Cybersecurity System Audits
Chapter 3 – IT Governance and Management
Objectives
- IT Management Practices
- Insourcing and Outsourcing
- Change Management
- Quality Management
- IT Organization Structure
- Roles and Responsibilities
- Segregation of Duties
- IT Audit Governance
Introduction to IT Management Practices
- IT management practices are important for ensuring the smooth functioning of IT services within an organization.
- The primary IT services—development, operations, and support—are supported by secondary management practices.
- These secondary activities include:
- personnel management, which deals with hiring and training employees;
- sourcing, which determines where and how work is performed;
- third-party service delivery management, which oversees external services;
- and change management, which governs IT system changes.
- Additionally, there are practices like financial management, quality management, portfolio management, controls management, security management, and performance and capacity management, all of which ensure IT services meet business needs.
Personnel Management and IT Steering Committees
- Personnel management encompasses all activities related to hiring, training, and policy enforcement to ensure that employees align with organizational goals.
- It ensures that individuals are properly vetted and trained to carry out their functions. The IT steering committee, a cross-departmental team, ensures centralized management of IT practices across the organization.
- For example, HR usually handles hiring and training, but the IT steering committee ensures these processes are aligned with IT needs, facilitating collaboration between departments like HR and IT. This integration promotes the cohesive management of personnel within the IT framework.
Hiring and Background Verification
- Hiring is a vital personnel management function, ensuring that qualified individuals with verified backgrounds are selected.
- Background verification is a critical process to confirm the information provided by candidates. It includes checking their employment history, ensuring they have relevant work experience; education verification, confirming earned degrees; and military service checks, verifying military background and discharge status.
- Additionally, employers verify professional licenses and certifications and may perform criminal background checks to ensure there are no legal concerns.
- In certain cases, employers may also check for credit history and terrorist associations to further reduce risk.
Employee Policy Manuals
- An employee policy manual or handbook outlines the expectations and rights of employees. It typically includes key topics like company policies on security, privacy, and ethical conduct, ensuring that employees understand what is required.
- It also provides details on compensation, describing when and how employees are paid; benefits, explaining health coverage, retirement plans, etc.; and work hours, which define daily expectations.
- Policies on dress code, performance reviews, and promotions are also covered, providing clarity on professional behavior and opportunities for advancement.
- Finally, it addresses time off, including vacations and sick leave, and disciplinary processes for managing misconduct.
Initial Access Provisioning
- New employees require access to locations, systems, and networks to perform their duties. Initial access provisioning is the process that determines what access rights should be granted based on their roles.
- For instance, a job template helps predefine access rights for various positions, ensuring consistency. Managers make formal requests for necessary permissions based on these templates.
- Proper access provisioning minimizes security risks by granting employees only the privileges needed for their job.
- Ensuring an efficient process helps organizations manage access control effectively, protecting sensitive information while ensuring employees can perform their tasks efficiently.
Job Descriptions
- A job description is a formal document outlining the responsibilities, skills, and qualifications needed for a specific role.
- It provides clear expectations for each position, from entry-level staff to senior executives. Job descriptions also include adherence to organizational policies, such as security and acceptable use.
- For example, an IT manager’s description would outline responsibilities for overseeing IT operations, while also ensuring compliance with security protocols.
- Additionally, job descriptions must include standard clauses, such as equal opportunity statements, ensuring that the company complies with labor laws.
- This clarity helps employees understand their role and expected behavior within the organization.
Employee Development
- Effective organizations focus on employee development to align workforce capabilities with company goals.
- Training is essential to keep employees updated on necessary skills, policies, and the use of tools.
- Employees also need periodic updates on practices and techniques, helping them adapt to changing technologies.
- Performance evaluations assess employees' contributions against set expectations and may influence compensation decisions.
- A well-structured career path enables employees to visualize their advancement within the company, encouraging skill development to qualify for higher positions.
- Such programs foster employee growth and contribute to the long-term success of both the individual and the organization.
Mandatory Vacations
- Mandatory vacations are a strategy employed by organizations in high-risk sectors to mitigate operational risks. Requiring employees to take at least one week off allows the organization to conduct internal audits, ensuring there are no signs of misconduct.
- It also facilitates cross-training, as other team members step in to cover the absent employee’s duties, preventing dependency on a single individual.
- Additionally, the enforced absence reduces the risk of ongoing fraudulent or unethical activities, as they may be uncovered by others in the employee’s absence. This practice ultimately strengthens organizational integrity and operational transparency.
