Section 5.4 Vulnerability Assessments
As you study this section, answer the following questions:
- What are the top nine areas to research when conducting an assessment?
- What are the seven assessment types?
- What are the limitations of scans?
- Why is vulnerability assessment important?
- How do you interpret the outcomes of vulnerability scans?
- How do web application scanners work?
In this section, you will learn to:
- Scan for vulnerabilities on a Windows workstation
- Scan for vulnerabilities on a Linux server
- Test the security of a web application
The key terms for this section include:
| Term | Definition |
|---|---|
| Active assessment | A network evaluation that is obtained by actively testing the network for weaknesses. |
| Passive assessment | A network evaluation that is obtained by looking for weaknesses through observation with no direct network interaction. |
| Internal assessment | A network evaluation that is obtained by testing and analyzing processes and systems inside the network. |
This section helps you prepare for the following certification exam objectives:
| Exam | Objective |
|---|---|
| CompTIA CySA+ CSO-003 | 2.1 Given a scenario, implement vulnerability scanning methods and concepts
2.2 Given a scenario, analyze output from vulnerability assessment tools
2.3 Given a scenario, analyze data to prioritize vulnerabilities
2.4 Given a scenario, recommend controls to mitigate attacks and software vulnerabilities
2.5 Explain concepts related to vulnerability response, handling, and management
4.1 Explain the importance of vulnerability management reporting and communication
|
| TestOut CyberDefense Pro | 1.2 Monitor software and systems
2.1 Perform threat analysis
3.3 Perform penetration tests
4.3 Analyze indicators of compromise
|
5.4.1 Vulnerability Assessment Tools
Click one of the buttons to take you to that part of the video.
Vulnerability Assessment Tools 00:00-00:21 As a security analyst, your value depends on your ability to accurately find and fix an organization's vulnerabilities, and your ability to do so greatly depends on using the right tools for the job. In this video, I'll go through a few of these tools that are available to you.
Network Scans 00:21-01:59 Before we get into that, though, let's talk about network scans. We use network scans to find live computers on a network, which is information we want if we're doing any kind of remote meeting. Many times, someone gets onto a network through wardialing, which is a technique that uses a modem to dial a large block of phone numbers in an attempt to locate other connected systems. If the scan gets a response, it accepts the connection, and the dialer now has an access point into the network.
When you hear the word modem, your mind might instantly flash back to the days of busy signals and obnoxious connection sounds. Thankfully, we're pretty much past the era of dial-up. But modems are still used for fax machines, multi-purpose copiers, and as a backup for high-speed internet. We also see phone numbers used for video and audio meetings, which have become a mainstay in every market vertical. These sessions are susceptible to wardialing unless each session requires a password.
To make sure we're secure on our connection, we can use a very common network scanning tool called ping. Ping works by sending an ICMP message from one system to another. Based on the ICMP reply, we know whether a system is live and how quickly the packets traveled from one host to another. A ping sweep can be used to scan a range of IPs in search of live systems.
Because ping and ping sweeps are common everywhere, administrators should block pings at the firewall or set their IDSs to receive ping alerts. This is a basic part of hardening a network.
Qualys Vulnerability Management 01:59-02:27 Now, let's get deeper into some of the specific tools at our disposal. Let's start with Qualys Vulnerability Management, which is a cloud-based service that keeps all your data in a private virtual database. Qualys is easy to use, and it can scan large enterprises. Data is always encrypted during transit and at rest, so even though Qualys is cloud-based, your data is secure. Only their scanners reside on your network.
Nessus Professional 02:27-02:47 Second, is Nessus Professional. This is an assessment solution that actually resides on your network, making it more suitable for smaller organizations. It scans for known vulnerabilities, malware, and misconfigurations. Nessus also provides reporting, remediation, and ongoing monitoring.
Open-Source Tools 02:47-03:38 Next, let's look at two free, open-source tools that you can modify and share. The first is OpenVAS, which is a vulnerability scanner that has more than 50,000 vulnerability tests with daily updates. It's capable of various high-level and low-level internet protocols, and it allows both unauthenticated and authenticated testing.
Second, we have Nikto, which is a web-server scanner. Nikto tests for outdated versions of more than 1,250 servers and scans for more than 6,000 files and programs that have the potential to be exploited. It also checks for version-specific problems on more than 270 servers. It's important to note that this tool creates a large footprint by leaving a high volume of entries in the web server's log files.
Mobile Tools 03:38-03:52 Now, let's focus on the top mobile tools for vulnerability assessment. Mobile might not be the first thing that comes to mind when you think of network hardening, but you have to assess mobile devices to cover all your bases.
Retina CS for Mobile 03:52-04:11 The first tool is called Retina CS for Mobile, and it provides comprehensive vulnerability management for smartphones, tablets, and mobile devices generally. It can scan, prioritize, and fix smartphone vulnerabilities as well as report its findings from a centralized data warehouse.
SecurityMetrics Mobile 04:11-04:37 The second tool is called SecurityMetrics Mobile, and it also detects mobile device vulnerabilities. This program can help you protect customers' data and avoid unwanted app privileges, mobile malware, connectivity issues, threats to device storage, and unauthorized account access. You can expect a report containing a total risk score, a summary of revealed vulnerabilities, and remediation suggestions.
Nessus 04:37-05:05 The third tool is Nessus. It can be difficult to know all of a network's vulnerabilities if there are mobile devices connecting and disconnecting between testing. Nessus offers scanning that shows you which devices are unauthorized or non-compliant. It also alerts you to outdated versions of Apple iOS, and it highlights devices that haven't connected for a long period of time. This gives you a clearer picture of what's actually going on on your network.
Net Scan 05:05-05:16 The fourth tool is Net Scan. Net Scan provides discovery through network and port scanning. It looks for vulnerabilities, security flaws, and open ports as well.
Network Scanner 05:16-05:31 Finally, we have something called Network Scanner. This one gives you an overview of a network's overall usage. Network Scanner generates security issues and vulnerability reports that you can autosave and back up to your own web storage.
Assessment Reports 05:31-07:08 So, you can see that we have a lot of options for generating different assessment reports. Let's take a minute to cover the information you can get from one of these reports in more detail. Assessment reports provide detailed information on the vulnerabilities found after a scan. For example, they specifically cover scan information, target information, and results. The scan information includes the scanning tool's name, its version, and the network ports that were analyzed. The target information lists
the target system's name and address. The results section gives you a complete scanning report and contains subtopics that include target, services, classification, and assessment.
Let's look at each of the subtopics. The first is target, which includes each host's detailed information. The services section defines the network services by their names and ports. The classification section shows the scan's origin. And finally, in the assessment section, you find the scanner's assessment of each vulnerability. There are also two categories of reports to know. First, there's a security vulnerability report. It gives you information on all scanned devices and servers, including open and detected ports, new vulnerabilities, and suggestions for remediation with links to patches. Second, is a security vulnerability summary. This covers every device or server that was scanned and gives you information about current security flaws, their severity levels, and a summary of resolved issues.
Summary 07:08-07:24 That's it for this lesson. To review, we covered network and mobile vulnerability assessment tools. We also reviewed what to expect from an assessment report.
5.4.2 Vulnerability Assessment Tool Facts
As a security analyst, it is critical for you to accurately find and fix vulnerabilities in an organization's systems. To do this, you need the right tools.
This lesson covers the following topics:
- Vulnerability scanning methods overview
- Proprietary assessment tools
- Open-source assessment tools
- Mobile tools
- Assessment reports
Vulnerability Scanning Methods Overview
Vulnerability scanning is an integral part of cybersecurity. It helps detect and identify weaknesses in networks and systems, allowing organizations to take steps to protect themselves from malicious actors. There are several different methods of vulnerability scanning, each with its advantages and disadvantages.
