Cybersecurity System Audits
Chapter 2 – The Audit Process
Objectives
- Introduction
- Audit Description
- IS audit function management and its process
- Listing ISACA IS audit and assurance guidelines and standards
- Risks types and steps to analyze them
- Describe the internal controls
- Explanation of control assessments
- Demonstration of IS audit
- Explanation of IS audit process
- How to apply audit principles
Introduction
- This chapter focuses on how an audit should be conducted, emphasizing the process rather than regulations, laws, or technical details..
- It primarily covers the formal audit procedure, marking the start of Domain One, where the audit process truly begins.
- The audit follows a systematic, scientific approach, where auditors apply procedural and ethical frameworks to assess and evaluate the effectiveness of an organization.
- This process is guided by the ITAF (Information Technology Assurance Framework) and ISACA's Code of Ethics, both of which aim to enhance the audit profession and facilitates continuous improvement.
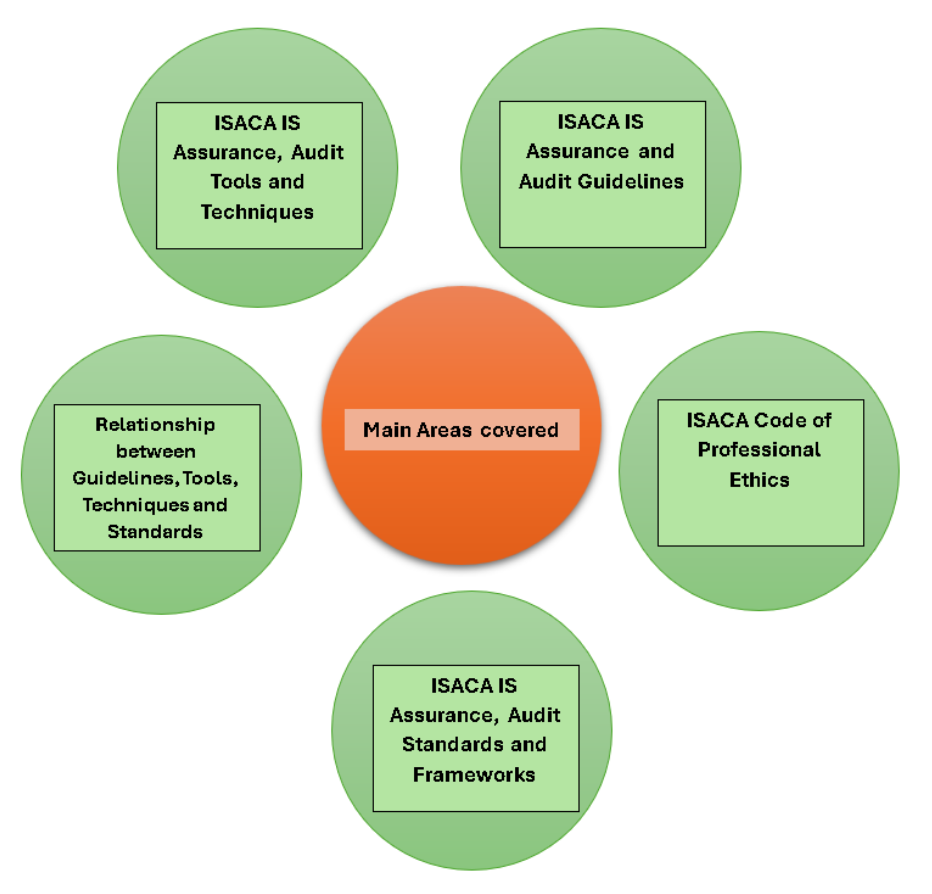
ISACA IS Audit Best Practice
- The creditability of an audit relies on the use of universally accepted standards.
- ISACA is a global leader in developing IS audit and assurance guidelines, tools, techniques, standards, and a professional code of ethics.
- These standards set the foundation for benchmarking IS audits.
ISACA Code of Professional Ethics
- Support the implementation of, and promote compliance with, relevant standards, procedures, and controls for information systems.
- Perform their duties with due diligence and professional care, following established standards and best practices.
