CYB306 Class Discussion-5
Think-Pair-Share on "An Intelligent Edge-Cloud Collaborative Framework for Communication Security in Distributed Cyber-Physical Systems"
Objectives:
- Foster collaboration and critical thinking by engaging students with advanced concepts in edge-cloud frameworks and cybersecurity.
- Encourage peer-to-peer learning and discussion to deepen understanding of the paper's key contributions and challenges.
Instructions:
Part 1: Pre-Reading (Individual Work)
Assignment of Roles: Each group of 6 students will have these roles:
- Summarizer (1): Summarize the key contributions of the paper.
- Concept Analyzer (2): Analyze the technical concepts (e.g., edge-cloud collaboration, distributed systems, and communication security).
- Challenge Identifier (1): Identify challenges and limitations mentioned in the paper.
- Application Thinker (1): Suggest potential real-world applications for the proposed framework.
- Question Creator (1): Develop two thought-provoking questions to guide group discussions.
Read and Take Notes:
Each student reads the paper and prepares notes focusing on their assigned role.
Part 2: Think (Individual Reflection)
Spend 10 minutes reflecting on the following:
- What are the paper's primary objectives?
- How does the proposed edge-cloud framework address communication security in distributed systems?
- How does the proposed solution compare with traditional security approaches?
Part 3: Pair (Small Group Discussions)
- Form pairs within your group (3 pairs per group). Each pair discusses for 15 minutes:
- Their understanding of the framework and its importance.
- Insights from their individual roles and any differing perspectives.
- Any questions or unclear points that need further clarification.
Part 4: Share (Group Collaboration)
Reassemble in your group of six. Each pair summarizes its discussion in 5 minutes.
As a group, spend 20 minutes to:
- Combine insights into a cohesive understanding of the paper.
- Answer the two questions created by the Question Creator.
- Discuss real-world examples of distributed cyber-physical systems and how the proposed framework could improve their security.
Deliverables (Post-Activity)
Group Summary Document (to be submitted by each group): A one-page summary of the paper focusing on:
- Main contributions.
- Key technical concepts.
- Challenges and limitations.
- Real-world applications.
- Responses to the two thought-provoking questions.
Presentation (5 minutes per group):
- Briefly present the group's understanding and discussion outcomes. Highlight unique perspectives or innovative applications proposed during discussions.
Evaluation Criteria
Criteria Points
- Depth of Understanding 20
- Team Collaboration 20
- Original Insights 20
- Quality of Deliverables 20
- Presentation Clarity 20
Total: 100 Points
An Intelligent Edge-Cloud Collaborative Framework for Communication Security in Distributed Cyber-Physical Systems
Abstract
The rapid growth of IoT (Internet of Things) and smart services facilitate many CPS (Cyber-Physical Systems) such as smart health, smart grid and so on. Nevertheless, the communication security issues in CPS are becoming more and more important with the growing complexity of the CPS network and the increasing dependency of critical network infrastructure on cyber-based technologies. In recent years, deep learning technology has shown its superiority in detecting communication security attacks, but its high computational complexity and the massive amount of data generated by IoT devices have brought challenges to traditional cloud computing technology in terms of bandwidth and computing resources. In this paper, we have analyzed the characteristics of heterogeneity and hierarchy in attacks on CPS. We have also analyzed the role of edge intelligence in handling the security of large-scale data commu-nication in CPS. Furthermore, we proposed a CPS communication attack detection framework based on edge cloud collaboration, aiming to improve the parallel efficiency of hardware resources when executing detection tasks. We aim to enhance the intelligence of physical devices and the degree of cloud collaboration, satisfying the real-time processing requirements of large-scale, hierarchical CPS attack detection. Furthermore, through simple simulation experiments, we verified the effectiveness of the proposed edge cloud collabo-ration framework in CPS attack detection.
Introduction
With the rapid growth of IoT (Internet of Things) and smart services, many CPS (Cyber-Physical Systems) such as smart health, smart grid, smart industry and smart transportation are being developed in the market [11]. The growing complexity of the CPS network and the increasing dependency of critical network infrastructure on cyber-based technologies have made them vulnerable to attacks towards the communication channels in various domains of CPS [8]. Figure 1 illustrates a typical architecture of CPS, which contains the physical domain, cyber-domain, and the system domain. The inter- and intra-domain communication networks are vulnerable to various kinds of attacks. Therefore, the communication security of CPS has become a critical concern. Recently, deep learning (DL) has achieved great success in various domains including security-related applications, such as intrusion detection, malware detection, access control, anomaly detection, and classifications, and shows great potential for communication security in CPS [10].
Detecting and preventing attacks in a timely manner is significant to reduce the losses. However, with the more affordable sensors, better data acquisition systems, and faster communication networks in the CPS, the growing connected physical facilities are continuously generating large amounts of data to process, such as environmental monitoring, mobile health systems, intelligent transportation systems, and so on. The volume, velocity, variety, and veracity of data of CPS propose new challenges for the attack detection system of CPS, such as computation power, and network bandwidth, to provide real-time attack detection.
The conventional method often resorts to cloud computing with center servers to host the computation-intensive deep learning models for threat detection. However, these cloud-only approaches put great computation and band-width pressure on the cloud servers and the communication network. The system throughput will become the bottleneck for providing real-time detection. In addition, weekly or monthly security analysis reports will not be sufficient to detect and mitigate the attacks that may exist at every time when CPS is dealing with large amounts of data.
Recently, distributed cloud computing techniques, especially edge computing, offer excellent potential as a new computing solution to address these real-time attack detection problems in CPS. Edge computing extends the cloud computing paradigm to the network edge. The close-to-physical edge devices can bridge the gap between physical devices and the cloud, and collectively perform real-time compute-intensive applications directly at the network edge.
