Chapter 4 – IT Life Cycle Management
Objectives
- To establish a comprehensive framework for managing the development
- Implementation
- Testing
- Maintenance of IT systems
- Ensuring efficient operations
- Enhanced quality
- Risk mitigation
- Compliance adherence
- Continuous improvement throughout the IT lifecycle.
Overview of Business Processes and IT Integration
- Business Processes in Organizations: Organizations use business processes to manage tasks related to software development, maintenance, and IT infrastructure. These processes offer control over key activities, like software acquisition and management, ensuring efficient project execution.
- Evolution of Business Applications: Earlier, organizations custom-built software in-house and managed it on-premises. Today, Software-as-a-Service(SaaS) applications are more common, with integrations and minimal in-house development, shifting focus from software development life cycle to system acquisition life cycle.
- Implications for IT Infrastructure: This transformation necessitates a lifecycle management approach similar to software development, as business processes are often complex and interlinked with applications.
Role of IS Auditors in Lifecycle Management
- Auditing Methodologies and Practices: IS auditors must scrutinize an organization’s processes for software and infrastructure acquisition, development, and management. Understanding lifecycle management provides insights into the organization's efficiency in translating requirements into functioning systems.
- Auditing Software Applications: Auditors focus on input, processing, output controls, calculation accuracy, and data integrity. Ensuring these controls are effective confirms that the applications support key business processes reliably.
- Effective Audits: Audits reveal how well the organization manages software and infrastructure, identifying areas for improvement in the development and maintenance processes.
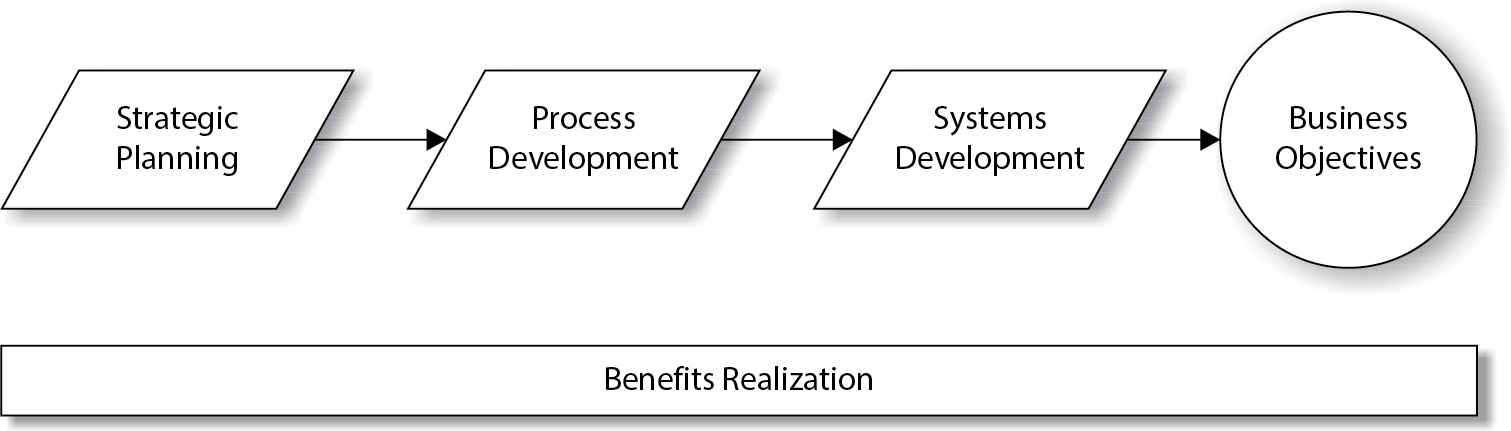
Benefits Realization in Business Processes
- Concept of Benefits Realization: Benefits realization, or business realization, results from strategic planning, process development, and systems implementation, driving business operations toward set objectives.
- Strategic Alignment: This approach aligns business processes, systems acquisition, and development, forming the core of business operations. Effective benefits realization indicates that the organization is achieving its strategic goals efficiently.
- Audit’s Role in Benefits Realization: Audits of these activities offer an objective evaluation of their success, highlighting how effectively the organization leverages processes and systems to realize business benefits.
Introduction to Program Management
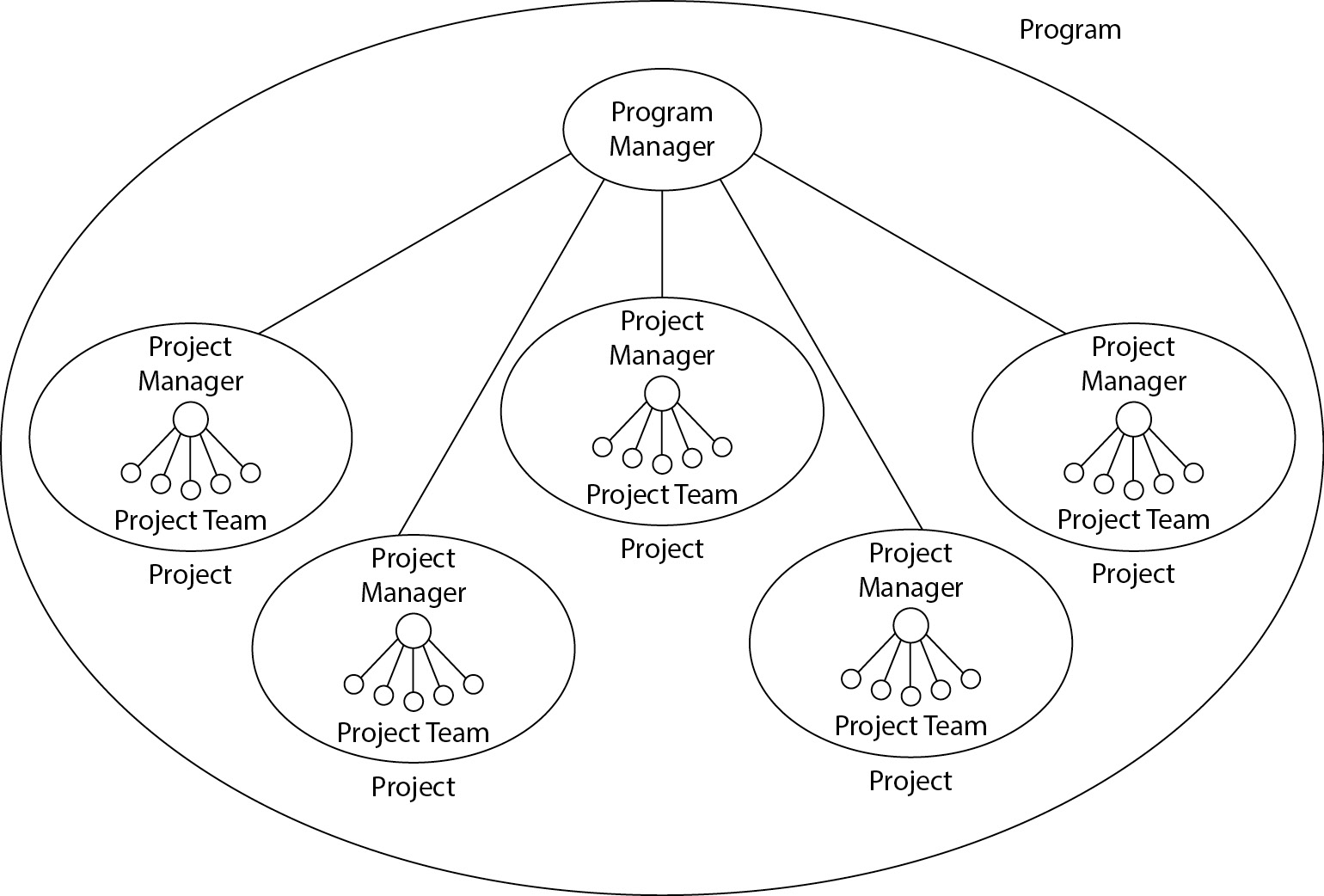
- What is a Program? A program is a collection of projects organized to achieve specific business goals. It involves managing large, complex activities over multiple years, with each project having its own manager, budget, and schedule.
- Features of a Program: Programs have defined scopes, budgets, resources, and timelines. They aim to align projects, manage dependencies, resolve conflicts, and coordinate shared resources.
- Role of Program Manager: The program manager oversees all projects, managing resources, schedules, and conflicts, ensuring that each project contributes to the overall objectives
Introduction to Program Management
 .
.
Starting a Program
- Developing a Program Charter: The charter defines program objectives, timelines, funding, key leaders, and executive sponsors. It formalizes the program’s foundation, setting the scope and direction.
- IdentifyingResources: Senior management determines necessary resources like funding, personnel, systems, and assets. These resources form the backbone of the program, enabling its launch and progression towards objectives.
- Launching a Program: With a clear charter and identified resources, the program is initiated, aligning its efforts with the organization’s strategic goals.
- ProgramManagerRole: Middle or senior managers often act as program managers, even if their title doesn’t specify it. They manage multiple projects, coordinate resources, address issues, and resolve conflicts, driving projects towards shared goals. The emphasis is on achieving outcomes rather than titles.
Running a Program
- MonitoringProjectSchedules: Program managers track project progress, frequently communicating with participants to stay updated. Adjustments are made as needed to maintain momentum.
- ManagingBudgetsandResources: Continuous budget monitoring ensures control over spending across projects. Resources are managed creatively due to scarcity, with the program manager often reallocating resources to meet project needs.
- ConflictManagement: Resource conflicts are common, as projects often compete for the same assets. The program manager must address these conflicts or escalate unresolved issues to senior management.