- Serve stakeholders in a lawful and honest way, upholding high standards of conduct and character, and avoid any actions that could discredit the profession.
- Protect the privacy and confidentiality of information obtained during their duties, unless legally required to disclose it. Such information must not be used for personal gain or shared with unauthorized parties.
- Maintain their competence in their field and only take on tasks they are qualified to complete professionally.
- Communicate the results of their work to relevant parties, disclosing all significant facts.
- Support the professional education of stakeholders to enhance their understanding of information systems security and control.
IMPORTANT:
Non-compliance with the Code of Professional Ethics may lead to an investigation into the conduct of a member and/or certification holder, potentially resulting in disciplinary action.
ISACA IT Audit and Assurance Standards Framework Objective
The objectives of IS audit and assurance standards are to inform:
- IS auditors -> about the minimum level of performance needed to fulfill the professional responsibilities outlined in the code of ethics.
- The management -> about the profession’s requirements concerning the work conducted by audit practitioners.
- The CISA certification holders -> that failure to adhere to these standards will lead to a review of their conduct by the ISACA board of directors, potentially resulting in disciplinary action.
Standards, Guidelines and Practices
- ISACA IS Audit and Assurance Standards are considered mandatory requirements for IS auditing.
- Includes standards, guidelines, tools, and techniques for multiple levels of documentation.
- Based on ISACA Code of Professional Ethics
Audit Management Overview
- What is Audit Management?
- Audit management ensures that audits are conducted systematically and professionally.
- It includes setting up a structured audit function aligned with the organization’s mission and goals, ensuring audits are performed according to standard procedures, and maintaining auditor independence.
- Importance of Audit Management
- Proper audit management ensures consistency, efficiency, and transparency in evaluating organizational controls.
- It establishes a framework that supports risk management and compliance with regulatory requirements.
Key Components of Audit Management
- Audit Charter
- The audit charter is a formal document that defines the authority, scope, and responsibilities of the audit function.
- It outlines the auditor’s responsibilities and establishes the framework for conducting audits in alignment with organizational objectives.
- Audit Strategy
- An audit strategy provides a high-level plan to guide the audit function over time.
- It aligns the audit function with organizational risks and business objectives and serves as the blueprint for audit activities.
- Audit Program
- The audit program is a detailed plan for carrying out individual audits.
- It includes the scope, objectives, resources, and methodology for each audit, ensuring that audit activities are focused and consistent.
The Audit Charter
- Purpose of the Audit Charter
- The audit charter defines the scope and responsibilities of the audit team.
- It ensures that the audit function operates independently and provides sufficient authority to ensure that recommendations are implemented without giving auditors too much control.
- Roles and Responsibilities
- The charter outlines the roles of the audit team, emphasizing adherence to ISACA standards.
- It ensures auditors maintain ethical standards and independence, preventing conflicts of interest that could undermine audit integrity.
Introduction to the Audit Program
- Definition of an Audit Program
- An audit program is the plan that outlines how audits will be conducted within an organization.
- It covers scope, objectives, resources, and the procedures used to evaluate controls and form an audit opinion over a set period.
- The Role of an Audit Program
- The audit program helps standardize the audit process, ensuring that each audit follows a consistent methodology.
- It serves as a guide for auditors, ensuring that all necessary aspects of the audit are covered and adequately resourced.
Components of Audit Program
- Resources and Procedures
- Resources refer to the budget, staff, and tools available for the audit.
- Procedures outline the methodology auditors will use to evaluate controls, including steps such as sampling, testing, and documentation.
- Scope and Objectives
- The scope defines the specific areas, systems, or processes to be audited, while the objectives state the purpose of the audit.
- Both elements ensure the audit is focused and provides value by addressing key risks and controls.
Strategic Audit Planning
- What is Strategic Audit Planning?
- Strategic audit planning involves identifying future audit activities based on the organization’s goals, risks, and regulatory requirements.
- The plan includes estimating the resources necessary to perform these audits, including staffing, tools, and budget allocation.
- Why Strategic Planning is Important?
- Without strategic planning, audit activities may become reactive and disorganized.
- A well-structured audit plan ensures that audits are aligned with organizational goals and risks, providing timely insights into business processes and controls.