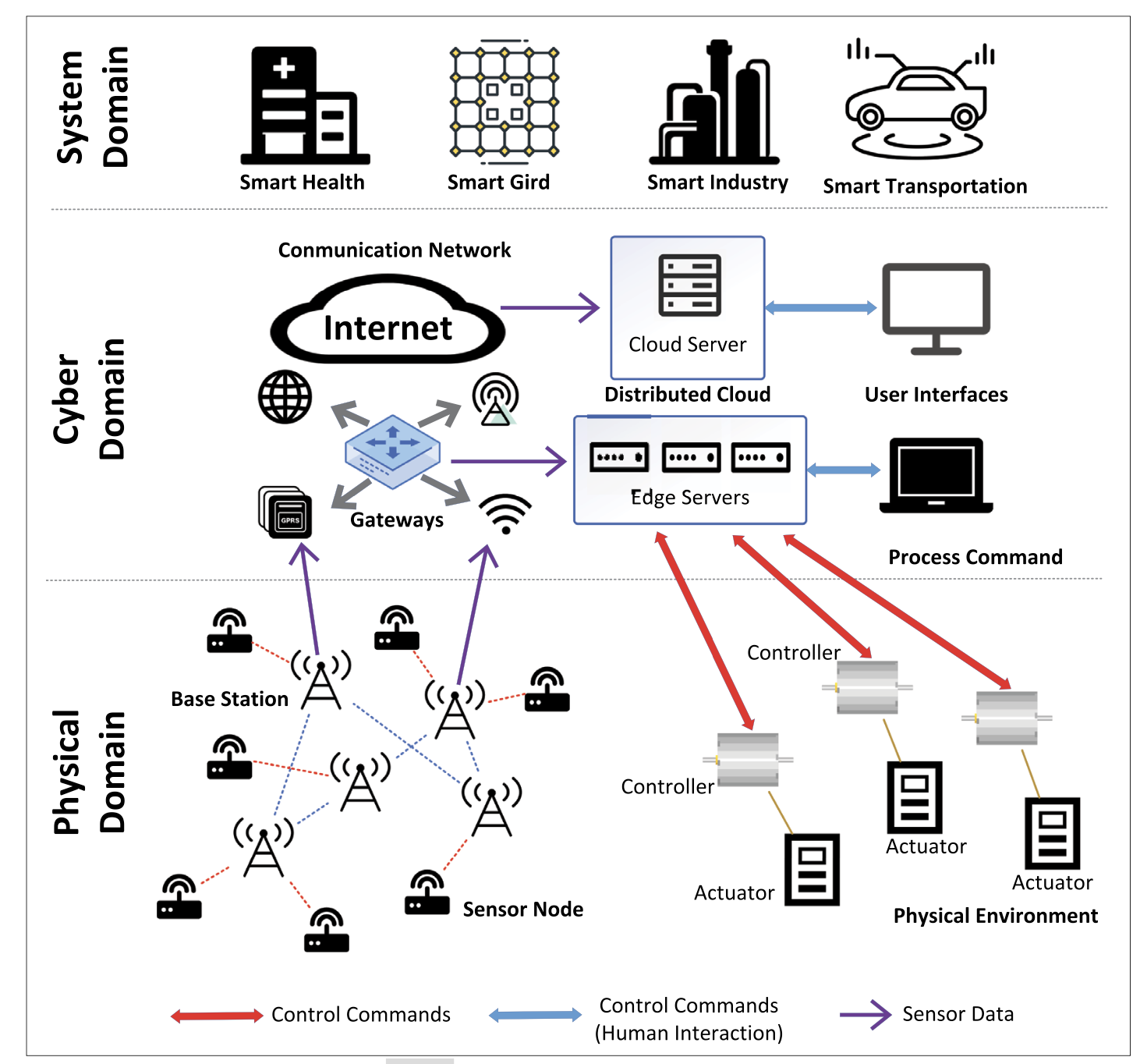
FIGURE 1. Communication security is critical for cyber-physical system with complex network infrastructure.
Recently, distributed cloud computing techniques, especially edge computing, offer excellent potential as a new computing solution to address these real-time attack detection problems in CPS.
Nevertheless, deploying efficient attack detection methods with edge-cloud collaborative intelligence is still a big challenge for the following 3 reasons: (i) Data Volume and Com-putational Complexity. The amount of data generated by the physical devices and the network is huge, while AI algorithms such as deep learning have large computational requirements. (ii) Task Heterogeneity and Hierarchical Attribute of Attack Detection. In CPS, different domains face diverse attacks, requiring multiple deep learning models. The hierarchical attack detection process uses lower domain models’ results or extracted features to detect attacks in upper domains, adding complexity to designing effective detection strategies. (iii) Inefficiency of co-processing of big data and deep learning platforms. The current mainstream in-memory computing platforms for big data (e.g., Spark and Flink) currently only run on CPUs, and prevent powerful GPU resources from being utilized for big data processing with DL. Meanwhile, DL platforms such as TensorFlow and MxNet are not welldocked with big data platforms and do not support edge-cloud collaborative computing to cope well with large-scale CPS attack detection.
In this paper, we explore edge intelligence’s potential in processing large-scale data for communication security in CPS. We propose a robust, scalable edge-cloud collaborative framework for attack detection that incorporates edge-cloud collaborative parallel processing. This design emphasizes user-friendliness, cloud-edge collaboration, reliability, and load balancing. We address the challenge (i) by proposing a hierarchical architecture where edge server clusters first process raw data before it reaches the cloud, which reduces bandwidth and computational load on cloud servers and improves real-time attack detection. In response to challenge (ii), we allow the cloud center to maintain a global view of all edge server clusters. This global perspective can be used for detecting specific global attacks and effectively utilizing the detection results from edge servers of lower layers. To overcome the challenge (iii), we devise a distributed memory architecture and a communication adaptation technology to facilitate efficient GPU acceleration for data processing and ensure effective large-scale CPS attack detection. With this proposed framework, we aim to improve the parallel efficiency of hardware resources, promote the intelligence of physical devices, enhance cloud-edge collaboration, and enable realtime processing of large-scale and hierarchical CPS attack detection.