- Network scanning looks for exposed services, open ports, and misconfigured devices.
- Application scanning seeks to detect vulnerabilities in web applications.
- Operating system scanning looks for vulnerabilities in operating systems.
Each of these methods helps to provide a complete picture of an organization's security posture, allowing for better protection against cyber threats. The following video gives a quick overview of vulnerability scanning methods:
Video
Click one of the buttons to take you to that part of the video.
Implementing Vulnerability 00:00-01:13 James Stanger: When it comes to vulnerability in management, you really need to make sure you use that vulnerability scanner in the best way, there are best practices here, and to tell us about that, we've got a veteran in this, in Brian Calkin. Brian, how are you doing?
Brian Calkin: I'm great, James. How are you?
James Stanger: Doing great, man. Doing great. Tell us a bit about yourself and some of your experience when it comes to vulnerability management, and let's get into what it means about asset discovery and all sorts of fun things like that.
Brian Calkin:Yeah, sure. So, just real quick on me. In cybersecurity the past 20 years or so, started off as a SOC analyst but then quickly rose up through the ranks, and had various leadership management roles within a couple of different organizations. But part of the time, I was the person in charge of our instant response team and also, we had a consulting arm of the organization that handled, primarily vulnerability scanning and vulnerability management, so I've got some good experience there.
James Stanger: And, you've done a lot of work, and worked with the Center for Internet Security, right, the CIS folks?
Brian Calkin: Yeah, absolutely. A long-time CIS employee, started way back in 2010, I think, and still an employee there today.
Vulnerability Scans 01:13-05:55 James Stanger: And, so let's talk about when it comes to doing this. You've got to figure out what assets you're gonna work with. How do you discover those things, and what are some of the best practices involved in that?
Brian Calkin: Sure. I think it's a couple of different approaches. I think, you know, depending on the vantage point you wanna take, I think that's one of the best vantage points you can take, is that of the attacker out there.
James Stanger: Mm.
Brian Calkin: And so you need to start with something like an external vulnerability scan that's gonna take a look and see what the attacker can see, somebody on the outside of your organization, discover things like your public facing, web servers, DNF servers, those types of things; anything public facing, or Internet facing. I think then, from there, you'd wanna move to an internal vulnerability scan, to identify - should someone breach that perimeter and they inside, what might they be able to do within your network, and so internal vulnerability scan will help kind of answer some of those questions for you.
James Stanger: Great. There's credential and then there's non-credential types of scans, tell us a bit more about that, and what [INAUDIBLE]
Brian Calkin: Yeah, absolutely. I think that - again, it depends on your goals, for instance, if you are running a non-credential scan, you are basically deploying a vulnerability scan inside the network that has - again, this sort of a same vantage point of an attacker, that doesn't have any access to anything, you're sort of just poking around, and looking at, seeing what they can find, but inevitably, they're going
to likely run up against things like, host based firewalls on work stations and their view will be limited. I think a much better [CLEARS THROAT] approach would be to do a credential vulnerability scan, which actually gives the vulnerability scanner software access to the systems to be able to log in, and you just get a much richer data set, in terms of, you know, running software or open vulnerability, those types of things on the end points themselves.
James Stanger: So you can plug in, user name, password, public keys etcetera, right, to figure?
Brian Calkin: Yeah, absolutely. You can do that. I mean, there's also an approach where you can use agents, you can actually install software and end points, you can run vulnerability scans with actual agents as well, and so you know that the technology has certainly matured over the years, and it's [INAUDIBLE]
James Stanger: It has indeed.
Brian Calkin: Yeah.
James Stanger: You mentioned something earlier about, like, depending on the goal that you have in mind, 'cause there are these frameworks out there, for example, those for the Center for Internet Security, there's the PCI DSS, Payment Card Industry, things like that. OWASP, you know, for real, real heavy into applications. Tell us more about these frameworks, and how you can kinda configure some of these scanning tools for them.
Brian Calkin: Yeah, absolutely. Yeah, so again, speaking on my CIS experience, you know, we actually have a vulnerability scanner within CIS, I called CIS-CAT actually, that will go and it'll perform vulnerability scans. Essentially, vulnerability scans against work stations, looking to see if those end points are configured, check out CIS benchmark best practices. So, a CIS benchmark is essentially just a recommendation, or a hardening guide and how you would securely configure out a Windows end point, for instance. And so, this vulnerability scanner's looking to see how in-compliance or not, that given system is.
James Stanger: And you can tune them, and set them up for, for example, Payment Card Industry, or for OWASP, or what have you, just kinda take those into consideration.
Brian Calkin: Yes, exactly, yeah. Yeah, depending on the particular-- obviously, if you were processing credit card payments, you have certain regulations you must abide by, and so you need to make sure that the vulnerability scanner that you are using is able to account for that, so you'd wanna--
James Stanger: What are some of the special considerations, for example, scheduling and during work hours, or not during work hours, things like that, sensitivity levels, stuff like that?
Brian Calkin: Yeah. The nice thing about vulnerability scanners is they can be scheduled, I think, generally, the best practice recommendation would be to schedule these types of things off hours. The reason for that is because, depending upon the, we'll say the level of aggression that the scanner has, [LAUGHTER] if it's a very, you know, highly-- I say aggressive, meaning it's trying to dive as deep as possible, find as many vulnerabilities as possible, you get a super rich data source and a super great report back, but the risk is, you could potentially cause the system to freeze, or to lock, or to go down, and so if you're running critical loads during the day, you obviously don't want those systems to go down. And so, best to run those more sort of aggressive scans after hours, you know, after business hours and schedule accordingly.
James Stanger: So, there's certain sensitivities and performance levels, you gotta think about and...
Brian Calkin: Yeah.
James Stanger: ...Worry about a little bit?
Brian Calkin: Yeah, absolutely. The goal is to find vulnerabilities and not introduce more problems into your infrastructure. You're trying to solve problems, not cause them.
James Stanger: That makes perfect sense. Brian, thanks so much for you time, man, I really appreciate it.
Brian Calkin: Yeah, you're welcome. Thanks, James.
Proprietary Assessment Tools
Here are two common tools for overall scanning, reporting, remediation, and ongoing monitoring.
Nessus Professional
Nessus, produced by Tenable Network Security ( tenable.com/products/nessus ), is one of the best-known commercial vulnerability scanners. Nessus scans for known vulnerabilities, malware, and misconfigurations. It also provides reporting, remediation, and ongoing monitoring. It is available in the following options:
- Nessus Manager for on-premises installations
- Tenable Cloud for a cloud solutions
- Nessus Professional version that is designed for smaller networks
The product is free to use for home users but paid for on a subscription basis for enterprises. As a previously open-source program, Nessus also supplies the source code for many other scanners. Default scans can be performed using the plug-ins from Nessus's subscription feeds. A custom plug-in can be created using Nessus Attack Scripting Language (NASL). Nessus Professional allows remote scanning of hosts while Nessus Manager and Tenable Cloud can work with locally installed agent software.
