Cybersecurity System Audits
Chapter 3– IT Governance and Management
Objectives
- IT Governance and Management
- Policies, Procedures, Standards and Guidelines
- IT Governance Frameworks
- Digital Transformation and Balance Score Card
- IT Steering Committee
- Types of Policies and Standards
- DFDs and DSDs
- Risk Management
- Life cycle of Risk Management
- Asset Identification
Introduction to IT Governance and Management
What is IT Governance?
IT Governance ensures that the IT organization’s activities are aligned with the overall business goals. It involves setting policies, delegating authority, and monitoring IT processes to ensure that they meet organizational objectives.
This framework helps senior management exert strategic control over IT processes to drive business success. Effective IT governance ensures that IT activities are purposefully aligned with business objectives, improving efficiency, minimizing risks, and maximizing return on IT investments.
Importance of IT Governance:
- Alignment with Business Goals: IT governance ensures that IT supports the organization's overall mission, goals, and objectives.
- Control and Monitoring: Governance provides strategic control over IT processes through policies, objectives, and continuous monitoring of performance.
- Adaptation to Business Needs: IT governance structures allow IT processes to evolve and adapt to changing business requirements.
IT Governance Structure
What is the IT Governance Structure?
IT governance structure refers to the framework that defines how decisions are made and responsibilities are allocated within the IT organization. It outlines the roles, processes, and procedures that ensure IT activities are aligned with business strategies. IT governance structure is crucial for maintaining consistency and ensuring that IT systems can adapt to the organization’s evolving business needs.
Key Components of IT Governance Structure:
- IT Steering Committee: Responsible for setting long-term IT strategies that align with business objectives and guiding policy enforcement.
- Delegation of Authority: Senior management delegates responsibility to IT leaders, ensuring accountability in IT decisions.
- Monitoring and Reporting: Continuous monitoring of IT processes ensures they remain aligned with the organization’s goals and adapts to changes in business strategy.
Human Resources Management in IT Governance
Human Resources Management in IT Governance
Human resources management (HRM) in IT governance involves assigning clear roles, responsibilities, and processes for IT personnel. It ensures that the IT team is properly structured to meet the demands of the business and that resources are efficiently allocated. HRM ensures that IT personnel are aligned with business strategies, which improves overall IT performance and supports the organization’s long-term goals.
Key Elements of HRM in IT Governance:
- Role Definition: Establishing clear roles and responsibilities within the IT department ensures accountability and improves efficiency.
- Staffing and Resource Allocation: HRM ensures that the right number of IT staff are in place and that they are trained to meet the organization’s technological demands.
- Training and Development: Continuous training keeps IT personnel updated with the latest technologies and best practices, ensuring they are well-equipped to handle IT challenges.
IT Policies, Standards, Processes, and Procedures
What are IT Policies?
IT policies are formal guidelines that govern the behavior and decision-making processes within the IT department. They provide a framework for managing IT resources, ensuring that IT operations are aligned with business objectives and comply with regulatory requirements. IT policies and standards ensure that IT operations are consistent, efficient, and aligned with business goals. They also reduce risks associated with regulatory compliance and operational inefficiencies.
Key Components of IT Policies, Standards, Processes, and Procedures:
- IT Standards: Standards provide consistency in technology and operations, ensuring that all IT systems are aligned with organizational goals.
- IT Processes: Processes are high-level activities that dictate how IT systems are managed and maintained to ensure alignment with business goals.
- IT Procedures: Detailed steps that IT personnel must follow when implementing policies and processes, ensuring consistency and compliance.
Management Practices in IT Governance
What are Management Practices in IT Governance?
Management practices in IT governance refer to the methods used to oversee and control IT resources. These practices ensure that IT investments, processes, and personnel are managed in a way that supports the organization's strategic goals. Management practices ensure that IT resources are used effectively and efficiently, maximizing the value that IT delivers to the business while minimizing risks and inefficiencies.
Management Practices in IT Governance:
- Financial Management: This involves budgeting for IT initiatives, ensuring that spending aligns with business priorities and delivers value.
- Performance Management: Regularly reviewing IT performance ensures that IT systems are meeting business needs and can be optimized for better results.
- Change Management: Effective change management processes ensure that any updates or changes to IT systems align with business strategies and minimize disruption.
IT Contracting and Contract Management Strategies
IT Contracting:
IT contracting involves negotiating agreements with vendors and service providers to supply technology products and services. Effective contracting ensures that the organization gets the best value for its IT investments and that the contracted services meet business needs.
Contract Management Strategies:
- Vendor Selection: Choosing vendors based on their ability to meet IT and business requirements while providing cost-effective solutions.
- Negotiating Terms: Ensuring favorable contract terms, including pricing, delivery timelines, service-level agreements (SLAs), and penalties for non-compliance.
- Monitoring Contracts: Regularly reviewing vendor performance to ensure that contractual obligations are being met and adjusting as necessary to meet changing business needs.
Why Contract Management is Important:
Effective contract management reduces risks related to third-party relationships, ensures that IT services are delivered on time and within budget, and allows organizations to adapt contracts based on changing business requirements.