Employee Termination Procedures
- When an employee leaves the organization, the termination process ensures both security and compliance. The first step is to revoke physical access to office locations.
- This is followed by disabling the employee's network and system accounts to prevent unauthorized access to sensitive information.
- Whether accounts are locked or permanently removed depends on the organization’s policy.
- In cases where audit logs depend on account IDs, it may be necessary to lock the account rather than delete it.
- Ensuring proper account handling minimizes security risks and helps maintain accurate records for auditing purposes, protecting the organization from potential breaches.
Transfers and Reassignments
- During transfers or reassignments, employees often accumulate unnecessary privileges, a situation known as privilege creep.
- For example, an employee who moves from finance to IT may retain access to financial systems, creating a security risk.
- Accumulated access across roles can enable employees to perform unauthorized actions.
- To mitigate this risk, organizations must carefully manage access control by revoking any outdated privileges during role changes.
- A well-implemented access management process ensures that employees only retain the privileges necessary for their new position, helping to prevent misuse and maintain organizational security standards.
Sourcing Options
- Sourcing refers to how and where an organization’s workforce is located and hired.
- Insourced workers are full-time or temporary employees hired by the organization itself, while outsourced personnel are contractors or consultants hired externally.
- A hybrid model involves using both.
- Additionally, sourcing can vary based on location: on-site workers operate at the organization's physical location, while off-site local workers perform tasks near the premises but not on-site.
- Off-site remote workers are further away, typically in the same country, while offshore workers are located internationally, and nearshore workers operate from nearby countries.
Insourcing and Outsourcing Overview
- Insourcing refers to the practice of hiring employees for long-term roles within an organization. It involves managing internal personnel who perform core business functions.
- Insourcing provides stability and better alignment with company culture and goals. On the other hand, outsourcing refers to hiring external contractors or consultants for specific tasks or projects.
- Organizations outsource for various reasons, including project duration, where contractors are employed for short-term needs, and skills requirements, where external expertise is sought for specialized skills that are not needed on a full-time basis.
Reasons for Outsourcing
- Organizations opt for outsourcing to handle tasks efficiently and cost-effectively. One reason is variable demand, where workforce needs fluctuate, such as seasonal peaks.
- High turnover positions, like IT helpdesk roles, are outsourced to reduce the costs of constant training and replacement. Outsourcing also allows organizations to focus on core activities by transferring non-core functions, such as IT support, to external vendors.
- Financial reasons often motivate outsourcing, such as offshoring to reduce costs by leveraging lower wages in other countries. Finally, outsourcing can ensure complete time coverage by hiring teams in different time zones for 24/7 service.
- Objectivity is another benefit, as external personnel can approach tasks like process improvement with impartiality.
- Lastly, outsourcing can lead to reduced costs, especially when offshoring work to countries with lower labor rates, thereby improving the organization's competitive position in the market.
Outsourcing Risks
- Although outsourcing offers significant benefits, there are associated risks that organizations must carefully evaluate.
- One key risk is higher than expected costs. While initial cost savings may seem appealing, unforeseen expenses—such as frequent travel for oversight or changes in currency exchange rates—can quickly escalate, making outsourcing more expensive than anticipated.
- Another major risk is poor quality. Outsourced tasks, especially when done offshore, may not meet the organization's internal quality standards, leading to subpar results.
- Another critical issue is the loss of control. When an organization outsources services, particularly to foreign entities, it relinquishes a certain level of oversight.
- Adjustments to workflows and processes can become time-consuming and more costly. There's also a concern about the integrity and background of outsourced personnel, particularly when dealing with countries that lack comprehensive background check systems.
Mitigating Outsourcing Risks
- To mitigate the risks associated with outsourcing, organizations need to implement several measures. A well-defined service level agreement (SLA) is essential, as it outlines expectations regarding work performance, timelines, and quality standards.
- The SLA should include provisions for quality, defining error rates or performance targets. It is also critical to specify security policies and controls in the contract, ensuring that the outsourcing provider maintains appropriate safeguards to protect intellectual property and sensitive data.
- Organizations should retain the right to audit the provider’s operations to verify compliance with agreed-upon standards, offering a way to address potential issues.
- Other critical contract provisions include business continuity planning, where the outsourcing provider must have measures in place to maintain operations during emergencies or disasters.
- Contracts should also address employee integrity, ensuring that the provider performs proper background checks on its staff.
