Section 5.5 Vulnerability Scoring Systems
As you study this section, answer the following questions:
- Why is it helpful to use tools based on known vulnerability databases?
- What are five helpful government-sponsored resources?
- What is the value of a CVSS score to a cybersecurity specialist?
- How is a CVSS score calculated?
- Which CVSS tools are available to evaluate potential vulnerabilities on your network?
Key terms for this section include the following:
| Term | Definition |
|---|---|
| Common Vulnerability Scoring System (CVSS) | A system that categorizes vulnerabilities by threat level. |
| CVSS calculator | A calculator for determining the risk level of vulnerabilities based on base, temporal, and environmental metrics. |
| Cybersecurity and Infrastructure Security Agency (CISA) | A large government-sponsored organization that provides many resources for cybersecurity. |
| National Vulnerability Database (NVD) | A government-sponsored, detailed database of known vulnerabilities. |
| Full disclosure | A public, vendor-neutral forum for the discussion of vulnerabilities and threats that often has the newest information. It also has tools, papers, news, and events related to vulnerabilities and threats. |
This section helps you prepare for the following certification exam objectives:
| Exam | Objective |
|---|---|
| CompTIA CySA+ CS0-003 | 1.4 Compare and contrast threat-intelligence and threat-hunting concepts
2.2 Given a scenario, analyze output from vulnerability assessment tools
2.3 Given a scenario, analyze data to prioritize vulnerabilities
4.1 Explain the importance of vulnerability management reporting and communication
|
5.5.1 Vulnerability Scoring Systems
Click one of the buttons to take you to that part of the video.
Vulnerability Scoring Systems 00:00-00:37 In this lesson, I'm going to talk about vulnerability scoring systems. In the United States, the Department of Homeland Security has a color-coded advisory system that categorizes the danger of potential threats to citizens. This system gives security professionals direction by telling them how quickly to act and which efforts to make to keep the country safe. There's a similar scoring system in place for IT security threats to organizations and businesses. It's called the Common Vulnerability Scoring System, or CVSS. Instead of colors, this system uses numbers to rank IT vulnerabilities.
CVSS Calculator 00:37-01:01 A CVSS calculator can determine a vulnerability's severity level based on three metrics: base, temporal, and environmental metrics. Base metrics describe a vulnerability's unique characteristics. Temporal metrics describe its changeable attributes, and environmental metrics describe vulnerabilities that are only present in certain environments or implementations.
Government Resources 01:01-01:23 This scoring system creates a way for you to prioritize vulnerabilities that you might discover on your network. It also gives you credibility when you present your remediation plan of action, as these are internationally recognized scores. Through the Department of Homeland Security, the US government sponsors five valuable resources for security analysts. Let's go through them one by one.
Common Vulnerabilities and Exposures 01:23-01:55 The first one is Common Vulnerabilities and Exposures, or CVE. This is a list of standardized identifiers for known software vulnerabilities and exposures. CVE is free to use and publicly available at cve.mitre.org. There are currently 94 CVE numbering authorities from 16 countries, which provides a good evaluation baseline for you. It also provides standardization, which allows data exchange for cybersecurity automation and aids professionals as they determine the best assessment tools to use.
National Vulnerability Database 01:55-02:36 The CVE list also supplies the National Vulnerability Database. The National Vulnerability Database, or NVD, was originally created in 2000. You can find it at nvd.nist.gov. The NVD list includes more specific information for each entry than the CVE list, such as fix information, severity scores, and impact ratings. This list is searchable by product name or version number, vendor, operating system, impact, severity, and related exploit range. This detailed database adds breadth to your research. The variety of ways to find results on the site makes searches very efficient.
Cybersecurity and Infrastructure Security Agency 02:36-03:10 The third resource is the Cybersecurity and Infrastructure Security Agency, or CISA. You can access it at us-cert.gov. This government site provides information exchange, training and exercises, risk and vulnerability assessments, data synthesis and analysis, operational planning and coordination, watch operations, and incident response and recovery resources. This site is valuable because it belongs to a large governmental organization with many resources committed to helping you with cybersecurity.