Here is an example of an agent scan run from Nessus Manager:
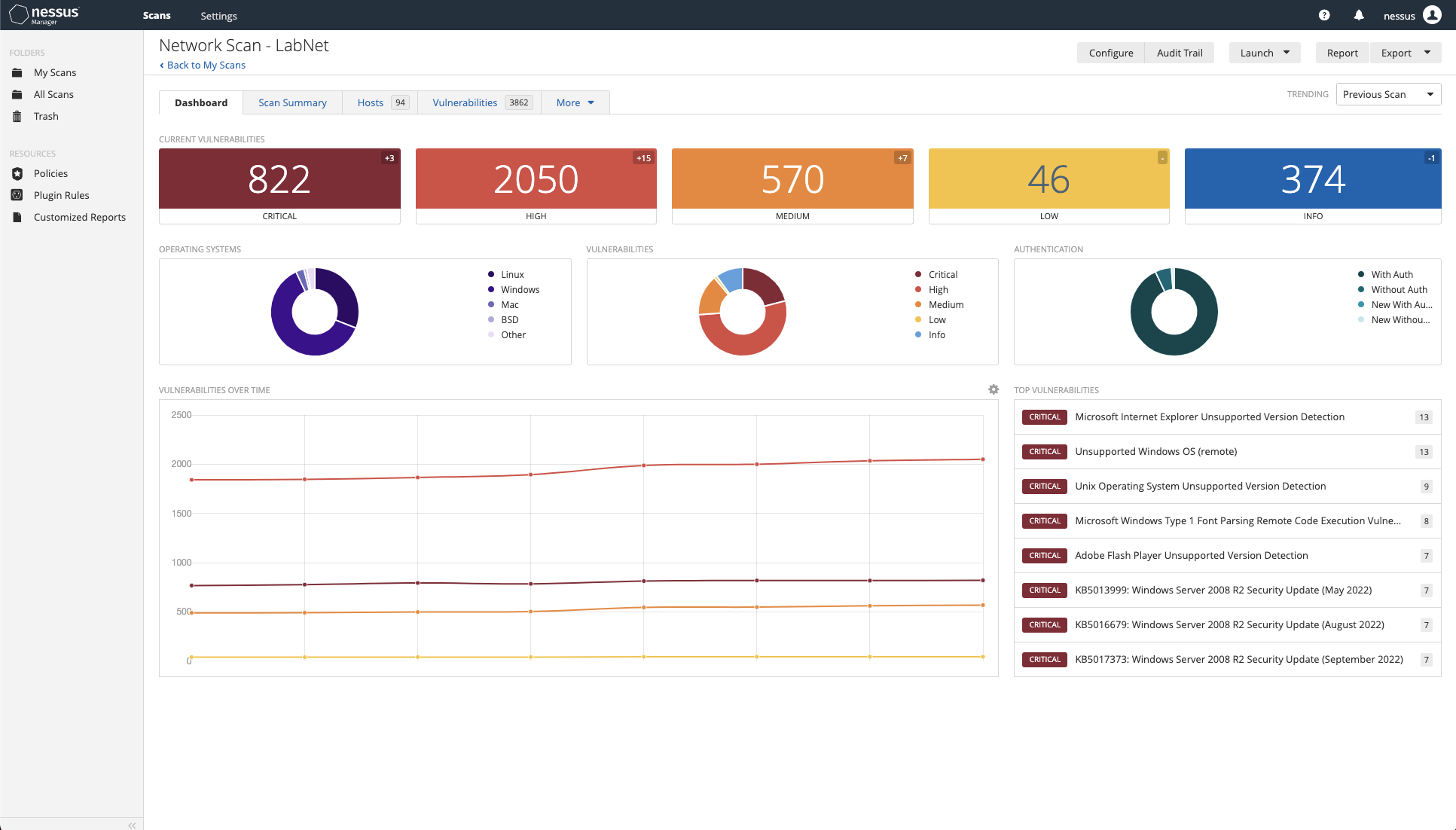
Details
The top section lists the current vulnerabilities as follows: Critical: 822, High: 2050, Medium: 570, Low: 46, Info: 374, Total: 3862
The middle section shows the ring graphs for operating system comparison, vulnerability comparison, and host count comparison.
The bottom section lists the top hosts and top vulnerabilities.
Scan dashboard in Tenable Nessus. (Screenshot courtesy of Tenable Nessus tenable.com .)
Select the Vulnerabilities tab to dig deeper into the scan results. It is obvious that most issues are due to patch management (or rather the complete lack of any sort of patch management). The other significant issue includes software that is no longer supported by Microsoft.
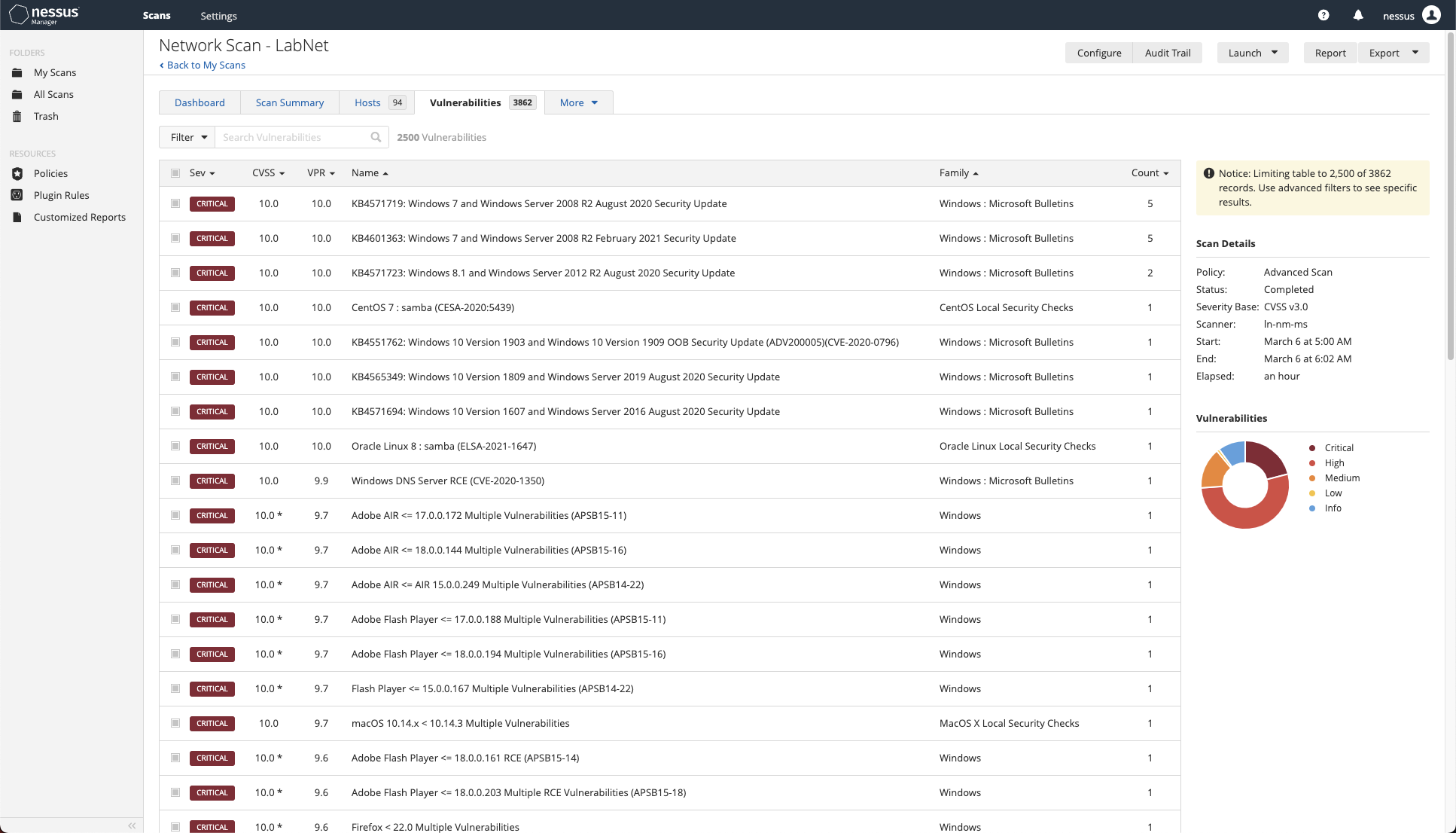
Examining the critical findings. (Screenshot courtesy of Tenable Nessus tenable.com .)