SaaS, IaaS, and PaaS Considerations
- When considering cloud-based services, organizations often turn to Software-as-a-Service (SaaS), Infrastructure-as-a-Service (IaaS), or Platform-as-a-Service (PaaS) solutions.
- SaaS allows organizations to use software hosted by a third party, eliminating the need for internal servers or maintenance teams.
- IaaS provides virtualized computing resources over the internet, allowing companies to rent infrastructure like servers and storage.
- PaaS offers a platform for developers to build and deploy applications without managing the underlying hardware.
- These models offer significant capital and labor savings, as they reduce the need for upfront investments in hardware and minimize ongoing maintenance tasks.
Change Management
- Change management is an essential business process designed to control changes within an IT environment. A formal change management process comprises six steps.
- Request: The initial submission of a proposed change.
- Review: Evaluation of the potential impacts and risks associated with the change.
- Approve: Management or a change control board formally approves or denies the change.
- Perform: The change is implemented following the approved plan.
- Verify: Testing and monitoring to ensure the change works as intended.
- Back out: If the change fails verification, a rollback procedure restores the system to its previous state.
- Each step involves detailed recordkeeping.
Financial Management in IT
- Financial management is a critical component of IT, particularly because IT services are cost-intensive.
- Organizations must manage their finances carefully, ensuring both short-term and long-term budgeting plans are in place. Strategic financial decisions, such as whether to develop, purchase, or rent software, significantly impact IT operations.
- For example, developing software in-house requires resources and expertise, while purchasing a license or renting via a cloud/SaaS model may reduce upfront costs.
- In addition, financial management also covers decisions related to IT services like helpdesk, PC support, and network management, determining whether these should be insourced or outsourced.
Software Acquisition Models
- In financial management, one of the key decisions involves software acquisition. Organizations must decide between three main options.
- Develop: Building custom applications in-house or using contracted developers.
- Purchase: Buying licenses from vendors and deploying software on owned servers.
- Rent: Opting for a Software-as-a-Service (SaaS) model where the application is hosted by a third party, and organizations pay based on usage.
