Section 7.5 Social Engineering
As you study this section, answer the following questions:
- What is social engineering?
- What are the three phases in the social engineering process?
- What is the difference between a spam and a spim attack?
- What is an opportunistic attack?
- Why would an attacker use URL obfuscation?
- What are the different types of phishing attacks?
In this section, you will learn to:
- Identify social engineering
The key terms for this section include:
Key Terms and Definitions
| Term | Definition |
|---|---|
| Social engineering | Entices or manipulates people to perform tasks or relay information that benefits an attacker. Social engineering tries to get a person to do something they would not do under normal circumstances. |
| Elicitation | A technique that tries to extract information from a target without arousing suspicion. |
| Scanning | A technique that social engineers often use to gather information when trying to penetrate a network system remotely. |
| Pretexting | Researching and gathering information to create convincing identities, stories, and scenarios to be used on selected targets. |
| Preloading | Sets up a target by influencing the target's thoughts, opinions, and emotions. |
| Impersonation | Pretending to be trustworthy and having a legitimate reason for approaching the target to ask for sensitive information or access to protected systems. |
| Spam | Social engineering attack in which the attacker sends an email or banner ad embedded with a compromised URL that entices a user to click it. |
| Spim | Similar to a spam attack, except the malicious link is sent to the target using instant messaging instead of email. |
| Obfuscation | Techniques used to mask something important, like a URL. |
| Phishing | Social engineering attack in which the attacker masquerades as a trustworthy entity and leverages emails with malicious hyperlinks or malware-infected attachments. |
| Pharming | Social engineering attack in which the attacker executes malicious programs on the target’s computer so that any URL traffic redirects to the attacker’s malicious website. |
This section helps you prepare for the following certification exam objectives:
| Exam | Objective |
|---|---|
| CompTIA CySA+ CS0-003 | 1.2 Given a scenario, analyze indicators of potentially malicious activity
2.2 Given a scenario, analyze output from vulnerability assessment tools
|
| TestOut CyberDefense Pro | 4.1 Manage security incidents
|
7.5.1 Social Engineering Overview
Click one of the buttons to take you to that part of the video.
Social Engineering Overview 00:00-00:42 A social engineering attack involves human interaction. The attacker tries to trick their victim, convince them to do things, or make them give out information they wouldn't under normal circumstances.
Because this attack involves humans, it's very hard to protect your data and assets against social engineering. It's also much harder to track and catch it before any damage is done. The best way to minimize social engineer's impact is to educate employees, managers, administrators, custodial staff, clients, users, consumers—essentially, the entire planet should learn to recognize and respond appropriately to social engineering attacks.
Manipulation and Motivation 00:42-01:46 Social engineers are master manipulators. They're very good at discerning signs and behaviors worth exploiting for information. Some of the tactics that exploit human weakness include moral obligation, innate human trust, threatening, asking for very little, and using ignorance.
If the attacker exploits the victim's willingness to be helpful and assist them out of a sense of responsibility, that's leveraging moral obligation.
If the attacker exploits the victim's natural tendency to trust others, they're taking advantage of innate human trust. The attacker wears certain clothes, creates a certain demeanor, and speaks words and terms the victim is familiar with so they'll trust the attacker and give them what they want.
A threat is when the attacker intimidates the victim by promising negative consequences if they don't comply with the attacker's request.
And attackers will often promise some reward in return for very little to nothing, asking the victim to do a small favor or share a bit of information in return for a huge payoff.
Ignorance means the victim isn't educated in social engineering tactics and prevention, so they can't recognize an attack even when it's happening to them.
Social Engineering Process 01:46-01:56 Now let's talk about the steps involved in a social engineering attack. These steps can be divided into three main parts: research, development, and exploitation.
Research Phase 01:56-02:18 The research phase is when the attacker starts gathering information about the company or organization they'll attack. Attackers use a process called footprinting to do this.
This is when the attacker goes through the target company's official websites and social media, performs dumpster diving, searches for employees' names, email addresses, and IDs, goes on a company tour, and conducts other types of on-site observation.
Development Phase 02:18-02:56 Then he'll move on to the development phase, which has two parts: selecting individual targets within the company being attacked and forming a relationship with the targets.
Usually, attackers choose people who not only have access to the information or object they desire, but show signs of being frustrated, over-confident, or arrogant, or having other traits that make it easy to extract information from them.
Once he's selected his targets, the attacker will start forming a relationship with them through conversations, emails, shared interests, and so on. This builds the victims' trust in the attacker, allowing them to be comfortable and relaxed so that they'll be even more willing to help.
Exploitation Phase 02:56-04:10 The exploitation phase is when the attacker takes advantage of the relationship with the victim and uses the victim to extract information, obtain access, or accomplish the attacker's purposes in some way. Some examples include disclosing a password and username over the phone; introducing the attacker to other company personnel, providing social proof for the attacker; inserting a USB flash drive with a malicious payload onto a company computer; opening an infected email attachment; exposing trade secrets in a discussion with a supposed peer; and pretexting.