Select one of the items to view the report to determine how significant it really is:
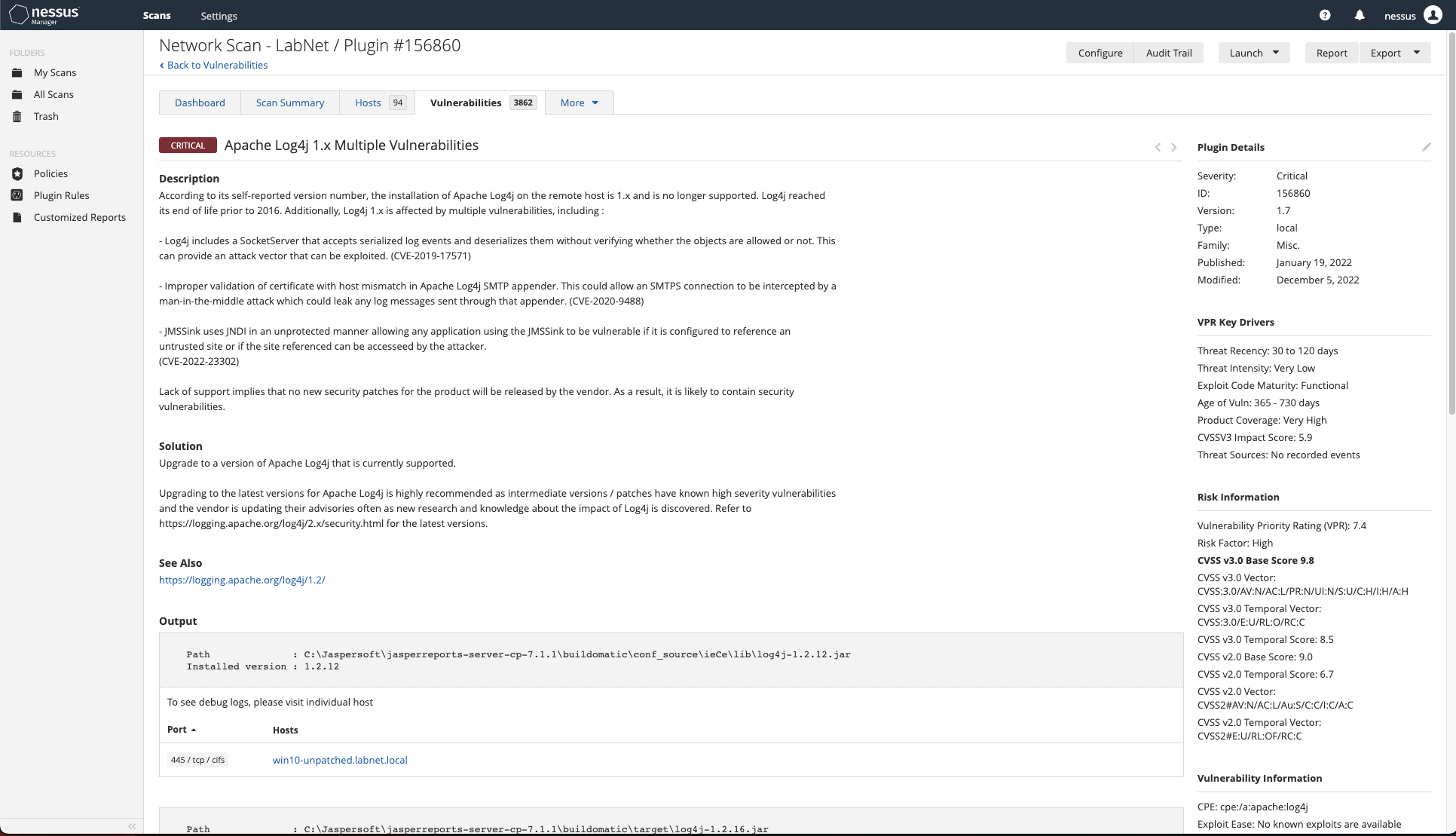
Investigating one of the findings — note the CVSS metrics on the right. (Screenshot courtesy of Tenable Nessus tenable.com .)
It can also be helpful to check other sources to find out whether any exploits have been developed. This SANS page displays a sample warning. As you can see, patching this exploit is a top priority (and luckily should be very easy to do). If the exploit were found on a web server, it would be even more serious. To remediate these systems, we would run Windows Update, ensure that Windows Update is properly scheduled in the future.
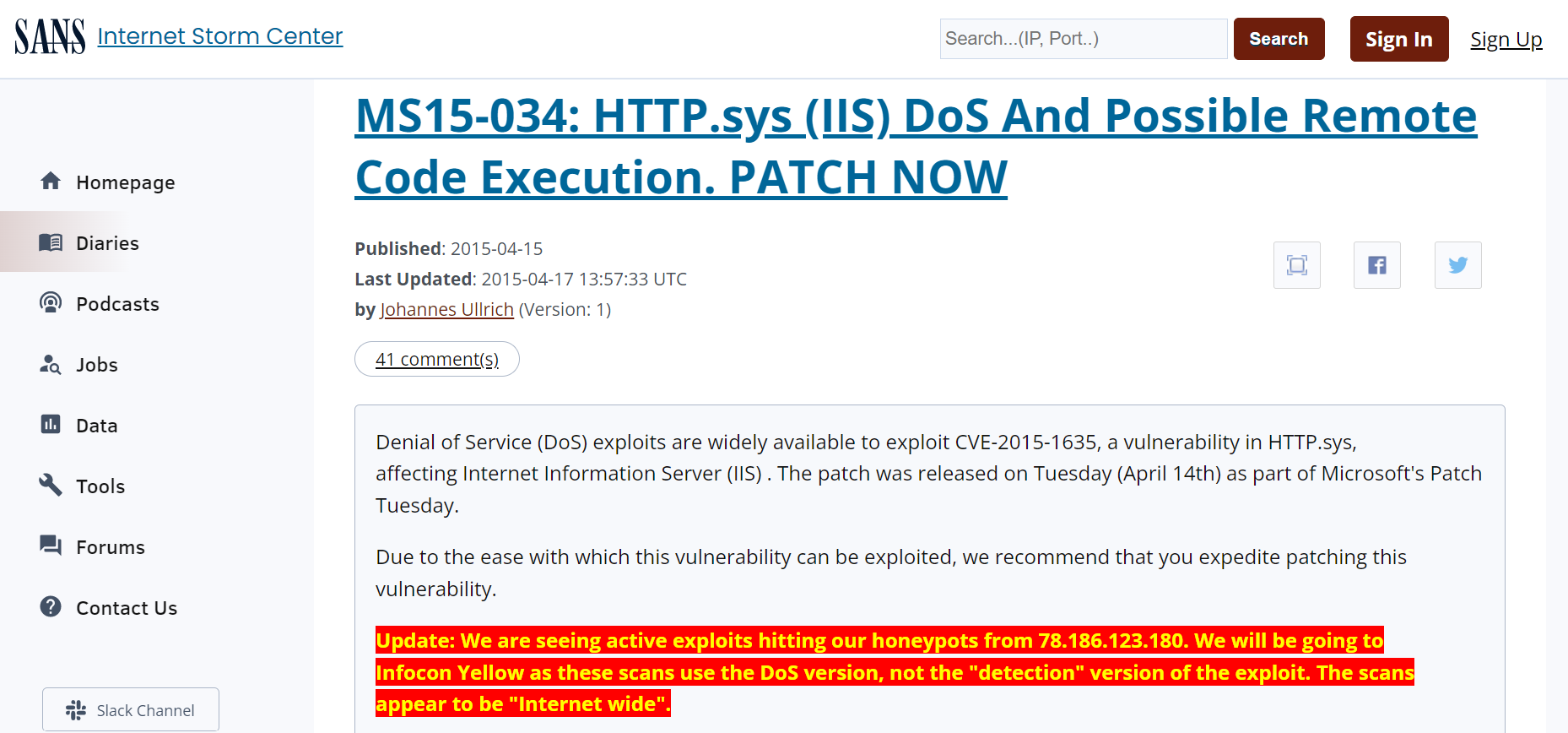
Detail
There is a search box and a sign in/sign up option at the top. The heading at the top reads, M S 1 5 colon H T T P dot sys left parenthesis I I S right parenthesis DoS and possible remote code execution. PATCH NOW. The information on the published date, last updated date, and last published by is given below the heading. A box below has several lines of text.