- CreatingStatusReports: Program managers provide detailed updates to senior management. These reports cover issues, conflicts, and resolutions, ensuring transparency and informed decision-making.
- Executive Intervention: Unresolved conflicts may require prioritization by senior management to maintain program progress. Status reports help executives understand resource needs and project alignments.
Introduction to Project Portfolio Management (PPM)
- ProjectPortfolio: A project portfolio includes all active projects within an organization, regardless of their relation to common objectives. It encompasses projects from different programs supporting diverse goals.
- Centralized Information Management: A portfolio consolidates data on all projects, enabling senior management to access key details like sponsors, managers, timelines, budgets, and dependencies.
- PurposeofPPM: PPM offers a strategic overview of the organization’s projects, facilitating decision-making, better resource allocation, and alignment with broader business goals.
- Efficient Tracking: The electronic storage of project data allows for sorting and filtering, helping executives monitor project progress, manage dependencies, and optimize resource usage.
- Alignment with Business Objectives: PPM supports overall business strategy by ensuring that projects are progressing in line with organizational priorities, providing a comprehensive view of active initiatives.
Introduction to Business Case Development
- IT's Role in Business: IT is designed to support business objectives, meaning every IT project should lead to tangible benefits, even if it’s highly technical or abstract.
- PurposeofBusinessCase: It explains expected business benefits before initiating a project, following a feasibility study. The feasibility study defines potential solutions, but the business case focuses on costs, benefits, and their impact on the business.
- Components of a Business Case:
- Business Problem: Detailed problem description.
- Feasibility Results: If applicable, includes study results.
- High-Level Project Plan: Timeline and resource estimates.
- Budget: Execution and solution costs.
- Metrics: How benefits will be measured, backed by past project examples.
- Risks: Identifies potential risks and mitigation strategies.
Introduction to Project Management
- Definition of a Project: A project is a managed sequence of tasks aimed at achieving a specific objective. It may involve a single person or multiple teams and can last from a few days to years.
- OrganizingProjects: Projects must align with organizational goals, receiving formal approval and consistent documentation.
- Social Context and Culture: A project involves teams with defined relationships, creating a social environment that influences project execution.
- Models of Project Team Structures
- Direct Report: The department manager serves as project manager, with team members directly reporting to them. Variations include managers participating as team members.
- Influencer: The project manager has no direct authority and must rely on persuasion to drive progress.
- Pure Project: The project manager holds authority over the team, though members do not report directly to them.
- Matrix Model: Authority is shared between project managers and department managers, both overseeing team members.
Steps in Project Management
The following are the steps that must be considered and planned at the beginning of the project:
- Initiating a Project
- Setting team priorities
- Project kickoff meeting
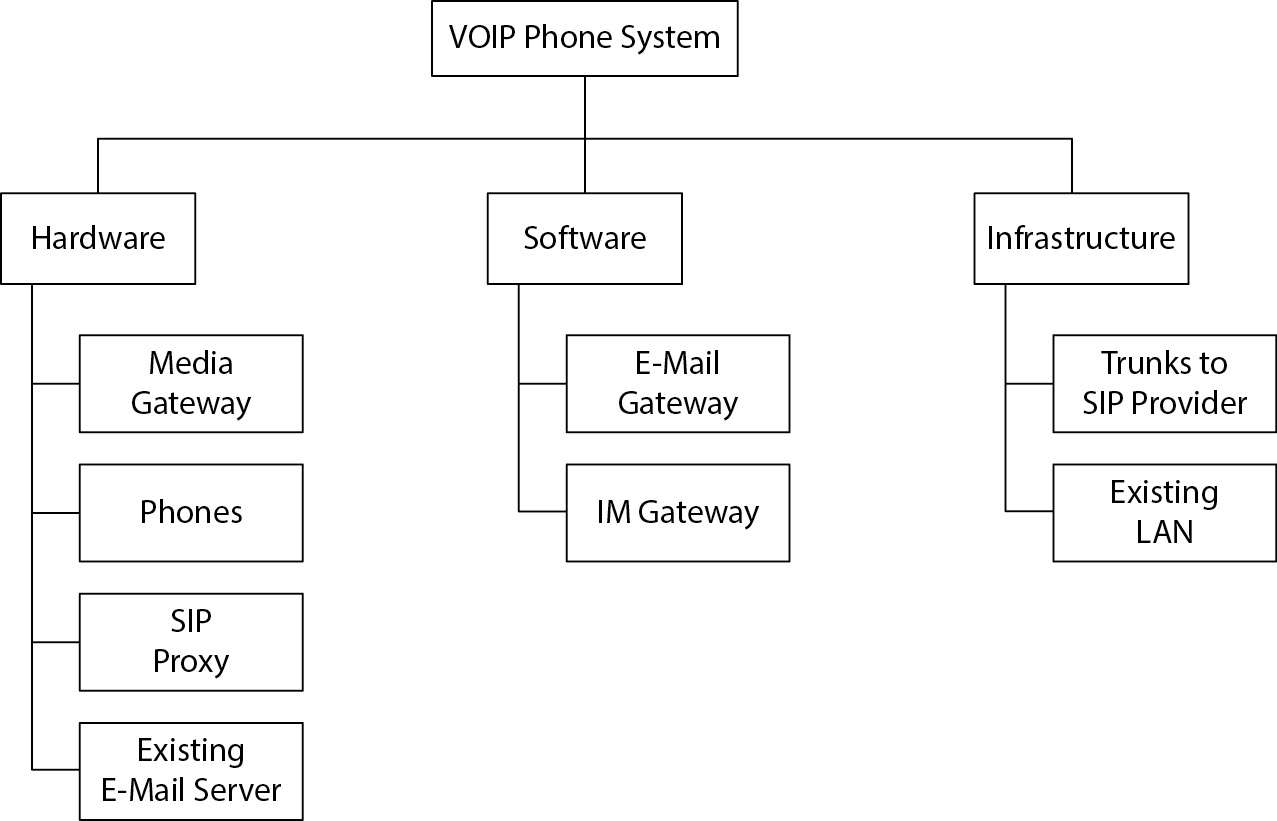
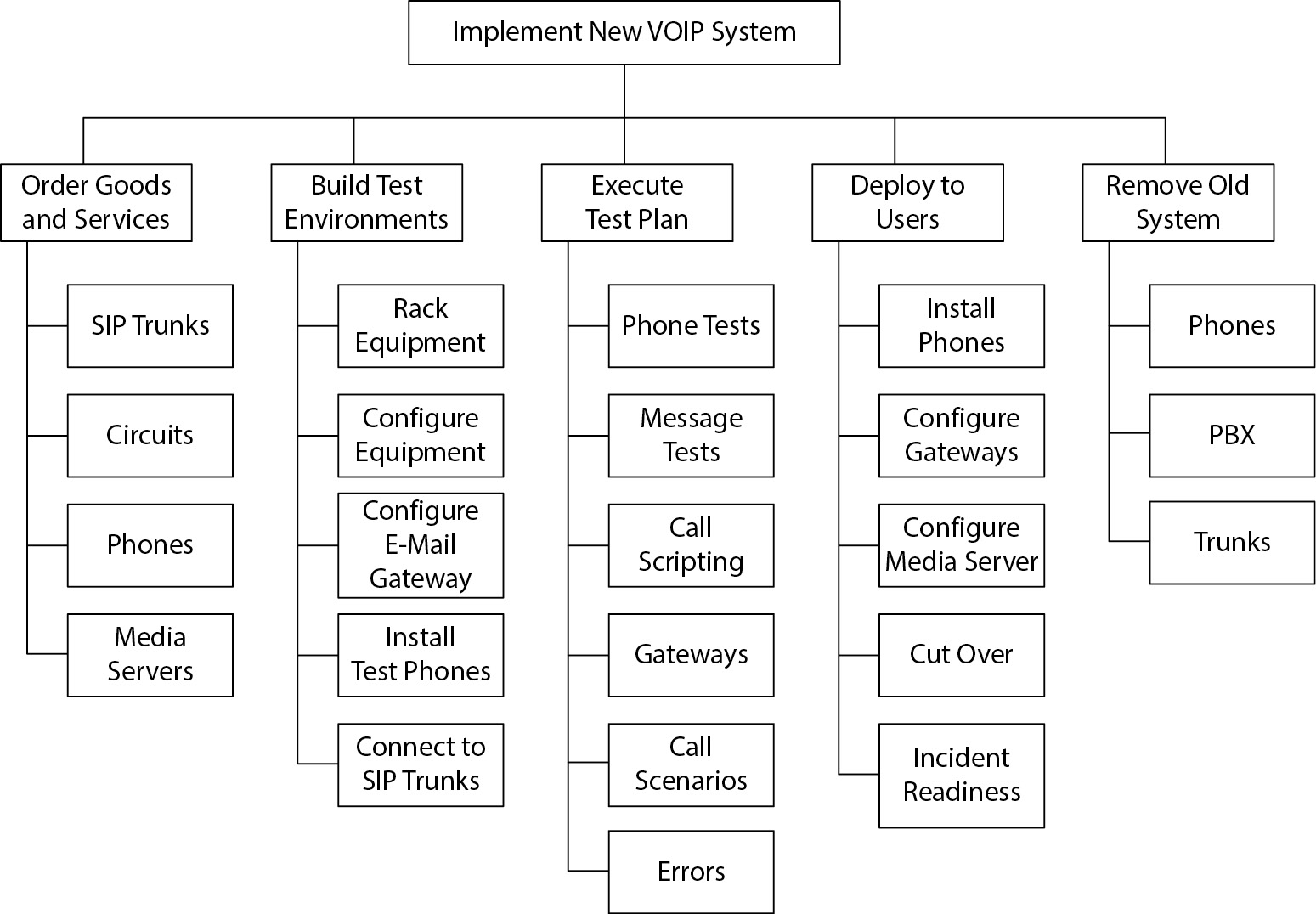
Object Breakdown Structure (OBS)
An OBS is a graphical or tabular representation of project components, offering a hierarchical view from high-level systems to detailed parts. It aids management and team members in visualizing project scope and objectives.