- Each choice has financial implications, such as development costs, capital investment in servers, or ongoing subscription fees, and the decision also depends on the level of control the organization requires.
Quality Management
- Quality management in IT involves controlling, monitoring, and improving business processes to ensure continuous improvement.
- Quality management systems can cover a variety of IT activities, including software development, software acquisition, IT operations, and security. An effective quality management system relies on several components, including fully documented processes, key measurements for evaluating process performance, and management reviews of these measurements.
- Additionally, audits should be conducted regularly to ensure compliance with quality standards, and process changes should be made when measurements indicate a need for improvement or modification in existing processes.
- In quality management, key measurements are essential for evaluating the performance of processes. These measurements go beyond simple tallies and involve recognizing, classifying, and quantifying incidents, events, problems, and defects.
- By tracking these metrics, management can understand how well processes are functioning and where improvements are needed.
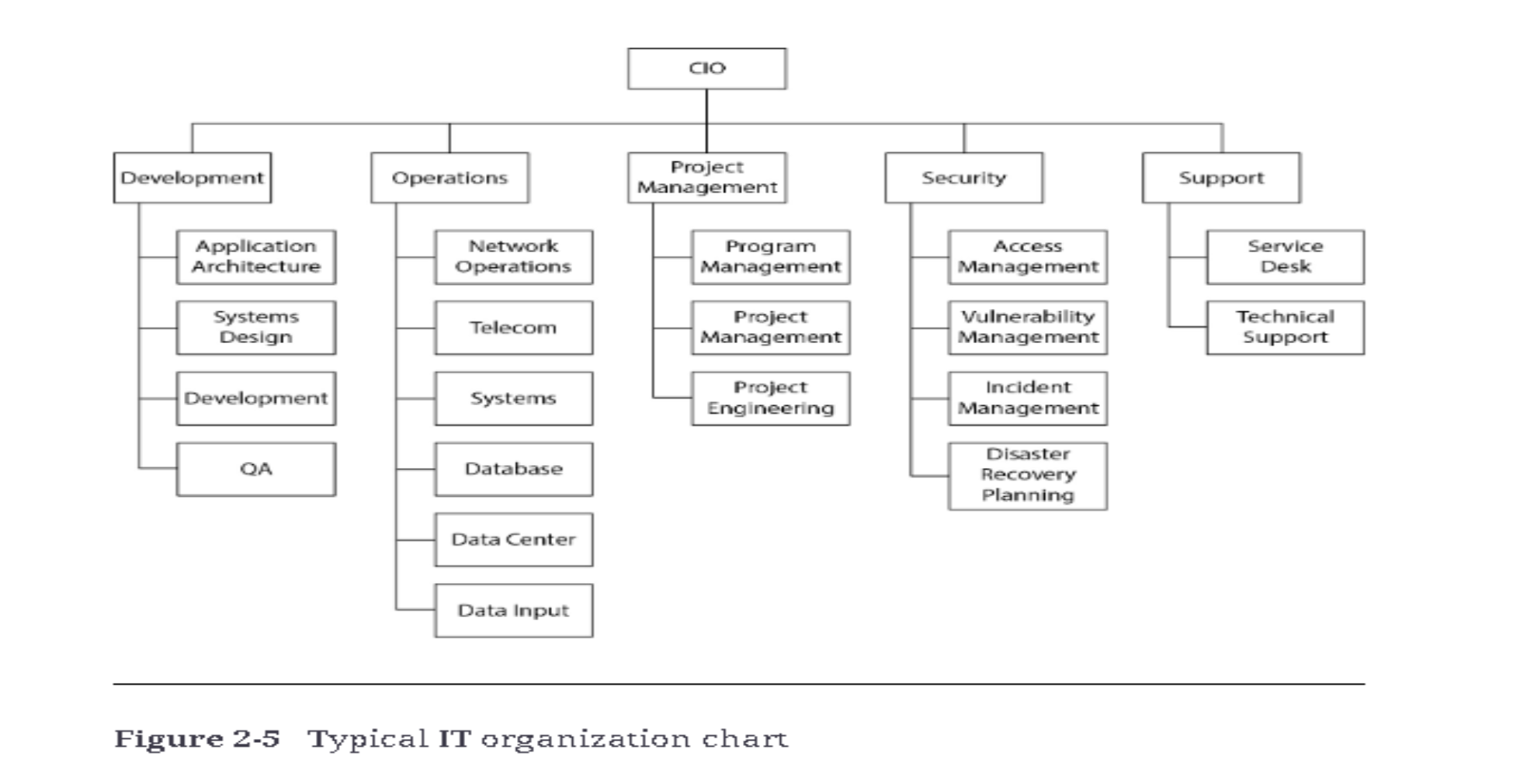
Typical IT Organization Structure
- The structure of an IT organization is dynamic, constantly evolving to meet the needs of the business. Figure 2-5 illustrates a typical IT organization chart, highlighting the flow of responsibilities and communication.
- Organizational structures are "living" entities, subject to changes based on several factors, such as short- and long-term objectives, market conditions, regulations, and attrition.
- These factors influence how departments and leadership are realigned to foster new synergies, improve efficiencies, or comply with emerging regulations.
- Succession planning is often employed to address unexpected leadership changes and ensure continuity in key roles.
Typical IT Organization Structure
Succession Planning in Organizational Structure
- Succession planning is an essential strategy for managing unexpected changes in leadership.
- Many organizations formalize this process to prepare for resignations, terminations, or unforeseen absences.
- A succession plan identifies potential candidates who can temporarily fill key positions, ensuring continuity until a long-term replacement is found.
- Succession planning helps mitigate the risks associated with leadership gaps and ensures that the organization can maintain stability and operational efficiency even during periods of transition.