Common Weakness Enumeration 03:10-03:47 The fourth resource is Common Weakness Enumeration, or CWE. You can find it at cwe.mitre.org. CWE is a community-developed list of common software security weaknesses. The community strives to create commonality in software security weakness descriptions. This creates a reference for identifying, mitigating, and preventing vulnerabilities. It also provides a standardized way to evaluate assessment tools. This site combines diverse ideas and perspectives from professionals, academics, and government sources to create a unified cybersecurity standard.
Common Attack Pattern Enumeration and Classification 03:47-04:18 The fifth government-sponsored resource is Common Attack Pattern Enumeration and Classification, or CAPEC. You can find it at capec.mitre.org. It's a dictionary of known cyberattack patterns used by hackers. You can search the list by attack mechanism, attack domain, key terms, and CAPEC ID number. You can browse through the list to see common attacks and their specific patterns. There are other helpful resources available besides the ones sponsored by the Department of Homeland Security. I want to talk about two of them.
Japanese Vulnerability Notes 04:18-04:43 The first is from a non-profit organization in Japan called JPCERT or JVN, which stands for Japanese Vulnerability Notes. This organization is dedicated to helping cybersecurity professionals protect their organizations from attack. It offers detailed information on vulnerabilities, including affected products, possible impacts, solutions, vendor statements, and reference documents.
Full Disclosure 04:43-05:11 The final resource is a mailing list from nmap called Full Disclosure. Not only do they provide a mailing list that often has the newest vulnerabilities listed before they show up on the government-sponsored resources, but the site also provides a vendor-neutral forum for discussing exploitation strategies and vulnerabilities. It's a resource for discovering events that are happening in the cybersecurity community. You can find it at seclists.org/fulldisclosure.
Summary 05:11-05:55 That's it for this lesson. In this lesson, we discussed that a vulnerability scoring system exists to help you evaluate and prioritize the severity level of the vulnerabilities you find. It's critical for security professionals to stay up to date on the most current attack methods. Fortunately, you have several valuable resources that are free for you to access. We introduced you to seven. The first five are sponsored by the United States government. They are CISA, NVD, CVE, CWE, and CAPEC. We also highlighted the Japanese JPCERT or JVN. We finished up by looking at the Full Disclosure vulnerabilities mailing list.
5.5.2 Vulnerability Scoring System Facts
This lesson focuses on vulnerability scoring systems. In the United States, the Department of Homeland Security has a color-coded advisory system that signifies levels of potential threat. This system gives direction on how quickly to act and what efforts to make regarding a threat.
Similarly, a scoring system called the Common Vulnerability Scoring System (CVSS) is in place for IT security threats to organizations and businesses.
This lesson covers the following topics:
- Common Vulnerability Scoring System (CVSS)
- CVSS calculator
- CVSS vector string
- Benefits of CVSS
- CVSS tools
- Government resources
- Non-government resources
Common Vulnerability Scoring System
Common Vulnerability Scoring System (CVSS) is an industry-standard method for assessing the severity of software vulnerabilities. It provides an objective measure of the risk posed by a given vulnerability, allowing IT teams to prioritize remediation efforts and allocate resources more effectively. It was developed by the Forum of Incident Response and Security Teams (FIRST). The following table compares the severity level and the base score range of CVSS 2.0 and CVSS 3.0.
| CVSS 2.0 | CVSS 3.0 | ||
|---|---|---|---|
| Severity | Base Score Range | Severity | Base Score Range |
| - | - | None | 0.0 |
| Low | 0.0-3.9 | Low | 0.1-3.9 |
| Medium | 4.0-6.9 | Medium | 4.0-6.9 |
| High | 7.0-10.0 | High | 7.0-8.9 |
| - | - | Critical | 9.0-10.0 |
CVSS is a vital tool for IT teams to identify, assess, and address potential vulnerabilities, helping to ensure the security of their systems and the data they contain. CVSS is based on the concept of risk. It considers the likelihood of a vulnerability being exploited on a particular system and the potential impact on that system. CVSS is not designed to measure the exploitability of a vulnerability, nor does the scoring take into account the cost of fixing the vulnerability.