Work Breakdown Structure (WBS)
A WBS provides a logical depiction of tasks required to complete the project, detailing both high- level and fine-grained tasks. It serves as a foundation for creating the project schedule and provides clarity on task sequence.
Breakdown Structures
Managing Projects
Role of the Project Manager: The project manager develops and maintains the project schedule, ensuring that it reflects task progress, updates, and changes. This includes adding new tasks, adjusting dependencies, and adapting to unexpected issues.
- Key Activities:
- Recording Task Completion: The project manager updates the schedule as tasks are
- Running Project Meetings: Regular meetings with participants ensure that progress, issues, and next steps are clearly discussed. The project manager manages agendas, minutes, and communication updates.
- Tracking Project Expenditures: The project manager monitors spending, ensuring that the project remains within budget and reporting financial details as necessary.
- Key Activities:
Skills for Success: A successful project manager should be highly organized, detail-oriented, communicative, and skilled in negotiation. People skills are critical to effectively managing teams and facilitating collaboration.
Adaptability: In smaller organizations, a single individual may assume multiple roles, while larger projects may require distinct teams for each role, ensuring effective task management and project success.
The RACI Matrix in Project Planning
- Roles in the RACI Model:
- Accountable: One individual is accountable for overall project success.
- Responsible: One or more individuals are responsible for completing tasks.
- Consulted: Subject matter experts provide guidance throughout the project.
- Informed: Stakeholders are kept updated on project progress.
- Use of RACI Charts: Program and project managers create RACI charts to clarify each team member’s role, enhancing coordination and communication.
Detailed Activities in Project Planning
- Task Identification: All tasks needed for project completion are identified, often using a WBS
- Task Estimation: Time and effort estimation for each task is crucial, using metrics
- Task Resources: Resources include people, equipment, software licenses, and materials, often requiring specific expertise
- Task Dependencies: Some tasks depend on the completion of others, and managing these dependencies ensures smooth project progression.
- Milestone Tracking: Significant events, such as design or testing completion, act as milestones. Reviews at these points allow management to decide whether to continue or adjust the project.
- Task Tracking: Ongoing monitoring of task status helps anticipate resource needs and identify delays, enabling timely intervention.
Estimating and Sizing Software Projects
- Tools and Methods: Estimation tools and methodologies improve accuracy and reduce effort. They include OBS, WBS, Source Lines of Code (SLOC), and Function Point Analysis (FPA).
- Using OBS and WBS: The OBS visualizes the system structure, while WBS breaks down tasks, making large projects more manageable.
- SLOC and KLOC: SLOC/KLOC estimates are traditional methods for sizing software projects based on code lines, though newer methods focus on features, pages, or forms.
- Constructive Cost Model (COCOMO): Developed in the 1970s, COCOMO uses factors like KLOC and complexity ratings to estimate effort, with three levels: Basic, Intermediate, and Detailed.
- Beyond Man-Months: Other costs include development tools, workstations, servers, software licenses, network devices, storage, and connectivity, training requirements, equipments and travel.
Scheduling Project Tasks
- Creating the Project Schedule: Once tasks, resources, dependencies, and effort levels are identified, the project manager creates the schedule using tools like Trac, Microsoft Planner, or Microsoft Project.
- Initial Schedule Adjustments: After entering tasks into a planning tool, the initial end date may exceed management's expectations.
- Visual Tools for Project Scheduling
- Gantt Chart: A Gantt chart visually represents tasks, their duration, dependencies, and percent completion. It uses rows for tasks and horizontal bars for time, providing an overview of project progress.
- PERT Chart: The Program (or Project) Evaluation and Review Technique (PERT) chart displays tasks, timelines, and dependencies in sequential order, helping visualize task progression and identify potential bottlenecks.
Scheduling Projects
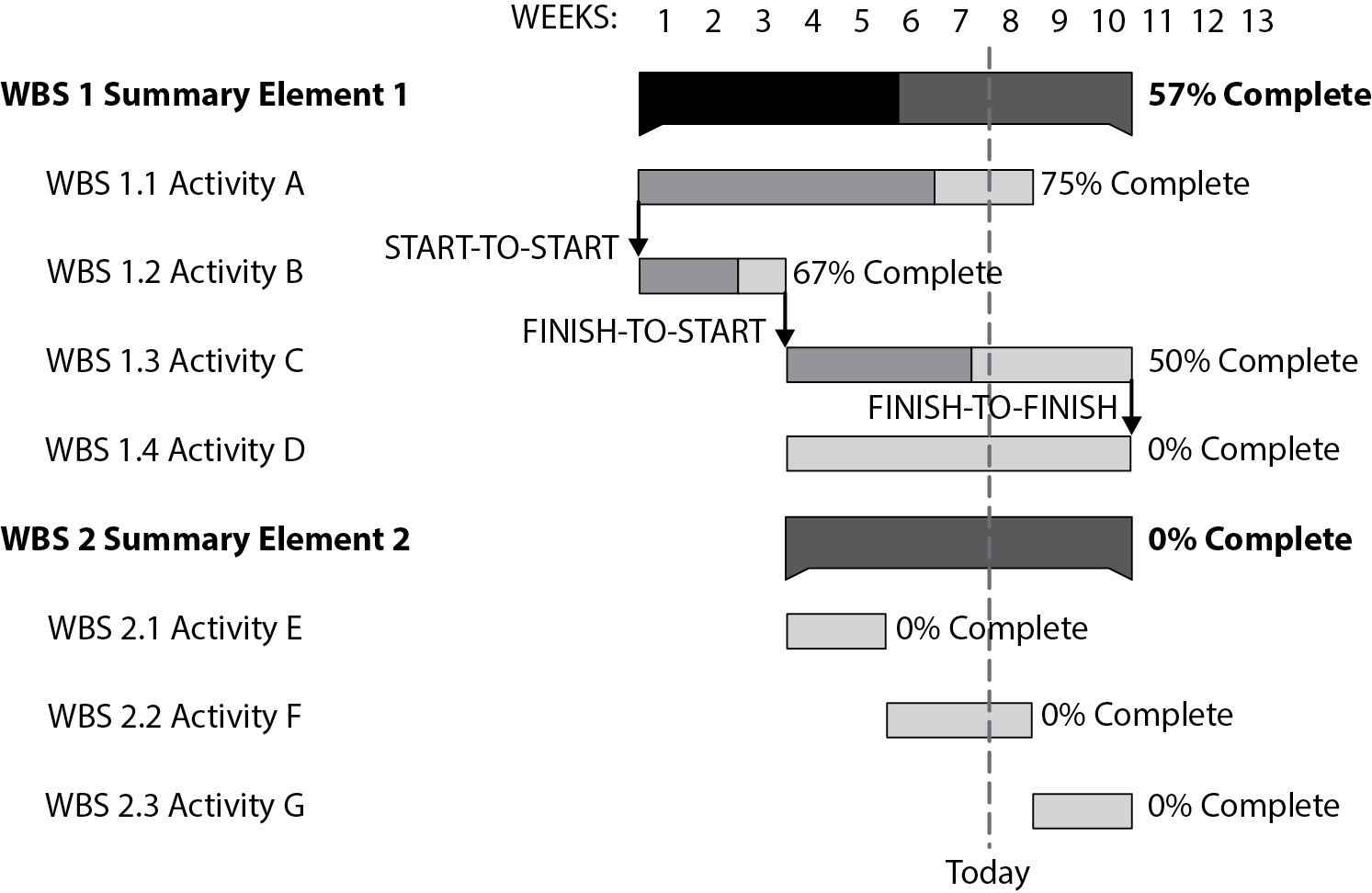
Squeeze to Fit, Timebox Management and Project Records
- Squeeze to Fit: Projects often overrun initial timelines and budgets, requiring managers to compress schedules by removing dependencies and optimizing tasks.
- Timebox Management: Timeboxing divides projects into fixed periods with specific deliverables.
- AgileSprints: Agile methodology divides projects into one-to-four-week sprints, focusing on short-term goals. This approach is not limited to software development, enabling teams to achieve results rapidly.
- Types of Project Records:
- Project Plans: Initial plans, task schedules, and updates.
- Project Changes: Documented changes in schedule, deliverables, and budget.
- Legal Documents: Contracts, SLAs, and proposals.
- Meeting Records: Agendas, minutes, issues, and decisions.
- **ResourceConsumption:**Purchaseorders,invoices,andtimesheets.
- **Deliverables:**Drafts,finalversions,andapprovals.
Good-Cheap-Fast Triad in Project Management
- Principles of the Triad:
- If the project is Good and Cheap: The project will not be fast.
- If the project is Good and Fast: The project will not be cheap.
- If the project is Cheap and Fast: The project will not be good.
- Applying the Triad: Managers must choose the most desirable characteristics for a project, balancing budget, schedule, and quality to achieve optimal results.
Comprehensive Project Documentation
- PurposeofDocumentation: Documentation supports various roles, ensuring users understand system operation, support teams can assist users, and IT operators manage systems effectively.
