Section 2.6 Security Testing
As you study this section, answer the following questions:
- What are the seven attack phases of the kill chain model?
- What is the MITRE ATT&CK framework?
- Explain the four categories of the Diamond Model.
- What information can be found in the Open-Source Security Testing Methodology Manual?
In this section, you will learn to:
- Understand how to find vulnerabilities and risks
- Detecting potential weakness
- Identify the different roles of attacks and attackers
- Explain the four categories of the Diamond Model
The key terms for this section include:
| Term | Definition |
|---|---|
| Reconnaissance | The adversary gathers information about the network using network probes, open-source intelligence (OSINT), and social engineering. The aim is to map the total attack surface and identify potential attack vectors. Targets are then researched, identified, and ultimately selected. |
| Weaponization | The attacker identifies a method by which identified vulnerabilities can be exploited, often through weaponized code, such as carefully crafted scripts, custom malware binaries, compromised websites, social engineering, and other methods. The exploit code is coupled with a payload that will assist the attacker in maintaining and extending covert access. |
| Delivery | The weaponized code is inserted into the environment using a selected attack vector, such as an email attachment, phishing website/download, USB media, and so on. |
| Exploitation | This results in the weaponized code running on the target system. For example, a phishing email may trick the user into running the code, while a drive-by download would execute on a vulnerable system without user intervention. |
| Installation | The payload is successfully installed on the target system using methods to remain undetected and achieve persistence. |
| Command and Control | During this stage, the payload establishes a connection to a remote server, enabling the attacker to connect to the target and download or fabricate additional information. (Also known as C&C or C2.) |
| Actions on Objectives | The adversary uses the compromised system to achieve or progress towards goals, such as data exfiltration, DoS vandalism, or escalating access across the target network or other connected networks. |
This section helps you prepare for the following certification exam objectives:
| Exam | Objective |
|---|---|
| CompTIA CySA+ CS0-003 | 1.4 Compare and contrast threat-intelligence and threat-hunting concepts
3.1 Explain concepts related to attack methodology frameworks
|
2.6.1 Attack Frameworks
Click one of the buttons to take you to that part of the video.
Attack Frameworks 00:00-00:15 Attacks on system security usually follow one of several standard models. In this video, we'll review the kill chain process, the MITRE ATT&CK framework, and the Diamond model of intrusion analysis.
Kill Chain 00:15-00:31 The kill chain was derived from a process framework by Lockheed Martin. It includes seven phases: reconnaissance, weaponization, delivery, exploitation, installation, command and control, and finally, and actions on objectives.
Reconnaissance 00:31-00:46 During the reconnaissance phase, targets are researched, identified, and ultimately selected. The attacker identifies potential attack vectors and maps out the total attack surface using information gathered from open-source intelligence, social engineering, and network probes.
Weaponization and Delivery 00:46-01:07 Attackers need a way to weaponize their threat so they can remain undetected. During the weaponization phase, the malware code is encapsuled into commonly used and seemingly innocent file formats such as PDF files, image files, or Word documents. The weapon is then delivered via regularly used methods such as websites or email attachments.
Exploitation and Installation 01:07-01:24 During the exploitation phase, the weaponized file is executed on the target system. Then the weapon is installed to avoid attention and remain functional for as long as possible. The attacker also ensures ongoing access by installing a backdoor into the target system.
Command and Control 01:24-01:33 During the command and control phase, the attacker can communicate with the weapon. The attacker can command and control the weapon within the targeted system.
Actions on Objectives 01:33-01:47 During the actions on objectives phase, the attacker works to meet their objective. This could include intrusion, extraction of information, or destruction of data. The attacker may even be use the current system as a pathway to their final target.
The Mitre Att&ck Framework 01:47-02:17 While the kill chain process focuses on perimeter security, the MITRE Att&ck framework focuses on what happens within the network or the cloud. The MITRE corporation provides Adversarial Tactics, Techniques, and Common Knowledge matrices, or ATT&CK matrices. These matrices provide access to databases full of known tactics, techniques and procedures that are each tagged with an ID and categorized based on their persistence, lateral movement, initial access, and other factors.