Role of the IT Steering Committee
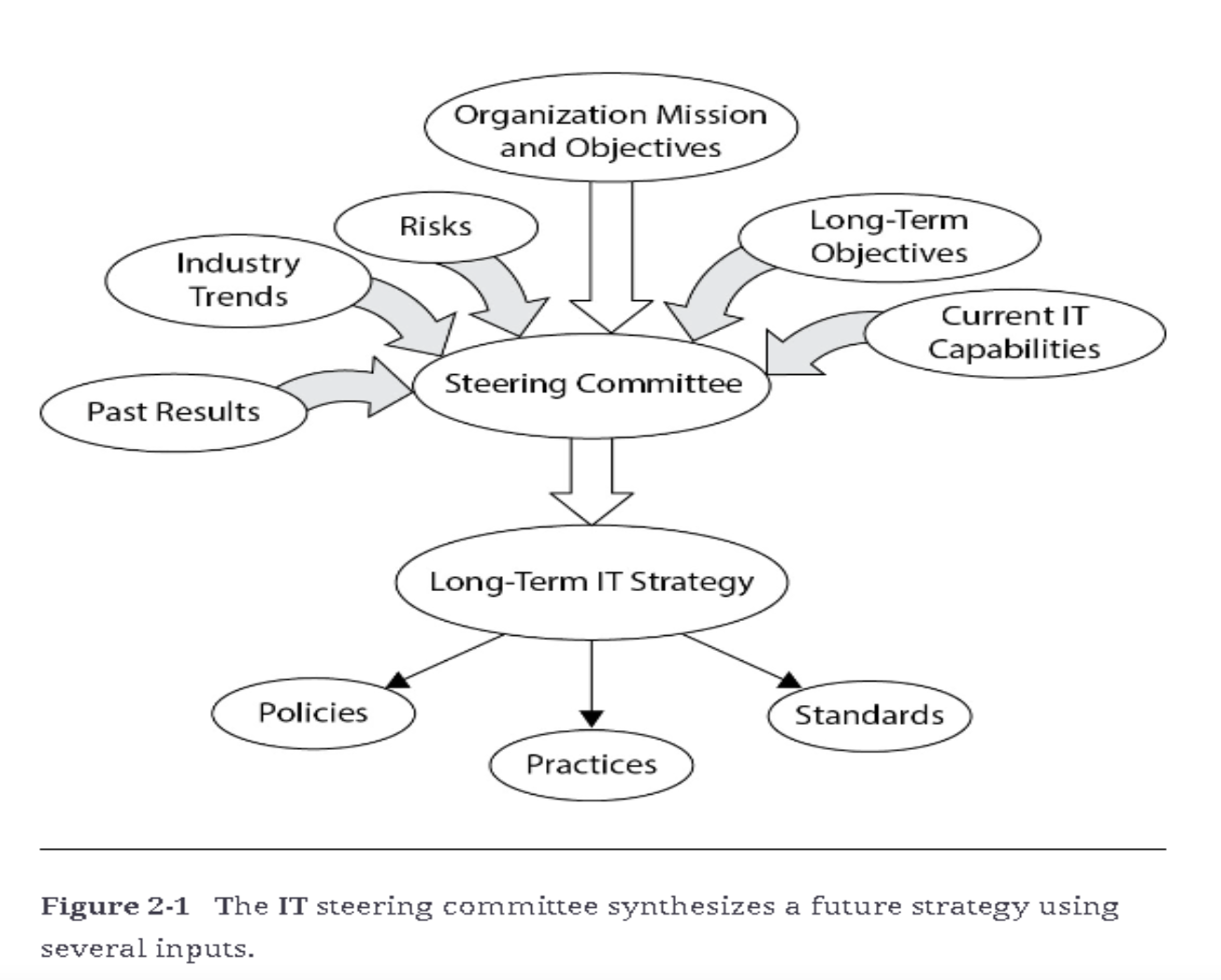
What is an IT Steering Committee?
The IT steering committee is a group of senior executives and IT leaders responsible for setting the long-term IT strategy. It ensures that IT processes and initiatives are aligned with business goals and adapts IT strategies to meet the changing needs of the organization. The IT steering committee plays a critical role in ensuring that IT investments and initiatives support the overall business strategy, improving governance and accountability.
Key Responsibilities of the IT Steering Committee:
- Setting IT Strategy: Defining the long-term IT roadmap that supports business goals.
- Policy Development: Creating and enforcing IT policies that align with organizational objectives.
- Monitoring IT Performance: Regularly reviewing IT processes to ensure they are delivering value to the business.
The Role of the IT Steering Commitee
IT Governance Frameworks
What is an IT Governance Framework?
IT governance frameworks provide structured guidelines for aligning IT processes with business objectives. Organizations can adopt established frameworks to manage IT governance more effectively without reinventing the wheel. Governance frameworks provide organizations with a proven structure for managing IT, ensuring compliance, security, and alignment with business objectives.
Common IT Governance Frameworks:
- COBIT: Developed by ISACA, COBIT is a framework for managing and governing enterprise IT, focusing on aligning IT with business goals.
- ISO/IEC 27001: An international standard for information security management, ensuring that IT systems are secure and compliant.
- ITIL: A set of best practices for IT service management that focuses on delivering value through IT services.
COSO Governance Framework
What is COSO Framework?
COSO (Committee of Sponsoring Organizations of the Treadway Commission) is a framework focused on internal controls and risk management. Originally developed for financial systems, COSO is now used to manage IT-related risks and internal controls within organizations. COSO provides a structured approach to managing IT-related risks, ensuring that internal controls are effective, and that IT systems are secure, compliant, and aligned with business objectives.
Key Elements of COSO:
- Internal Control: Ensures that IT systems are governed by robust internal controls that mitigate risks and ensure compliance with regulatory requirements.
- Risk Management: Focuses on identifying, assessing, and managing risks that could affect IT systems.
- Compliance: Ensures that IT processes comply with internal policies, laws, and regulations.
Digital Transformation and IT Governance
What is Digital Transformation?
Digital transformation refers to the process by which organizations leverage digital technologies to fundamentally change their business operations. This transformation affects how businesses use IT todeliver products and services, manage data, and interact with customers.
Impact on IT Governance:
- Increased Reliance on IT: Digital transformation makes IT a critical part of the business process, requiring stronger IT governance structures.