- DocumentationTypes:
- Users:: Guides for system operation and troubleshooting.
- Support: Procedures for problem-solving and user assistance.
- ITOperations: Monitoring, backups,recovery,andmaintenanceinstructions.
- Developers: Technical descriptions of system components and interfaces.
- Auditors: Controls, data processing, and compliance documentation.
- Configuration Management: Change management and infrastructure details.
- Security: Controls, logging, and incident response plans.
- Disaster Recovery: Recovery procedures for business continuity.
Project Management Methodologies
- Overview of Methodologies: Managing a project is complex, and different methodologies are used depending on project type. Each methodology varies in approach, documentation, and management techniques.
- Common Methodologies:
- Waterfall: Linear and sequential, suitable for projects with clear requirements.
- Agile: Iterative, allowing flexibility, commonly used in software development.
- Scrum: A subset of Agile, focusing on short sprints and daily stand-ups for progress tracking.
- Lean: Emphasizes value and efficiency, minimizing waste in project processes.
Introduction to PMBOK
The Project Management Body of Knowledge (PMBOK) is an international standard that outlines essential project management processes, documented by the Project Management Institute (PMI).
- Process-Based Model: PMBOK describes processes through inputs (e.g., documentation), tools and techniques (mechanisms), and outputs (e.g., deliverables or services).
- The Five Process Groups: PMBOK organizes project processes into five groups, guiding project management from start to finish:
- Initiating: Defining the project scope and obtaining approval.
- Planning: Establishing goals, tasks, timelines, and resources.
- Executing: Performing tasks to achieve project objectives.
- Controlling and Monitoring: Tracking progress, managing changes, and ensuring alignment with plans.
- Closing: Finalizing all activities and formally closing the project.
- The Five Process Groups: PMBOK organizes project processes into five groups, guiding project management from start to finish:
Knowledge Areas
- PMBOK's process groups and knowledge areas form a matrix, ensuring each process aligns with a specific group and knowledge area
- Benefits of PMBOK: It provides a structured approach to project management, enhancing consistency, predictability, and overall success. PMBOK is detailed in A Guide to the Project Management Body of Knowledge, available through PMI publications.
| Project Integration Management | Project Human Resource Management |
|---|---|
| Project Scope Management | Project Communications Management |
| Project Time Management | Project Risk Management |
| Project Cost Management | Project Procurement Management |
| Project Quality Management | Project Stakeholders Management |
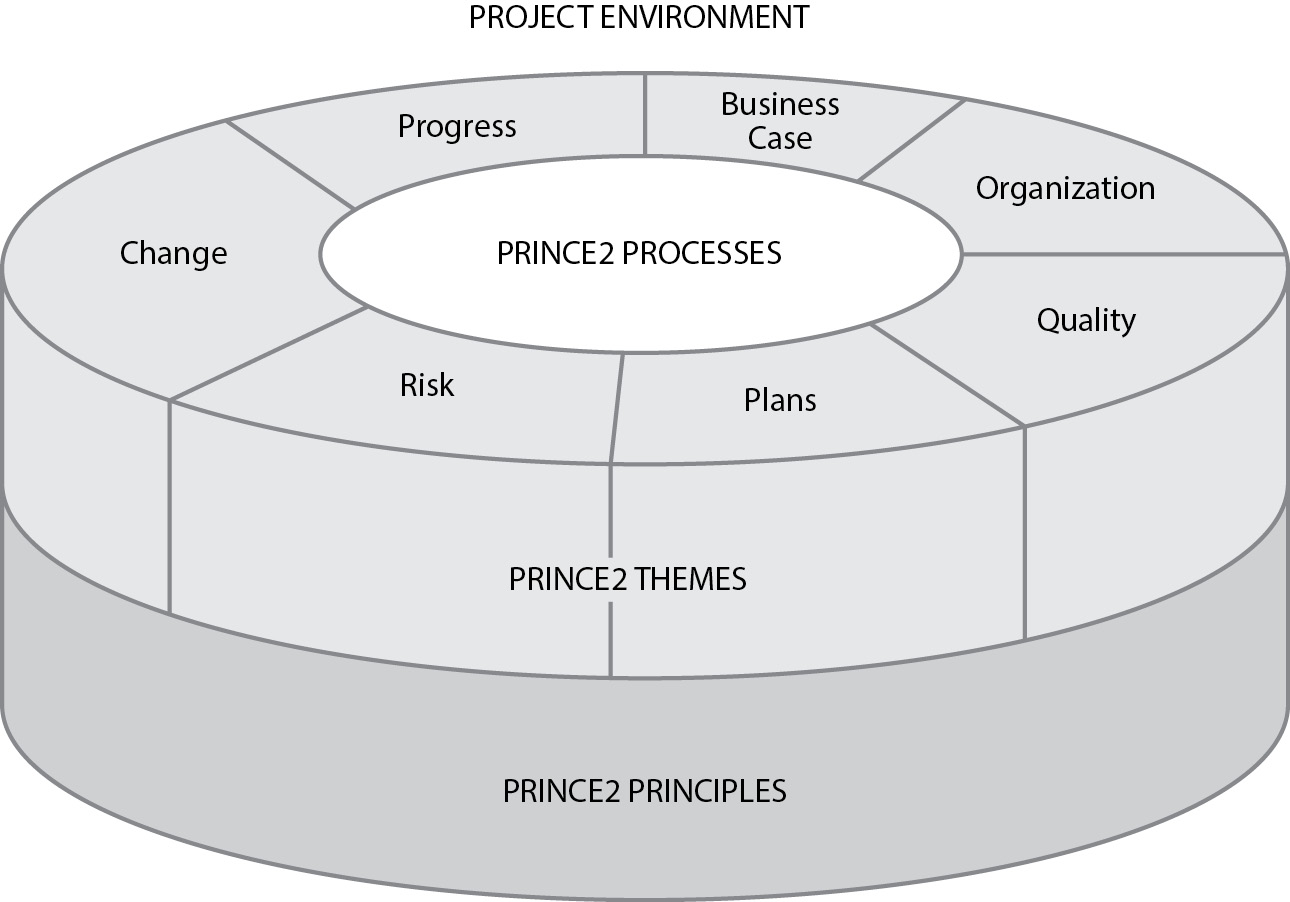
Projects in Controlled Environments (PRINCE2)
- Introduction to PRINCE2: PRINCE2, developed by the U.K. Office of Government Commerce and now managed by AXELOS, is a process-driven project management framework.
- Top-Level Processes: PRINCE2 organizes projects into seven processes:
- Starting Up a Project (SU)
- Directing a Project (DP)
- Initiating a Project (IP)
- Controlling a Stage (CS)
- Managing Product Delivery (MP)
- Managing Stage Boundaries (SB)
- Closing a Project (CP)
PRINCE2 integrates principles, themes, and processes, offering a structured approach to project management, widely adopted in the U.K. and internationally.
Projects in Controlled Environments (PRINCE2)
Scrum in Agile Project Management
Scrum is an iterative, incremental process used in agile software development. It defines specific roles:
- ScrumMaster: Project manager or team leader.
- Product Owner: Represents the customer’s interests.
- Team: Members executing project tasks.
- Users: End-users of the software.
- Stakeholders: Customers, vendors, and suppliers.
- Managers: Provide project resources.
- Scrum Team Size: Typically five to nine members; larger projects use a "Scrum of Scrums," scaling to hundreds of developers.
Scrum in Agile Project Management
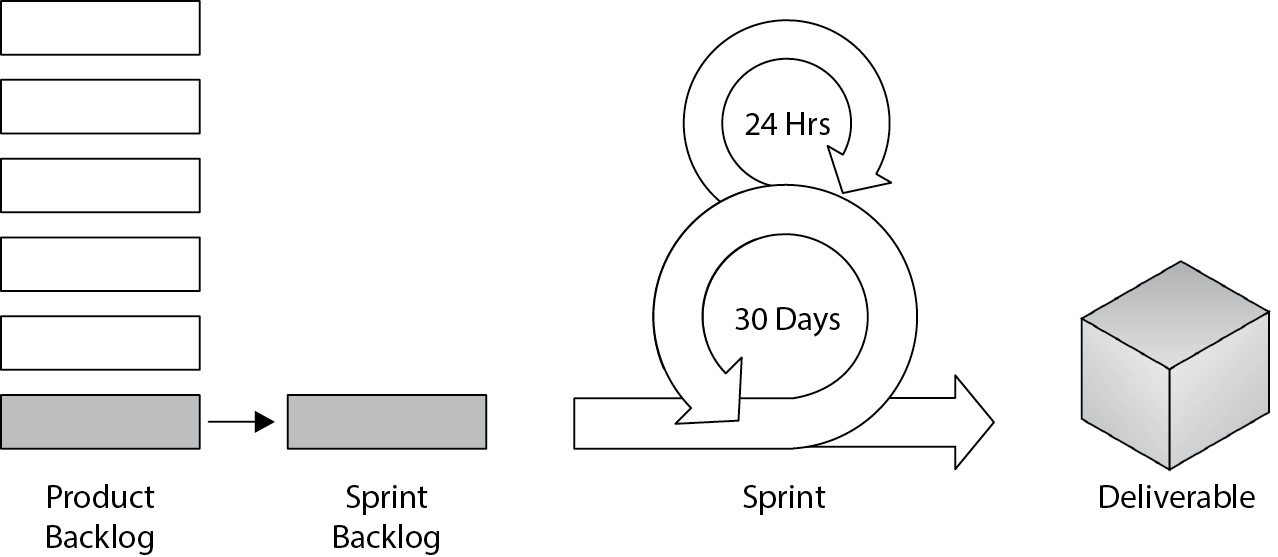
Sprint Process
SprintProcess: A sprint is a two-to-four-week effort focused on producing part of the project deliverable. Daily standup meetings (15 minutes) allow the team to address three questions:
- What was completed yesterday?