CVSS Calculator
A CVSS calculator can determine the risk and severity of a vulnerability. After identifying the threat agent, affected system, impact on the system, and probability of the threat agent accessing the system, the last step is to apply a formula (which varies depending on the identified metrics) to arrive at a CVSS score. A somewhat complicated formula calculates CVSS scores, but the scoring process can be broken down into five steps.
- Identify the threat agent. The most common threat agents used in CVSS scoring metrics are unauthenticated, authenticated, and remote unauthenticated users. Keep in mind that each of these threat agents has a separate impact score.
- Identify the affected system. This includes identifying the product name and the type of system involved.
- Assign a score based on impact. Assign a score based on the impact of exploiting the vulnerability on the affected system. Scoring metrics include confidentiality, integrity, availability, and accountability.
- Identify the probability of the threat agent accessing the system. Determine if the threat agent can successfully access the system. This includes evaluating the system's environment and the threat agent's abilities.
- Calculate the overall CVSS score. The formula used to calculate the overall CVSS score will vary depending on the scoring metrics identified in previous steps.
NIST provides a useful Common Vulnerability Scoring System Calculator available at https://nvd.nist.gov/vuln-metrics/cvss/v3-calculator/
CVSS Vector String
A CVSS vector string is a piece of additional information provided alongside a CVSS score to provide more context around the scoring metrics used to calculate the overall CVSS score. The vector string is broken into fields that include the following:
| Metric | Description |
|---|---|
| Vulnerability identifier | The vulnerability identifier field contains the identifier used to calculate the overall CVSS score. |
| Impact | The impact field provides the overall impact score (determined using the scoring metrics discussed in the previous section) to the affected system due to the exploitation of the vulnerability. |
| Environmental concerns | The environmental concerns field indicates the risk associated with the vulnerability in the target host environment. |
| Additional information | The additional information field provides details about the vulnerability, such as the vendor name, the impact type, and more. |
Benefits of CVSS
CVSS provides an objective measure of the risk posed by a given vulnerability, allowing IT teams to prioritize remediation efforts and allocate resources more effectively. It is important to note that CVSS is not a measure of exploitability, so it does not indicate whether or not a vulnerability can be exploited. Instead, it is designed to provide insight into a vulnerability's potential impact in the event it is exploited. CVSS also gives IT teams more granular information about the vulnerabilities in their systems, allowing them to take a more targeted and efficient approach to remediate those vulnerabilities. It is important to note that each vulnerability has its own CVSS score, allowing IT teams to prioritize those vulnerabilities that pose the highest risk.
CVSS Tools
Given the importance of CVSS, many tools are available to help organizations calculate a CVSS score and understand the potential risks associated with a given vulnerability. The following table identifies some common tools used to calculate a CVSS score:
| Tool | Description |
|---|---|
| Nessus | Nessus is a widely used vulnerability assessment tool to identify system vulnerabilities. It also enables organizations to gauge the risk associated with those vulnerabilities based on several factors, including the CVSS score. |
| OpenSCAP | OpenSCAP is an open-source scanner used to identify system vulnerabilities. It also provides the ability to calculate a CVSS score based on the vulnerabilities identified in the system. |
| Qualys | Qualys is another widely used vulnerability assessment tool to identify system vulnerabilities. It also provides the ability to calculate a CVSS score based on the vulnerabilities identified in a system. |
| OpenVAS | OpenVAS is an open-source scanner used to identify vulnerabilities in systems. It also provides the ability to calculate a CVSS score based on the vulnerabilities identified in the system. |
| SecurityScorecard | SecurityScorecard is a cloud-based solution that enables organizations to assess and improve their security posture. It also provides the ability to calculate a CVSS score based on the vulnerabilities identified in the system. |
Government Resources
The US government, through the Department of Homeland Security, has sponsored five valuable resources for security analysts.