Pretexting is using a fictitious scenario to persuade someone to perform an action or give out information they're not authorized to share. Pretexting usually requires the attacker to perform research to create a believable scenario. So, the more the attacker knows about the organization and the victim, the more believable the attacker's fictitious scenario will be.
If the exploitation is successful, the only thing left to do is wrap things up without raising suspicion. Most attackers tie up loose ends, like erasing digital footprints and ensuring no items or information get left behind. A well-planned and smooth exit strategy is the attacker's goal and their final act in the exploitation phase.
Summary 04:10-04:47 Social engineering is such a prevalent threat because it involves humans. So, let's review the key things to remember about social engineers: skilled attackers will know which human weaknesses to exploit based on people's feelings, emotions, and personalities. They're also detail-oriented, patient observers. They're skilled manipulators and good at forming relationships. The best ones will even clean up their tracks to make sure they won't get caught even if the victim realizes what's happened some time later. And the best defense against social engineers is user education.
7.5.2 Social Engineering Overview Facts
Social engineering refers to enticing or manipulating people to perform tasks or relay information that benefits an attacker. Social engineering tries to get a person to do something they would not do under normal circumstances. Security analysts need to be aware of these threats and also educate all employees and users so they will be less likely to fall for any social engineering traps.
This lesson covers the following topics:
- Manipulation tactics
- Social engineering process
- Simulating social engineering attacks
Manipulation Tactics
Social engineers are master manipulators. The following table describes some of the most popular tactics they use on targets.
| Manipulation Type | Description |
|---|---|
| Moral obligation | An attacker uses moral obligation to exploit the target’s willingness to be helpful and assist them out of a sense of responsibility. |
| Innate human trust | Attackers often exploit a target’s natural tendency to trust others. The attacker wears the right clothes, has the right demeanor, and speaks words and terms the target is familiar with so that the target complies with requests out of trust. |
| Threats | An attacker may threaten or intimidate a target, being convincing enough to make them comply with the attacker’s request. |
| Ignorance | Ignorance means the target is not educated in social engineering tactics and prevention; thus, they cannot recognize social engineering when it happens. The attacker knows this and exploits the ignorance to their advantage. |
Social Engineering Process
| Phase | Description |
|---|---|
| Research | In the research phase, the attacker gathers information about the target organization. Attackers use a process called footprinting, which uses all resources available to gain information. This includes going through the target organization’s official websites and social media, performing dumpster diving, searching sources for employees’ names, email addresses, and IDs, and going through an organizational tour or other kind of onsite observation. Research may provide information for pretexting. Pretexting uses a fictitious scenario to persuade someone to perform an unauthorized action, such as providing server names and login information. Pretexting usually requires the attacker to perform research to create a believable scenario. The more the attacker knows about the organization and the target, the more believable a scenario the attacker can come up with. |
| Development | The development phase involves two parts: selecting individual targets within the organization being attacked and forming a relationship with the selected targets. Usually, attackers select people who not only have access to the information or object they desire but also show signs of being frustrated, overconfident, arrogant, or somehow easy to extract information from. Once the targets are selected, the attacker starts forming a relationship with them through conversations, emails, shared interests, etc. The relationship helps build the targets’ trust in the attacker, allowing the targets to be comfortable, relaxed, and more willing to help. |
| Exploitation | In the exploitation phase, the attacker takes advantage of the relationship with the target and uses the target to extract information, obtain access, or accomplish the attacker’s purposes in some way. Some examples include disclosing passwords and usernames, introducing the attacker to other personnel, providing social credibility for the attacker, inserting a USB flash drive with a malicious payload into an organization's computer, opening an infected email attachment, or exposing trade secrets in a discussion. If the exploitation is successful, the only thing left to do is to wrap things up without raising suspicion. Most attackers tie up loose ends, such as erasing digital footprints and ensuring no items or information are left behind for the target to determine whether an attack has occurred or identify the attacker. A well-planned and smooth exit strategy is the attacker's goal and final act in the exploitation phase. |
Simulating Social Engineering Attacks
To measure social engineering vulnerabilities, security analysts can play the role of the attacker by using various tools designed to help in this endeavor. Baiting and phishing attack simulations are very common and follow the same approach as an actual attack.
Several commercial tools are available to help organizations create and track various "campaigns." A campaign is designed to focus on one specific metric and runs during a defined time frame. Most commercial tools are cloud-based and offer sophisticated tracking and reporting capabilities. Social engineering assessment can also use open-source tools. Two popular tools are the S ocial-Engineer Toolkit ( SET ) https://github.com/trustedsec/social-engineer-toolkit and Gophish https://getgophish.com/ . The Social-Engineer Toolkit offers many capabilities, such as creating a legitimate-looking web page or creating malicious attachments. In contrast, Gophish focuses more on providing a user-friendly graphical interface and tools for managing campaigns.
7.5.3 Social Engineering Motivation Facts
There are many different types of social engineering attacks and motivation techniques. A security analyst should be familiar with these.