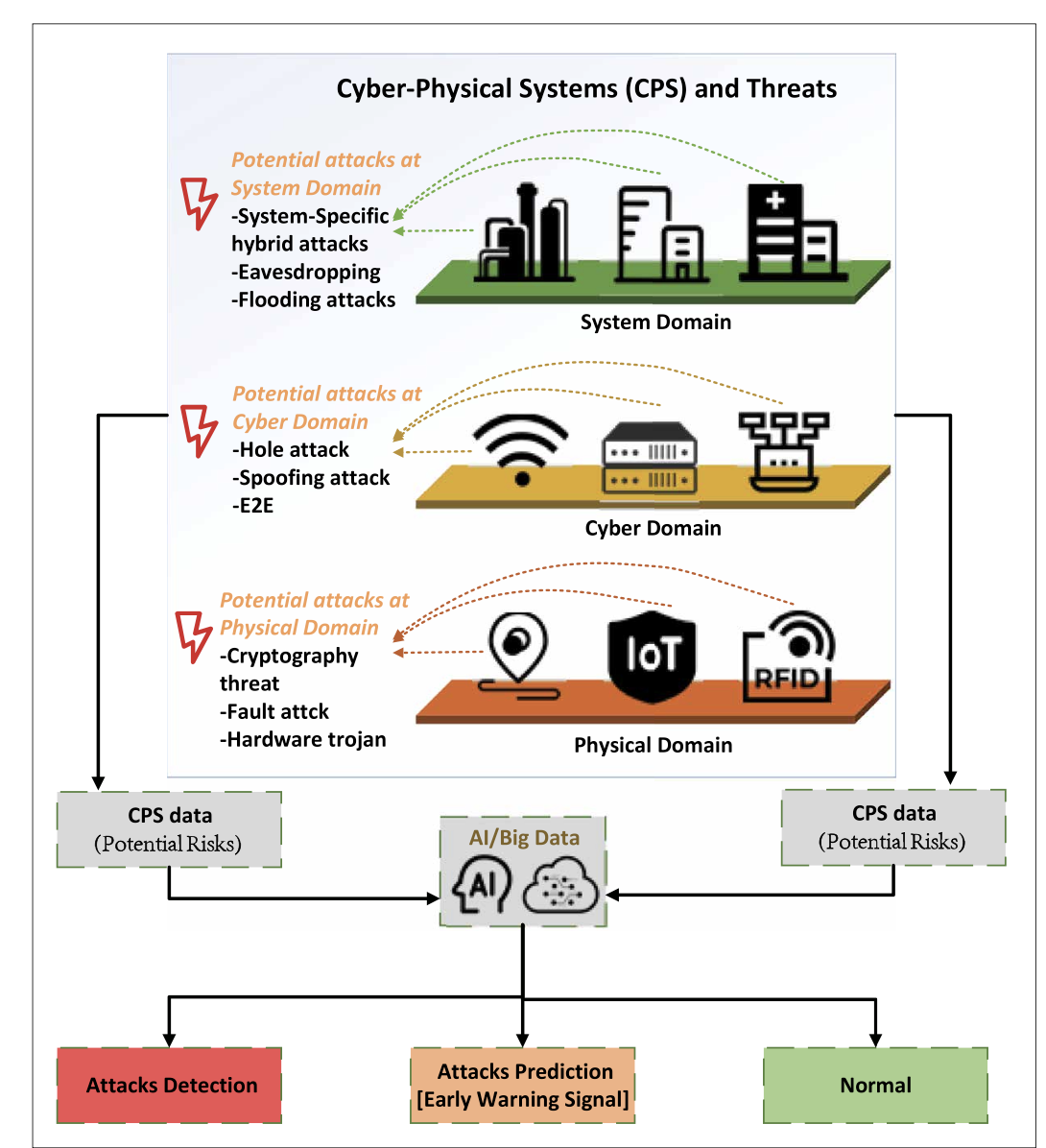
FIGURE 2. Illustration of the potential attacks towards various domains of CPS and the role of ML/DL and big data in CPS communication security.
Communication Security in CPS and its Detection Methods
Overview of CPS
Cyber-Physical System (CPS) is a complex system that combines different cyber and physical systems. It is a completely new technology that merges real-world physical and cyber spaces. The cyber environment in CPS represents a digital environment created by a computer program that creates a world to compute, communicate and manage while the physical environment of CPS runs with various sensors and the Internet of Things (IoT). The reliance on CPS for various applications such as in the transportation, energy, medical, and manufacturing sectors is gradually increasing.
As shown in Fig. 1, there are three domains in the CPS: the physical domain, the cyber domain, and the system domain [7] (i) The physical domain aims at recognizing the world, which usually consists of GPS, sensors, actuators, cameras, and IoT. These devices can also collect various kinds of data from the real world. (ii) The cyber domain takes charge of the data processing and exchange between sensors and communication applications. The communication technologies used in this domain include wired (e.g., LAN, WAN) [12], network devices (e.g., switches, routers), and wireless (e.g., Bluetooth, ZigBee, WiFi, 4G, and 5G). (iii) The system domain processes various information uploaded from the cyber domain, specifically including instructions for the operation of various physical sensors and actuators. There are various applications in the system domain, such as smart grid, smart health, smart industry, and smart transportation.