| Resources | Description |
|---|---|
| Common Vulnerabilities and Exposures (CVE) | The CVE is a list of standardized identifiers for known software vulnerabilities and exposures. It is free to use, and it is publicly available at cve.mitre.org. Facts about the CVE include:
|
| National Vulnerability Database | The National Vulnerability Database was originally created in 2000. It can be found at nvd.nist.gov. The NVD list includes detailed information for each entry in the CVE list, such as:
|
| Cybersecurity & Infrastructure Security Agency (CISA) | CISA is a government agency tasked to understand and manage risk to the nation's critical infrastructure. Its website is cisa.gov. The government site provides:
|
| Common Weakness Enumeration (CWE) | CWE is a community-developed list of common software security weaknesses. Its website is cwe.mitre.org. Be aware of the following facts regarding CWE:
|
| Common Attack Pattern Enumeration & Classification (CAPEC) | CAPEC is a dictionary of known patterns of cyber attacks used by hackers. Its website is capec.mitre.org. This list is searchable by:
|
Non-Government Resources
Two non-government sites also provide valuable information for the ethical hacker.
| Resources | Description |
|---|---|
| JPCERT | JPCERT is Japan's CERT organization. It provides security alerts and Japanese Vulnerability Notes (JVN). The website is . This site provides detailed information about each vulnerability, including:
|
| Full Disclosure | Full Disclosure is a mailing list from nmap. Its website is seclists.org/fulldisclosure/ . Full Disclosure is a public forum to discuss of software vulnerabilities and attack techniques. Full Disclosure:
|
5.5.3 CVSS Scoring Considerations
This lesson covers the following topics:
- CVSS scoring considerations
- Vulnerability score adjustment examples
- CVSS score calculations
- CVSS score calculation tools
CVSS Scoring Considerations
Assessing the severity of a vulnerability is a crucial component of vulnerability analysis. It is important to remember that vulnerability scores are not static; they are subject to change based on several factors. When adjusting vulnerability scores, organizations must consider a variety of special considerations, such as the availability of patches, the impact of the vulnerability, and the level of sophistication of the threat actors targeting them. By taking the time to consider these additional factors, organizations can ensure that their vulnerability scores are appropriately adjusted and accurately reflect the actual risk posed by the vulnerability.
Organizations consider several factors to ensure that vulnerability scores are appropriately adjusted. Some of the most common include the following:
| Consideration | Explanation |
|---|---|
| Availability of patches | When vulnerabilities are associated with a piece of software, one of the most important considerations is whether a patch is available. Organizations should be able to use the CVSS vector to find out how quickly a vendor plans to patch a specific vulnerability. In many cases, vendors will provide this information in their security advisories. However, if no patches are available, this is a significant factor that will influence the severity of the vulnerability. For example, a remote code execution vulnerability in a critical piece of software, such as an operating system, will likely have a CVSS score of 10. If an effective patch is available, an organization may shift the score lower, depending on the complexity of the patch. |
| Impact of the vulnerability | Considerations generally include the potential damage caused by successful exploitation and the effort required to mitigate it. For example, a vulnerability that allows an attacker to gain unauthorized access to a single, low-value system will have a lower score than a vulnerability allowing an attacker to modify or delete data stored in a database. |
| Level of sophistication of threat actors | Sophistication level of threat actors determines the likelihood that an attacker can successfully exploit a vulnerability. Some threat actors are well-funded and highly sophisticated, able to identify and exploit vulnerabilities without difficulty. Others rely solely on weaponized vulnerabilities and toolkits and are, therefore, more limited in their ability to execute a successful attack. |
| Asset value | An asset's value may influence a vulnerability's score. Highly valuable assets, like those with far-reaching impacts if breached, may have little tolerance for vulnerabilities, skewing all scores into the high/critical range. |
| Weaponization | Weaponization assesses the likelihood that an attacker will be able to weaponize a vulnerability to achieve their objectives. This metric considers factors such as the attack vector (AV) and attack complexity (AC) which affect the ease with which an attacker can create a functional exploit. An attacker can easily use weaponized exploits to gain unauthorized access to a system, steal sensitive information, or carry out other malicious activities. Additionally, attackers can easily share weaponized exploits for others to use. |
| Exploitability | A vulnerability with high exploitability is more likely to be targeted by an attacker and therefore requires urgent attention. Conversely, a vulnerability with low exploitability may be less urgent as it is less likely to be exploited. The exploitability of a vulnerability depends on many factors, including its attack complexity (AC), the availability of tools and techniques to exploit it (weaponization), and any security measures already in place to defend against the vulnerability. Vulnerability scanning tools and penetration testing can help quantify a vulnerability's exploitability. It is important to note that low exploitability does not mean that a vulnerability is not severe. Analysts must carefully consider all aspects of a vulnerability, including its potential impact, to make informed decisions about remediation. |
These vulnerabilities are highly valuable to attackers. Standard vulnerability scanning techniques cannot detect unknown zero-day exploits because the scanner depends upon a vulnerability database of known vulnerabilities.