This lesson covers the following topics:
- Social engineering attacks
- Motivation techniques
Social Engineering Attacks
The following table describes a few social engineering attacks.
| Attack | Description |
|---|---|
| Shoulder surfing | Shoulder surfing involves looking over someone's shoulder while they work on a computer or review documents. This attack's purpose is to obtain usernames, passwords, account numbers, or other sensitive information. |
| Eavesdropping | Eavesdropping is an unauthorized person listening to private conversations between employees or other authorized personnel when sensitive topics are being discussed. |
| USB and keyloggers | When on-site, a social engineer can also steal data through a USB flash drive or a keystroke logger. Social engineers often employ keystroke loggers to capture usernames and passwords. As the target logs in, the username and password are saved. Later, the attacker uses the username and password to conduct an exploit. |
| Spam and spim | When using spam, the attacker sends an email or banner ad embedded with a compromised URL that entices a user to click it. Spim is similar, but the malicious link is sent to the target using instant messaging instead of email. |
| Hoax | Email hoaxes are often easy to spot because of their bad spelling and terrible grammar. However, hoax emails use a variety of tactics to convince the target they are real. |
Motivation Techniques
The following table describes different types of attackers.
| Motivation Technique | Description |
|---|---|
| Authority and fear | Authority techniques rely on power to get a target to comply without questioning the attacker. The attacker pretends to be a superior with enough power that the target complies right away without question. The attacker could also pretend to be there in the name of or upon the request of a superior. Authority is often combined with fear. If an authority figure threatens a target with being fired or demoted, the target is more likely to comply without a second thought. |
| Social proof | Social proof means the attacker uses social pressure to convince the target that it is okay to share or do something. In this case, the attacker might say, "If everybody is doing it, it is okay for you to do it, too." |
| Scarcity | Scarcity appeals to the target's greed. If something is in short supply and unavailable, the target is more likely to fall for it. |
| Likeability | Likeability works well because humans tend to do more to please a person they like than someone they do not like. |
| Urgency | To create a sense of urgency, an attacker fabricates a scenario of distress to convince an individual that action is immediately necessary. |
| Common ground and interest | Common ground and shared interest work because sharing a hobby, life experience, or problem instantly builds a connection and establishes trust between two parties. |
7.5.4 Social Engineering Techniques
Click one of the buttons to take you to that part of the video.
Social Engineering Techniques 00:00-00:38 In the development phase of a social engineering attack, targets are selected and then exploited to obtain information or access. But, of course, it's not really that simple because not all attackers are the same. They all have different motives, attributes, and attack characteristics, and they employ different techniques to get what they want from their targets.
For example, a single hacker trying to exploit a vulnerability is going to have a completely different attack profile than an organized crime group waging an assault on your network. It's your job to understand the different types of threats and attackers that exist so you can protect your systems.
Opportunistic Attack 00:38-01:35 The first thing you need to be aware of is the difference between an opportunistic attack and a targeted attack. Let's start by looking at the less dangerous of the two, an opportunistic attack.
With an opportunistic attack, the attacker is almost always trying to make money as fast as possible with minimal effort. And because hiding your tracks and presence is very time-consuming, this type of attacker usually won't bother. They simply want to get in, grab the goods, and get out—think of it as the smash-and-grab of cyberattacks.
An opportunistic attack is typically automated and involves scanning a wide range of systems for known vulnerabilities, such as old software, exposed ports, poorly secured networks, and default configurations. When the scan finds a weakness, the attacker exploits the vulnerability, steals what they want, and gets out.
A common example of an opportunistic attack is ransomware. An attacker will gain access to a system, plant a virus that encrypts all user data, and demand payment for decrypting the data.
Targeted Attack 01:35-02:11 A targeted attack, on the other hand, is much more dangerous. A targeted attack is extremely methodical and often carried out by multiple entities that have substantial resources.
This attack's main goal is to do damage—for example, leak sensitive information or destroy important data. Targeted attacks almost always use unknown exploits and go to great lengths to cover their tracks and hide their presence. They also use completely new programs written from the ground up that are specifically designed for the target.
In the case of social engineering, a targeted attack often involves elicitation.
Elicitation 02:11-02:25 Elicitation is a technique used to extract information from a target without arousing suspicion. Attackers use different tactics to make the target comfortable or willing to share information. Let's talk about a few of the techniques attackers use on their victims.
Compliments 02:25-03:11 Sweet-talking and complimenting may seem cliche, but they work really well if they're done right. Most human beings are proud of their accomplishments and love to be acknowledged. An attacker might pay the target a compliment on their work in hopes that the target will take the bait and elaborate on the subject. Even if the target downplays their skill or ability, talking about the project might give the attacker valuable information.
For example, let's say a business hires an attacker to spy on their competition's project plans. The attacker might either try to get a job inside the target company or befriend an employee who has access to the plans.
Whichever way the attacker goes about it, the goal is to get close to someone involved in the project—a peer or a superior—and compliment them on their contributions to entice them to elaborate on the project's details.
Misinformation 03:11-03:56 Attackers might also engage a target by making a false statement on purpose. The attacker's hope, in this case, is that the target will correct them and give out the accurate details. The more precise the details the attacker gives, the better the chance that the target will take the bait and correct him.