Why Communication Security is Important in CPS
As CPS technology evolves, the security risks become greater and cannot be ignored. Threats and vulnerabilities in the complex interactions in CPS are becoming a new security concern and are difficult to assess [9]. Carreras Guzman et al.[2] underscores that the CPS system confronts not merely the unpredicted malfunctions of conventional constituents, but also involves complex interactions and security susceptibilities, such as Stuxnet offensives and the like. This complexity, along with the heterogeneity of CPS components, makes it difficult to ensure the security and privacy of CPS. Also, targeted attacks on multiple components of the CPS are difficult to identify, track, and inspect. Such security issues can shake the foundation of CPS and pose a great threat to real-world life. Therefore, it is necessary to study CPS security issues in depth and detect these vulnerabilities, threats, and attacks in a timely manner.
Figure 2 summarizes the security threats that can cause serious damage against the different domains of the CPS, each of which can be attacked manually or actively. Threats to the physical domain include attacks on the physical environment, such as sensors, actuators, and the Internet of Things; threats to the cyber domain include threats to data, data corruption, and system communications; while threats to the system domain can be a hybrid attack against multiple communication networks in the CPS.
Deep Learning Based Methods for Security in CPS
CPS-related security issues have become a new research hotspot while researchers focus on deep learning-based intrusion detection schemes. Deep learning (DL) provides a deep extension to traditional artificial neural networks (ANNs). Deep neural networks (DNNs) consist of a stacked set of models (layers) that learn a series of hidden representations in a hierarchical manner. The higher-level representations contain important features that amplify the input samples while discriminating and suppressing irrelevant features. Deep learning models have achieved state-of-the-art performance for many tasks, including object detection, pattern recognition, speech recognition, and natural language processing [13].
Sensor data and network data in the CPS are usually high and large-scale, and DL models are very effective in analyzing large-scale and high-dimensional data. Deep learning is mainly divided into supervised learning, unsupervised learning, and fusion of the two types of learning called hybrid DL. CNNs and recurrent neural networks(RNNs) are typical supervised learning methods. Deep autoencoders (AEs), deep belief nets(DBNs), restricted Boltzmann machines (RBMs), and generative adversarial networks (GANs) are typical unsupervised learning methods or hybrid DL methods. Table I shows potential DL methods for securing CPS. Despite the significant advantages of deep learning techniques in security detection, the practical deployment process necessitates the consideration of dynamic load adjustment, voluminous data flux, network communication, and dynamic task scheduling.
DePLoying Deep Learning Based Methods for Communication Security in CPS: ChALLenges and OPPortunities
CPS Generates Big Data With PotentIAL Attacks
With more and cheaper sensors, better data collection systems, and faster and more sophisticated communication networks in CPS, the increasing number of interconnected physical facilities, these devices and networks continue to generate large amounts of data, called Big Data [15]. The risk of attacks implied in CPS Big Data has become more difficult to detect. In addition, weekly or monthly security analysis reports will not be sufficient to detect and mitigate the attacks that may exist at every time when CPS is dealing with large amounts of data.
In this situation, big data technologies would be able to handle the challenges of the volume, velocity, variety, and veracity of the data. The existing big data and deep learning platforms provide potential power in dealing with the big data in CPS.
Spark. It is developed as a unified model for distributed big data processing. Spark extends the MapReduce model with data sharing abstraction called Resilient Distributed Dataset (RDD) which are cached in the memory of the cluster.
TensorFlow. It is an open-source end-to-end platform for creating Machine Learning and Deep Learning applications. It is a symbolic math library that uses dataflow and differentiable programming to perform various tasks focused on training and inference of deep neural networks.
Edge Computing Provides Close-to-PhysicAL Computation Power in CPS
Cloud computing extends the computing and storage capabilities of CPS and becomes a new technology called Cyber-Physical and Cloud Systems (CPCS). However, CPCS faces numerous important challenges. First, cloud computing can neither directly manage CPS devices nor meet the real-time requirements. Second, there are communication bottlenecks between the CPS and the cloud. Third, new security challenges are required to be overcome to accelerate the development of these integrated applications. Recently, edge computing [5] is a promising new technology to address these challenges. It extends the cloud computing paradigm to the edge of the network. Smart computing and storage for edge devices offer the possibility to tackle communication problems, real-time problems, and security problems.
DePLoying Efficient At tack Detection Methods With Edge-Cloud InteLLIgence in CPSs: ChALLenges and Solutions
| Methods | Working Principle | Application in CPS Communication Security |
|---|---|---|
| CNNs | CNNs mainly aim to reduce data parameters used by applying parameter sharing, sparse interactions, and equivariant representations. | CNNs can automatically learn features of raw security data; therefore, they can construct an end-to-end security model for CPS [10]. |
| RNNs | RNNs integrate a temporal layer to take sequential data and then learn multi-faceted variations with the hidden unit of the recurrent cell. | RNNs can classify network traffic with high accuracy in detecting malicious behavior [14] and show considerable potential in improving CPS security, specifically for time series-based threats. |
| AEs | An AE neural network is divided into two parts: The encoder obtains the input and converts it into a feature. The decoder learns to rebuild the original input from it. | AEs can be used for detecting malware or intrusion [4]. |
| GANs | The generative model learns the data distribution and generates data samples, and the discriminative model predicts the possibility of whether the generated samples are true. | GAN can enhance the system's ability to detect attacks by generating fake attack data [6]. |
| RBMs | RBMs are deep generative models developed for unsupervised learning. They are completely undirected models with no link between any two nodes in the same layer. | RBMs can be used for DDoS attack detection [1]. |
| DBNs | DBNs are composed of stacked RBMs that perform greedy layer-wise training to accomplish robust performance. | DBNs can be used for network anomaly detection [3]. |
TABLE 1. Potential DL methods for securing IoT systems.