Scan dashboard in Tenable Nessus. (Screenshot courtesy of Tenable Nessus tenable.com .)
After improving the patch management, upgrading the legacy Windows hosts to supported versions, and removing unsupported software, run the scan again and work from any findings that remain.
Qualys Vulnerability Management
Qualys Vulnerability Management is a cloud-based service that keeps data in a virtual private database. Qualys vulnerability management:
- Is easy to use and is capable of scanning large enterprises.
- Encrypts data during transit and at rest.
- Uses sensors that users install at various points in their network which:
- Upload data to the Qualys cloud platform for analysis.
- Can be implemented as agent software running on a host, as a dedicated appliance, or as a VM running on a platform such as VMware.
- Other deployment methods include:
- Passive network sensors.
- Out-of-band sensors for air-gapped hosts.
- Agents for cloud infrastructure and container apps.
In addition to the vulnerability scanner, Qualys also has an option for web application scanning.
Open-Source Assessment Tools
Open-source tools are free to use. The following table describes two commonly used open source vulnerability scanners.
OpenVAS
OpenVAS scanner ( openvas.org ) is open-source software, originally developed from the Nessus codebase prior to when Nessus became commercial software. The scanner is managed by Greenbone (greenbone.net) and is also available as a commercial (paid) product. OpenVAS is developed to be used on Linux.
- Has more than 50,000 vulnerability tests with daily updates.
- Handles various high-level and low-level internet and industrial protocols.
- Performs unauthenticated and authenticated testing.
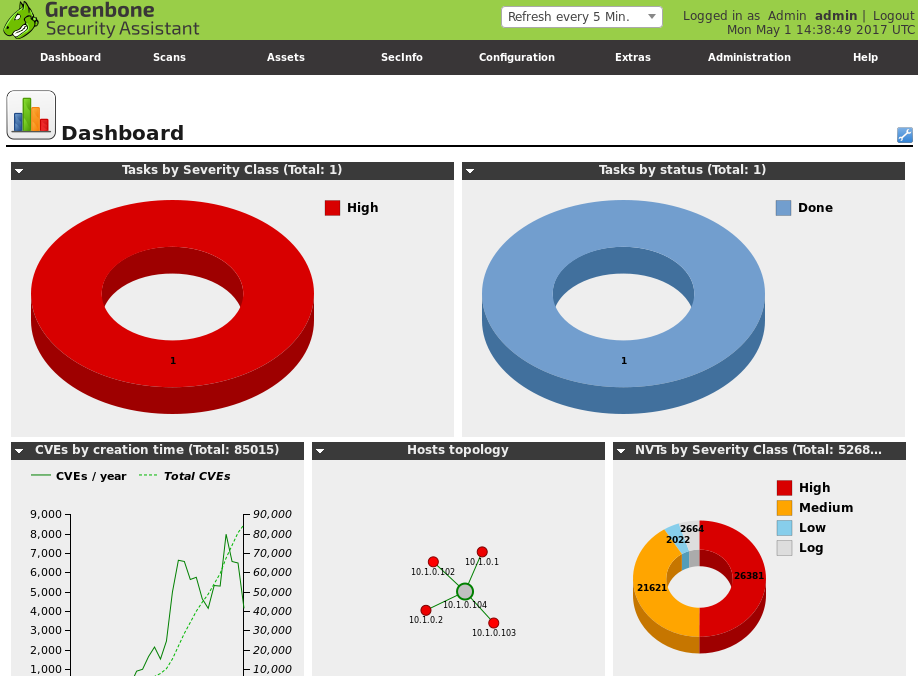
Detail
Three 3 dimensional ring graphs are titled, tasks by severity class, tasks by status, and N V Ts by severity class. A line graph is titled, C V Es by creation time and a point to point graph is titled, hosts topology.
The user interface of the OpenVAS vulnerability scanner. (Screenshot courtesy of Greenbone.)
Nikto
Nikto is a web server scanner. It:
- Tests for outdated versions of more than 1250 servers.
- Scans for more than 6,000 files and programs that can be exploited.
- Checks for version-specific problems on more than 270 servers.
Nikto creates a large footprint by leaving a high volume of entries in the web servers log files.
Mobile Tools
Mobile devices are important to include in a thorough assessment. The following table describes vulnerability management tools for mobile devices.
| Tool | Description |
|---|---|
| SecurityMetrics Mobile | Detects vulnerabilities in mobile devices. You can use it to:
|
| Nessus | Offers the following services:
|
| Net Scan | Provides discovery through network and port scanning. Net Scan can find:
|
| Network Scanner | Provides a view of how the network is used. Network Scanner:
|
Assessment Reports
The following table describes the two types of assessment reports.
| Report Type | Description |
|---|---|
| Security vulnerability report | The security vulnerability report includes:
|
| Security vulnerability summary | The security vulnerability summary report includes every device or server that was scanned. It provides information on:
|
Assessment reports provide detailed information on the vulnerabilities that are found in the network. The following table describes the three types of information provided.
| Information Type | Description |
|---|---|
| Scan information | The name of the scanning tool, its version, and the network ports that have been scanned. |
| Target information | The target system’s name and address. |
| Results | The results provide a complete scanning report. Sub-topics of the scanning report are:
|
5.4.6 Vulnerability Scan Analysis
Click one of the buttons to take you to that part of the video.
Vulnerability Scan Analysis 00:00-00:17 Vulnerability scanners aggregate different data points, allowing security analysts to review vulnerabilities and implement mitigation strategies. In this lesson, I'll go over some vulnerability scans and how we use them for different purposes.
Web Application Scanners 00:17-00:41 Let's first start with scans for web applications. A web application scanner goes over apps to analyze security details and produce a report showing any discovered vulnerabilities. This report could include sensitive content data or other important information. Generally, these scans consist of three parts: web crawling, link discovery, and data analysis.
OWASP ZAP 00:41-01:17 The Open Web Application Security Project, better known as OWASP, has created an open-source tool called OWASP ZAP, or OWASP Zed Attack Proxy. This is a web application tester that's based on a man-in-the-middle proxy, which might also be referred to as an on-path proxy. In short, this tool places itself between the web application and the tester's web browser, and grabs messages that are intended to go between the app and the browser. It then inspects the data, modifies the contents if necessary, and sends the packets to their original destination.
Burp Suite 01:17-01:46 Burp Suite is a web scanner that has multiple unique features. This scanner looks for common vulnerabilities, like cross-site scripting and SQL injections, usually from the OWASP Top 10 list. This tool maps content, application logins, and other server-side action. It can even perform out-of-band techniques that allow the user to discover server-side issues while being completely invisible to the apps' external actions. It even reports vulnerabilities that occur asynchronously on post-scan completion.
Nikto 01:46-02:16 Nikto is a web server scanner. It tests more than 1,250 outdated versions of web servers and scans more than 6,000 files and programs that can be exploited. It also checks for version-specific problems on more than 270 servers. It's important to note that this tool creates a large footprint by leaving a high volume of entries in the web server's log files. If a hacker uses this tool against your web server, diligent log auditing should alert you very quickly.