- Need for Agility: IT governance must adapt to rapidly changing technology landscapes, ensuring that IT processes can support new business models and innovations.
- Security and Compliance: As businesses digitize, IT governance must ensure that digital assets are secure and compliant with evolving regulations.
Why Digital Transformation is Important:
Digital transformation is reshaping industries, and organizations that adapt quickly can gain a competitive advantage. IT governance ensures that digital transformation initiatives are aligned with business objectives and managed effectively.
Balanced Scorecard in IT Governance
What is a Balanced Scorecard (BSC)?
The balanced scorecard is a management tool used to measure the performance and effectiveness of an organization’s IT governance. It ensures that IT processes are aligned with the organization’s strategic objectives and provides a comprehensive view of IT performance. The balanced scorecard provides a structured way to measure IT governance performance and ensure that IT processes are delivering value to the organization.
Key Perspectives of the Balanced Scorecard:
- Financial Perspective: Measures the cost-effectiveness and financial performance of IT initiatives.
- Customer Perspective: Tracks user satisfaction and the impact of IT services on customers.
- Internal Process Perspective: Monitors the efficiency of internal IT processes.
- Innovation and Learning Perspective: Tracks IT innovation and the development of new capabilities within the IT department.
The Standard IT Balanced Scorecard (IT-BSC)
What is the IT-BSC?
The standard IT balanced scorecard (IT-BSC) is an adaptation of the balanced scorecard designed specifically to measure the performance of the IT organization. It ensures IT processes are aligned with business objectives and supports overall organizational goals. IT-BSC ensures IT performance is evaluated effectively and aligns IT objectives with the broader business goals, improving efficiency and innovation.
- Business Contribution: Measures the perception of IT effectiveness by non-IT executives.
- User Satisfaction: Tracks end-user satisfaction with IT systems and support.
- Operational Excellence: Monitors key operational metrics like support cases, downtime, and defects.
- Innovation: Evaluates IT’s use of new technologies and the availability of staff training.
Information Security Governance
Information Security Governance
Security governance involves establishing roles, responsibilities, and processes to manage risks related to IT and information security. It ensures that security is aligned with the organization’s business objectives and addresses the risks to key assets. Security governance aligns security efforts with business objectives, ensuring systems are protected against risks and that the organization remains compliant with regulatory requirements.
Roles in Information Security Governance:
- Board of Directors: Sets the risk appetite and guides risk management strategies.
- Steering Committee: Develops operational strategies for security and risk management.
- Chief Information Security Officer (CISO): Oversees security policies, risk assessments, incident management, and compliance.
Roles and Responsibilities in Information Security Governance
Key Roles in Information Security:
- Board of Directors: Responsible for establishing the tone for risk appetite and security strategy.
- Steering Committee: Defines operational strategies and sets roles for managing security and risk.
- CISO (Chief Information Security Officer): Develops security policy, conducts risk assessments, manages vulnerabilities, and ensures compliance with regulations.
Additional Roles:
- CIO (Chief Information Officer): Manages IT strategy, operations, and service delivery.
- All Employees: Must comply with the organization’s security policies and processes.
- Management: Accountable for employee conduct and ensuring compliance with security protocols.
Clearly defined roles ensure that security risks are managed efficiently, responsibilities are distributed, and that every level of the organization contributes to maintaining security.
The Role of the CISO
CISO:
The Chief Information Security Officer (CISO) is responsible for developing and enforcing the organization’s security policies. The CISO oversees risk management, incident response, vulnerability assessments, and security awareness programs.
Responsibilities of the CISO:
- Security Policy Development: Ensures that security policies are aligned with business goals and regulatory requirements.
- Risk Management: Conducts regular assessments to identify and mitigate IT risks.
- Incident Response and Management: Oversees response procedures to security incidents to minimize their impact on the organization.
The CISO plays a crucial role in safeguarding the organization’s IT systems and ensuring that security strategies are effectively implemented across all levels of the organization.
Whom Should the CISO Report To?
Debate on CISO Reporting Structure:
There is an ongoing debate on whether the CISO should report to the CIO or act as a peer. Some organizations believe that the CISO should report to the CIO, while others advocate for independent reporting to ensure unbiased governance.
Reporting Structures:
- Reporting to the CIO: The CISO may report to the CIO for streamlined communication regarding IT and security.
- Independent Reporting: The CISO may report directly to the board or a senior executive, ensuring that governance, policy development, and risk management remain independent of IT operations.
- Hybrid Approach: The CISO may report to the CIO for security operations but act independently for governance and risk management.
The reporting structure affects the independence and effectiveness of security governance. A well-structured reporting line ensures that security efforts are aligned with business goals and IT processes.
Reasons for Security Governance
Why is Security Governance Necessary?
Organizations are increasingly reliant on their information systems for daily operations, making security governance essential. Security governance ensures that the organization is protected against security-related incidents that could disrupt business continuity.
Reasons for Security Governance:
- Dependency on Information Systems: Modern organizations depend heavily on IT systems to support critical operations.
- Risk Minimization: Security governance reduces the likelihood and impact of security breaches, ensuring system integrity and availability.
- Digital Transformation: As organizations digitize, security governance helps manage the associated risks.
Security governance protects the organization from potential security threats, ensuring business continuity and enhancing organizational resilience.
Security Governance Activities
Key Activities in Security Governance:
- Risk Management: Security governance includes regular risk assessments to identify and address vulnerabilities in IT systems.
- Process Improvement: It involves continuous evaluation and modification of security-related business processes to improve protection and efficiency.
- Incident Response: Security governance defines procedures for responding to security incidents, aiming to minimize damage and prevent future occurrences.
Additional Activities:
- Compliance Monitoring: Ensures that security policies meet legal and regulatory requirements.
- Business Continuity Planning: Prepares the organization for potential disruptions by developing continuity and disaster recovery plans.