The deployment of efficient attack detection methods in Cyber-Physical Systems (CPS) using edge-cloud intelligence presents a significant challenge. Edge computing offloads lightweight computing and real-time tasks to edge servers located near the data source. The cloud, on the other hand, manages intelligent computing tasks that demand high computational resources and complexity. Despite the potential of edge-cloud collaborative intelligence in resolving issues related to network bandwidth, computational load on the cloud, and real-time performance, its application in large-scale and hierarchical CPS attack detection still faces several obstacles. These challenges are detailed as follows:
- Data Volume and Computational Complexity. CPS involves massive amounts of data generated by physical devices and the network. Simultaneously, AI algorithms, such as deep learning, require substantial computational resources. These conditions create an environment where communication-intensive and computation-intensive tasks coexist. This coexistence puts significant pressure on network bandwidth and computational resources when conducting large-scale attack detection tasks in CPS.
- Task Heterogeneity and Hierarchical Attribute of Attack Detection. In CPS, different domains experience various types of attacks, necessitating multiple deep learning models. Moreover, the attack detection process is hierarchical, wherein the detection results or the extracted features of a deep learning model from a lower domain can assist in detecting attacks in upper domains. This heterogeneity and hierarchical structure add complexity to the design and implementation of effective detection strategies.
- Inefficiency of Co-processing Big Data and Deep Learning Platforms. The mainstream in-memory computing platforms for big data, such as Spark and Flink, predominantly use highlevel languages like JAVA or SCALA and currently run only on CPUs. hese limitations prevent the utilization of powerful GPU resources for big data processing and deep learning. Furthermore, deep learning platforms like TensorFlow and MxNet do not integrate well with big data platforms and lack support for edge-cloud collaborative computing, making them less effective in dealing with large-scale CPS attack detection.
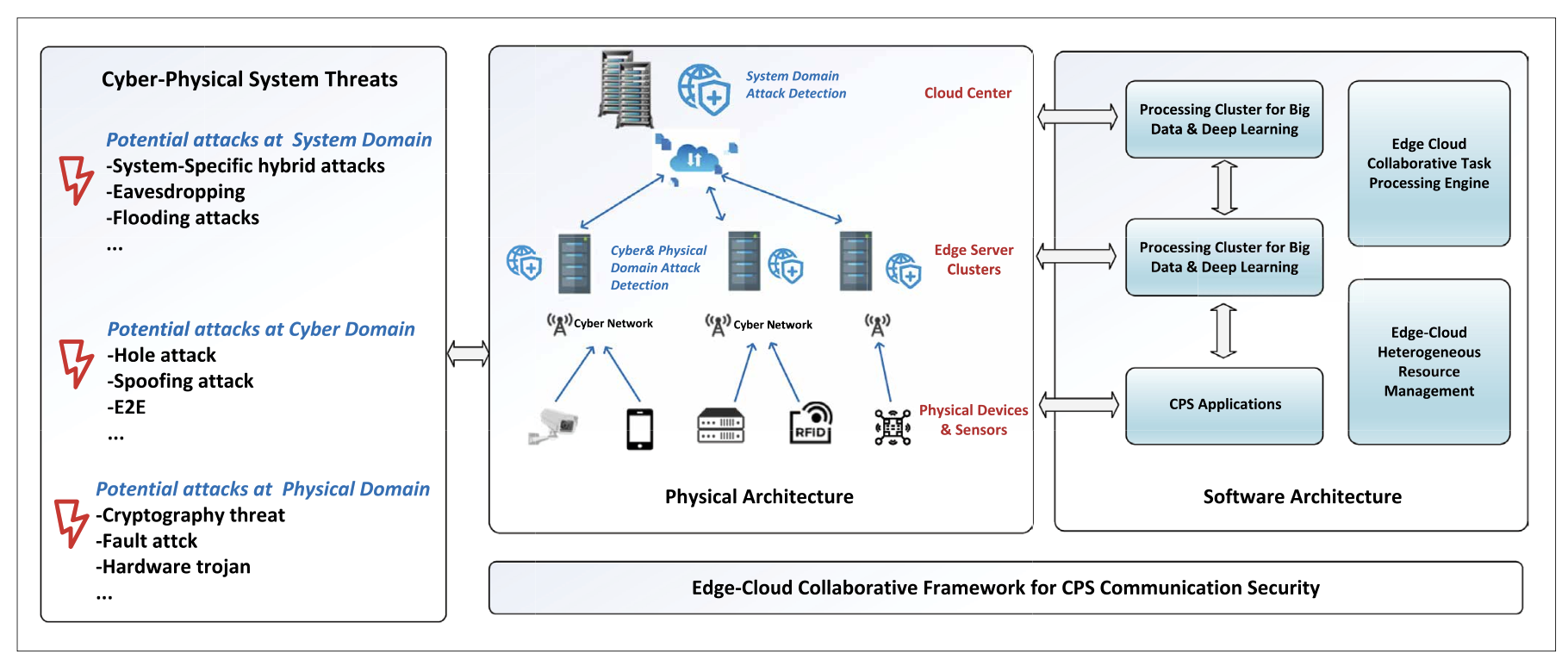
FIGURE 3. Overview of the edge-cloud collaborative framework for CPS communication security. The edge-cloud collaborative framework for CPS communication attack detection consists of a physical architecture and a software architecture. The physical architecture consists of three parts: Physical devices, Edge Server Clusters, and Cloud Center. The software architecture consists of CPS applications, processing cluster for big data & deep learning, task processing engine, and heterogeneous resource manager. The leftmost part of the diagram gives some of the attacks commonly faced by the three parts of the physical architecture.