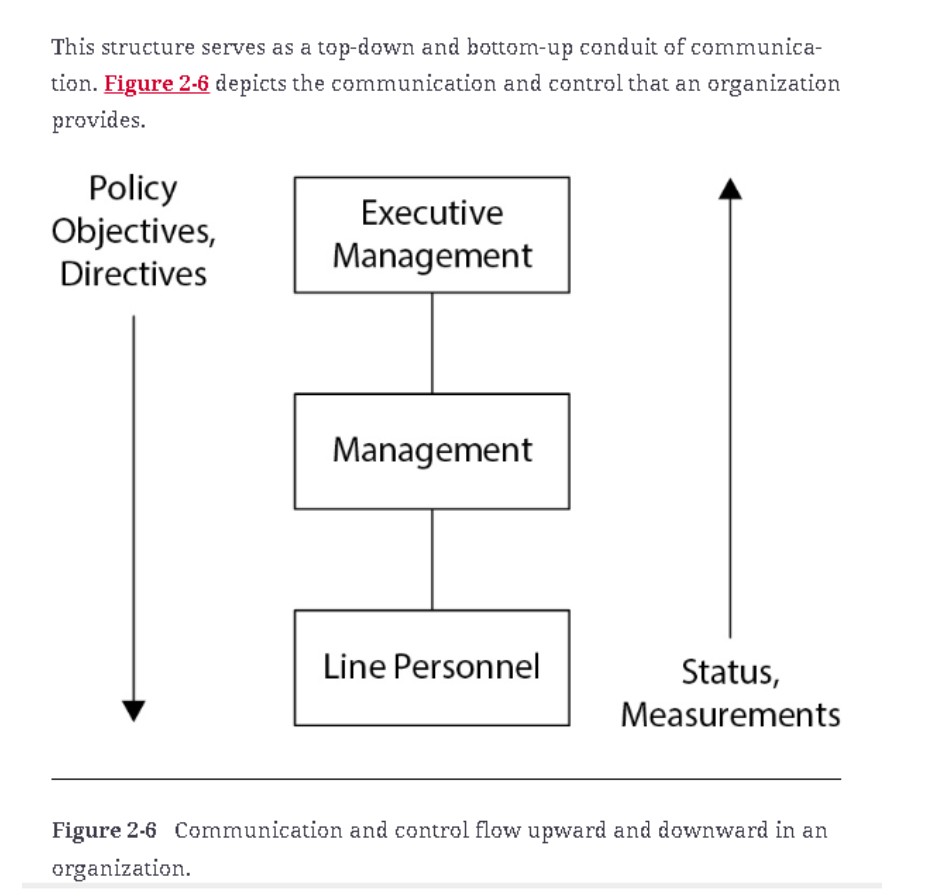
Communication and Control in an Organization
- Communication and control flow both upward and downward within an organization, as depicted in Figure 2-6.
- This structure ensures that information is shared across all levels of the organization, allowing executives to communicate directives and gather feedback from staff.
- The bidirectional flow of communication is crucial for maintaining transparency, accountability, and operational efficiency.
- It also fosters a culture of collaboration, where employees at all levels feel empowered to contribute to the organization’s success while adhering to established processes and controls.
Roles and Responsibilities
- In an IT organization, roles and responsibilities encompass various dimensions, including positions on the org chart, job titles and duties, and expectations regarding the use and protection of assets.
- Every individual within the organization has specific roles to fulfill, whether as part of executive management, asset ownership, or operational support.
- These responsibilities ensure that the organization’s assets are properly managed and that personnel at all levels understand their duties and obligations.
- Formal definitions of these roles help create a structured and efficient working environment.
Individual Roles and Responsibilities – Board of Directors
- The board of directors plays a pivotal role in overseeing the organization’s activities and ensuring that senior management is held accountable.
- The board is responsible for selecting, supporting, and reviewing the chief executive and ensuring the organization adheres to its mission and objectives.
- In private companies, board members typically include senior executives from the organization and external firms. In government, directors are often elected.
- Today, directors face increased scrutiny and are held to higher standards of personal responsibility for the outcomes of the organizations they govern.
Individual Roles and Responsibilities – Executive Management
- Executive management consists of the most senior leaders within the organization.
- These individuals are responsible for developing the organization’s mission, goals, and policies.
- They play a crucial role in enacting security policy, which defines the protection of organizational assets.
- By establishing clear objectives and ensuring policies are properly implemented, executives guide the organization toward achieving its strategic goals.
- Executive management also ensures that security policies are consistently applied across all levels of the organization, safeguarding critical assets and data.
Individual Roles and Responsibilities – Asset Owners
- An owner is an individual, typically a manager, who is designated as the steward of a specific asset.
- This responsibility includes ensuring the asset’s maintenance, integrity, and security. Depending on the organization’s security policy, the owner may also determine who has access to the asset and who is permitted to make changes to it.
- For instance, if the asset is information, the owner is responsible for managing permissions and ensuring that only authorized individuals can modify or view the data.
Individual Roles and Responsibilities – Managers
- Managers play a critical role in ensuring that their teams understand and adhere to the organization’s policies and procedures.
- In addition to managing day-to-day operations, managers are responsible for disseminating information about policies to their staff and ensuring compliance.
- They may also be held accountable for their staff’s behavior, particularly regarding adherence to security policies and procedures.
- Managers serve as the link between executive leadership and frontline employees, ensuring that organizational goals are met through effective policy implementation.