- What will be done by tomorrow?
- What obstacles exist?
- Sprint Retrospective: Held after each sprint, lasting up to four hours, to reflect on achievements and improvements.
- Documentation in Scrum:
- Product Backlog: Complete list of required features.
- Sprint Backlog: Implementation details for the current sprint.
- Burn Down Chart: Tracks remaining tasks for the sprint.
Systems Development Life Cycle (SDLC)
SDLC is a structured framework for developing, maintaining, and supporting information systems, covering software and infrastructure projects. SDLC often uses a gate process, requiring formal reviews at each phase to ensure compliance and readiness for the next phase.
PhasesofSDLC:
- Feasibility Study
- Requirements Definition 3. Design
- Development
- Testing
- Implementation
- Post-Implementation
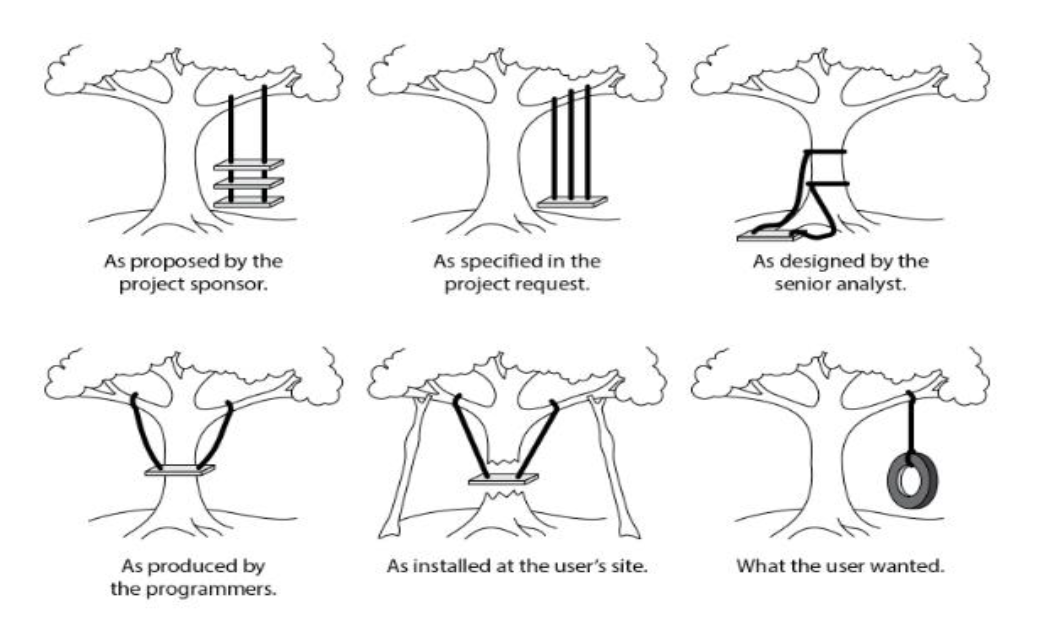
Models, Events and Triggers in SDLC
- Iterative Model: Repeats planning, design, coding, and testing until development is complete.
- Spiral Model: Adds prototyping, with repeated requirement and design phases until the design is complete.
- DevOps: Iterative development combined with operational processes, emphasizing continuous delivery.
- SDLC begins with management's decision to create or modify software based on events like:
- Market Changes: New competitors or innovations require software updates.
- Cost Shifts: Changes in operational costs necessitate software modifications.
- Regulatory Changes: Compliance with new laws drives system updates.
- Risk Changes: New vulnerabilities or threats prompt software revisions.
- Business Process Changes: Adjustments in processes require software support.
- Customer Requirements: New features requested by customers lead to software updates.
- Innovation: Organizations develop new features to gain a competitive edge.
Requirements Definition
Definition:
Requirements definition sets the foundation for new applications or modifications to existing ones. It outlines characteristics essential for functionality, performance, and compliance.
- FocusAreas:
- Business Alignment: Ensures that the system meets operational needs.
- Technical Feasibility: Confirms compatibility with current infrastructure.
- Categories of Requirements:
- Business Functional Requirements
- Technical Requirements and Standards
- Security and Regulatory Requirements
- Disaster Recovery and Business Continuity Requirements
- Privacy Requirements
- FocusAreas:
A clear requirements definition minimizes development risks, enhances user satisfaction, and ensures regulatory compliance, setting a clear path for the design and development phases within the SDLC.
Requirements Definition
Source Code Management
- Purpose of Source Code Management (SCM): SCM is vital in any software project, ensuring that code is secure, controlled, and consistently updated throughout the development process
- KeyFunctions:
- Protection: Restricts access to authorized personnel, safeguarding intellectual property and security-sensitive code.
- Version Control: Tracks changes, allowing reversion to earlier versions if issues arise. Ensures the integrity of the codebase during development.
- Recordkeeping: Maintains detailed records of modifications, aiding in accountability and troubleshooting.
- KeyFunctions:
Outsourced Development Considerations:
Organizations outsourcing development should establish clear rules about third-party access to sensitive code segments, maintaining security and compliance.
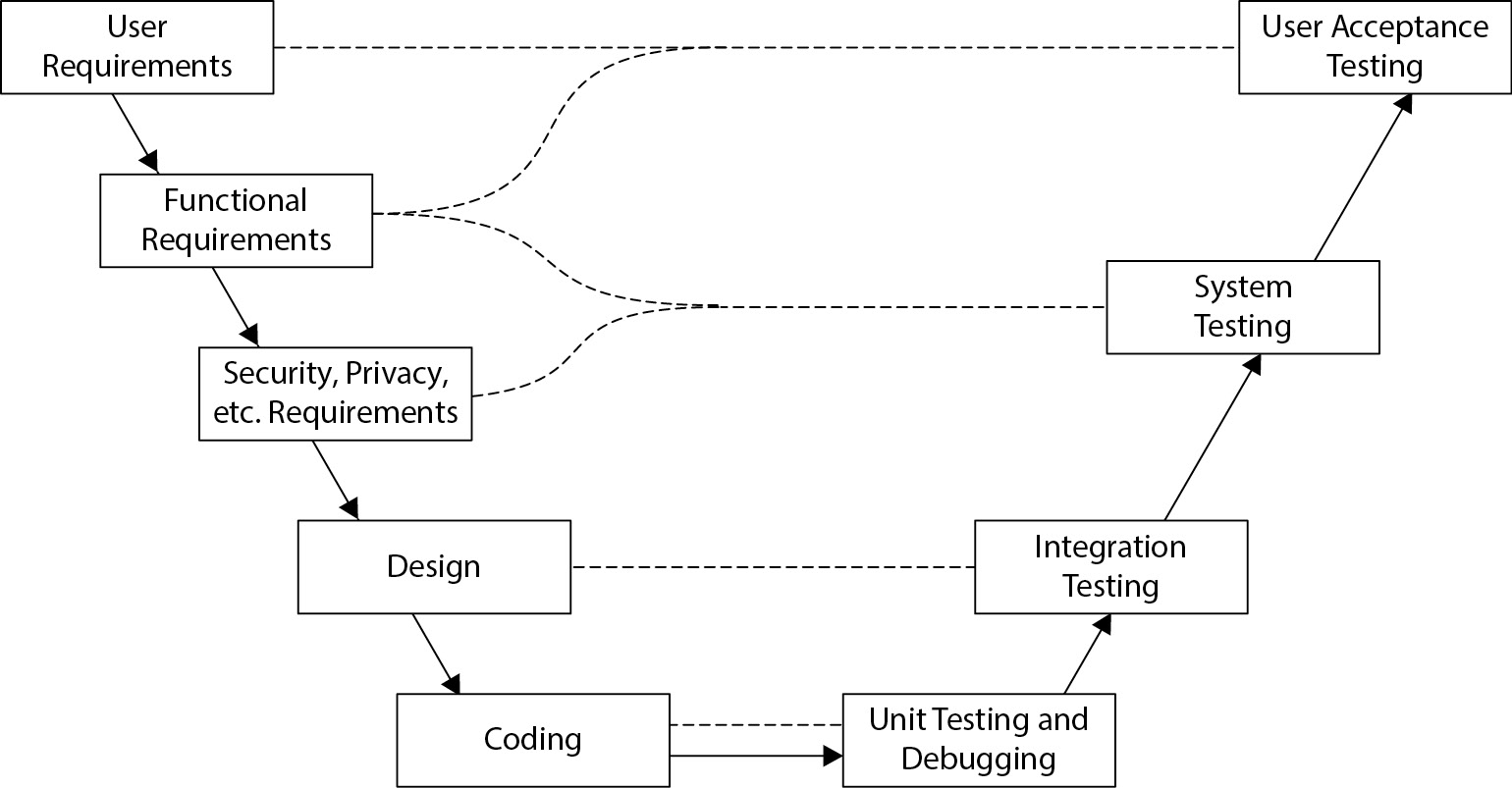
Testing in SDLC
Testing verifies the software’s adherence to requirements and ensures it meets user expectations before production. Each phase of testing addresses different aspects of software functionality and performance.
- Stages of Testing:
- Unit Testing: Conducted by developers to validate individual modules.
- System Testing: Tests integrated components to ensure end-to-end functionality.
- Functional Testing: Confirms software meets business functional requirements.