Proposed Edge-Cloud CoLLAborative Framework for CPS Communication Security
OverALL Architecture
We introduce an Edge-Cloud Collaborative Framework for CPS communication attack detection, designed to address the above challenges in Section III. The framework leverages edge servers to handle lightweight, real-time tasks, and the cloud for complex computations, thus efficiently managing resources for the massive amounts of data in CPS. It processes the heterogeneous and hierarchical CPS attack detection by distributing tasks between edge servers and cloud centers based on attack types and levels. To enhance computational efficiency and overcome inefficiencies of co-processing big data and deep learning platforms, the framework integrates Spark and TensorFlow in processing clusters. It also employs a heterogeneous task scheduling scheme, dividing detection tasks into sub-tasks to optimize overall execution efficiency. The specifics of this edge-cloud collaborative framework for CPS communication attack detection are illustrated in Fig. 3, detailing the physical and software architecture.
1) Physical Architecture
The physical part of the framework contains the following 3 parts.
- Physical devices. This part is composed of sensors, cameras, and other IoT devices. They upload the collected raw data to the edge server through the heterogeneous cyber network while offloading the tasks of physical domain attack detection to the edge server with richer computing and storage resources. The edge cloud intelligent computing platform reduces the risk of data and privacy leakage, relieves the pressure on network bandwidth caused by data transmission from cloud computing centers, and improves the real-time detection of attacks from massive heterogeneous data of multiple sources.
- Edge server clusters. These clusters are deployed as computing and storage resources between the cloud computing center and the terminal device. Some lightweight and realtime demanding attack detection models are deployed in the edge servers to analyze the uploaded data as well as the local network data to detect the physical and communication level attacks. Meanwhile, it also extracts the security features from its own local network and uploads them to the cloud center, which has a global view of all the edge server clusters for the detection of some global attacks such as DDoS.
- Cloud Center. It is composed of multiple high-performance servers and storage devices, which use efficient computing performance to execute detection tasks with high processing complexity and high consumption of resources which contains the application level attacks and the global attacks of the CPS system. A high-speed and reliable data collaboration mechanism is established between each server in the horizontal layer of the cloud computing center, which makes full use of cloud computing resources; in the vertical layer, some lightweight computing tasks are delegated to edge nodes to execute computing through the edge cloud co-processing protocol.
The attacks on CPS also demonstrate hierarchical characteristics, with attacks occurring in the physical domain, cyber domain, and system domain, corresponding to the mentioned Physical devices, Edge server clusters, and Cloud center.
2) Software Architecture
The software architecture contains the following parts. The task processing engine is deployed at both the edge servers and the cloud center, and the heterogeneous resource manager, on the other hand, is responsible for managing the computing and network resources across the entire edge-cloud platform. This ensures that tasks are executed efficiently, with simpler tasks handled at the edge and more complex tasks processed in the cloud.
- CPS Applications. This part consists of a range of CPS applications such as smart grid, smart city, smart industry, and so on.
- Processing cluster for big data & deep learning. It can perform intelligence CPS detection algorithm on large-scale data by fusing Spark and TensorFlow. The clusters can be deployed on edge servers and cloud centers to receive data and perform Spark-based in-memory big data processing and TensorFlow-based intelligence CPS detection algorithm on it.
- Task processing engine. It is designed to meet the dual requirements of batch processing of historical CPS attack analysis and stream processing of real-time CPS attack detection. Based on the execution engine of the Spark platform for CPU tasks and the characteristics of heterogeneous resources of the edge cloud platform, we design a unified task execution engine for heterogeneous resources of the edge cloud platform, which combines the advantages of high throughput of batch processing and low latency of stream processing.
- Heterogeneous Resource Manager. It is responsible for unified hierarchical management of any computing and network resources (e.g., cameras, gateways, etc.) on the edge cloud platform from data sources and edge servers to the cloud computing center path. It enables better collaborative scheduling and load balancing of edge cloud tasks to meet the real-time nature of CPS attack detection tasks, as well as the demand for computing resources.
Processing Cluster for Big Data and Deep Learning
We effectively integrate GPU into Spark, a key task for supporting intelligent CPS attack detection in big data contexts. Traditionally, Spark and TensorFlow have diverging programming styles and execution models, largely due to Spark’s Java virtual machine (JVM) foundation and Tensor-Flow’s C/C++/CUDA/OpenCL architecture for parallel GPU programming.
To bridge this gap and support intelligent CPS attack detection with big data, we virtualize GPU and TensorFlow into devices that Spark can call directly with Java or Scala. In our system, we adopt the communication adaptation technique shown in Fig. 4 to communicate with GPU and TensorFlow. There are a number of workers that run in the cluster, and Spark applications run in the JVM, which invokes Wrapper.jar to communicate with TensorFlow or GPUs. The Wrapper.jar, written in Java, facilitates communication between the Spark system, GPU, and TensorFlow. This jar package is provided by the Stub.so, which is written in C/C++ and exports interface that the Wrapper.jar can utilize via the Java Native Interface (JNI). Meanwhile, the Stub.so communicates with the GPU or TensorFlow using various function calls. In this way, we seamlessly manage large-scale data processing and execute deep learning tasks on the same platform, effectively leveraging the strengths of Spark in big data processing and the deep learning capabilities of TensorFlow.