Arachni 02:16-02:46 Arachni is an open-source web scanner that works in standard environments as well as highly complex web application environments, all while giving the user multiple deployment options. Arachni evaluates each web application individually, which in turn allows it to customize each request to specific technologies. This results in only relevant payloads being injected during checks, leading to smaller bandwidth usage, less stress to the web application, and faster and more accurate scans.
Infrastructure Vulnerability Scanners 02:46-03:07 Now, let's talk about vulnerability scans for deep infrastructure. In essence, vulnerability scanners are just tools that allow security analysts to check if networks, systems, and applications have security weaknesses that could make them vulnerable to attacks. Scanning a system's internal workings is often mandated by industry standards and government regulations.
Nessus 03:07-03:30 Nessus Professional is an assessment solution that resides on your network. This makes it more suitable for smaller organizations. It scans for known vulnerabilities, malware, and misconfigurations. Nessus also provides reporting and remediation as well as ongoing monitoring. Nessus lets you customize scans to fit your network's needs, and its results are easy to read.
OpenVAS 03:30-03:49 OpenVAS is a vulnerability scanner that has more than 50,000 vulnerability tests with daily updates. It's capable of various high-and low-level internet protocols as well as both authenticated and unauthenticated testing. OpenVAS also allows performance-tuning to improve a scan's accuracy and speed.
Qualys 03:49-04:11 Qualys Vulnerability Management is a cloud-based service that keeps all your data in a private virtual database. Qualys is easy to use, and it can scan large enterprises. Data is always encrypted during transit and at rest, so even though it's cloud-based, your data remains secure. Only the scanners themselves reside on your network.
Summary 04:11-04:31 That's it for this lesson. In this lesson, we learned about different vulnerability scanner categories. We learned about scanners that target web applications and scanners that do deep dives into an enterprise's internal infrastructure in search of known vulnerabilities and weaknesses.
5.4.7 Vulnerability Scan Analysis Facts
This lesson covers the following topics:
- Vulnerability scoring concepts
- Web application scanners
- Infrastructure vulnerability scanners
Vulnerability Scoring Concepts
Vulnerability scoring assigns a numerical score to a computer vulnerability. This score, commonly known as a CVSS score, is used to indicate the severity of the vulnerability and help prioritize remediation efforts. The scoring scheme considers the impact of the vulnerability on the system, the exploitability of the vulnerability, and the availability of mitigating factors such as firewall configurations or operating system patches.
Vulnerability scores are determined by various factors, including the type of vulnerability, the access required to exploit the vulnerability, the ease of exploitation, and the availability of mitigating factors. The score also provides a common language for communication between security professionals and vendors.
Video
Click one of the buttons to take you to that part of the video.
Analyzing Data to Prioritize 00:00-09:28 James Stanger: Any organization's gonna present vulnerabilities, the question is how do you prioritize your response to those vulnerabilities? Well, to teach us more about that, we've got MITRE'sown Cat Self, how are you doing, Cat?
James Stanger: I am excellent, thank you so much for having me here.
James Stanger: Ah it's great to have you here. Cat is the adversary emulation engineer for MITRE. Tell us a bit about what you do at MITRE and then let's talk for a second about a friend of ours, Tim Crothers. But, go ahead and tell us about yourself and what you do there.
Cat Self: Well, I am a Principal Adversary Emulation Engineer. What that means is I pay attention to, in my case in MITRE, we're very much about, like, making the world a better place. So, most of the projects that I'm on are very specifically open source driven, in order for us to be able to provide all the content and research that we do to the public and private sector. And so, with that said, a lot of what I do is based on open source intelligence and I do lots of research on bad guys, see what's available, and then I work on code to recreate what they do. And then we openly [LAUGHS] [INAUDIBLE] that's made that information.
James Stanger: Yeah, and you've done that for years though. You started in the military, right? And then you went on to do that at Target, etc., and now you're doing it here.
Cat Self: So, fun fact, I don't think there is a one role path for anything. I think, in cyber security, our field, now it's a field, came from a community. It came from a backhanded, like, afterthought of a community of-- oh, we might wanna put file permissions on file servers on Windows, like that was literally one of the first instances that the security, or the admin, was like-- hey, we created this incredible file system to be able to share these files, however, we should probably put a password on this. And the CEO was like-- no, I don't see anyone would do that, right, who would touch my files?
And so we literally right before, like two weeks before release, went in and then grabbed his files. And then the CEO was like-- oh, oh no no no no, we are absolutely adding this protection, hot fix, right now. And so that's where we came from and now we've evolved into being an actual field, which is amazing.
So, with that said, I started off in military intelligence, which is definitely not cyber and had a really great experience with that. And then I moved to software development. From software development, I moved into offensive engineering, which is basically offensive development on a red team.
And then threat hunting, and now I actually do adversary emulation, which is where I take cyber threat intelligence, blend it with the software or offensive engineering, and then also blend it with the threat hunting, so that way I can identify what can you actually see when I'm emulating these adversaries? As that's what I really wanna help build, is the visibility to that and allow the detection, so that way you'll always be able to detect me. And, as I get better, so do your defenses.
James Stanger: And you've got tremendous expertise in the Linux side of things as well as macOS, right?
Cat Self: You know, I wouldn't call it tremendous. I have definitely [INAUDIBLE]
James Stanger:I bet ya, I would haha.
Cat Self: ... in this field. Every time I think I understand something, I find out how much more I have to learn by somebody else.
James Stanger: You know, when it comes to prioritizing vendors, you know, there are ways that you can come up with, as it were, a score. For example, there's the CVSS way to do it, where you look at the attack factors and the complexity and a score from, say, zero to ten, ten being the worst, you know, what the situation is there. You have a particular perspective on how to do this, kind of three different elements that you look for in terms of prioritizing vulnerabilities, how do you go about doing that?
Cat Self: I like taking a more holistic approach. And remember I have an offensive engineering background, so, and a cyber threat intelligence background. So, with that said, my focus is always more like how many more factors really build into this picture? What does the context look like?
So, in prioritizing, a lot of times it's getting the right people at the table, and it's also having the right questions asked. So, with that said, one of the first things is visibility, understanding your attack surface, right. You can't really talk about anything until you actually know what does the world look like in which you're operating in?
James Stanger: Sure.
Cat Self: Once you have that, then you have the stakeholders, the people that actually care. And then you also need to know, what does your company care about? Because every company's different. And everyone has a different problem. And until you actually identify the right problem, you'll be building a solution and a prioritization for something that's irrelevant.
James Stanger: So you're thinking in terms of like asset value, right, the crown jewels, right? That sort of thing.
Cat Self: Crown jewels, yes. The crown jewels. So, kind of once you have some of these preliminary steps, 'cause we like to jump to prioritization, but not having due diligence done prior to that is usually a big falling of a lot of people.
And so making sure all that due diligence is done, the research is done, the right people at the right table, the stakeholders at the right table. And then using that attack surface to be able to frame the questions. Like, you know, the questions that should be asked at those tables of what should we prioritize, should be specifically built around-- who cares about us? What adversaries actually care about us? What do we care about? And where is that intersection between the adversaries that care about us and what we care about? Because that's what we should probably prioritize.
And then you really, like, focus on, like, drilling down and looking at-- let's be honest and transparent with no shame, what do we actually have here? Let's like scan everything, bring everything out on the table, like nothing is too small, needles in haystacks. And then just have to be really honest and then look at, okay, now where are the gaps? What can I not see?