The Diamond Model of Intrusion Analysis 02:17-03:21 The diamond model provides a framework for analyzing an intrusion. The model breaks up the features of the event into four categories – infrastructure, adversary, capability, and victim. Additional meta-features could include timestamps, methodologies, resources, directions, results, or phases.
Each of the four categories is represented by one corner of a diamond.
All parts of the diamond connect and can be reached from multiple directions, which provides some flexibility as you pivot between the corners. This helps to obtain a complete correlation of the various indicators related to the incident.
Let's say, for example, that you discover malware with malicious capabilities on one of your systems. While analyzing the malware code, you find the command and control domain name, which you can resolve to an IP address. Once you have an IP address, you could review your firewall logs to see if other systems had been contacted by the same command and control. Additionally, you could use the WHOIS command to determine the ownership information for the IP address.
Summary 03:21-03:36 That's it for this lesson. In this video, we discussed attack frameworks. We looked at the kill chain process, the MITRE ATT&CK framework, and the diamond model of intrusion analysis.
2.6.2 Exploring the Kill Chain
This lesson covers the following topics:
- Kill chain model
- Seven phases of an attack
Kill Chain Model
There are several models for describing the general process of an attack on system security. These steps are often referred to as a kill chain, following the influential white paper, Intelligence-Driven Computer Network Defense , commissioned by Lockheed Martin ( lockheedmartin.com/content/dam/lockheed-martin/rms/documents/cyber/LM-White-Paper-Intel-Driven-Defense.pdf ).
Kill chain analysis can identify a defensive course of action to counter the progression of an attack. Security teams must understand the kill chain stages in order to recognize how far suspicious activity has progressed. Additionally, the kill chain shapes analysis techniques as different approaches are suited to different stages. As an analyst, it is vital to identify suspicious activity as early in the kill chain as possible.