For example, let's say an attacker wants to confirm how many security points a building has implemented. The attacker might befriend a security guard and, at some point, make a statement such as, "Wow, I hear this building is a fort. It's impossible to get in. They have ten security cameras, six guards, and a fingerprint scanner. And that's just in the lobby!" By giving specific numbers and greatly exaggerating them, the attacker prompts the victim to correct him and state the accurate number of cameras and guards.
Feign Ignorance 03:56-04:39 Feigning ignorance is another elicitation technique that's really useful. It's similar to what we just discussed about making a wrong statement. But instead of giving lots of exaggerated and specific details, this technique involves making a wrong statement and then admitting to not knowing much about the subject.
For example, an attacker could approach a victim and say, "I don't know much about business, but I've heard ABC company's product is way ahead of the product from XYZ company." If the attacker knows the victim has some connection to the XYZ company, this statement will hopefully make the victim to not only correct the attacker, but also explain why the attacker is wrong in more detail. The explanation might help the attacker learn more, or at least have a chance to ask more questions without raising suspicion.
Be a Good Listener 04:39-05:10 The last technique I'll mention is being a good listener. This may seem very basic, but it's incredibly effective. People are willing to share more when they feel safe, cared for, and connected to the listener. An attacker may approach a victim and carefully listen to what they have to say, validate their feelings, and even share similar experiences, real or fabricated. The point is to be relatable and sympathetic. As the victim feels more connected to the attacker, their barriers go down and trust builds, leading the victim to share more information than they would have otherwise.
Pretexting, Preloading, and Impersonation 05:10-06:25 All the techniques mentioned so far involve some pretexting, preloading, and impersonation.
Pretexting is using a fictitious scenario to persuade someone to perform an action or share information they're not authorized to give out.
Pretexting is doing research and information-gathering to create convincing identities, stories, and scenarios tailored to specific targets. Preloading is influencing the target's thoughts, opinions, and emotions before something happens.
And impersonation is pretending to be trustworthy and approaching the target to ask them for sensitive information or convince them to grant access to protected systems.
For example, let's say an attacker comes into a building dressed in a technician's uniform. He has a badge, and he's carrying tools. He tells the front desk who called him and what he's there to fix. This attacker is simultaneously impersonating a legitimate technician and preloading his authority and legitimacy into the employee's mind. The employee is more likely to believe the attacker because there was no time for wondering about his presence or forming an opinion about his demeanor; these things were preloaded into the employee's mind. The pretexting part of this scenario was done prior to coming to the front desk by researching the authority figure's name to use as an explanation for being there and creating a convincing identity.
Interview and Interrogation 06:25-08:19 Another technique social engineers often use is interviewing and interrogating.
When investigators interview and interrogate suspects and witnesses, they use several elements, such as environment and tone of voice, to help put the other person at ease. Obviously, an interview with an investigator isn't relaxing—that's just the nature of the situation—but the investigator wants to read the other party correctly by not adding more stress than is already present.
The same is true for social engineers. They use many of the same tactics to read their victims, but unlike a good investigator, they also use them to manipulate people.
Ideally, attackers start with an interview first, then lead naturally and gradually into an interrogation.
In the interview phase, the attacker lets the target do the talking while the attacker mostly listens. This way, the attacker has the chance to learn more about the target and how to extract information.
Also, in this type of conversation, the target leads while the attacker mostly clarifies the target's statements and listens with sympathy. There's no specific checklist of topics or questions for the attacker to hit at this point; the best thing to do is just let the conversation flow from topic to topic according to the target's desires. This is usually a very casual and comfortable setting for the target. It's mostly a get-to-know you type of situation. The hacker's intent is to become more familiar with the target and build trust between the two parties.
Then the attacker leads the interview phase into an interrogation phase. It's most effective if this transition is smooth and natural, after the target already feels a connection with the attacker and trusts him.
In the interrogation phase, the attacker talks to the target about their statements. At this point, the attacker is mostly leading the conversation with questions and statements that will flow in the direction the attacker has in mind to obtain the information he's looking for. The attacker may also reveal some sensitive information to prompt the target to share more in return. It's all about manipulating and exploiting the target.
Environment 08:19-09:07 The environment the attacker chooses for conducting an interview and interrogation is essential to setting the mood. The location shouldn't be noisy or overly crowded. It's hard to get the target to keep going deeper into a subject without being distracted or becoming self-conscious if there's constant interruptions. Privacy is key to helping the target feel comfortable confiding in the attacker. It should be a stress-free and relaxing environment that puts the target at ease.
Seat arrangement is also important. Seats should be four to four-and-a half-feet apart and have a straight but comfortable back. The attacker shouldn't sit between the target and the door. The target should never feel trapped in any way. Lighting should be good enough for both parties to see each other clearly. This allows the attacker to read the target's micro-expressions and movements better. It also inspires the target to trust the attacker.
Observation 09:07-09:47 During these interviews and interrogations, the hacker pays attention to every change the target displays to help discern their thoughts and the topics that should be investigated further. The attacker pays attention to body language, such as arm and leg position, touching the face or hair, whether the target becomes pale or flushed, mouth and eyebrow movements, posture, head position, eyes, voice pitch and intonation, and word choice.
Pretty much every part of the human body is a clue about what's going on inside the mind. Most people don't even realize they're giving out clues or recognize them in other peoples' movements. But a skilled observer pays close attention and puts these clues together to discover thoughts and feelings.