These activities form the backbone of a strong security governance program, ensuring the protection of critical information and assets while maintaining business operations during incidents.
Security Governance Results
Expected Results from Effective Security Governance:
Effective security governance strengthens organizational resilience, enhances stakeholder trust, and provides a competitive edge by protecting critical assets.
- Increased Trust: Organizations that manage security well inspire greater trust from customers, suppliers, and business partners.
- Improved Reputation: Consistently well-managed security improves an organization’s standing in the business community, including among investors and regulators.
- Enhanced Security: Risk mitigation strategies and proper incident response lead to a more secure IT environment, reducing the likelihood of breaches.
Long-Term Benefits:
- Compliance with Legal Standards: Adherence to security policies and regulations reduces the risk of legal penalties.
- Business Continuity: Proper security governance ensures that even during a security incident, critical business processes remain operational.
Incident Response in Security Governance
Incident Response:
Incident response refers to the organized approach for handling security incidents such as data breaches, malware attacks, or system failures. It aims to contain and mitigate the impact of incidents while recovering systems to their operational state.
Steps in Incident Response:
- Preparation: Establishing a robust incident response plan that defines roles and procedures before an incident occurs.
- Detection and Analysis: Monitoring systems to detect unusual activities and quickly analyze the cause and impact of an incident.
- Containment and Recovery: Taking steps to contain the breach, mitigate the damage, and restore systems to normal functionality.
Business Continuity and Disaster Recovery Planning
Business Continuity and Disaster Recovery:
Business continuity planning (BCP) and disaster recovery (DR) are strategies that ensure critical business functions can continue during and after an IT disruption. BCP focuses on maintaining operations, while DR concentrates on recovering IT infrastructure after a disaster.
Elements of BCP and DR:
- Risk Assessment: Identifying potential risks that could disrupt business operations and determining their impact.
- Contingency Planning: Developing detailed plans that outline procedures for maintaining critical business processes in the event of a disruption.
- Testing and Drills: Regularly testing the effectiveness of the business continuity and disaster recovery plans to ensure preparedness.
BCP and DR are essential for minimizing downtime, maintaining business operations during crises, and ensuring a quick recovery from disruptions.
Resource Management in Security Governance
Resource management in security governance involves allocating manpower, budget, and other resources to meet security objectives. It ensures that the organization has the necessary tools and personnel to manage security risks effectively.
- Budget Allocation: Ensuring sufficient financial resources are allocated to security initiatives, including technology investments and staff training.
- Personnel Management: Assigning the right number of staff with the appropriate skills to handle security tasks.
- Resource Optimization: Continuously reviewing resource usage to ensure that security efforts are cost-effective and aligned with business goals.
Resource management ensures that security initiatives are adequately supported, reducing the risk of security breaches while maintaining operational efficiency.
IT Strategic Planning
IT strategic planning is the process of determining what the IT organization will be doing in the next two, three, or more years. It requires careful consideration of future technologies, practices, and long-term organizational goals.
- Formal and Iterative Process: Strategic planning should be an organized, continuous process rather than an ad hoc activity.
- Roles and Responsibilities: Specific individuals should be assigned planning roles, ensuring accountability in IT strategy development.
- Focus on the Future: IT strategic planning involves predicting future business activities and ensuring that IT can support those needs.
Strategic planning answers the question, “What will IT do in the future?” It involves analyzing information about future technologies and practices and integrating that with long-term organizational goals.
Key Steps in Strategic Planning:
- Understanding Business Needs: IT must anticipate how business activities will evolve in the next five years.
- IT Capacity Planning: Ensuring that IT systems will have sufficient capacity to support future workloads and transaction volumes.
- Innovation: IT may drive future activities or influence how business activities will be carried out.
Policies, Processes, Procedures, and Standards
What are Policies, Processes, Procedures, and Standards?
These elements define the organizational behavior and the use of technology within the IT department. Policies are the overarching rules that govern IT activities, while processes, procedures, and standards define how these activities should be carried out.
Key Definitions:
- Policies: High-level guidelines that define what must be done, without specifying how it must be done.
- Processes and Procedures: Processes define broad activities, while procedures provide detailed instructions for completing specific tasks.
- Standards: Defined best practices and protocols that ensure consistency in how IT systems are built and maintained.