Seven Phases of an Attack
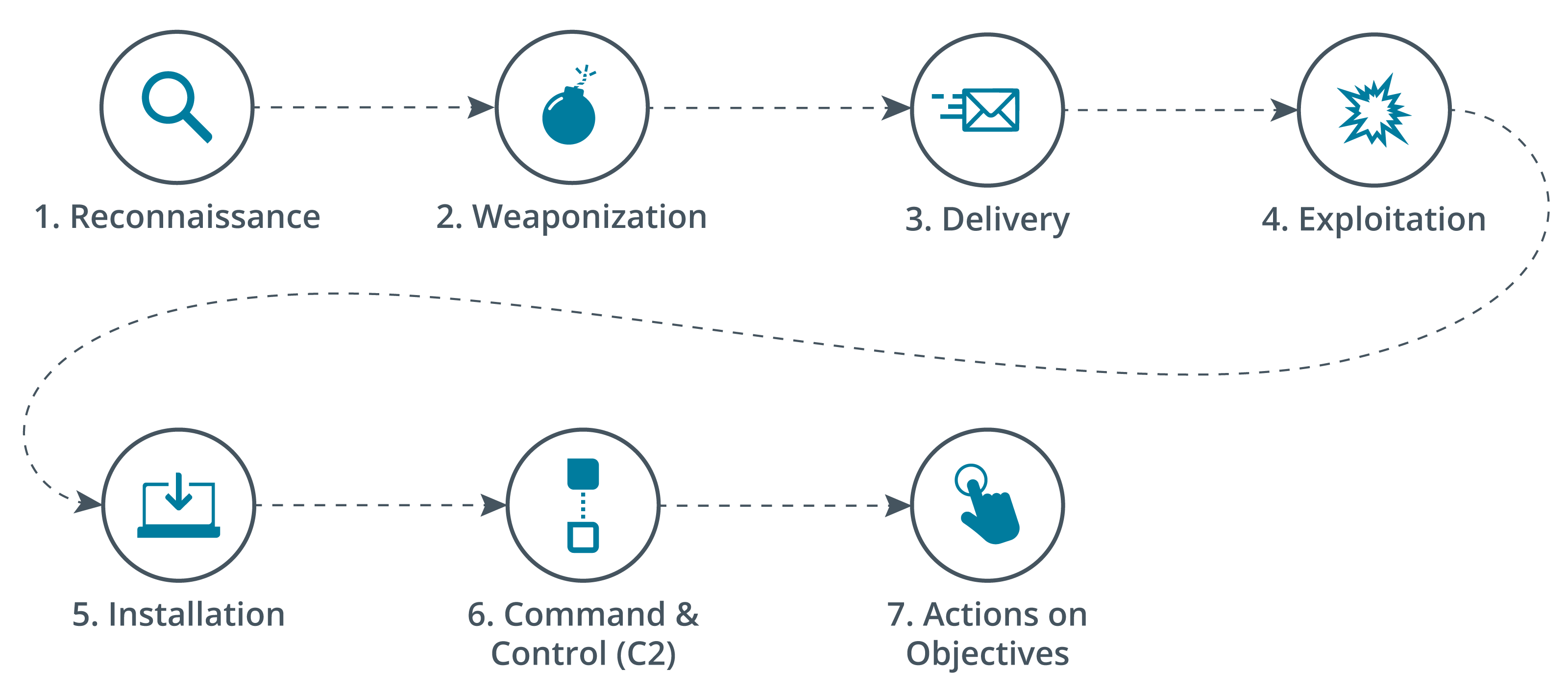
Details The stages of the kill chain with arrows indicating the order are as follows: Reconnaissance, Weaponization, Delivery, Exploitation, Installation, Command and Control (C2), and Actions on Objectives.
Stages in the kill chain.
The kill chain includes the seven phases of an attack as described in the following table:
| Stage | Description |
|---|---|
2.6.3 MITRE ATT&CK Framework
This lesson covers the following topics:
- Modified kill chain
- MITRE ATT&CK framework
- Developing a network threat model
Modified Kill Chain
As an early model, the kill chain has faced criticism for not accurately reflecting the chain of events in modern attack campaigns by focusing too much on perimeter security. Modified models, such as ones by AlienVault (now AT&T Cybersecurity) ( cybersecurity.att.com/blogs/security-essentials/the-internal-cyber-kill-chain-model ) and Sean Malone ( blackhat.com/docs/us-16/materials/us-16-Malone-Using-An-Expanded-Cyber-Kill-Chain-Model-To-Increase-Attack-Resiliency.pdf ), introduce iterative internal reconnaissance, lateral movement, privilege escalation, and data collection phases within Actions on Objectives. Once the attacker has achieved their initial objective without being detected, they may either maintain access or seek to remove any trace of their presence (anti-forensics).
The MITRE ATT&CK Framework
As an alternative to the lifecycle analysis described by a kill chain, the MITRE Corporation's Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK) matrices provide access to a database of known tactics, techniques, and procedures (TTPs). This freely available resource ( attack.mitre.org ) tags each technique with a unique ID and places it in one or more tactic categories, such as initial access, persistence, lateral movement, or command and control. The sequence in which attackers may deploy any tactic is not defined, so analysts must interpret each attack lifecycle from local evidence. The framework also allows analysts to compare the TTPs used by different threat groups.