Factors Affecting an Audit
- Organizational Goals and Objectives
- Audits should be designed to assess the effectiveness of controls that support an organization’s goals and objectives.
- For example, an organization focused on rapid expansion may require audits that assess the scalability and security of its systems.
- New Initiatives and Mergers
- New organizational initiatives, mergers, or acquisitions can significantly impact audit planning.
- Auditors must ensure that controls for new systems and business processes are evaluated to maintain compliance and minimize risk.
External Factors Impacting Audits
- Market Conditions
- Changes in market conditions, such as heightened competition or the introduction of new regulations, can drive the need for audits.
- For instance, companies may voluntarily undergo audits to showcase the security and reliability of their products and services.
- Technology Advancements
- Technological advancements such as the adoption of cloud computing or artificial intelligence require auditors to reevaluate business and technical controls.
- Changes in technology can introduce new risks, requiring updates to audit procedures.
Regulatory and Compliance Changes
- Impact of New Regulations
- New regulations can require significant changes to an organization’s audit program.
- For example, the introduction of the General Data Protection Regulation (GDPR) forced organizations to reevaluate their data protection controls and undergo more rigorous audits.
- Examples of Regulatory Requirements
- Compliance with laws such as Sarbanes-Oxley (SOX) or the Health Insurance Portability and Accountability Act (HIPAA) requires regular internal and external audits to ensure that financial and personal data is adequately protected.
Resource Planning for Audits
- Annual Resource Review
- Organizations must conduct annual reviews of the resources required to support audit activities.
- This includes reviewing the availability of internal audit staff, tools, and budget to ensure that audit activities are properly resourced.
- Staffing and Budgeting
- Audit resource planning must account for both internal and external audit needs.
- In addition to ensuring that internal audits can be performed, the organization must budget for external audit costs and allocate staff to support external auditors.
The Role of Technology in Audits
- Keeping Up with Technological Changes
- Auditors need to stay updated on changes in technology that impact business processes and controls.
- As organizations adopt new technologies, such as cloud platforms or AI, auditors must learn how these technologies affect risk management and compliance.
- Tools for Audit Management
- Many organizations rely on software tools to manage audit activities, track audit progress, and store evidence.
- These tools help streamline the audit process, reduce errors, and ensure that audit data is easily accessible for internal reviews and regulatory requirements.
Continuous Education for Auditors
- Importance of Continuous Learning
- IS auditors are required to maintain their technical competence by completing continuing education.
- This ensures auditors stay up to date with changes in technology, business practices, and audit standards, enabling them to conduct accurate and effective audits.
- Certification Requirements
- ISACA requires CISA certification holders to complete at least 120 hours of continuing education every three years.
- This includes attending conferences, webinars, and other training events to maintain their certification and stay current with industry trends.
Audit Laws and Regulations
- Why Laws and Regulations are Important
- Laws and regulations drive the need for internal and external audits.
- Organizations must perform audits to ensure compliance with industry standards and government regulations, such as SOX, HIPAA, or PCI-DSS, to avoid penalties and legal consequences.
- Examples of Key Regulations
- Regulations such as GDPR, PCI-DSS, and SOX require organizations to maintain specific controls and undergo regular audits to verify compliance.
- Non-compliance can result in financial penalties, lawsuits, and damage to the organization’s reputation.
ISACA Auditing Standards Overview
- Introduction to ITAF
- ISACA’s IT Assurance Framework (ITAF) is a professional practice framework for IS audit/assurance, consisting of the ISACA Code of Professional Ethics, IS audit and assurance standards, guidelines, and tools.
- These components help structure an effective audit process that complies with standards and ethical behavior.
- Availability of ITAF
- ITAF is currently in its third edition and is available for free at www.isaca.org/ITAF.
- CISA candidates should be familiar with ITAF's importance, even though memorization is not required for the exam.
ISACA Code of Professional Ethics
- Purpose of the Code
- The ISACA Code of Professional Ethics defines principles of professional behavior, including compliance with laws and standards, and upholding truth. Professionals earning CISA certification must sign a declaration supporting these ethical standards.
- Disciplinary Actions
- Violation of the ISACA Code may lead to disciplinary actions or loss of certification. CISA candidates must understand and be familiar with the code, though memorization is not required.
