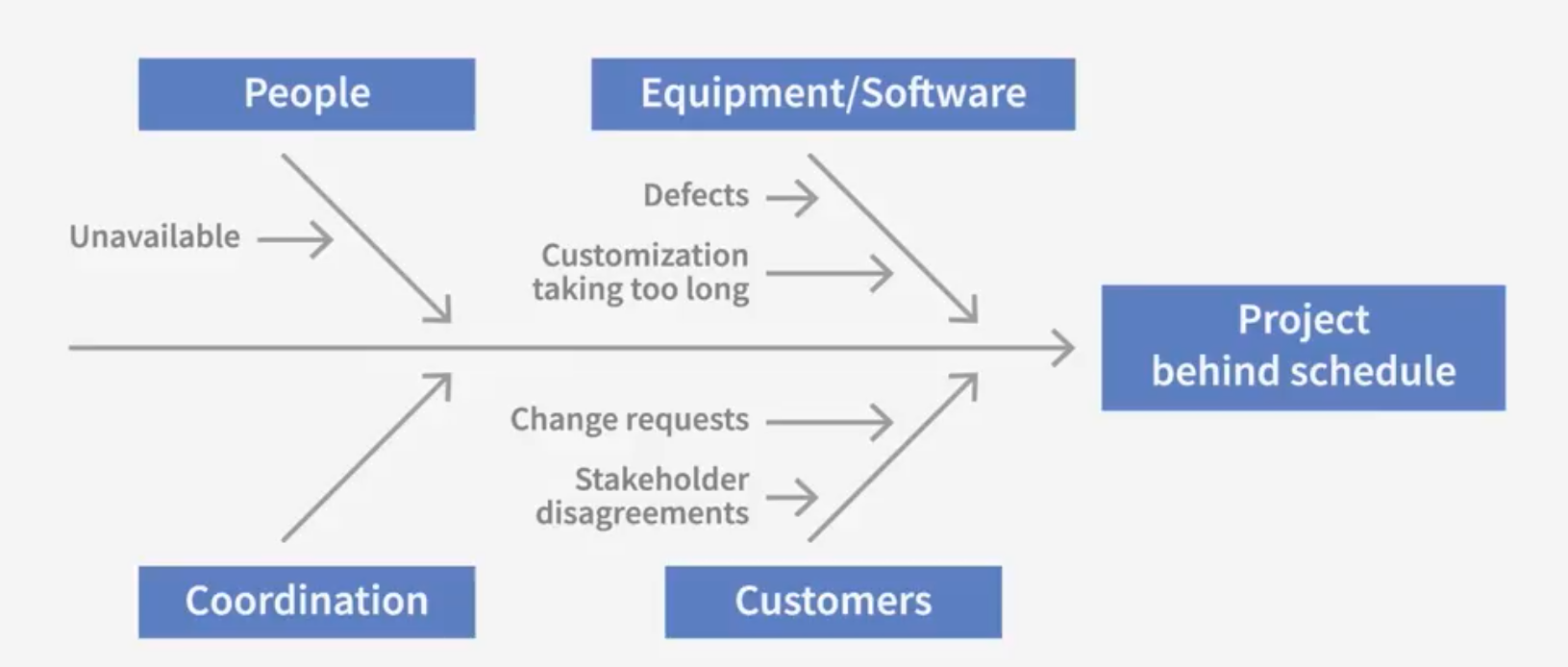
facts may lead the problems
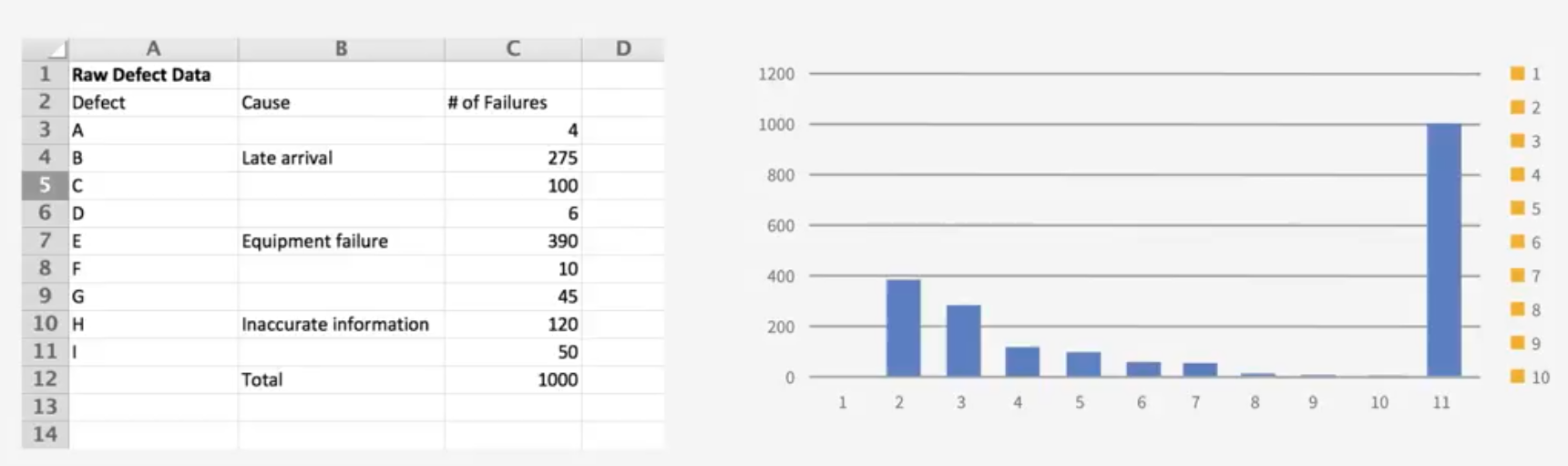
Develop Quality Management Plan
Ch03 - Quality.pdf
How to set up a change
- Identify what you want to control
- Components
- Project scope
- Requirements
- Schedule
- Project plan
- Baseline documents(control version)
- requirements approved by stakeholders is the baseline
- New requirement
- Change management process
- Decide whether to accept the change or deny it.
- decided by Change Review Board
- made up with key stakeholders
- Change management process
- Components
- Define a change management process
- depends on
- Company culture
- Project size
- Components
- Receive change request
- Evaluate change request
- Effect, Cost, Impact, Risk
- Change review board reviews evaluated change requests
- accpet or reject
- ask for more detail or revision
- Track change request
- Result
- Update baseline document to reflect the change
- Additional Considerations
- Setting thresholds