Summary 09:47-10:17 Okay, that's the end of this video, so let's review what we talked about. Social engineers are successful because their attacks are carefully crafted. They devote a lot of time and effort to developing and mastering their techniques. Each attacker is unique in their style and motivation. They might be opportunistic or tailor their attack to specific targets. They use techniques such as elicitation, pretexting, preloading, impersonation, interviews, and interrogation.
7.5.5 Social Engineering Technique Facts
Not all attackers are the same. Attackers can have different motives, skill sets, and abilities. Attackers commonly change techniques depending on the target. Regardless of the attacker and the target, some form of social engineering techniques are commonly used.
This lesson covers the following topics:
- Attack types
- Elicitation
- Scanning
- Pretexting, preloading, and impersonation
- Interview and interrogation
Attack Types
Attacks on a network are opportunistic or targeted. An attacker trying to find and exploit a vulnerability is classified as an opportunistic attack. An organized crime group waging an assault on a network is an example of a targeted attack. The following table describes the characteristics of the two types of attacks.
| Attack Type | Description |
|---|---|
| Opportunistic | An opportunistic attack is typically automated and involves scanning a wide range of systems for known vulnerabilities, such as old software, exposed ports, poorly secured networks, and default configurations. When a vulnerable system is found, the attacker exploits the vulnerability, steals whatever is easy to obtain, and gets out. |
| Targeted | A targeted attack is much more dangerous. A targeted attack is extremely methodical and is often carried out by multiple entities that have substantial resources. Targeted attacks almost always use unknown exploits, and the attackers go to great lengths to cover their tracks and hide their presence. Targeted attacks often use completely new programs specifically designed for the target. |
| Baiting | In this attack, the attacker uses a promise or reward to lure the victim into sharing personal or confidential information, like a password. For example, an attacker often leaves a USB drive in a conspicuous location to tempt someone to connect it to their computer. The USB drive typically contains malware designed to autorun or an intriguing document with macros. Autorun-enabled malware is less effective on newer operating systems that disable autorun capability, so the intriguing document approach is much more common. A common example of this attack is to create a file with a name like "executive bonuses" or "staff layoff plans." Once opened, the file contains macro code designed to exploit the computer. |
Elicitation
Elicitation is a technique that tries to extract information from a target without arousing suspicion. The following table describes some elicitation tactics.
| Tactic | Description |
|---|---|
| Compliments | Attackers may give a target a compliment about something they know the target did in hopes that the target takes the bait and elaborates on the subject. Even if the target downplays the skill or ability involved, talking about it might give the attacker valuable information. |
| Misinformation | Attackers might make a statement with the wrong details. The attacker’s intent is that the target gives the accurate details that the attacker wants to confirm. The more precise the details given by the attacker, the better the chance that the target takes the bait. |
| Feigning ignorance | Attackers might make a wrong statement and then admit to not knowing much about the subject. This statement hopefully gets the target to not only correct the attacker but also explain why the attacker is wrong in detail. The explanation might help the attacker learn or at least have a chance to ask questions without looking suspicious. |
| Being a good listener | An attacker may approach a target and carefully listen to what the target has to say, validate any feelings expressed, and share similar experiences (that may be real or fabricated). The point is for the attacker to be relatable and sympathetic. As the target feels more connected to the attacker, barriers go down, and trust builds. This may lead the target to share more information. |
Scanning
Scanning is a technique that social engineers often use to gather information when trying to penetrate a network system remotely. Attackers can use network scans to find live computers on a network.
One of the most common network scanning methods is ping, which works by sending an ICMP message from one system to another. Based on the ICMP reply, an attacker knows whether the system is live and how quickly the packets travel from one host to another.
A ping sweep can be used to scan a range of IPs looking for live systems. Because ping and ping sweeps are common, many administrators block pings at the firewall or set the intrusion detection system (IDS) to send alerts when pings are received. Because of this, there is a good chance an attacker's attempts will be shut down, especially if they are not meticulous.
Pretexting, Preloading, and Impersonation
| Step | Description |
|---|---|
| Pretexting | Pretexting is researching and gathering information to create convincing identities, stories, and scenarios to be used on selected targets. |
| Preloading | Preloading sets up a target by influencing the target's thoughts, opinions, and emotions. |
| Impersonation | Impersonation is pretending to be trustworthy and having a legitimate reason for approaching the target to ask for sensitive information or access to protected systems. |
Interview and Interrogation
| Concept | Description |
|---|---|
| Interview and interrogation flow | The interview phase flows into the interrogation phase as follows:
|
| Environment | The environment the attacker chooses for conducting an interview and interrogation is essential to setting the mood.
|
| Observation | During these interviews and interrogations, the attacker observes every change the target displays.
|
7.5.6 URL Obfuscation Techniques Facts
Obfuscation is frequently used to mask something important, like a URL. URL syntax is unique and often used when searching for suspicious sites and activity. By masking URLs, attackers can avoid detection, confuse users, and generate hidden functionality within payloads.