- User Acceptance Testing (UAT): Users validate that the software meets their needs.
- StructuredTestPlans: Test plans derived from requirements ensure systematic testing and repeatability, reducing errors and facilitating quality assurance.
Testing in SDLC
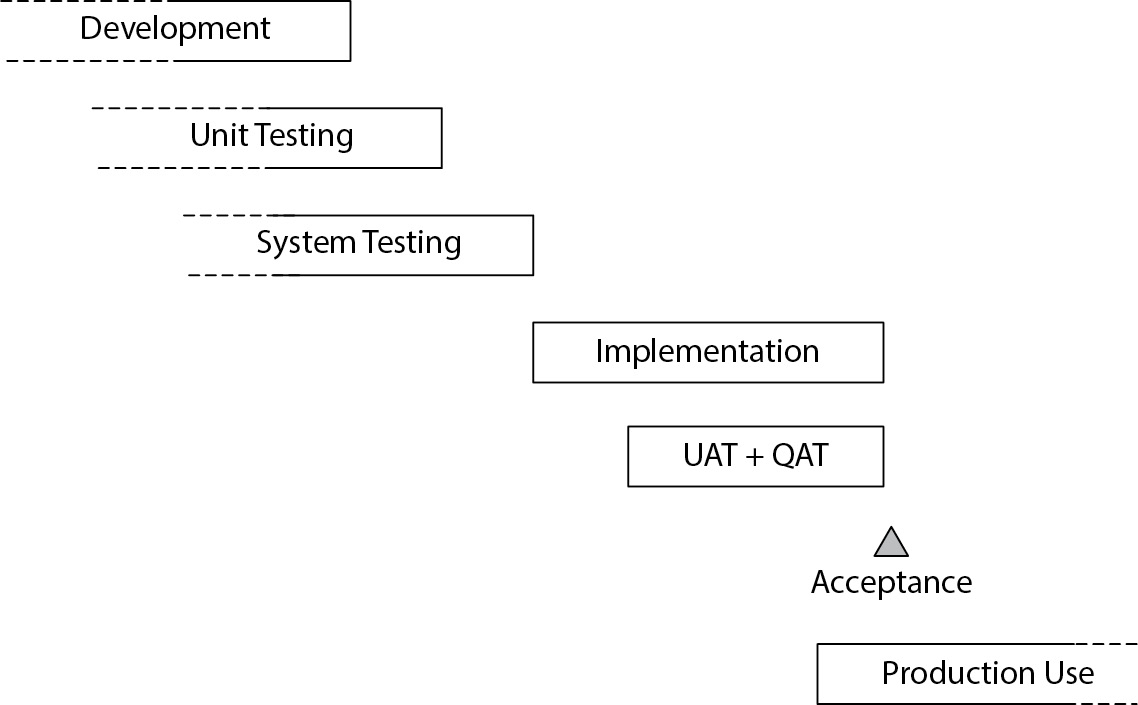
Implementation Planning
Implementation planning involves preparing the environment for the new software, building systems, and ensuring all components are ready for deployment. This phase demands strategic planning due to its complexity, as some tasks may need to begin during the development phase.
- Implementation Activities:
- Physical Space Preparation: Prepare data centers or collocation spaces for on-premises setups. Expansion may be necessary if existing space is insufficient.
- Build Production Systems: Configure servers, routers, and firewalls. For cloud-based environments, select vendors early and set up virtual machines.
- Install Application Software: Configure software, ensuring compatibility and functionality.
- Data Migration: Transfer data from legacy systems, requiring thorough testing to ensure accuracy.
Building and Configuring Systems
Building production systems is critical for ensuring a stable operating environment. It involves hardware procurement, server setup, and software configuration.
- Key Activities:
- Server Construction: For on-premises systems, organizations must build and configure physical servers. This may include procuring hardware, configuring operating systems, and setting up databases and application servers.
- Cloud Deployment: For cloud-based setups, choose a cloud vendor early and configure virtual machines on platforms like AWS or Azure. Ensure proper security configurations.
- Infrastructure Setup: Implement supporting infrastructure, including routers, switches, and firewalls, to secure the production environment.
- Outcome: A well-prepared production environment that supports stable software operations.
Cutover Strategies
Cutover is the final step in transitioning to a new system, where the organization shifts from the old system to the new one. It requires careful planning to minimize risks and ensure a smooth transition.
Types of Cutover:
- Parallel Cutover: Operate old and new systems simultaneously, comparing outputs to verify accuracy.
- Geographic Cutover: Implement changes region by region, common in retail or geographically distributed organizations.
- Module-by-Module Cutover: Migrate specific modules sequentially (e.g., accounts receivable followed by accounts payable).
- All-at-Once Cutover: Transition the entire system at once, used when downtime is minimal or low-risk.
Choose the cutover method that balances risk, efficiency, and cost-effectiveness while ensuring operational continuity.
Rollback Planning
Rollback planning is a contingency plan designed to revert to the old system if the new system fails post-cutover. It is critical for environments where system availability is vital.
- Why Rollback Planning is Essential:
- Ensures business continuity in case of critical issues in the new system.
- Protects data integrity by allowing a return to the previous environment.
- Provides a safety net during implementation, minimizing potential losses.
Rollback is considered only when the new system experiences severe failures that cannot be resolved quickly. Ensure that both systems are prepared for quick switchover and that data remains consistent throughout the process.
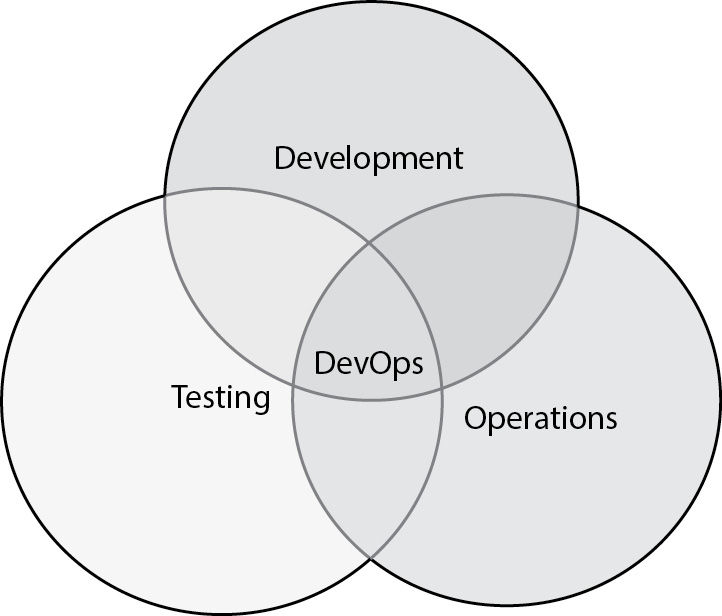
DevSecOps - Integrating Security with DevOps
What is DevSecOps?
DevSecOps integrates security into the DevOps process, ensuring that security measures are part of every stage of development, from design to deployment. Unlike traditional DevOps, which focuses primarily on speed and efficiency, DevSecOps emphasizes secure coding and automated security testing.
- Static and Dynamic Code Scanning: These tools automatically identify security vulnerabilities in the software codebase during the build process.
- Automated Security Testing: Security tests are conducted throughout the development lifecycle, including production environments.
- Remediation in Sprints: Identified vulnerabilities are fixed during subsequent development sprints, promoting faster responses to potential threats.
Benefits:
DevSecOps minimizes security risks, improves compliance, and accelerates the development of secure software by integrating security measures seamlessly.
DevSecOps - Integrating Security with DevOps
Prototyping - Building with User Feedback
Prototyping:
Prototyping is a development methodology where prototypes, or working models of the software, are quickly developed to get feedback from users. It emphasizes rapid design iterations and user involvement.
How it Works:
- User Interaction: Users provide input during the early stages, helping developers build components aligned with user expectations
- Frequent Testing: Developers create specific components rapidly and seek immediate feedback from users.
Pros and Cons:
- Advantages: Users can identify and correct issues early, minimizing the risk of incorrect approaches and costly redesigns later in development.
- Disadvantages: It may lead to incomplete systems, as certain technical or functional requirements not visible to users could be overlooked.
Rapid Application Development (RAD)
- RAD is a software development methodology emphasizing speed and flexibility, favoring small teams, prototypes, and user feedback. It responds to the limitations of slower, structured methodologies like the waterfall model.
- Small Teams: Comprising experienced developers and analysts working in tight time frames.
- Prototypes: Prototyping plays a significant role, enabling iterative improvements based on user feedback.
- Central Code Repositories: RAD projects emphasize code reuse, using repositories to maintain software components.
Benefits:
RAD accelerates development cycles and improves adaptability, making it well-suited for projects where speed is critical. However, it may lack the rigor of traditional models, leading to challenges in maintaining software quality and scalability.
System Development Types
- Data-Oriented System Development: DOSD is a data-centric software development approach where data design drives the development process. It is often used in complex environments like airline reservation systems, payment processing, and cloud-based platforms like Salesforce.
- Object-Oriented System Development: OOSD is based on the principles of object-oriented programming (OOP), where software is built using objects that represent real-world entities. It focuses on classes, objects, methods, encapsulation, inheritance, and polymorphism.
- Component-Based Development: This approach breaks down software into independent, reusable components, often located on different systems but working together as a cohesive whole using standard protocols like CORBA, RPC, or SOA.
- Web-Based Application Development: Web-based development utilizes web standards like HTML and HTTP to build software applications accessible through web browsers. It supports various development models, including agile, DevOps, RAD, DOSD, and OOSD.