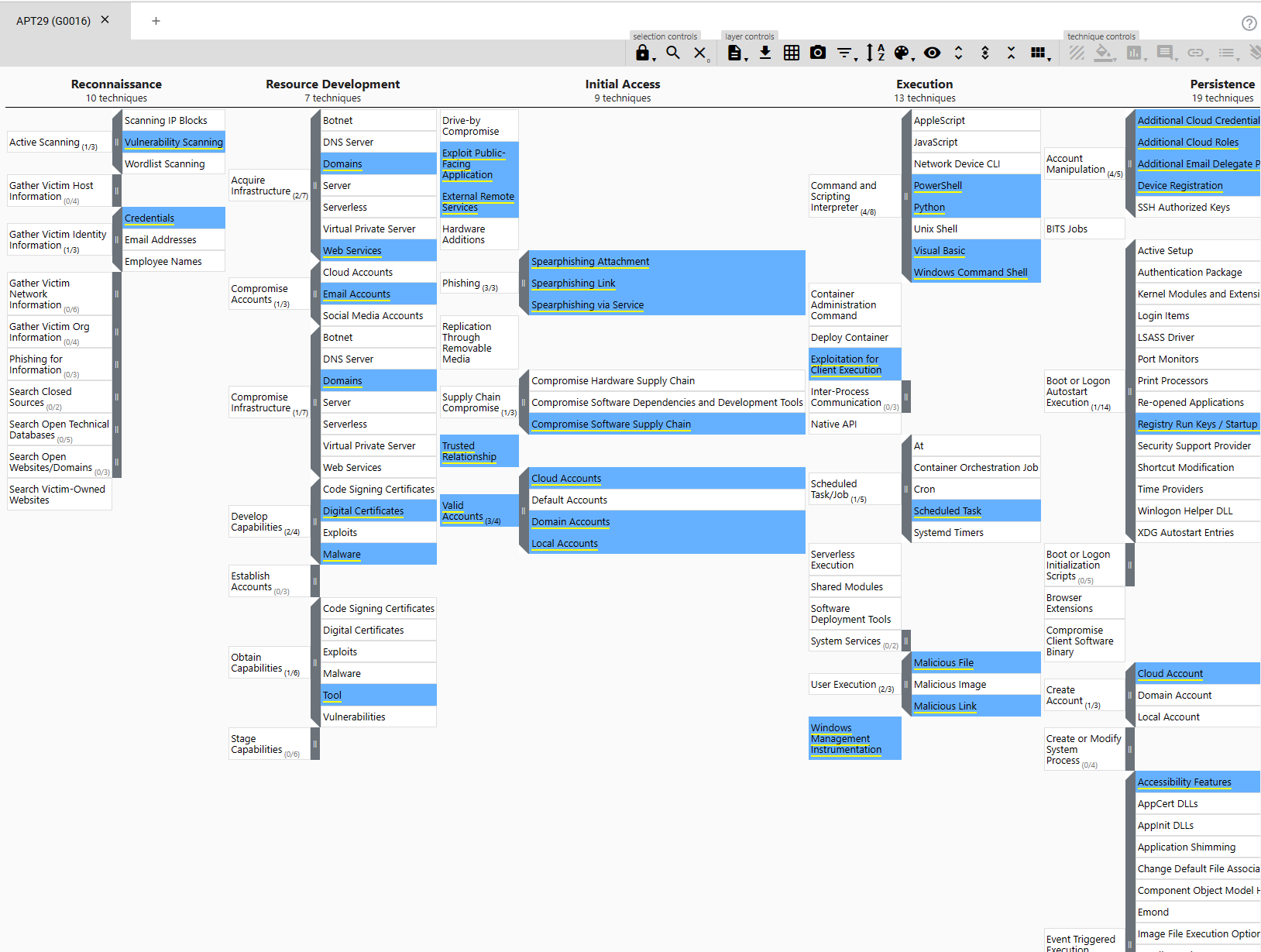
Detail
The table heads are as follows: reconnaissance (10 techniques), resource development (7 techniques), internal access (9 techniques), execution (13 techniques), and persistence (19 techniques).
This screenshot shows the MITRE ATT&CK navigator highlighting the TTPs of the threat group APT29 attributed to Russia's Foreign Intelligence Service. (Screenshot courtesy of MITRE ATT&CK.)
Developing a Network Threat Model
Threat actors represent a person, group, or organization responsible for malicious activities. They are often motivated by financial gain, political gain, or simply a desire to cause harm. This lesson reviews different threat actor types, their tactics, and methods to identify and defend against them. Organizations and individuals can be more aware and better prepared to fend off malicious attacks by exploring threat actor concepts.
Video
Click one of the buttons to take you to that part of the video.
Developing a Network Threat Model 00:00-01:00 Well when it comes to developing a network threat model, it's important to kind of wonder about the network, to think about it very carefully and also think about the applications as they use the network. I thought I'd start out with this little picture here, it's a picture I took of something in Scotland, it's a mountain in Scotland, called The Cobbler. It was named because it kind of looked like somebody, a cobbler, who makes shoes, kind of bending over and kind of doing their work and everything.
If you ask me, it kind of looks like one of the Nazgul in Lord of the Rings, doesn't it? Kind of semi on the horse, or something, see the little hood there. Or it looks like a hacker right, wearing a hoodie, right.