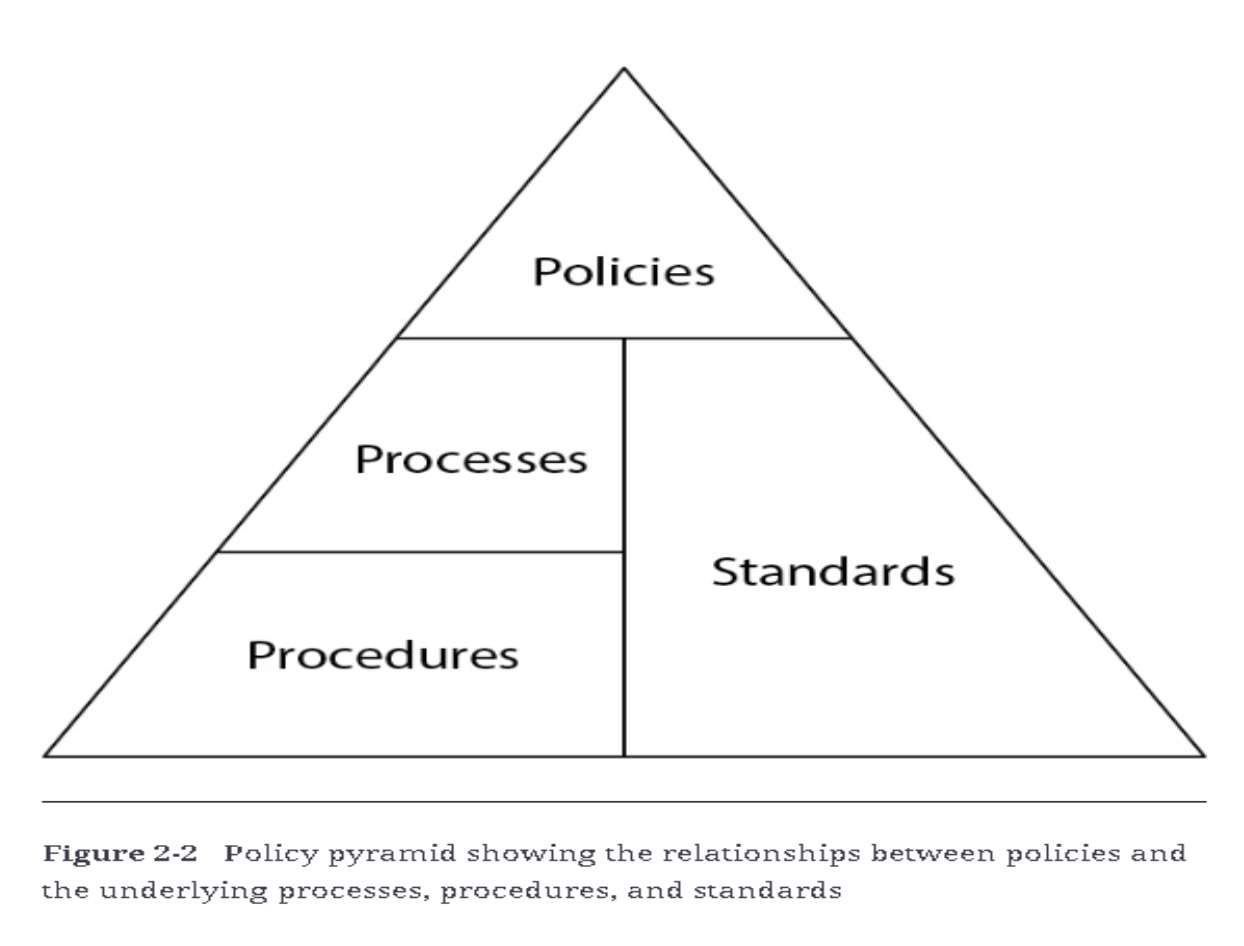
The Relationship Between Policies, Processes, Procedures, and Standards
- Policies define high-level objectives, processes guide activities, procedures outline specific steps, and standards set technical criteria. These elements work together to ensure consistency and efficiency in IT operations.
- Policies are typically broad, while processes and procedures provide more detailed guidance on how to execute tasks. This hierarchical relationship ensures that the organization’s objectives are met while maintaining operational control and security.
- Policies: Provide overarching rules that dictate organizational behavior.
- Processes and Procedures: Break down policies into actionable steps and specific guidelines.
- Standards: Ensure technical and operational consistency.
The Relationship Between Policies, Processes, Procedures, and Standards
Types of policies
Information Security Policy
An information security policy defines how an organization will protect its critical assets from threats. It specifies roles and responsibilities, risk management practices, security processes, and acceptable use guidelines. The policy forms the foundation for an organization's overall approach to managing information security.
Acceptable Use Policy
The acceptable use section of a security policy defines behaviors that are permitted and those that are prohibited in the organization. It sets boundaries for how IT systems, data, and resources can be used.
Privacy Policy
A privacy policy outlines how an organization manages, protects, and shares personal information related to private citizens. It defines how private information is collected, stored, and transmitted, and how it will be protected from unauthorized access.
Data Classification Policy:
A data classification policy establishes levels of sensitivity for the organization’s information. It categorizes data to ensure that more sensitive data is given higher levels of protection.
- Top Secret: The highest level of classification, typically involving national security or critical business information.
- Secret: Sensitive information that requires significant protection but may not be as critical as top-secret data.
- Public: Information that can be freely shared without risk.
System Classification Policy
A system classification policy establishes levels of security for IT systems that store and process classified information. Systems that store more sensitive data receive higher levels of security, including system hardening measures.
Site Classification Policy
A site classification policy establishes security levels for an organization’s work locations. The policy defines physical security measures based on factors such as the criticality of the staff and the value of the data processed at the site.
Access Control Policy
An access control policy defines how access to systems, data, and physical locations is granted, reviewed, and revoked. It outlines the procedures for approving access and the roles responsible for managing it.
Mobile Device Policy
A mobile device policy defines the rules for using mobile devices in the organization, including personally owned devices (BYOD). It outlines the conditions for using these devices to access business information and systems.
Social Media Policy
A social media policy governs how employees can represent the company on social media, both in personal and professional contexts. It aims to protect the organization’s reputation and ensure that sensitive information is not inadvertently shared online.
IT Standards and It’s Types
IT Standards:
IT standards are official, management-approved statements that define the technologies, protocols, suppliers, and methods used by an IT organization. These standards help create consistency across the organization, making it more cost-efficient and effective.
Types of IT Standards
- Technology/Product Standards: These standards specify what technologies or products are used across the organization, including operating systems, database management systems, and application servers. Consistency in technology reduces complexity and improves support.
- Protocol Standards: These refer to the protocols an organization uses for communication, such as TCP/IP for internal networks or TLS for secure transmissions. Standardized protocols ensure secure, efficient data transmission.
- Supplier Standards: Supplier standards define the vendors from which the organization purchases IT products or services. Standardizing suppliers can result in negotiated discounts and streamlined support.
Types of Standards
Methodology Standards
Methodology standards refer to the standardized practices used in IT processes, such as software development, system administration, and network engineering. These practices ensure that tasks are performed consistently and correctly across the organization.