Individual Roles and Responsibilities – Users
- Users are individuals who interact with organizational assets as part of their job duties.
- Each user is responsible for the proper use of these assets and must not allow unauthorized individuals to access them.
- Users are expected to perform their tasks lawfully and in accordance with organizational policies.
- Whether full-time employees, part-time workers, or contractors, users must ensure that they follow established guidelines to protect the organization’s assets and data integrity.
- Their role is crucial in maintaining the organization’s security posture.
Executive Management Positions – CIO and CTO
- Within executive management, the Chief Information Officer (CIO) is the top leader of the IT organization, responsible for overseeing all aspects of information technology.
- The Chief Technical Officer (CTO) is typically responsible for the organization’s overall technology strategy.
- While the CIO focuses on managing the internal IT infrastructure, the CTO may focus on technology development and innovation, depending on the organization's mission.
- Both roles are critical in ensuring that the IT strategy aligns with broader business objectives and supports the organization’s growth and success.
Executive Management Positions – CRO, CSO, and CISO
- The Chief Risk Officer (CRO) oversees all aspects of risk management, including information risk, business risk, and compliance risk.
- The Chief Security Officer (CSO) manages both information security and physical security, ensuring that the organization’s assets are protected from threats.
- The Chief Information Security Officer (CISO) focuses specifically on information security, overseeing activities like incident management, disaster recovery, and compliance with security standards.
- These roles are integral to the organization’s ability to manage risk, respond to security incidents, and maintain compliance with legal and regulatory requirements.
Software Development Roles
- Within the IT organization, several roles focus on software development.
- A systems architect is responsible for designing the overall architecture of the organization’s information systems.
- A software engineer or developer focuses on writing and maintaining software applications, often working closely with systems architects to ensure that the applications meet business needs.
- A software tester ensures that changes to programs are tested for functionality and security before they are implemented in the production environment.
- Each of these roles is essential to developing and maintaining the organization’s software systems.
Data Management Roles
- In data management, positions like data manager, data scientist, and database architect focus on designing, maintaining, and analyzing data systems.
- The data manager oversees data architecture and ensures data quality, while the data scientist employs scientific methods to extract insights from data.
- The database architect designs data models, while the database administrator (DBA) is responsible for building and maintaining databases.
- These roles ensure that the organization’s data is secure, accessible, and used effectively to support business operations and decision-making.
Network Management Roles
- Network management roles are responsible for designing, implementing, and maintaining the organization’s communication networks.
- A network architect designs data and voice networks, ensuring they meet the organization’s objectives.
- The network engineer configures and maintains network devices such as routers, switches, and firewalls.
- A network administrator performs routine tasks, like monitoring network performance and making configuration changes.
- Together, these roles ensure that the organization’s networks are secure, reliable, and optimized to support business operations.
Systems Management and Operations
- Systems Management oversees the architecture, design, and maintenance of servers and operating systems, ensuring that IT infrastructure is secure, reliable, and supports the organization's objectives. Key roles include:
- Systems Architect: Designs the architecture of systems, focusing on both internal and interconnected components.
- Systems Engineer: Builds and maintains servers and their operating systems.
- Systems Administrator: Handles routine maintenance and configuration of systems.
- Operations focuses on the day-to-day functioning of IT systems. This includes tasks like monitoring, backups, and managing batch jobs. Key roles in operations include:
- Operations Manager: Oversees the operations team.
- Operations Analyst: Monitors system health and maintains operational records.
- Systems Operator: Executes backup tasks and monitors system performance.
Security Operations Roles
- Security Operations ensures that IT systems are protected from threats, maintaining confidentiality, integrity, and availability. Core roles in security operations include:
- Security Architect: Designs security controls such as firewalls, intrusion detection, and authentication systems.
- Security Engineer: Implements and maintains security infrastructure as designed by the security architect.
- Security Analyst: Monitors logs from systems like firewalls and intrusion detection systems, issuing security advisories.
- Access Administrator: Manages user permissions and access levels across systems.
- Security Auditor: Conducts internal audits to verify the effectiveness of security controls, ensuring compliance with security policies and regulations.
Segregation of Duties (SOD)
- Segregation of Duties (SOD), also known as separation of duties, ensures that no individual has excessive privileges to carry out potentially harmful actions on their own.
- It introduces checks and balances so that high-value and high-sensitivity tasks are coordinated by two or more authorized individuals.