Or it looks like security analyst because that's what we are, we're security analysts. And our job, when it comes to network, modeling network threats and things like this, is to profile certain tactics, techniques and procedures. You'll see this constantly throughout the security analyst professional life, talking about TTPs.
Process 01:00-02:19 So basically, you basically start with the tactics, that's the bigger concept and then, which basically describes, you know, what the hackers are doing. The technique, some people will even use the word tools, but it's the techniques that hackers do to conduct attacks on a network or on an application or against an individual, for that matter.
And then the procedures, the actual ways that they go about doing it. And so you're going to kind of look for ways to recognize certain attacks and you're going to look to see how you can recognize things, for example, see too, for example, command and control traffic. How you can basically identify traffic, such as that, or indicators that compromise etc.
Now years ago they developed, MITRE developed something called the CVE database and the idea is that if an attack gets known, they publish it, they publish tons of information about it, about what the nature of the attack is, what, how to go about mitigating it, etc. And you can go there to cve.mitre.org to learn more. The higher the score, like, you know, nine point two, or something like that, that's a critical vulnerability. The lower the score, you know, two point O, it's something like, it's informational. Still important, but not quite as critical.
Considerations 02:19-03:45 But we kind of realized, as an industry, that it's not enough to just say, well here are these different kinds of attacks. So after a while we kind of started thinking about well, how can we model attacks against the network? How can we basically take an attack stage, whether that be according to the Diamond Model or the Lookheed Martin model or to MITRE, or to whatever model you can think of. I prefer creating a customized one, that's relevant for your organization. Cause each organization's different.
If you run a very small company of 15 people or even 115 people, you have different set of concerns than a company the size of Google, for heaven's sake. So you basically take a look at the attack stage, the malicious action and the killed steps, the steps you can take to mitigate a particular attack. So now you can start to model practically how things are working.
So you can actually use the MITRE ATT&CK framework, for example, and you can see where it lists the initial reconnaissance, that the hacker will do, the initial compromise, how the hacker establishes a foothold, escalates privileges, you get the idea. But what you can do is use the MITRE ATT&CK framework, either the Enterprise framework or the mobile framework. And you could basically come up with a profile of the different procedures.
This i-chart here is MITRE's framework and basically it lists most of the different known types of attacks. But what you can do, is you ca model certain types of attacks.
Attack Models 03:45-06:35 For example, MITRE and other organizations have put together actual models of different attackers, attack groups. There are attack groups that focus on attacking health care or the hospitality industry or they focus on attacking finance. And they're given names, names like APT 29 or fin6.
The reason why these have names and number is because these are basically attack groups, whether they're state sponsored attack groups from whatever evil country you can think of, or whether they're just groups of attackers that are in it for private gain, we know what their activities are like. We know what their profile is like.
In fact, I know a person who works for a major retailer in the UK. He feels that he has been able to identify a specific group by the nature of the applications that they're using. These are customized applications that bad guys are using to attack web applications. And the reason why this person I know, the reason why he thinks that, and he's right, that he can identify a specific attacker, is because they have certain little idiosyncrasies, little strange ways of creating their attack code.
And so they can say, well this person's using this particular strange little type of way of defining a variable, or creating an application. And they can track that in the network. So basically MITRE has said, well we have certain attack groups. In this case it's fin6.
And if you look at the red here in this graphic I'm showing you here, these are the different specific attacks that fin6 likes to conduct. Here's fin7, another attack group and the yellow shows how they like to attack systems. Well what you can do is that, if you feel you have an organization that is attacked by fin6 and fin7, you can actually compare the two.
So you could basically say, well looking here we could start with the red is fin6, the yellow is fin7 and the green are the common areas of attack. So now you're actually starting to model a specific attack, set of attacks.
Now you can say, well I need to set my controls, my security controls to take a look at PowerShell and schedule tasks and scripting and everything else in green. This way, instead of boiling the ocean with all sorts of different, you know, spraying different technologies to stop or detect the hacker, you are now going after specific activities.