Vulnerability Score Adjustments Examples
Consider a hypothetical remote code execution (RCE) vulnerabilisty with a CVSS score of 10. During the risk assessment process, the organization discovers that successfully exploiting the vulnerability requires an attacker to be connected to the same network as the vulnerable application. Further analysis reveals that the vulnerable application only runs on a single, fully air-gapped system. This information would be a justifiable reason to lower the score since the computer is not accessible via the network.
Another example might include a vulnerability marked as "informational" and not designated with a CVSS score, such as vulnerabilities associated with web applications. Further investigation of these vulnerabilities often reveals that the web application is easily exploitable and could result in significant damage.
CVSS Score Calculations
Calculating a CVSS score can quickly become a complex and daunting task. CVSS, or the Common Vulnerability Scoring System, is a framework used to score and rank the severity of IT vulnerabilities, helping organizations better understand and prioritize the threats they face. The scoring system uses a set of metrics that measure a vulnerability's technical, environmental, and temporal characteristics. Knowing how to calculate a CVSS score can be helpful.
The CVSS scoring system consists of several metrics used to calculate a given vulnerability's risk level and grouped into three categories—Impact, Exploitability, and Remediation.
Categories:
- Impact - The potential damage or harm caused by the vulnerability.
- Exploitability - The ease and likelihood of exploiting a vulnerability.
- Remediation - The cost and effort required to fix the vulnerability.
Metrics:
- Scope - The number of systems and people affected by the vulnerability.
- Confidentiality - The extent to which data is disclosed.
- Integrity - The extent to which the system's functionality is changed or impaired.
- Availability - The extent to which a system is unavailable.
- Privacy - The extent to which the system's privacy is impacted.
- Operations - The extent to which the system's security is affected.
- Other - Any other relevant or important factors.
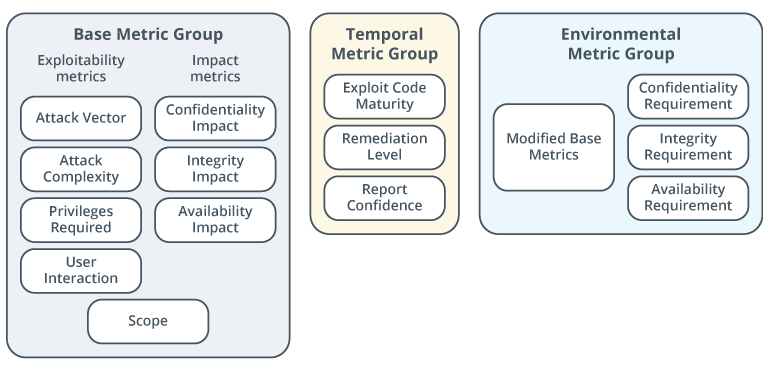
Description
Base metric group - exploitability metrics: attack vector, attack complexity, privileges required, and user interaction; impact metrics: confidentiality impact, integrity impact, and availability impact; scope. Temporal metric group - exploit code maturity, remediation level, and report confidence. Environmental metric group - modified base metrics, confidentiality requirement, integrity requirement, and availability requirement.
CVSS score metrics are grouped into three categories.
CVSS Score Calculation Tools
There are several CVSS score calculators. A few are listed below:
| Calculator Name | Online Location |
|---|---|
Common Vulnerability Scoring System Calculator | https://nvd.nist.gov/vuln-metrics/cvss/v3-calculator/ |
| Common Vulnerability Scoring System Version 3.0 Calculator | https://www.first.org/cvss/calculator/3.0 |
Cisco Security Common Vulnerability Scoring System | https://sec.cloudapps.cisco.com/security/center/cvssCalculator.x |