- Reverse Engineering: Reverse engineering analyzes an existing system to understand its functionality, often to replicate or enhance it. It is commonly used in malware analysis and binary software analysis.
System Development Tools - IDEs and CASE
What are System Development Tools?
System development tools assist developers in writing, testing, and debugging software. Common tools include Integrated Development Environments (IDEs) and Computer-Aided Software Engineering (CASE) tools.
- IDEs:
- IDEs integrate coding, debugging, and version control within a single interface, increasing developer productivity. Examples include Eclipse, IntelliJ IDEA, and Visual Studio.
- CASE Tools:
- Upper CASE: Tools for requirements gathering and design.
- Middle CASE: Tools for detailed design and UI/UX.
- Lower CASE: Tools for code generation and testing.
- IDEs:
These tools enhance consistency, reduce development time, and improve code quality, making them essential in modern software development.
Fourth-Generation Languages (4GLs)
Fourth-generation languages (4GLs) are high-level programming tools developed to simplify software development. Unlike first- to third-generation languages, 4GLs are event-driven and less detailed, focusing on simplifying tasks such as report generation, database queries, and form design. They are often designed for use by non-technical users, making it possible for individuals with minimal programming skills to create applications.
- Characteristics:
- 4GLs are primarily adjuncts to core software functionality, aiding in reporting, querying, and high-level operations.
- They are often integrated into larger applications, enabling developers to generate code efficiently.
- Examples of 4GLs: Common 4GLs include SQL for database management, Visual Basic for Applications (VBA), and MATLAB for numerical computation, illustrating their broad range of applications.
Infrastructure Life Cycle
- DevelopmentLifeCycle: The infrastructure development life cycle is crucial for building and maintaining the systems that support applications. It follows structured processes to ensure reliability, security, and scalability.
- Phases of the Life Cycle:
- Planning: Define infrastructure requirements based on business needs, security, and regulatory compliance.
- Design: Create architectural blueprints for networks, servers, storage, and data protection measures.
- Implementation: Set up physical or virtual infrastructure components, including network configurations, security systems, and data storage solutions.
- Testing: Ensure all components function as intended, meet security standards, and support application performance.
- Maintenance: Perform regular updates, monitoring, and troubleshooting to ensure ongoing functionality. A well-managed infrastructure life cycle enhances business agility, security, and continuity.
- Phases of the Life Cycle:
Cloud vs. On-Premises Infrastructure
- Cloud-Based vs. On-Premises: The choice between cloud-based and on-premises infrastructure depends on factors like cost, control, and compliance. Both have advantages and limitations, impacting deployment strategies.
- Cloud-Based Infrastructure:
- Pros: Scalability, reduced capital expenses, and flexibility. Services are provisioned quickly, enabling rapid adaptation to changing needs.
- Cons: Limited control over physical resources, potential data residency issues, and reliance on third-party compliance.
- On-PremisesInfrastructure:
- Pros: Greater control, compliance assurance, and data proximity. Suitable for high-security environments or critical data storage.
- Cons: Higher capital investment, longer deployment cycles, and increased maintenance responsibilities.
- Cloud-Based Infrastructure:
Organizations must weigh the pros and cons based on business requirements, security standards, and cost considerations.
Security in Infrastructure Implementation
- Implementing Security Measures: Security is a primary focus during infrastructure development and implementation. It includes physical, network, system, and application layers, ensuring comprehensive protection against threats.
- SecurityElements:
- Physical Security: Data centers must have restricted access, video surveillance, and security personnel.
- Network Security: Firewalls, intrusion detection systems (IDS), and virtual private networks (VPNs) protect data traffic and communication channels.
- System Security: Operating systems and databases must have access controls, encryption, and regular patch management.
- Data Security: Encryption in transit and at rest, along with robust data loss prevention (DLP) systems, ensure data integrity and privacy.
- SecurityElements:
Outcome:
Implementing a layered security approach helps maintain confidentiality, integrity, and availability (CIA) of infrastructure components.
Cloud-Based Infrastructure - Legal & Compliance Considerations
- Using cloud-based infrastructure requires careful consideration of legal and compliance factors. Organizations must ensure that the cloud provider meets industry standards and legal requirements for data protection.
- ComplianceAreas:
- Data Privacy Laws: Understand regulations like GDPR, HIPAA, and CCPA, which mandate strict controls over personal data handling and storage.
- Data Sovereignty: The physical location of data storage affects legal rights and obligations, impacting access and protection measures.
- Compliance Audits: Regular audits ensure that cloud environments meet established legal and regulatory standards.
- ComplianceAreas:
Organizations must collaborate with legal teams and cloud providers to establish clear guidelines for data storage, access, and compliance.
Infrastructure Development - Future Trends
- TrendsinInfrastructureDevelopment: As organizations adapt to emerging technologies, infrastructure development is evolving. Key trends include:
- Edge Computing: Shifts processing closer to data sources, reducing latency and improving performance.
- Hybrid Cloud Models: Combine on-premises, private, and public cloud resources, offering a balance of control, flexibility, and scalability.
- Automation & AI: Automating infrastructure management using AI for predictive maintenance, resource optimization, and dynamic scaling.
- Security Enhancements: Zero-trust architecture and AI-driven threat detection are becoming essential for proactive infrastructure security.
- Sustainability: Energy-efficient infrastructure, green data centers, and cloud optimization contribute to reduced carbon footprints.
Application Controls Overview
- Need for Controls:
- Applicationsaccept,process,store,andtransmitinformation,makingcontrolsessentialtomaintaindataintegrity.
- Controls are implemented at three stages: input, processing, and output.
- Input Controls: Ensure that only valid data enters the system, protecting against errors or unauthorized data entry.
- Processing Controls: Verify that data is correctly processed, preventing data manipulation or processing errors.
- OutputControls: Ensure that data output is accurate and accessible only to authorized users,maintaining confidentiality and integrity.
- TypesofApplicationControls:
- Preventive Controls: Aim to stop errors or unauthorized access before they occur. Examples include input validation and user access controls.
- Detective Controls: Identify errors or irregularities during processing, such as audit logs or monitoring systems.
- Corrective Controls: Focus on restoring systems or correcting errors post-detection. Examples include rollback procedures and error correction processes.
Effective application control implementation requires a holistic approach, integrating all three control types to ensure comprehensive data protection across the application lifecycle.
Overview of Input Controls
- Input Controls Definition:
- Input controls ensure that data presented to an application for processing is authorized, reasonable, complete, and maintains integrity.
- These controls protect applications from erroneous data,unauthorized input,and potential security breaches.
- Input controls involve implementing various techniques to validate and authorize data before it is accepted by the system.
- Input authorization and validation are critical to maintaining data integrity at the entry point, preventing errors and unauthorized transactions from affecting processing and output.
Input Authorization Techniques
- User Access Controls:
- Only approved users such as system operators, input clerks, and analysts are permitted to log in and access applications. Each user must have unique login credentials.
- Entity Access Controls:
- Only authorized entities within organizations are permitted access. This includes service accounts and hosts, all requiring unique login credentials.
- Workstation Identification:
- Only approved workstations can be used for transactions, verified through electronic serial numbers, network addresses, or digital certificates.
- Approved Transactions & Batches:
- Transactions must be approved through manual signatures, online checks, or other methods before processing.
- Source Documents:
- Data is often input only from controlled source documents, like invoices, checks, or customer forms, ensuring data accuracy and integrity.
Input Validation Types and Techniques
- Type Checking:
- Ensures each input field accepts only the appropriate type of data (e.g., numeric fields accept only digits).
- Range & Value Checking:
- Validates that input values fall within acceptable ranges (e.g., dates, postal codes, telephone numbers).
- Existence Checks:
- Confirms that each required field contains data before proceeding with processing.
- Consistency Checks:
- Compares related fields to ensure data matches expected values (e.g., ZIP code matching city and state).
- Length Validation:
- Limits the number of characters in fields to prevent issues like buffer overflow attacks.
- Check Digits & Hash Totals:
- Verifies numeric values for integrity by recalculating check digits or hash totals.
Error Handling in Software Applications
- Need of Error Handling:
- When input validation fails, software applications need to handle errors effectively. Error handling ensures that invalid data does not proceed further into the system.
- Proper error handling helps in identifying and logging errors, making it easier for analysts to understand what went wrong and where.
- This process includes error rejection methods like batch rejection, transaction rejection, suspending batches, or requesting data re-input.
- Applications must generate error logs or reports detailing rejected input to prevent misinterpretation and aid in troubleshooting.
- Without detailed error records, analysts may mistakenly assume successful data input, complicating future error resolution.
Batch and Transaction Rejection
- Batch Rejection:
- If batch totals do not align with expected values, the entire batch is rejected. This action allows analysts to review and resolve batch discrepancies.
- Applications usually lack the capacity to identify specific batch issues; hence, rejecting the batch is the safest measure.
- TransactionRejection:
- Individual transactions that fail validation checks are rejected to prevent corrupt data from entering the system.
Both types of rejection ensure data accuracy and maintain system integrity.
- Hold in Suspense:
- If issues arise, entire batches are held in suspense to allow corrections before reprocessing.
- Request for Re-input:
- Users may be prompted to re-enter data if specific fields are flagged as incorrect during validation checks.
Ensuring Accuracy, Security and Integrity
- Run-to-Run Totals: These totals confirm that data retains accuracy through transaction steps, preventing tampering or errors.
- Limit Checking: Calculation results exceeding set limits are rejected, maintaining consistency within the system.
- Batch Totals: Recalculating totals at the end of batch processing ensures that the integrity of batch data is maintained.