ISACA Audit and Assurance Standards
- ISACA’s standards provide a framework for minimum performance related to security, audit activities, and post-audit actions.
- These standards are essential for guiding IS auditors in their day-to-day work.
- The full text of the standards is available at www.isaca.org/standards.
- Understanding their importance is key for CISA candidates.
- Audit Charter (Standard 1001)
- Formal Definition of Audit Activities The audit charter formally defines the scope, authority, and responsibility for audits in an organization. Senior management must support the charter to ensure audits are conducted appropriately.
- Significance of the Audit Charter It sets the foundation for the audit program, ensuring that auditors have clear guidelines and boundaries within which to operate.
- Professional Independence (Standard 1003)
- Behavioral Independence The IS auditor should maintain professional independence from the auditee, ensuring no conflicts of interest affect the audit’s outcome.
- Avoiding Conflicts Even the appearance of impropriety should be avoided. IS auditors must be vigilant about maintaining ethical standards in all their activities.
- Due Professional Care (Standard 1005)
- Exercise of Professional Care IS auditors must follow all applicable audit standards and exercise due professional care. This includes conducting audits meticulously and adhering to industry best practices.
- Conformance to Standards Auditors must ensure their work meets ISACA standards, avoiding negligence or oversight during the audit process.
- Proficiency (Standard 1006)
- Required Skills and Knowledge IS auditors must possess the necessary skills and knowledge to perform IS audits effectively. Continuing education and professional development are key to maintaining proficiency.
- Continuous Learning Auditors are required to undergo regular training to keep up with technological and regulatory changes that affect audit practices.
- Audit Criteria (Standard 1008)
- Objective and Measurable Criteria IS auditors must select criteria that are objective, measurable, and reasonable for evaluating the effectiveness of controls. This ensures that the audit’s findings are based on sound evidence.
- Use of Criteria Appropriate audit criteria guide the auditor’s judgment and help provide clarity in audit reports.
- Risk Assessment in Audit Planning (Standard 1202)
- Risk-Based Audit Approach
IS auditors should use a risk-based approach when determining which controls and activities should be audited. This ensures that higher-risk areas receive more attention during the audit. - Business and Operational Risks
Risk assessment includes evaluating security risks as well as broader business and operational risks. Decisions should be thoroughly documented to maintain transparency.
- Risk-Based Audit Approach
- Audit Supervision and Performance (Standard 1203)
- Supervising Audit Work IS auditors are responsible for overseeing audit work, ensuring it is conducted according to the plan and schedule. Audit staff must be competent, and evidence must be gathered systematically.
- Documentation and Findings Audit findings must be documented, and conclusions should be based on collected evidence, ensuring the integrity of the audit process.
- Audit Reporting (Standard 1401)
- Developing the Audit Report IS auditors must create a comprehensive audit report documenting the audit process, findings, conclusions, and recommendations. The report must follow an established format, including the scope, coverage period, and recipient organization.
- Sufficiency of Evidence The audit report should contain sufficient evidence to support the auditor’s findings and conclusions.
- Follow-Up Activities (Standard 1402)
- Ensuring Corrective Action IS auditors should follow up on audit findings to ensure management has taken the recommended corrective actions. This step is essential to ensure that issues identified during the audit are addressed effectively.
- Timing and Scheduling Follow-up activities should be scheduled at an appropriate time, based on the nature and severity of the audit findings.
- Evidence (Standard 1205) - Gathering Audit Evidence IS auditors must collect sufficient and appropriate evidence to draw reasonable conclusions about the effectiveness of controls and procedures. Evidence may include documentation, records, audit logs, and the results of testing procedures. - Evaluating Evidence Auditors should assess the sufficiency and integrity of the evidence gathered. This evaluation ensures that audit findings and conclusions are based on solid, verifiable information.
- Using the Work of Other Experts (Standard 1206)
- Evaluating the Work of Other Experts IS auditors may need to rely on the work of other auditors or experts. Before doing so, they must assess the qualifications and independence of the external auditors, as well as the relevance and adequacy of their work.