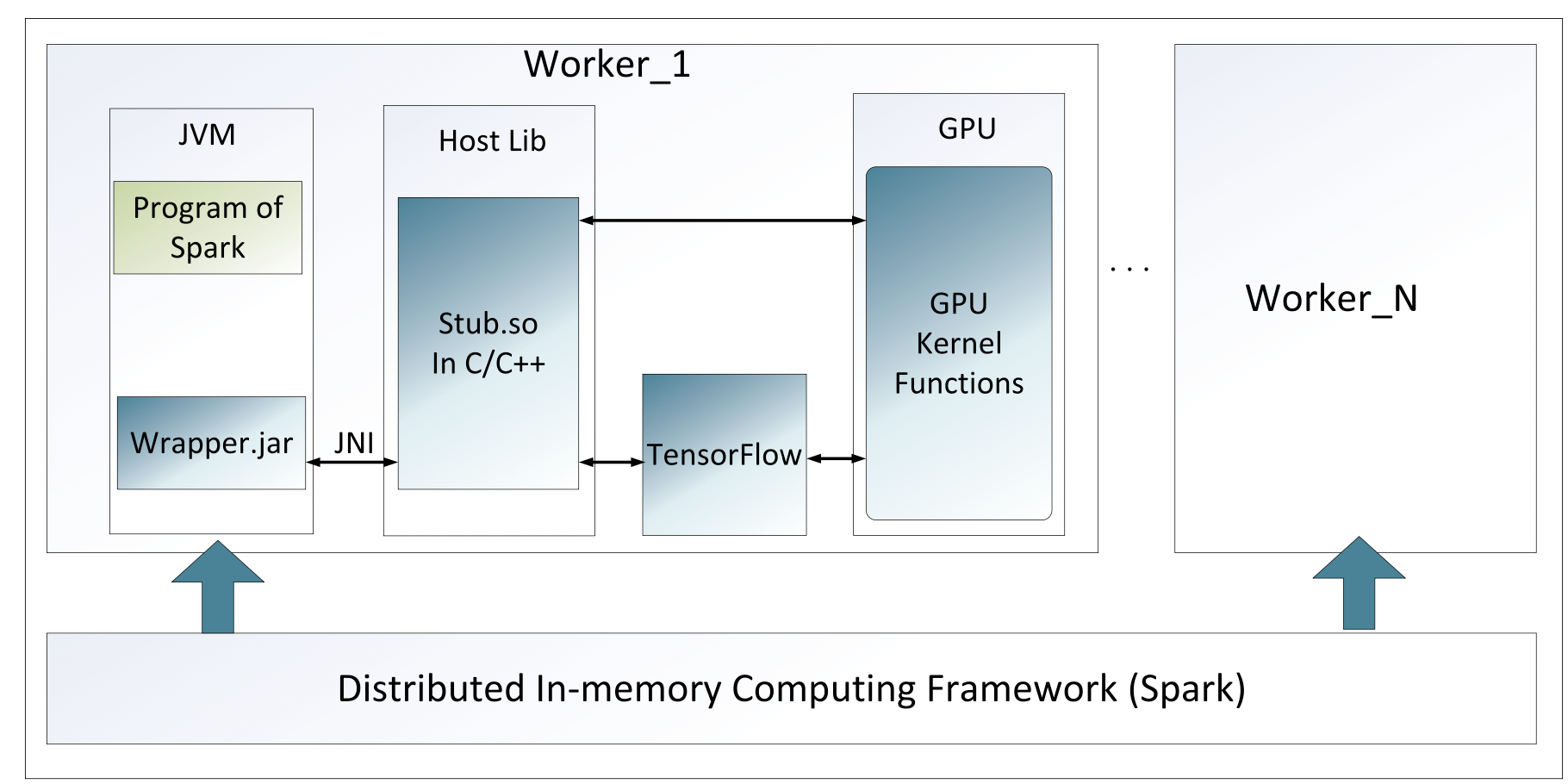
FIGURE 4. Processing cluster fusing Spark and TensorFlow for intelligent CPS attack detection.
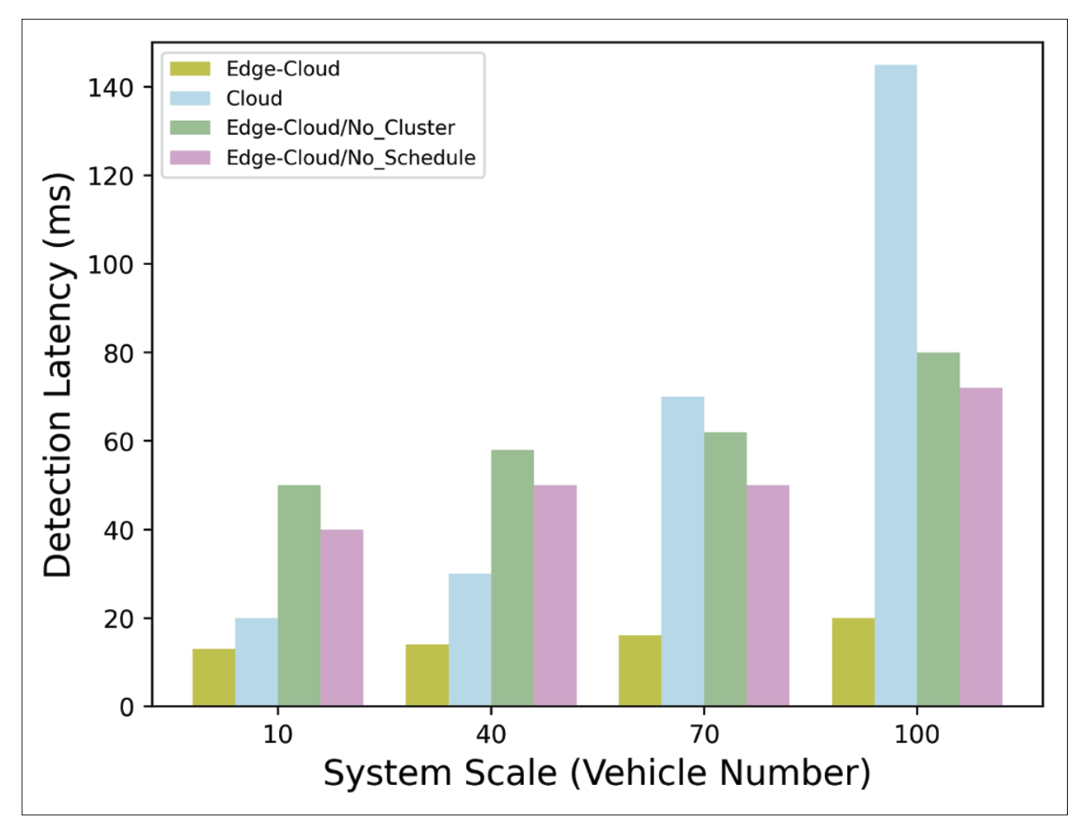
FIGURE 5. Detection latency for cyber-physical transportation system with different execution schemes. Egde-Cloud is our proposed collaborative framework, Cloud denotes the cloud-only approach, Edge-Cloud/No_Cluster denotes our framework variant without fusing Spark and TensorFlow, and EdgeCloud/No_Schedule is our framework variant without a heterogeneous task scheduling scheme.