This lesson covers URL obfuscation techniques:
URL Obfuscation Techniques
The following table describes some obfuscation techniques:
| Obfuscation Technique | Description |
|---|---|
| URL shorteners | URL shorteners are online tools for creating short links from long URLs. They are common on social media, where character limits are a concern. While they offer convenience, they also pose security risks. Malicious actors can use URL shorteners to disguise harmful content, conduct social engineering attacks, and collect user data. One of the primary risks associated with URL shorteners is phishing attacks. Attackers can use shorteners to disguise malicious links to trick unsuspecting users into clicking them. Additionally, URL shorteners often bypass controls like URL filtering and blocklisting, making detecting and mitigating malicious activity more difficult. Another risk is data privacy. When users create shortened URLs, they often provide information to the shortening service, such as the original URL, the date and time of creation, and the IP address associated with the creator of the shortened link. This information can be used to track user activity across the Internet. URL shorteners rely on third-party services to redirect users to the original URL. The shortened URL may no longer work if the third-party service goes offline or the link is not correctly maintained. This characteristic is typically referred to as "link rot." To mitigate these risks, users should be cautious when clicking on shortened URLs, particularly if unfamiliar with the source. They should also use reputable URL shorteners and avoid creating shortened links for sensitive information. Additionally, users should inspect shortened URLs by revealing the original site |
| URL un-shortening | Clicking a shortened link is not a good method of determining where it leads. If it leads to a malicious site, clicking it will lead to trouble. Fortunately, there are several sites designed to help investigate shortened URLs without clicking them, such as unshorten.me or VirusTotal |
| QR codes | QR codes offer convenience and are often used to replace URLs. Most modern camera apps have built-in QR code recognition, allowing users to scan codes to visit websites without typing or clicking. QR codes offer a "fun factor," which makes them all the more enticing for users and effective for attackers. |
| URL doppelgangers | A doppelganger domain is one that is missing the dot between the subdomain and domain part, for example wwwgoogle.com instead of www.google.com. A savvy attacker may work to locate doppelgangers for popular websites and then register them as unique domains hosting malicious content. Fortunately, Google owns the doppelganger for their site, and it redirects to the originally intended destination. |
| Character swapping | Character swapping substitutes one or more characters in a URL for very similar looking ones. This will not always be readily apparent by simply looking at the URL yourself (especially depending on the font style). Consider the two examples below.
|
| URL encoding | URL encoding seeks to mask the content of a URL to avoid pattern matching or simple visual inspection detection methods and to confuse engineers, analysts, and users. Consider the examples below. In this example, colons and slashes are replaced with their URL encoded (hexadecimal) equivalents. %3A represents ":" and %2F represents "/".
In this example, every character of the URL is replaced with its hexadecimal equivalent. Most search engines can convert encoded URLs.
In this example, the entire URL is encoded using base64 and preceded with some qualifiers to help identify its purpose. Loading the string into a browser reveals what the string of characters represents.
|
| URL redirects | In the context of obfuscation, URL redirects often take advantage of a poorly secured website. Website developers often program redirect functionality within their pages to send visitors to companion sites and payment processors. This redirect capability can be abused, allowing an attacker to use the site to send visitors anywhere. The redirect URL often looks like:
The vulnerable component is a PHP element and could use any name, not just "redirect.php" as shown here. The vulnerable component may use a different language, but PHP is very common. For example, if Google had this vulnerability on their site (they do not), the redirect may look like:
The appeal of this obfuscation method is that the URL's root (www.google.com) is trustworthy, but the user will land on the page referenced in the redirect, which is likely not trustworthy. Combining this method with other obfuscation techniques to mask the redirection URL can make it highly effective. |
Visit https://www.comptia.org/certifications/cybersecurity-analyst/ for more on how these concepts relate to certification.
7.5.7 Phishing and Internet-Based Techniques
Click one of the buttons to take you to that part of the video.
Phishing and Internet-Based Techniques 00:00-00:11 Now that we've explored the different phases involved in a social engineering attack, let's talk about some specific attacks.
Phishing 00:11-01:36 One of the most successful social engineering methods is called a phishing attack. This is when a social engineer masquerades as a trustworthy entity in an electronic communication.
The attacker might send out a mass email that looks like it came from your bank, PayPal, Amazon, eBay, or the government. Attackers even copy graphics and text directly from the authentic site to make the email look completely legitimate.
The goal is to trick the recipient into revealing usernames, passwords, bank account numbers, credit card numbers, or some other sensitive information. The message will most likely say something like, "We have reason to believe that we have your money, and we need to get it to you. Give us your contact information so we can return your money."
If you click on any links in the email, it brings up a page that looks like a legitimate web page for an actual organization. This page asks you to put in your username and password, your account number, or some other sensitive piece of information. When you hit Submit, the information goes to the person who sent the email, not to the institution. Unfortunately, this approach is very easy to execute and extremely successful.
Many recent large-scale security breaches directed at major retailers and government organizations were orchestrated using simple phishing emails that tricked employees into supplying the attacker with their username and password.
There are several variations of the phishing attack that you also need to be familiar with.
Spear Phishing 01:36-01:46 In spear phishing, attackers gather information about the victim, like which online banks they use. Then they send phishing emails that appear to be from that specific bank.