And one way to be able to see what those gaps really look like a lot of times is where adversary emulation and red team and tool assessments really come in. And one thing that I found that really helps with this process on prioritization is you kind of hit two things.
One is gap analysis, you can't prioritize what you don't know about. And the other one is going to be-- what should I care about, right? There are two different aspects. One way I found to able to address the gap analysis is usually through any type of offensive engineering.
So, with that said, there is a three tier approach I would recommend, depending on your company's maturity model, right? Again, you have to have visibility into your environment, in order for this to be able to even be applied. But, in red team operation with Target, which I know we'll get to Tim Crothers' talk soon.
James Stanger: haha.
Cat Self: But, when I was at Target, what our team did was we had a three tier operation. We had what we called known, unknown and throw down. And known was very specifically-- is my anti-virus working? If I download poison ivy which, by the way, is from the nineties, does it catch it?
Right, like this is a very simple thing, but you'd be amazing how many security issues are a result of configuration issues. Did I configure my files correctly? Does my files have root permissions when they absolutely should have a service permission that only operates in a very specific scope? So, doing a known test, right, this is things that should absolutely be caught. Doing an unknown test. Now, unknown tests are usually based on-- what rules to I have in the environment? Like, if I have a very specifically targeted firewall rule, does it trigger? Does it work? Does it block this? Or does it allow this very specific instance in?
You know, typically things are done by admins as testing to verify their tools. But they absolutely can be done to be able to ensure that the security controls are also working. And then the third one is throw down, which is my personal favorite, primarily 'cause I'm an adversary engineer.
And that's where you take an adversary, you do a full kill chain, which Lockheed Martin has coined that term as kill chain. Or FireEye has, well now they're Trellix, they have what they call the attacker life cycle, which is based the events of an attacker based on observed events, like their flow of pattern of behavior.
You take one of those and then you run that full gauntlet against your environment to be able to see how does your people and process respond to this? Not just your tools. And then where are your gaps in that regard? So those are three helpful operations that I found to be able to build as a organization matures, those three operations will tend to grow with an organization until they've outgrown that.
James Stanger: Well, and see this is so key, because you're basically describing context awareness, right? And, like you said, visibility, call it a single pane of glass if you want. But, and then the impact, you put those two things together and then you really know, you know, where to go and what to prioritize, makes perfect sense to me.
Cat Self: Vulnerability management, I feel like it's a great place to start, it's not the end. I think we see these really great tools, like the CVEs, right? And then we have all these other different Metrix and they're phenomenal. But, nothing in this world is perfect by itself, like it's a combination, it's a marbled cake. And it's finding out that right marbling that works for your organization that really makes things effective.
James Stanger: I love that, I love that. I'm gonna use that, it also makes me a little hungry too, but that's okay [LAUGHS]. Well Cat, thank you so much for your time on this, describing how you go about prioritizing vulnerabilities, really appreciate it.
Cat Self: Absolutely, it was an honor to be here. Thank you.
Web Application Scanners
A web application scanner analyzes web applications looking for security vulnerabilities, malware, and programming issues. It produces a report showing any vulnerabilities discovered.
The reported data may include sensitive content as well as analysis of the gathered data. Generally, these scans consist of three parts:
- Web crawling
- Link discovery
- Data analysis
Many web application scanners use an interception proxy. An interception proxy analyzes how web applications operate by controlling and displaying the data and code that passes between a client (browser) and a web application. The proxy intercepts inbound and outbound communication for review or modification before processing or forwarding it. This behavior allows for potent application testing and evaluation. An intercepting proxy is used in dynamic code analysis and is an essential tool for pen-testing and attacks. The following subsections provide a review of four web application scanners.
Burp Suite
Burp Suite is a proprietary interception proxy and web application assessment tool. It is a very popular tool for analyzing and exploiting web applications and is developed and maintained by PortSwigger Web Security ( www.portswigger.net ). Burp Suite is available as a feature-restricted community edition and a subscription-based professional edition. Most advanced and automated features are only available in the professional edition.
Burp Suite includes an integrated browser pre-configured to use the intercepting proxy. Browser activity is captured, or "intercepted," and displayed on the Proxy Intercept tab. The proxy controls browsing activity, so each request is "held" until the tester is ready to proceed. This behavior allows the request to be inspected and potentially modified to manipulate the web application's operation. Burp Suite can:
- Perform automated tasks such as:
- Content discovery
- Fuzzing
- Password attacks
- Injection attacks
- Vulnerability scans
- Modify request values, such as the following, before sending them on:
- content-type parameters
- cookie values
- data values
- Maps content, application logins, and other server-side action.
- Can perform out of band techniques that allow the user to discover server-side issues.
- Is completely invisible to the app's external actions.
- Reports vulnerabilities that occur asynchronously after scan completion.
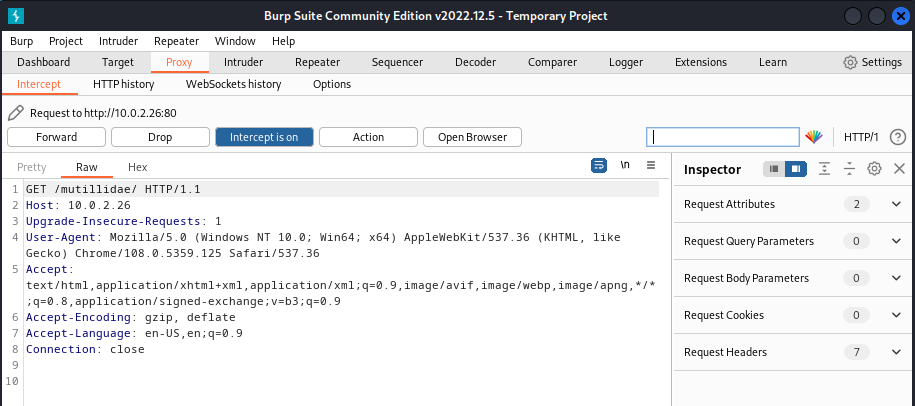
Detail
The intercept is on button is selected. Below that the raw tab is selected. It is followed by the information on host, requests, and user agent. The menu on the right titled inspector shows the number of request attributes, request query parameters, request body parameters, request cookies, and request headers.
Viewing requests made by the browser in Burp Suite. (Screenshot Burp Suite Community Edition from PortSwigger - www.portswigger.net )
Intercepted content can be manipulated by the Intruder feature of Burp. Intruder can quickly identify the vulnerable elements on a page and provide numerous automated methods to exploit them. This screen capture shows how Intruder has identified three potentially vulnerable elements on a login page and highlighted them in green.
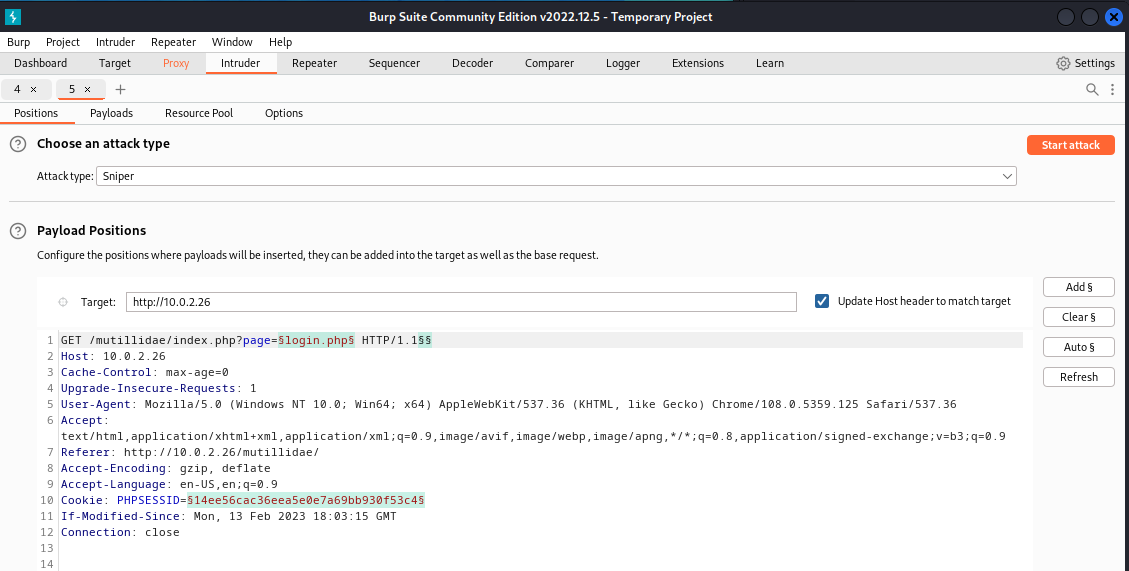
Details
The positions tab is selected from the 4 options below. The page is divided into 2 sections titled, choose an attack type and payload positions. The box to input the attack type is present in the top section along with a start attack button. The bottom section has a box to input the target. The box is followed by few lines of information. Add, clear, auto, and refresh buttons are on the right.