The goal is to minimize task execution time and communication latency while maximizing resource utilization.
Heterogeneous Task ScheduLIng Scheme for Edge-Cloud CoLLAborative
The Cyber-Physical System (CPS) safety inspection platform regularly encounters the demand for comprehensive intelligent security detection tasks or concentrated inspection operations, which imposes manifold deployment challenges, encompassing the system’s burden-bearing capability, dynamic data magnitude, network communications, and dynamic task orchestration. Therefore, we present a resolution approach for task scheduling, cooperatively executed by the Edge-Cloud Collaborative Computing Task Processing Engine and the Heterogeneous Resource Stratified Manager, aiming for the optimized appropriation of resources.
First, The task processing engine divides detection tasks into sub-tasks, following two primary patterns: model partition and model collaboration. The model partition pattern leverages deep learning techniques to split complex detection models for edge server execution. Conversely, the model collaboration pattern utilizes multi-model detection, where the edge server runs a simple model for local data feature extraction and detection, and the cloud center executes a complex model for global attack detection. After task division, a set of subtasks is formed, each with predefined execution dependencies, forming a Directed Acyclic Graph (DAG). Each subtask has its own computing preference, such as execution on CPU or GPU.
After partitioning, based on the DAGs, our system assigns these subtasks to appropriate resources (CPU or GPU, edge server or cloud center) through a heterogeneous task scheduling and mapping scheme, which considers various constraints including resource capacity, task dependencies, data volume, task resource preferences, and communication latency. The goal is to minimize task execution time and communication latency while maximizing resource utilization. After task division and allocation, the processing cluster is used for the parallel processing of tasks and ensures that each task can proceed according to the predefined execution dependencies.
Use Case: Edge-Cloud CoLLAborative Attack Detection in Cyber-PhysicAL Transportation System
A cyber-physical transportation system (CPTS) employs a massive network of heterogeneous sensors and mobile wireless devices to enable advanced sensing and communication capabilities. However, the open attribute of the wireless communication process, particularly between sensors and traffic controllers, attracts potential attackers due to its vulnerability to security breaches such as eavesdropping and jamming.
To develop a robust understanding of these threats and their countermeasures, we simulate a scenario where we aim to detect eavesdropping and jamming attacks on moving vehicles. The experimental setup was designed based on the MATSim platform, simulating the driving data for approximately 10,000 cars over a week. This includes artificially introduced noise in 5% of the dataset to simulate jamming attacks and an abnormal increase in communication volumes to mimic the eavesdropping attacks. The simulated road network consisted of 10 edge servers and one cloud server, with each edge server responsible for the cars in its allocated area. For detecting time-based anomalies indicative of attacks, we opted for a Long Short-Term Memory (LSTM) net-work as the primary model.
Our edge-cloud collaborative detection framework’s performance was compared with a cloud-only approach, the results of which are shown in Fig. 5. As the cloud center and bandwidth become potential bottlenecks, the latency of the cloud-only approach increases dramatically with the number of cars. Our proposed framework, which combines Spark and TensorFlow in a computing cluster using a heterogeneous task scheduling scheme, outperforms its variants. This is due to its enhanced parallel efficiency of hardware resources when executing detection tasks.
Conclusion
The risks are becoming more and more acute in terms of communication security against Cyber Physical System (CPS). Moreover, the inter-connected physical facilities will continuously generate a large amount of data to process and largescale communication over networks in the CPS. Recently, deep learning (DL) based methods have shown their superiority in solving problems for communication security. However, how to deploy these methods to process large-scale data in complex real-world CPS with the aim of high efficiency, roust, and real-time processing is a nontrivial task. In this work, we identify the opportunities of edge intelligence for handling the big data in CPS for communication security and propose an edge-cloud collaborative framework for CPS communication attack detection which is expected to improve the parallel efficiency of hardware resources in executing detection tasks, and promote the intelligence of physical devices and the degree of cloud-edge collaboration, to meet the demand for realtime processing of large-scale and hierarchical CPS attack detection. Although the proposed edge-cloud collaboration framework can be effectively applied to CPS communication attack detection, it requires additional effort to address issues such as network latency, task balancing, data privacy, and security. These areas present opportunities for future research. For example, to tackle the problem of network latency, data preprocessing, and filtering can be performed on edge devices to reduce communication overhead.
Acknowledgment
This work was supported in part by the Fundamental Research Funds for the Central Universities under Grant x2wjD2230230, in part by the National Natural Science Foundation of China(NSFC) under Grant 62262014, and in part by the Changsha Municipal Natural Science Foundation under Grant kq2208290.