- Supplemental Testing If necessary, IS auditors should conduct additional testing to validate the work of other experts, ensuring that all audit findings are accurate and reliable.
- Audit Sampling (Standard 2208)
- Selecting Audit Samples Audit sampling helps auditors evaluate large sets of data without reviewing every item. The sample should be representative of the overall data set to ensure the audit findings are accurate and valid.
- Evaluating Sample Results Once the sample is selected and tested, auditors must evaluate the results to determine if the controls being tested are effective. If issues are found in the sample, they may indicate broader problems that need further investigation.
ISACA Audit Guidelines
- Purpose of ISACA Guidelines
- ISACA’s audit guidelines clarify how to apply audit standards.
- These guidelines provide auditors with specific examples and recommendations for carrying out audits according to best practices.
- Guideline Components
- The guidelines cover a wide range of topics, such as how to assess independence, how to handle irregularities, and how to structure audit reports.
- Understanding these guidelines helps auditors perform audits more effectively.
ISACA Audit Guidelines
Some of the important guidelines are:
- Organizational Independence (Guideline 2002)
- Professional Independence (Guideline 2003)
- Audit Evidence (Guideline 2205)
- Follow-Up Activities (Guideline 2402)
- Audit Reporting (Guideline 2401)
Relationship Between Standards and Guidelines
- Standards
- ISACA audit standards serve as fundamental rules that all IS auditors must follow.
- They are regarded as mandatory principles, much like a legal framework for auditors to ensure professional and ethical audit activities.
- Guidelines
- ISACA guidelines complement the standards by offering further explanations and assistance on how the standards can be implemented in real-world audit scenarios.
- They serve as practical advice for auditors to achieve compliance with standards.
ISACA Risk IT Framework
- Overview of the Framework The ISACA Risk IT Framework provides a structured approach to managing IT-related risks within the broader enterprise risk management program. It offers guidance on integrating IT risk into overall business risk considerations.
- Key Components The framework consists of three primary components:
- Risk governance,
- Risk evaluation,
- Risk response.
- Together, these elements help organizations identify, assess, and address IT risks in a structured and business-focused manner.
Risk Governance, Evaluation and Response
- Risk Governance Risk governance ensures that IT risk management is aligned with the organization’s overall risk management efforts. It integrates IT risks into enterprise risk management, ensuring that decision-makers are aware of the potential IT risks and their impact on business objectives.
- Risk Evaluation Risk evaluation involves assessing the potential impact of risks on business processes and assets. This process helps organizations determine which risks need to be addressed and prioritize them accordingly.
- Risk Response The Risk IT Framework also provides a structured process for responding to identified risks. This includes risk treatment through mitigation strategies, such as implementing controls or transferring risk through insurance.
Risk Mitigation and Countermeasures
- Once risks are identified, auditors must recommend or evaluate the implementation of mitigating controls.
- These countermeasures reduce the probability or impact of risks, helping organizations protect their assets and operations.
- During audits, IS auditors may apply additional scrutiny to high-risk areas by increasing sampling rates, conducting more interviews, or performing additional tests to ensure controls are effective.
- After implementing countermeasures, auditors should reassess controls to ensure they are effective.
- This involves continuous monitoring of the control environment and re-testing where necessary to confirm improvements.
- Some controls may include self-monitoring mechanisms. Auditors should review the records of these self-monitoring systems to assess their impact on risk mitigation.
Types of Controls in Risk Management
- Physical, Technical, and Administrative Controls Controls are classified into three types:
- Physical (e.G., Locks, cameras),
- Technical (e.G., Encryption, firewalls), and
- Administrative (e.G., Policies, procedures).
These controls work together to reduce risks and ensure business objectives are met.
Classes of Controls in Risk Management
- Preventive, Detective, and Deterrent Controls Controls can be classified by function:
- Preventive controls stop unwanted events,
- Detective controls record events,
- Deterrent controls discourage undesirable actions.
Auditors must evaluate these classes to ensure that risks are effectively managed.
- Corrective, Compensating, and Recovery Controls
- Corrective controls address problems after they occur
- Compensating controls fill in gaps where direct controls cannot be implemented,
- Recovery controls restore systems to normal operations after an incident.