- Hash Values: Hashing is used to verify data sets at various processing stages, detecting any tampering or alterations.
- Manual Recalculation & Reconciliation: Analysts manually recalculate key transactions to confirm data correctness, comparing old and new data sets to verify consistency.
- Data File & Database Security: Access controls restrict data file and database access to authorized users only, protecting data from unauthorized access.
- Error Handling: Transactions requiring re-entry are reviewed by personnel other than those who initially entered the data.
- File Versioning & Labeling: Version verification prevents accidental processing of outdated files, and labeling ensures correct media usage.
- Source File Retention & Transaction Logs: Source files and logs are retained to support troubleshooting or reprocessing weeks or months after the initial input, enhancing system reliability.
Output Controls in Applications
- Output Controls:
- Output controls verify the accuracy and validity of final calculations or data transformations.
- HandlingSpecialForms:
- Forms like checks, invoices, or certificates must be serialized, securely stored, and logged to prevent unauthorized use.
- ReportDistribution:
- Printed reports require secure handling, such as tamper-proof envelopes, while electronic reports need encryption and password protection during transmission and storage.
- Output Reconciliation:
- Reconciliation checks ensure that numeric or financial data matches input data, intermediate calculations, or control totals, verifying data integrity.
Auditing the Systems Development Life Cycle (SDLC)
- Auditing SDLC:
- Auditing the SDLC helps organizations understand the effectiveness of processes used to create and maintain software.
- Without examining development processes, root causes of recurring issues in applications may remain unknown.
- IS auditors provide insights to improve software development by examining not just the applications and controls, but also the methods and techniques used in development.
- Auditing SDLC enables organizations to identify process inefficiencies, support compliance, and improve software quality.
- Auditors must focus on the documentation and validation mechanisms for each development phase, as exam questions often emphasize design, requirements, and implementation audit details.
Auditing Program and Project Management
- Audit Activities:
- IS auditors assess whether projects are managed effectively, ensuring they align with organizational objectives and management's requirements.
- Critical aspects include senior management oversight, risk management techniques, project planning methodologies, issue resolution strategies, cost management, status reporting, change control, and recordkeeping.
- Proper controls in project management confirm that systems support business processes as intended, verifying project feasibility and outcome alignment.
- IS auditors review how steering committees influence decisions, the robustness of risk management, and the adequacy of project documentation for accountability.
- Auditing project management provides assurance that resources are used effectively and that systems fulfill intended functions.
Auditing the Feasibility Study
Feasibility Audit Focus:
- IS auditors evaluate feasibility studies to confirm that project initiation is based on sound analysis and rationale.
- They assess budgets,cost justifications,and the project's criticality to business operations, ensuring costs can be independently verified.
- Auditors examine alternatives considered, such as reusing existing systems, to ensure a reasonable solution is chosen.
- Auditing feasibility ensures that projects proceed with clear business benefits, minimizing risks related to incorrect solution selection or resource wastage.
- IS auditors ensure feasibility studies are comprehensive, involving stakeholder analysis, cost-benefit comparisons, and risk assessments.
Auditing Requirements Development
- Requirements Audit Scope:
- IS auditors verify the development of project requirements, ensuring all stakeholders contribute accurately and their inputs are represented.
- Auditors identify contributors to requirements and ensure their inputs were considered without unauthorized alterations.
- Reasonableness checks confirm that requirements align with feasibility study findings and that final requirements receive management approval.
- Effective requirements auditing prevents the inclusion of ambiguous or conflicting requirements, ensuring that the resulting system aligns with organizational needs.
- Properly defined and validated requirements are key to project success, minimizing redesign and rework in later phases.
Auditing the Design Phase
- Design Audit Activities:
- IS auditors examine whether the design phase accurately translates requirements into detailed specifications that support development.
- They check whether the design aligns with feasibility study outcomes, contains necessary details for developers, and meets business needs.
- Auditors review design approvals, ensuring management involvement and validation.
- Testing and user acceptance testing (UAT) plans should be defined during this phase to ensure readiness for development and implementation.
- Design audits help ensure that software development starts on a solid foundation, reducing implementation issues and increasing user satisfaction.
Auditing Software Acquisition
- Acquisition Audit Focus:
- IS auditors assess software acquisition, verifying whether a formal RFP or RFI process was conducted and requirements were included in vendor documents.
- They ensure vendor selection aligns with requirements and that references, evaluations, or pilots were completed before purchase.
- Contracts must contain protection clauses for the organization, and legal review is essential before signing.
- Proper auditing of software acquisition helps prevent mismatches between organizational needs and vendor offerings, ensuring system functionality and support.
- Auditors ensure that procurement aligns with compliance requirements and that vendor performance meets contractual terms.
Auditing Software Testing
- TestingAuditFocus:
- IS auditors verify whether test plans were developed during requirements and design phases, covering all elements of design and requirements.
- Auditors check whether all tests were completed successfully, test results were archived, and testers can be contacted for clarification.
- Parallel testing and UAT are critical parts of testing audits, ensuring software functions as intended before implementation.
- Effective auditing of testing minimizes risks of errors or failures during implementation, ensuring systems are robust and meet user needs.
- Test result documentation provides evidence for compliance and performance assessments in later stages.
Auditing Business Controls
- Overview of Business Controls:
- Business controls are critical checkpoints within business processes that ensure key activities are executed correctly.
- IS auditors identify key processes and controls, focusing on both automated IT controls and manual process-based controls.
- Auditors must consider a holistic process perspective, as personnel are responsible for monitoring, managing, and documenting processes.
- Documentation is crucial as a control itself,ensuring clear guidance and traceability of business operations.
- IS auditors must verify that processes are aligned with business objectives, with controls supporting overall integrity.
Auditing Application Controls
- ApplicationControlsScope:
- Auditors ensure that valid data enters the system (input controls), calculations are correct (processing controls), and output data is accurate (output controls).
- Transaction flow audits trace data from input through processing to output, ensuring data integrity and authorized changes.
- Observations during audits focus on segregation of duties, input validation, authorization, error handling, and report controls.
- Data integrity tests involve entering invalid data and testing for proper rejection or error handling by the application.
- Auditing ensures that applications maintain data accuracy and fulfill organizational requirements.
Testing Online Processing Systems
- EnsuringDataIntegrityinOnlineSystems:
- Online systems must maintain record locking and handle user conflicts effectively, preventing unauthorized data changes.
- IS auditors test application logic for atomicity, ensuring transactions are completed as a whole or not at all.
- Examples of audit tests:
- Two users attempting simultaneous updates on the same record.
- Concurrent record deletion and updating attempts.
- Parent-child relationships in databases tested for integrity under stress conditions.
- Auditors assess how the application manages simultaneous access to business records, ensuring data consistency.
Continuous Auditing Techniques
- OnlineAuditingMethods:
- Audit Hooks: Embedded modules that trigger alerts for specific conditions.
- SCARF/EAM: Independent log creation for continuous audit checks.
- Integrated Test Facility (ITF): Allows test transactions within live environments, isolating test data.
- Continuous and Intermittent Simulation(CIS): Parallel processing of transactions to compare outcomes.
- Snapshots: Capturing key transaction data for later review.
- Online Inquiry: Direct querying of transactions for detailed audits.
Continuous auditing minimizes business disruption while providing real-time insights into application performance.
Auditing Third-Party Risk Management
- Auditing Third-Party Processes:
- Completeness of Third-Party Population: Auditors verify that all third parties are represented in risk management programs.
- Risk Criteria Review: Evaluation of risk criteria to ensure comprehensive coverage of potential third-party risks.
- Legal Agreements: Review contract language for adequate security controls and obligations.
- Classification Verification: Check whether third parties are correctly tiered based on risk.
- Questionnaire Evaluation: Analyze the contents,responses,and processing of third-party questionnaires to ensure thorough risk assessment.
Summary
- Strategic Alignment: Ensures business operations meet set objectives through strategic planning, process, and systems development.
- Project Management: Guides resources, sets objectives, manages schedules, roles, and change, ensuring successful project outcomes.
- SDLC Implementation: Focuses on software creation, implementation, and maintenance, driving continual improvement across phases.
- Infrastructure Development: Mirrors SDLC, ensuring seamless application access and supporting business requirements.
- Business Process Life Cycle (BPLC) & Reengineering: Enhances process creation and improvement, supported by benchmarking and maturity models.
- Application Controls: Enforces data integrity through input, process, and output controls, ensuring secure and accurate system operation.
- Auditing Controls & Alignment: Validates system alignment with business and regulatory standards through lifecycle audits and computer-aided audit techniques (CAATs).
Question
- What testing activities should developers perform during the development phase?
- Security testing
- Integration testing
- Unit testing
- Developers should not perform any testing
- The purpose of input validation checking is to
- Ensure that input values are within acceptable ranges.
- Ensure that input data contains the correct type of characters.
- Ensure that input data is free of hostile or harmful content.
- Ensure all of the above.
- A software developer has informed the project manager that a portion of the application development is going to take five additional days to complete. The project manager should
- Inform the other project participants of the schedule change.
- Change the project schedule to reflect the new completion time.
- Create a project change request.
- Adjust the resource budget to account for the schedule change.
- A global organization is planning the migration of a business process to a new application. What cutover methods can be considered?
- Parallel, geographic, module by module, or all at once
- Parallel, geographic, or module by module
- Parallel, module by module, or all at once
- Parallel, geographic, or all at once
- The reason that functional requirements need to be measurable is
- Developers need to know how to test functional requirements
- Functional tests are derived directly from functional requirements
- To verify correct system operation
- To measure system performance