And that's an important thing to think about and there are other ways that you can even get more specific to model a specific attack. And in a threat modeling, this is the Microsoft threat modeling tool, it's available free for download. What you can do is take a look at how data flows throughout an organization.
Internal and External Security 06:35-07:48 So you basically, in this case I have a Cloud, set of Cloud technologies, that I am using. I am tracking how that application information goes inside of my border boundary, my network and then goes outside in using the Cloud. The whole idea is that I can model how information flows in and out of my application, in and out of my network. The more I model this, the more I can start saying to myself, well let me show you something. In this case, there's an unencrypted data flow going on internally.
Now some people might say, well if it's internal, you're okay. Well that's not the case. Bad guys work inside your company, even people you might want to trust. The whole point here is that I'm identifying how information is flowing back and forth and, if I can identify a particular weakness by modeling it, as information flows in and out of my network, then I have the opportunity to apply controls or to basically change a process. In this case, let's think about encrypting this particular flow. That's how you go about modeling attacks and activities in your network.
2.6.4 Diamond Model of Intrusion Analysis
This lesson covers the following topics:
- The Diamond Model of intrusion analysis
- The four categories of the Diamond Model
- Analytic example of the Diamond Model
The Diamond Model of Intrusion Analysis
The Diamond Model of Intrusion Analysis is set out in a paper by Sergio Caltagirone, Andrew Pendergast, and Christopher Betz ( activeresponse.org/wp-content/uploads/2013/07/diamond.pdf ). The Diamond Model suggests a framework to analyze an intrusion event by exploring the relationships among four core features: adversary, capability, infrastructure, and victim. These four features are represented by the four vertices of a diamond shape. Meta-features may also describe each event, such as date/timestamps, methodologies, resources, direction, kill chain phase, result, etc. Each feature is also assigned a confidence level, indicating data accuracy or the reliability of a conclusion or assumption assigned to the value by analysis. The higher the value the higher the confidence.