Whaling 01:46-01:52 Whaling is another form of phishing that targets senior executives and high-profile victims.
Vishing 01:52-02:03 Vishing is like phishing, but instead of an email, the attacker uses Voice over IP, or VoIP, to gain sensitive information. The term is a combination of voice and phishing.
SMS Phishing 02:03-02:20 There's also SMiShing, or SMS Phishing. In this type of phishing attack, the social engineer sends a text message with an urgent topic to trick the victim into taking immediate action. The message could contain a malware link or a fake phone number to extract information from them.
Pharming 02:20-02:43 Pharming is another attack to look out for. It involves the attacker executing malicious programs on the target's computer so that when the user enters any URL, it redirects traffic to the attacker's malicious website. This attack is sometimes called phishing without a lure. A pharming attack can be performed two ways: DNS cache poisoning and Host file modification.
DNS Cache Poisoning 02:43-03:03 In DNS cache poisoning, the attacker launches the attack on the chosen DNS server. Then the attacker changes the target website's IP address to a fake website. When the user enters the target website's URL, the DNS server redirects the user to the fake IP address and then to a fake website controlled by the attacker.
Host File Modification 03:03-03:32 In host file modification, the attacker sends a malicious code as an email attachment.
When the user opens the attachment, the malicious code executes and modifies local host files on the user's computer. When the user enters a target website's URL in the browser, the compromised host file automatically redirects the user's traffic to the fraudulent website controlled by the attacker. Pharming attacks can also be executed by malware like Trojan horses and worms.
Social Networking 03:32-04:38 In recent years, with the growth of social media, many social engineers are turning to applications such as Facebook, Twitter, and Instagram to gather information and steal identities.
Many people post their entire lives on social media, from pictures, locations, and friendships to interests, hobbies, and work. The abundance of information makes it easy for an attacker to piece together clues about possible targets and victims. After collecting all this information, the attacker is much better prepared to launch an attack.
Also, many attackers use social media to scam users. For example, they may post malicious links with enticing headlines about a celebrity's secret, some kind of political scandal, children and animals suffering in a faraway place, fun quizzes, and other themes that will make users curious. There are also many sexual solicitation scams.
All these scams are designed to draw in the user. And once they've clicked the link and been redirected to a malicious site, the attacker controlling the site will request personal information and sensitive data such as email, address, and credit card number.
Summary 04:38-05:00 Okay, that's it for this video. So, to review, social media is becoming an important tool for attackers looking to gather information about specific businesses or people. Many of the attacks are some variation of a phishing attack, like spear phishing, whaling, SMS phishing, vishing, or pharming.
7.5.8 Phishing and Internet-Based Technique Facts
Users interfacing with the internet, through email or browsing websites, can pose substantial security threats to an organization. Attacks that entice users to provide sensitive information or click a link that installs malware are called social engineering attacks. Increasing user awareness of these types of threats and how to avoid them successfully is critical to an organization's overall security.
This lesson covers the following topics:
- Phishing
- Other social engineering attacks
Phishing
One of the most successful social engineering attacks is called a phishing attack. In a phishing attack, the social engineer masquerades as a trustworthy entity and leverages emails with malicious hyperlinks or malware-infected attachments. Clicking on the link leads the user to a website that typically prompts for credentials, or opening the attachment leads to the execution of a macro file resulting in an infection or launching a reverse shell.
| Phishing Attack | Description |
|---|---|
| Spear phishing | In spear phishing, an attacker gathers information about the victim, such as their online bank. The attacker then sends a phishing email to the victim that appears to be from that bank. Usually, the email contains a link that sends the user to a site that looks legitimate but is intended to capture the victim's personal information. |
| Whaling | Whaling is another form of phishing that targets senior executives and high-profile victims. |
| Vishing | Vishing is like phishing, but instead of an email, the attacker uses voice over IP (VoIP) to gain sensitive information. The term is a combination of voice and phishing. |
| Smishing | In SMS phishing (smishing), the attacker sends a text message with a supposedly urgent topic to trick the victim into taking immediate action. The message usually contains a link that either installs malware on the victim's phone or extracts personal information. |
Phishing Campaigns
A phishing campaign tests an organization's vulnerability to this type of social engineering attack and measures the effectiveness of security awareness training. A campaign focuses on a specific theme and difficulty level and uses it as a gauge to measure vulnerability. Phishing campaigns typically correlate to security awareness training activity to show before and after results, hoping to demonstrate a reduction in vulnerability levels after completing awareness training activities.