Configuration Standards
Configuration standards define the specific settings and configurations applied to systems like servers, workstations, and network devices. This creates a uniform environment, which simplifies support and reduces downtime.
Architecture Standards
Architecture standards refer to the design and structure of the organization's IT systems, databases, and networks. These standards provide guidelines for constructing consistent IT environments across all branches or divisions.
Benefits of IT Standards
Standards help create a simpler, leaner IT organization by minimizing the number of technologies, protocols, and suppliers that must be supported. This leads to more efficient resource management and improved system reliability.
- Cost Efficiency: Fewer types of hardware and software mean reduced costs for training, support, and maintenance.
- Streamlined Operations: Standards create uniformity, making it easier for IT teams to manage systems, troubleshoot issues, and apply updates.
- Improved Expertise: By focusing on a limited set of technologies, the IT team can develop deep expertise in those areas, enhancing overall system performance.
Enterprise Architecture (EA)
Enterprise architecture is a comprehensive framework that aligns business goals with IT systems and processes. It is both a business function and a technical model used to ensure IT systems meet the organization’s long-term strategic needs.
- Provides detailed mappings of IT systems and their relationships to business functions.
- EA adapts to changes in business and technology to ensure ongoing alignment.
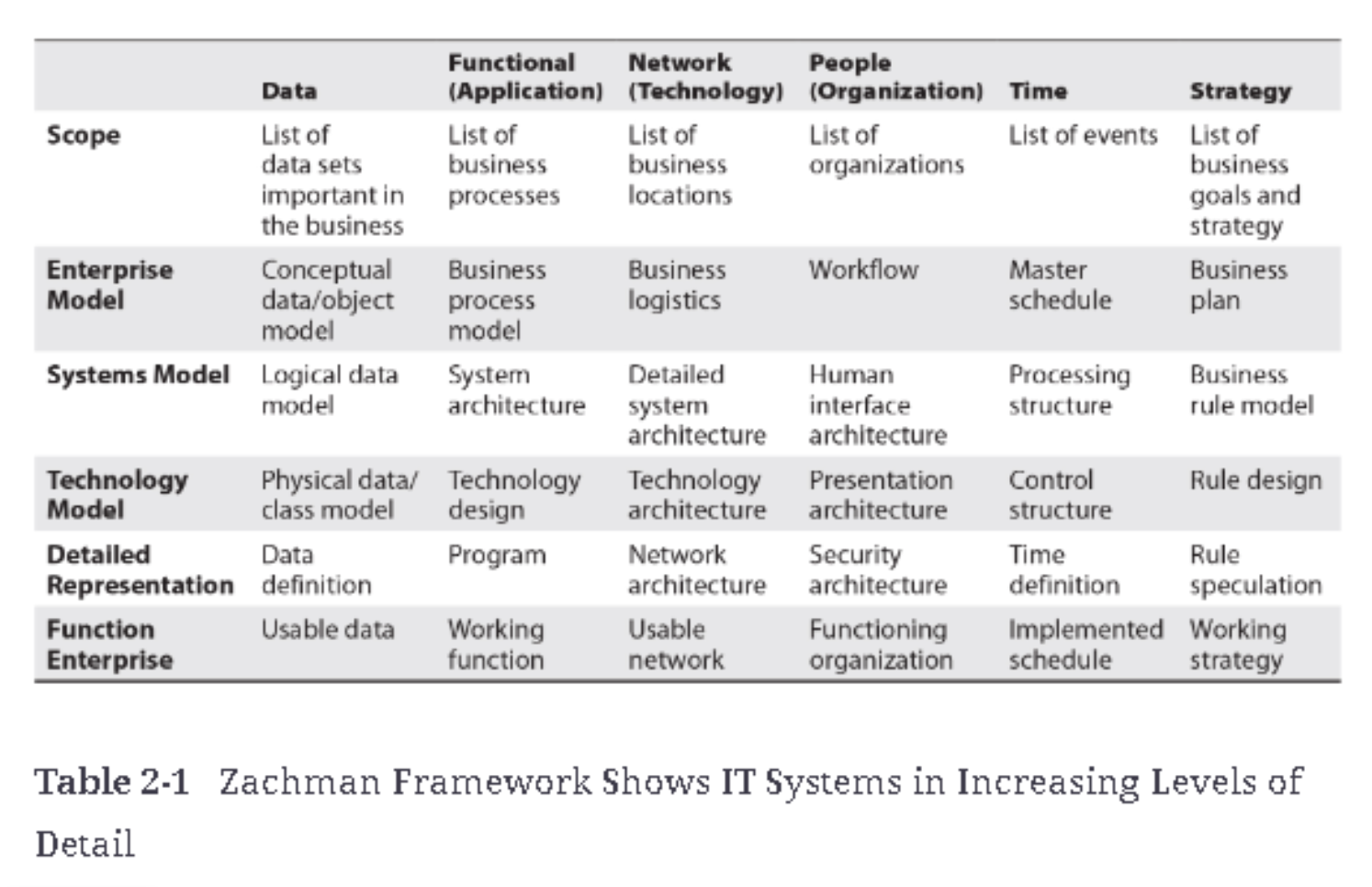
Zachman Framework
The Zachman Framework is an enterprise architecture model that structures IT systems in increasing levels of detail, much like the construction of a building. It starts with high-level business functions and moves down to technical details such as databases, networks, and applications.
- Breaks down IT environments into increasing levels of specificity, from business functions to system-level details.
- Helps IT professionals understand how different systems work together to support the organization.