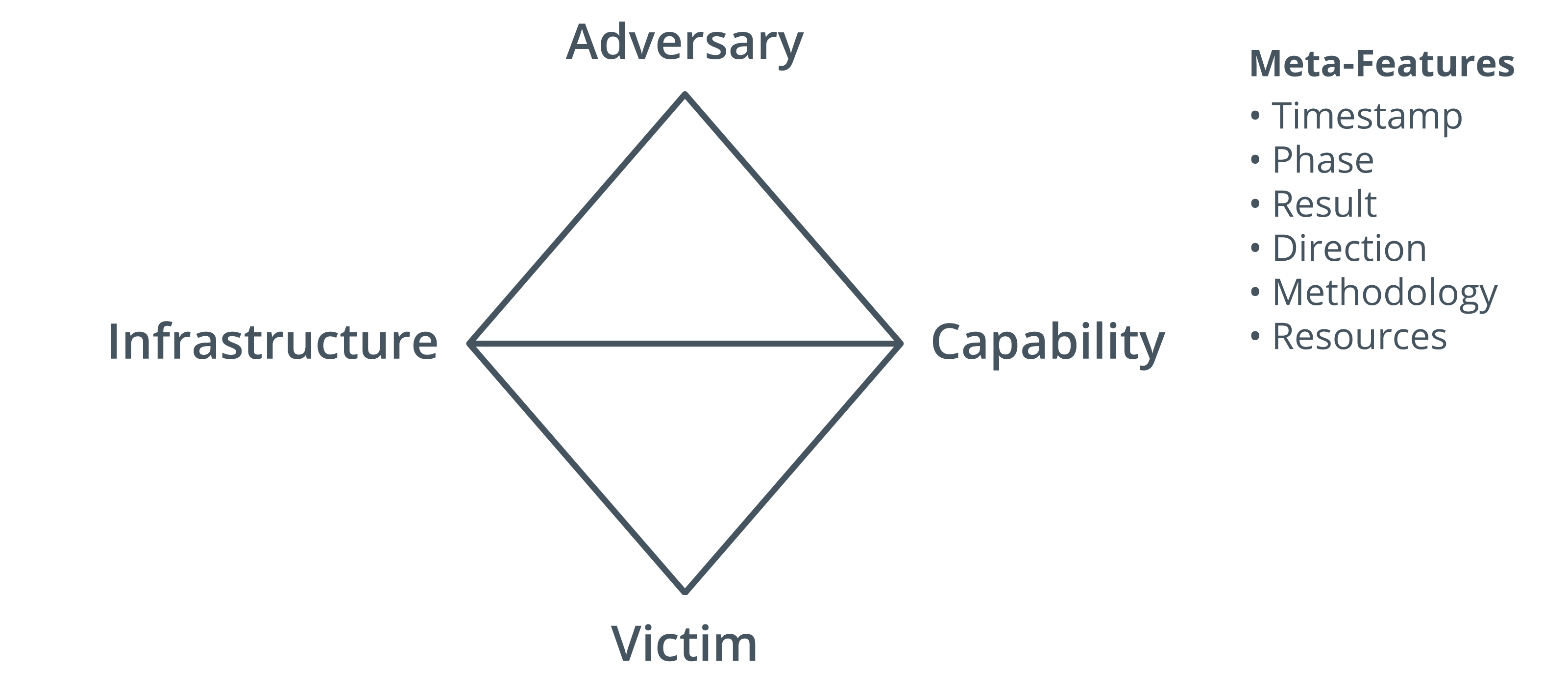
Intrusion event represented in the Diamond Model. (Image: Released to public domain by Sergio Caltagirone, Andrew Pendergast, and Christopher Betz [ activeresponse.org/wp-content/uploads/2013/07/diamond.pdf ].)
The Four Categories of the Diamond Model
The four core features of the Diamond Model are:
| Feature | Description |
|---|---|
Analytic Example of the Diamond Model
The power of the model lies in the ability to pivot along the vertices of the diamond to produce a complete analysis and correlation of the indicators of compromise (IoCs) that represent the event. The following is an example of pivoting:
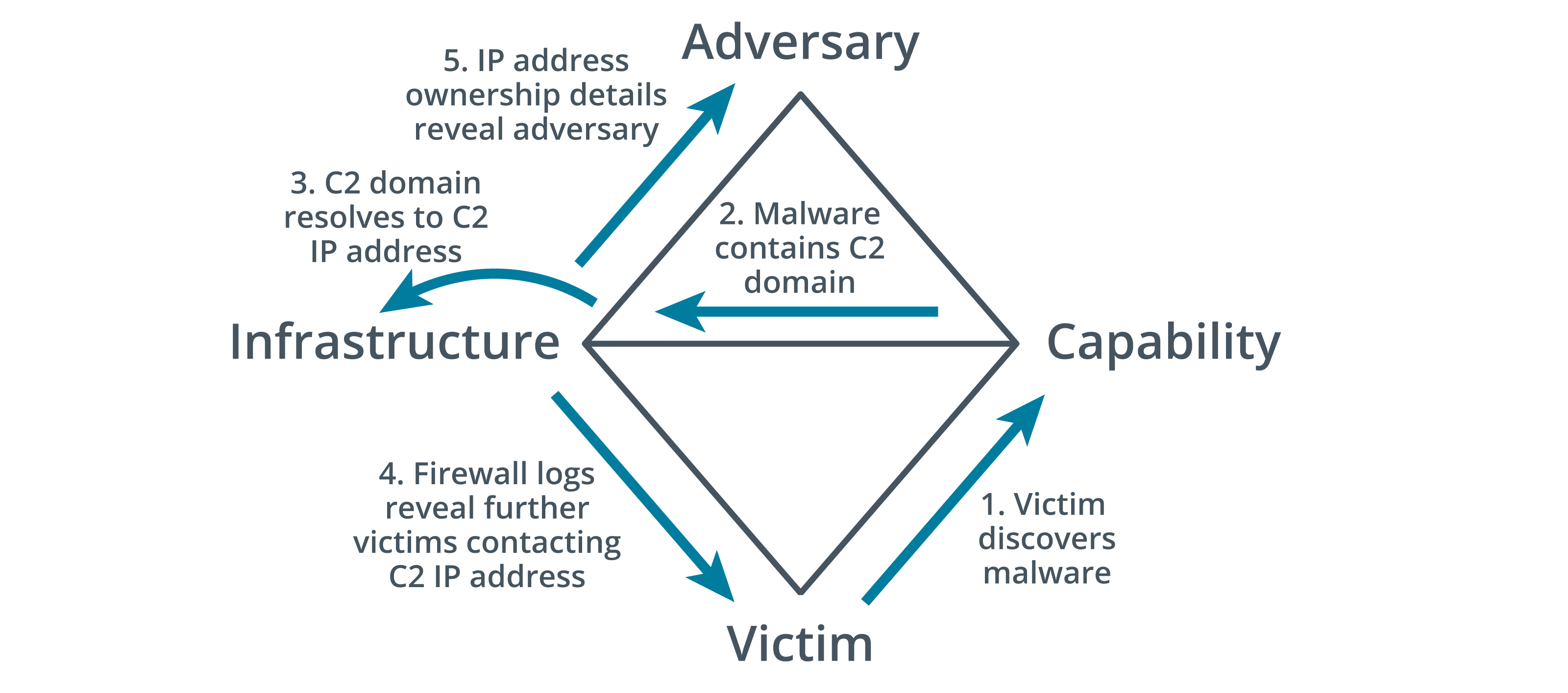
details
A arrow pointing from victim to capability reads, victim discovers malware. Another arrow pointing from capability to infrastructure reads, malware contains C 2 domain. A curved arrow on infrastructure reads, C 2 domain resolves to C 2 I P address. An arrow from infrastructure to victim reads, firewall logs reveal further victims contacting C 2 I P address. Another arrow pointing from infrastructure to adversary reads, I P address ownership details reveal adversary.
Diamond Model analytic pivoting example. (Image: Released to public domain by Sergio Caltagirone, Andrew Pendergast, and Christopher Betz [ activeresponse.org/wp-content/uploads/2013/07/diamond.pdf ].)
Events can be linked into attack graphs and activity threads, graphed along each vertex, representing the paths an adversary could take (if analyzing an attack in progress) and those that were taken (if analyzing past activity). Also, threads can be assigned to activity groups, which can be used to represent campaigns by particular adversaries.
While the Diamond Model is difficult to apply to manual "pen and paper" analysis, it has been used to develop automated threat intelligence analysis engines which are often integrated with various SIEM platforms.
2.6.5 Open-Source Security Testing Methodology Manual