- project manager can decide small change
- Emergency changes
- Setting thresholds
- depends on
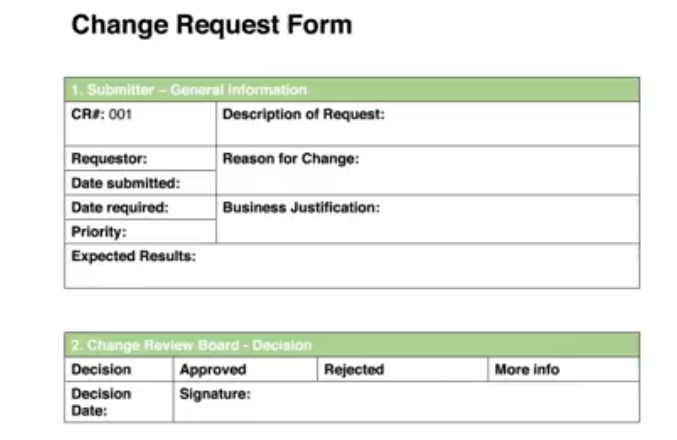
- Ch03 - CR Form.pdf
- Ch03 - Change Solution.pdf
How to plan procurement
procurement plan
- Identify purchase needs
- Skills
- Additional resources
- Products
- Materials
- Document procurement processes
- Identify vendors
- Select vendors
- Manage contracts
- Describe the make-or-buy decision process
- Understand needs
- Determine if products are available
- Determine suitability
- List potential vendors
- Describe research
- Criteria for list
Procurement Plan
- Find out what to do first
- Give yourself a confidence boost
- Build a growth mindset for happiness
- Create balance and overcome burnout
How to obtain approval to procceed
- face-to-face sign off meeting is more effective
arrange specific meeting for approval
Plan Approval
- Present plan
- Ask for signatures
- after present, once agreed
Challenge: Change
Ch 03 - Chapter 03 CR Form.pdf