Zachman Framework Illustration
Data Flow Diagrams (DFDs)
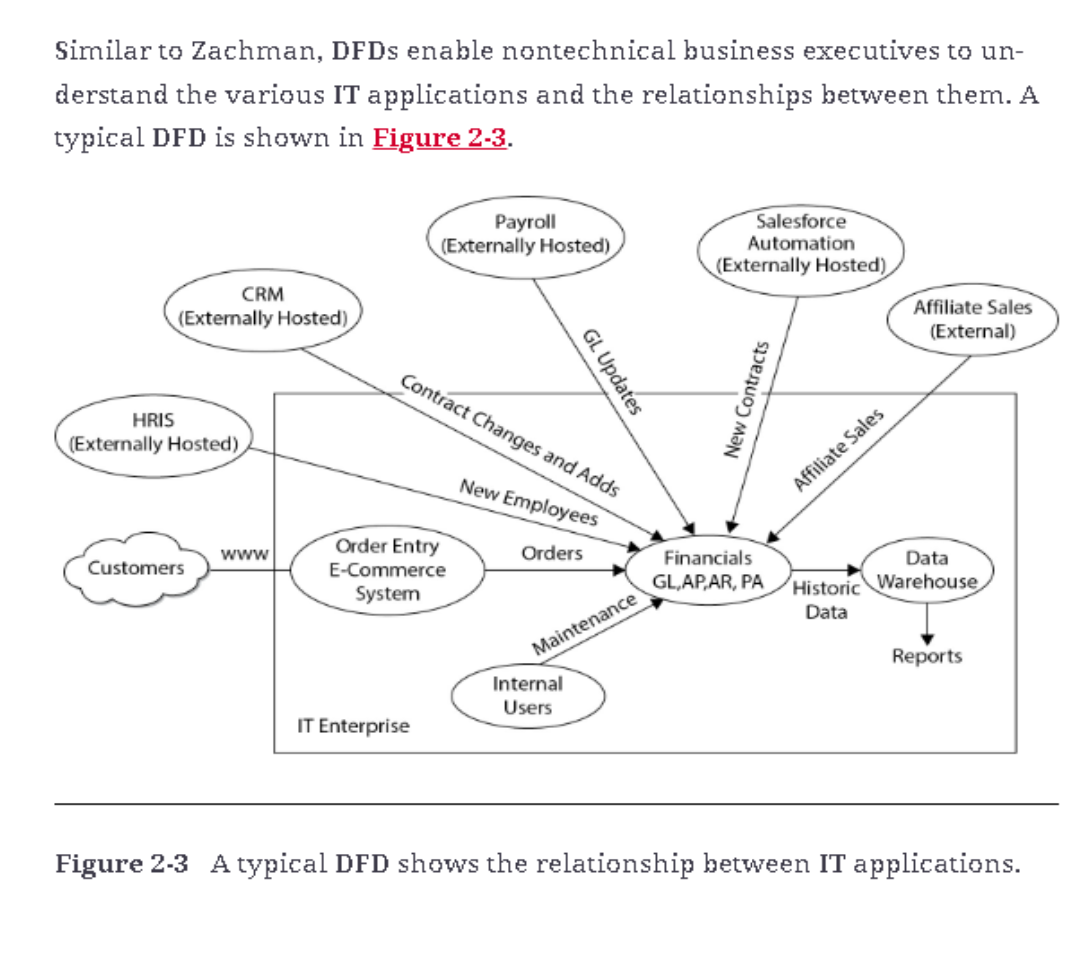
Data Flow Diagrams:
Data flow diagrams (DFDs) are visual representations that illustrate how data flows between IT applications. They depict the flow of information in business terms and can break down processes to a very detailed level.
Specifications accompanying DFDs can provide granular details, including field lengths and protocols. It show the interactions between different applications and how data is transmitted across them. DFDs help both technical and non-technical stakeholders understand the flow of information within the organization, supporting better decision-making around IT systems and processes.
Data Storage Diagrams
Data Storage Diagrams:
Data storage diagrams provide a visual or tabular representation of where data is stored across the organization. They document the instances of structured data stored in formal management systems, such as databases. Identifies where critical data is housed across the enterprise, providing a clear map of storage points.
Zero Trust Architecture:
Zero trust is a security model that assumes no part of an IT environment can be trusted by default. Even internal systems are treated as potentially compromised, and strict security controls are applied to all interactions. Every user and system must verify its identity before gaining access to any resource. Constant monitoring ensures that any suspicious activity is detected and responded to immediately.
Risk Management and Appetite Overview
Risk Management
Risk management is the process of identifying, analyzing, and mitigating risks that could affect an organization’s operations. It is a continuous and phased set of activities that ensures risks are managed consistently and effectively. The process ensures risks are aligned with the organization’s overall goals and risk appetite.
Risk Appetite
Risk appetite refers to the organization’s overall approach to risk—whether it is risk-averse or willing to take on certain risks. An organization’s risk management program should reflect its risk appetite to ensure that risk decisions align with business objectives. Organizations must balance risk-taking with the potential benefits of pursuing new opportunities.
Risk Treatment Options
What are the Four Risk Treatment Options?
Once a risk has been identified, an organization can take one of four actions: accept, mitigate, transfer, or avoid the risk. These actions are known as risk treatments, and they often involve a combination of two or more solutions.
Risk Treatment Options Explained:
- Accept: The organization acknowledges the risk and does nothing to change it.
- Mitigate: Actions are taken to reduce the risk to an acceptable level.
- Transfer: The risk is shared with another entity, such as an insurance company.
- Avoid: The activity associated with the risk is discontinued.
Choosing the appropriate risk treatment ensures that the organization can manage risks effectively while still pursuing its business objectives.