- This prevents unauthorized activities like fraud, data manipulation, or exposure.
- SOD has long been established in accounting departments to prevent conflicts of interest, but IT departments have only more recently adopted full SOD practices due to scandals in the 1980s and 1990s, along with regulations like Sarbanes-Oxley.
- SOD principles include dividing responsibilities between multiple parties, creating transparency, and ensuring proper authorization for activities.
- Given the complex nature of modern IT environments, SOD plays a crucial role in protecting sensitive information and ensuring compliance with regulatory standards.
- SOD principles include dividing responsibilities between multiple parties, creating transparency, and ensuring proper authorization for activities.
SOD Controls: Transaction Authorization & Split Custody
- One example of an SOD control is transaction authorization. This control requires two or more people to approve high-value or high-risk transactions.
- For instance, in retail environments, a manager’s approval may be required for refunds or large transactions. In IT systems, authorization may be required for activities that exceed predefined limits. By having multiple levels of authorization, organizations ensure that no single person can independently execute critical actions, which reduces the risk of fraud or unauthorized system changes.
- Split custody is another key control within SOD. It involves dividing control of high-value or sensitive assets between multiple individuals.
- For example, the password to an encryption key might be split in half, with one half assigned to one person and the other half to another. Similarly, banks use this practice for their vaults, requiring two or more people to combine their knowledge to access the vault. This ensures that no single person has complete control over the asset, reducing the likelihood of theft or fraud.
SOD Controls: Workflow-Based Approvals & Periodic Reviews
- Many IT systems incorporate workflow-enabled applications that require multiple levels of approval for certain tasks.
- For example, in an application used to provision user accounts, additional managerial approvals may be required for granting administrative privileges. This workflow ensures that critical tasks, such as granting access to high-value systems or information, are subject to oversight and multiple levels of scrutiny, preventing unauthorized or unapproved changes.
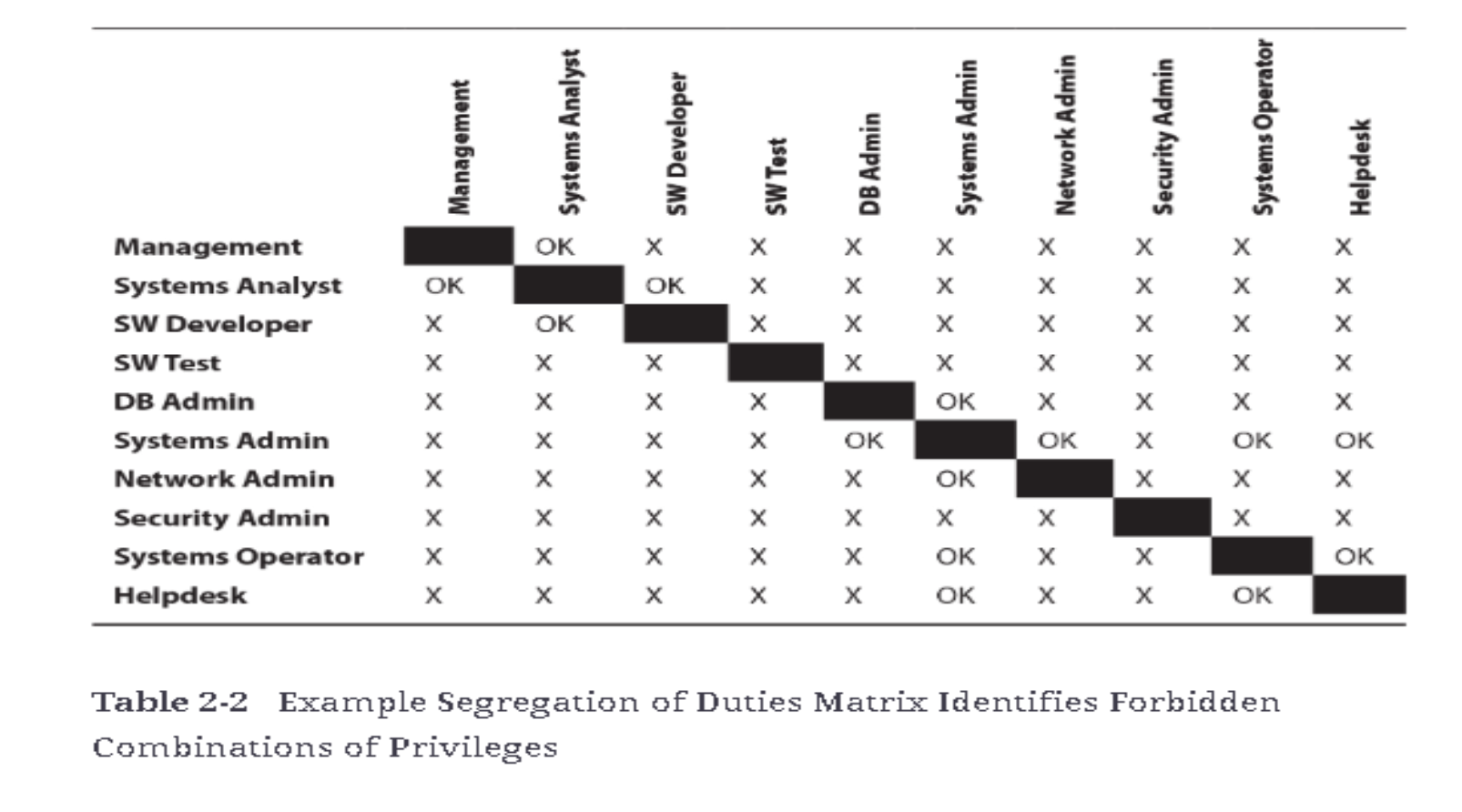
- Periodic reviews are essential for ensuring ongoing compliance with SOD policies. Internal IT teams or external auditors should regularly review user access rights to identify potential conflicts.
- For example, access privileges can be compared against a Segregation of Duties matrix to ensure that no individual has excessive control over critical tasks. If any issues are identified, management can take corrective action, such as reducing access privileges or introducing additional controls.
Segregation of Duties
Mitigating Segregation of Duties Issues
- When Segregation of Duties (SOD) issues are identified, management must decide how to mitigate them.
- One option is to reduce the conflicting access privileges of the individual involved.
- Alternatively, new preventive or detective controls can be introduced to compensate for the conflict.