This lesson covers the Open-Source Security Testing Methodology Manual.
Open-Source Security Testing Methodology Manual
The Open Source Security Testing Methodology Manual (OSSTMM) is a comprehensive guide to security testing. It provides a detailed set of procedures for managing operational security. The OSSTMM is provided by the Institute for Security and Open Methodologies (ISECOM), an open security resource organization ( isecom.org ).
The Open Source Security Testing Methodology Manual (OSSTMM) is a framework that provides a comprehensive and structured approach to security testing. The OSSTMM covers various aspects of security testing, including operational, physical, and wireless security testing. It provides a standardized methodology for conducting security tests and assessing the effectiveness of security controls.
The OSSTMM is relevant to security operations because it can help security analysts identify vulnerabilities and weaknesses in an organization's systems, software, and networks. Using the OSSTMM helps security analysts develop consistent and repeatable testing processes across all systems to ensure that security testing is conducted thoroughly and consistently. By providing a structured framework for security testing, the OSSTMM helps security analysts quickly identify areas of weakness that attackers commonly target.
The OSSTMM is licensed under Creative Commons and is freely available to everyone. The manual was created by Pete Herzog and is maintained by an international team of security professionals. The most recent edition of the Open-Source Security Testing Methodology Manual was released in December 2010. A PDF of the Open Source Security Testing Methodology Manual (OSSTMM) can be downloaded from isecom.org/OSSTMM.3.pdf .
The OSSTMM covers a wide range of topics related to security testing, including vulnerability assessment, network security, application security, and software security. The manual includes the following sections:
- Security Analysis
- Operational Security Metrics
- Trust Analysis
- Work Flow
- Human Security Testing
- Physical Security Testing
- Telecommunications Security Testing
- Data Networks Security Testing
- Compliance Regulations
- Reporting with the STAR (Security Test Audit Report)