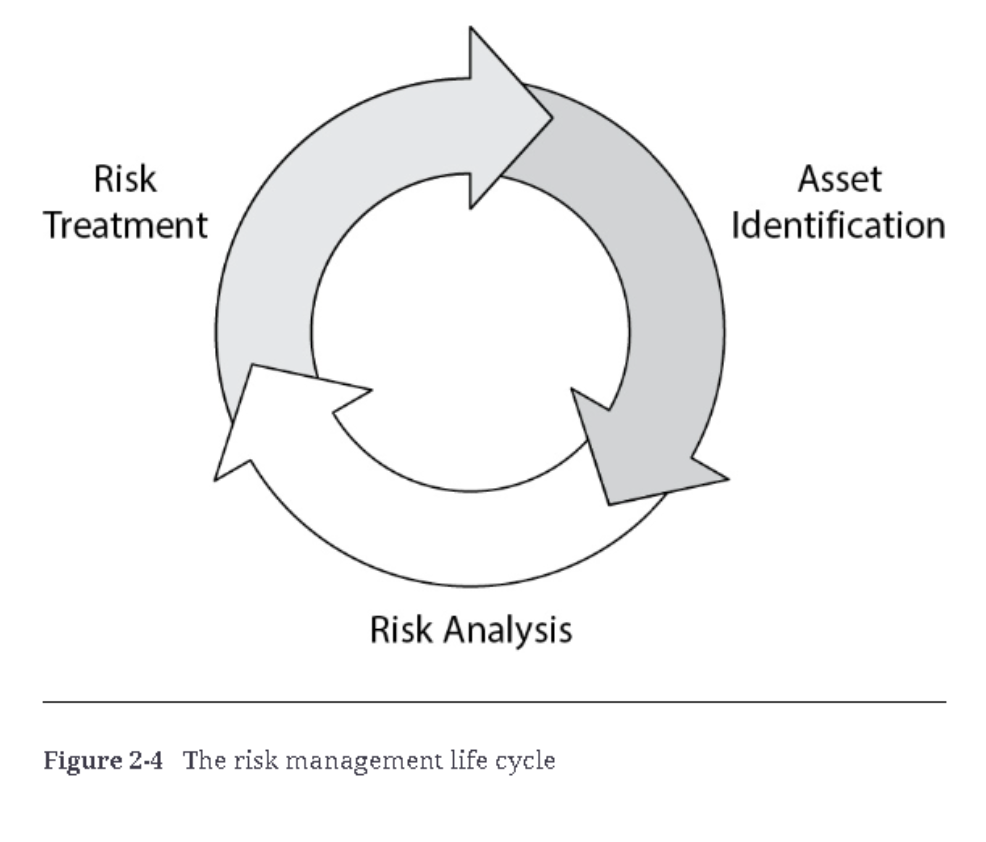
The Risk Management Life Cycle
The risk management life cycle is a continuous process that involves identifying, analyzing, and treating risks. It follows a systematic approach that helps ensure risks are consistently addressed.
Key Phases of the Life Cycle:
- Identification: Discover potential risks through various methods.
- Analysis: Evaluate the potential impact of risks and explore mitigation strategies.
- Treatment: Choose and implement risk treatment options.
By following a structured life cycle, organizations can ensure that risks are not only identified but also monitored and managed over time.
Asset Identification in Risk Management
Asset identification is the first step in the risk management process. It involves identifying all of the assets that need protection, whether they are physical, virtual, or intangible.
Types of Assets Identified:
- Physical Assets: Buildings, equipment, IT hardware, and supplies.
- Intangible Assets: Information, intellectual property, and brand reputation.
- Personnel: Employees are often considered the most valuable asset, as they perform the organization’s processes.
How Are Assets Grouped in Risk Management?
In risk management, assets are often grouped into categories to simplify the analysis and treatment of risks. Grouping allows similar assets to be managed together based on their shared risk profiles.
Common Methods for Grouping Assets:
- By Type: Similar assets, such as all laptop computers, may be grouped together.
- By Location: Assets may be grouped based on their physical location, such as servers in a data center.
- By Business Process: Grouping assets according to the business processes they support can help prioritize critical functions.
Sources of Asset Data for Risk Management
An organization can obtain asset data from various sources to build an asset inventory. This inventory forms the basis for identifying and managing risks.
Common Sources of Asset Data:
- Financial Asset Inventory: Provides a record of the organization’s physical assets and their financial value.
- Interviews with Key Personnel: Discussions with staff members help identify intangible assets, such as intellectual property.
- IT Systems Portfolio: Managed IT systems often have records of critical hardware and software assets.
How is Asset Data Organized?
Once assets are identified, they must be organized or classified for effective risk management. This allows risk managers to focus on specific groups of assets and tailor risk treatments accordingly.
Methods of Organizing Asset Data:
- By Geography: Assets can be grouped by their physical location to address location-specific risks.
- By Business Process: Grouping assets according to the processes they support helps prioritize those critical to operations.
- By Sensitivity: Some assets, particularly data, may be grouped based on their sensitivity or regulatory requirements.
Risk Analysis
Risk analysis is the process of identifying and assessing risks within an organization, focusing on the intersection of threats, vulnerabilities, probabilities, and impacts. It involves both quantitative and qualitative methods to estimate the level of risk.
- Risk is commonly expressed as the formula,
Risk = Probability × Impact, which applies to both qualitative and quantitative analysis. - Another common formula includes asset value, expressed as
Risk = Probability × Impact × AssetValue.
Threat analysis identifies potential threats that could harm the organization’s assets, while vulnerability analysis examines the weaknesses in systems that make them susceptible to threats. Together, these analyses form a comprehensive view of risks.
Summary
- IT Governance and Management
- Policies, Procedures, Standards and Guidelines
- IT Governance Frameworks
- Digital Transformation and Balance Score Card
- IT Steering Committee
- Types of Policies and Standards
- DFDs and DSDs
- Risk Management
- Life cycle of Risk Management
- Asset Identification