- Examples include increased logging of user actions, enhanced exception reporting, or periodic reconciliations of sensitive data sets.
- These measures help ensure that unauthorized activities are detected and addressed promptly.
Regular SOD Matrix Review
- An organization should conduct regular reviews of its SOD matrix, especially when new roles or applications are added.
- This ensures that the SOD framework remains up-to-date and relevant to the organization’s evolving needs.
- Periodic reviews allow the organization to proactively identify potential conflicts before they result in unauthorized actions, fraud, or compliance violations.
- Updating the SOD matrix helps the organization maintain robust controls and ensure that all critical tasks are subject to the necessary oversight.
Auditing IT Governance
- IT governance focuses more on business processes than on technology, making audits of IT governance rely heavily on interviews and documentation reviews.
- Effective governance audits examine whether the IT strategy aligns with the organization's goals and whether proper controls are in place.
- IS auditors review documentation and interview both IT personnel and end users to assess the effectiveness of governance structures.
- An audit provides insights into the maturity and operational performance of the IT department. Several signs can indicate poor IT governance:
- Discontentment among staff and end users: Burned-out IT staff or unhappy users may indicate poor governance.
- Poor system performance: Frequent downtime or a large backlog of support tasks suggests inefficiency.
- Nonstandard hardware/software: A mix of technologies may indicate a failure to enforce technology standards.
Project dysfunction: Late or over-budget projects signal a lack of project management discipline. These issues point to a lack of governance maturity and should be addressed in governance reviews.
Auditing Documentation and Records
- At the heart of an IT audit is the examination of documentation and records, which reflect IT control, planning, and daily operations.
- Auditors review documents like the IT charter, organization charts, job descriptions, and performance reviews to evaluate the maturity and effectiveness of IT governance.
- These documents provide evidence of management’s commitment to strategic IT planning and offer insight into how well policies are being implemented and followed across the organization.
Summary
- Assigned IT management roles ensure that resource allocation, enterprise performance, and operational capabilities coordinate with business requirements by validating alignment with standards and procedures for change management and compliance with sourcing, financial, quality, and security controls.
- Formal organizational structure ensures alignment between operational roles and responsibilities within the enterprise, where a separation of duties ensures individual accountability and validation of policy alignment between coordinated team members.
- Regular audit of the IT governance process ensures alignment with regulatory and business mandates in the evolving enterprise by ensuring that all documentation, contracts, and sourcing policies are reviewed and updated to meet changes in the living enterprise.