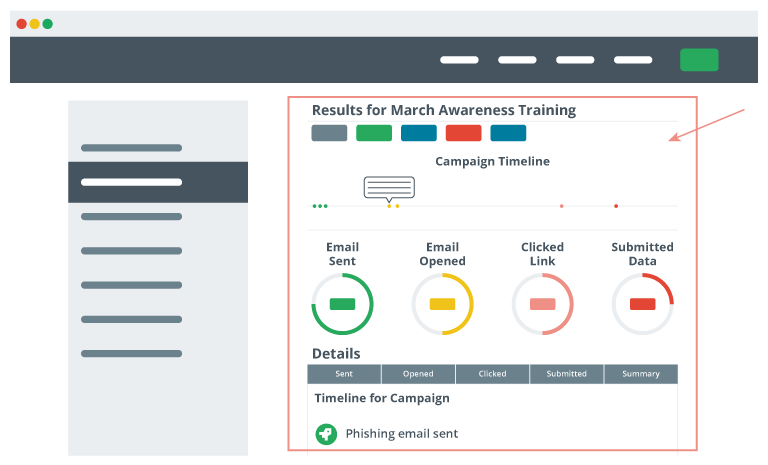
Other Social Engineering Attacks
The table below describes other common social engineering attacks.
| Social Engineering Attack | Description |
|---|---|
| Pharming | Pharming involves the attacker executing malicious programs on the target’s computer so that any URL traffic redirects to the attacker’s malicious website. This attack is also called phishing without a lure. The attacker is then privy to the user’s sensitive data, like IDs, passwords, and banking details. Pharming attacks frequently come in the form of malware such as Trojan horses, worms, and similar programs. Pharming is commonly implemented using DNS cache poisoning or host file modification.
|
| Social networking | Many attackers are turning to applications such as Facebook, Twitter, and Instagram to steal identities and information. Also, many attackers use social media to scam users. These scams are designed to entice the user to click a link that brings up a malicious site the attacker controls. Usually, the site requests personal information and sensitive data, such as an email address or credit card number. |
7.5.9 Use the Social Engineer Toolkit
Click one of the buttons to take you to that part of the video.
Use the Social Engineer Toolkit (SET) 00:00-00:21 In this demo, we're going to talk about how attackers can capture user credentials from a web page. While there are many different methods used to gain unauthorized access to a user's web account, we're going focus on how to clone a website's sign-in page and direct the user to enter the information on a fake page.
Choose a Site to Clone 00:21-01:18 All right. Let's get started. We're going to use one of the many exploits from the Social Engineering Toolkit. Because this is a demo, we're going to use a fake website, but this could be done to most real sites fairly easily. I'll enter the credentials to show how the tool works.
Since we're using a fake website, we can navigate straight to it. But since we're only going to clone one page of the site, we need to know what the full URL is for the login page. Let's go to www.fakewebsite.com.
This is a Wordpress site, which makes things a little easier, since the login page name is almost always the same. To make sure, though, we'll click the login button on the page and see where it takes us. I'll scroll down here and click Log in.
Now that we're on the login page, we can look in the address field and see the full URL of the page we want to clone.
Clone the Website 01:18-03:18 Since we'll need this URL later, we're going to copy it. Now that we have the page we want to clone, let's open up the Social Engineering Toolkit. Since it's a command line app, we're going to work in the terminal. Once it opens, I'll type in ‘setoolkit' and press Enter.
On this screen, you can see that there are two attack options, Social Engineering Attacks and Penetration Testing. The remaining options are for maintaining the Social Engineering Toolkit. The option that we're looking for can be found under Social Engineering Attacks. I'll select 1 and press Enter. We're interested in cloning a website, so we'll select Option 2, Website Attack Vectors.
To get to the clone option from here, we'll select 3, Credential Harvester Attack Method, and then 2, Site Cloner.
Since we'll be using this machine to host the cloned page and listen for credentials, we can leave the default options. I'll just press Enter to continue. Next, we'll use Ctrl+Shift+V to paste the URL we copied earlier and press Enter again.
Now the Social Engineering Toolkit is saying, "Hey, do you understand what we're saying here?" Yes, yes I do. It also offers a couple of troubleshooting instructions in case the tool isn't working. Since we expect it to work, we'll just press Enter to continue.
Now we're finally at the page that will show us if the tool sees anything interesting. Earlier, I set up a website with a name that's just a little different from the name of the website we're cloning. This is the page that would be sent to a user to try to trick them into opening it. It's basically the same address, but with the number 1 at the end. Let's go to that page in our web browser. I'm going to keep the terminal open on the side and open the web browser on the other side of the screen so you can see the tool working. I'll do that by opening Firefox and navigating to www.fakewebsite1.com.
Enter Credentials on the Cloned Website 03:18-04:23 When I navigated to the cloned webpage, something happened on the right, in the tool. It displayed some information. This just shows a connection request that was served to the requesting computer. Now let's see what happens if I put in some user credentials. I'll type in ‘admin' for the user and ‘letmein' for the password. Press Enter to log in.
And there we go. In the terminal, you can see some more information from the tool. The tool tries to guess what information is important. This time, it correctly identified the password field, but didn't find a username field. That's because Wordpress username fields have kind of ambiguous names. But that information was still transmitted to the tool, as you can see right here.
It's worth noting that, after an attempted authentication, the Social Engineering Toolkit actually redirected us to the real website. This means that, typically, a user would likely just assume that they had entered their credentials incorrectly and try again. They probably wouldn't suspect a thing.
Summary 04:23-04:41 And that's it for this demo. We discussed how someone might use the Site Cloner in the Social Engineering Toolkit, and we saw how an attacker can clone a website's look and feel and trick users into entering their credentials on a fake website.