Using Burp Suite Intruder to identify potentially vulnerable page elements. (Screenshot Burp Suite Community Edition from PortSwigger - www.portswigger.net )
The web application can then be attacked using different methods, such as sniper in this example, and a summary of results is provided on the dashboard for review after completion. The summary report provides details for each identified issue, which can be further evaluated using other tool features.
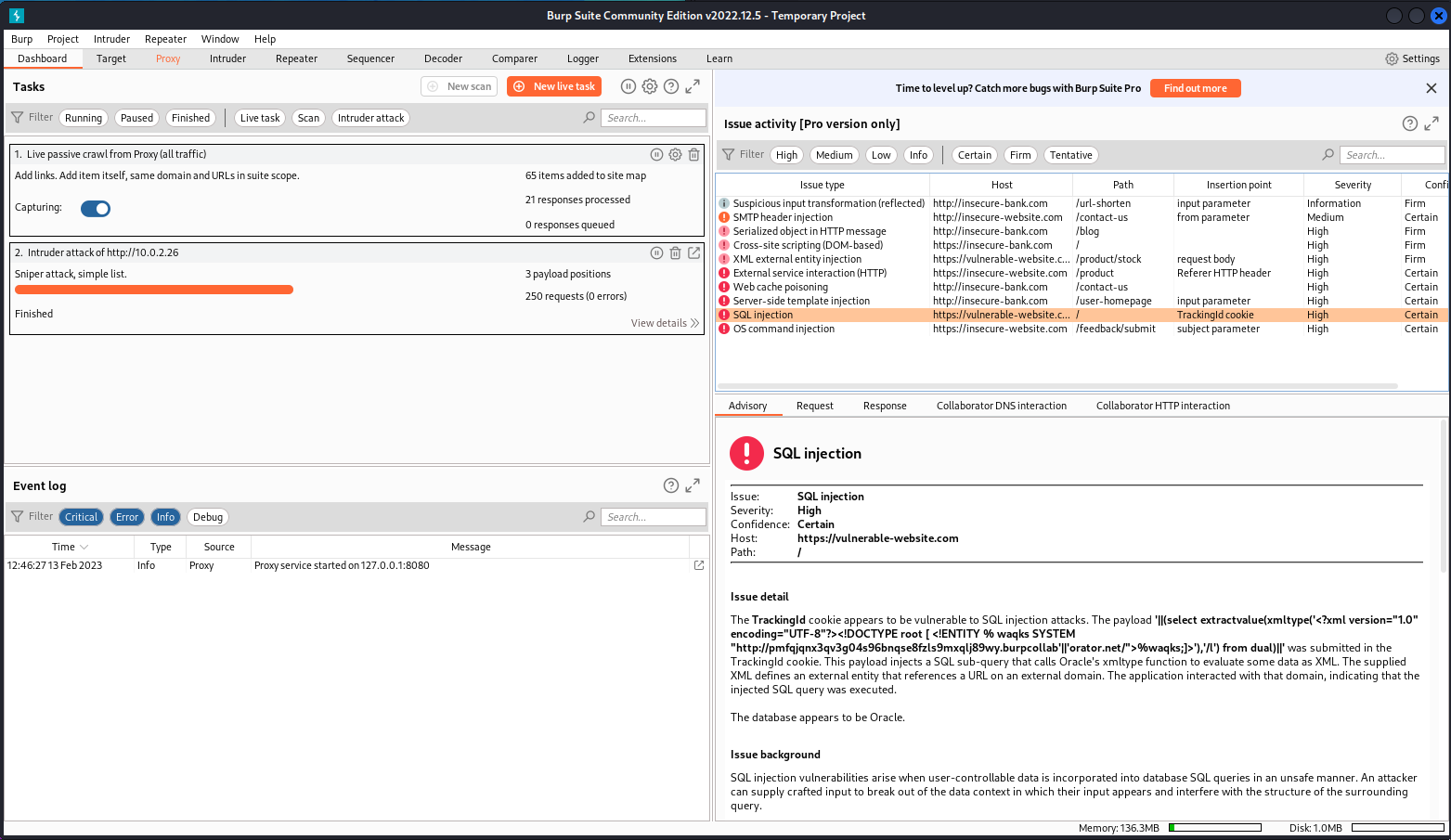
Using the dashboard to review issues discovered with the Burp Suite sniper attack feature. (Screenshot Burp Suite Community Edition from PortSwigger - www.portswigger.net .)
Burp Suite is a very powerful and feature-rich tool. PortSwigger Web Security offers free learning material to help pen testers and analysts increase their knowledge of web application technologies and the features available in Burp Suite. The PortSwigger Web Security Academy website is https://portswigger.net/web-security .
The following video describes the process of analyzing Burp Suite output.
Video 2 - 5.4.7 Vulnerability Scan Analysis Facts
Click one of the buttons to take you to that part of the video.
Analyzing Burp Suite Output 00:00-04:08 Burp Suite is an interesting little application not only because of its name but because of what it does. But before we get into what that application is let's talk about what you pointed at and it's effectively the browser and the web server, okay. Cuz it sits in the middle and listens to those connections and you analyze them and learn things about them.
So let me explain. What does the browser represent to the attacker? Well, I mean these days we use our browsers for everything to check email, to administer Cloud services, to buy Rolling Stones tickets whatever that might be. So it is the primary I would argue interstice and that just means the thing that sits in between you and the server.
It also represents an interstice in that hackers like to get in there and see if they can cause problems. So it's a collection of tools really a web browser. We see it as one thing, but actually it's many different things. It's a user interface. It's a rendering engine.
It's a network stack that has interpreters for things like JavaScript, HTML obviously. It has frames, persistence mechanisms like cookies you get the idea. It has data stores from in memory, to cache, to history, cookies, of course, always fun and other elements. So there's the network stack which creates the session and the network sockets which makes the browser interesting in a couple of ways.
One if there's a problem with the code inside of the browser that actually makes the browser then you have the possibilities of things like buffer overflows, or cross-sites scripting, or issues with frames, etc all sorts of fun. But also when it comes to network stack it creates sessions you know logins, okay.
And so it's important to learn the anatomy of a session when a web browser and its network stack and all of that goes and talks to a web server. This is why session identifiers, and user identifiers, session cookies and things that are so important to understand. So let's take a look at the anatomy of a session because you won't understand Burp Suite until you really have a good understanding of this.
So, you could use it UDP or TCP, the old three-way handshake, of course. You got the login parameters, there's GET and POST and what they're used for make sure you understand that well. So the idea is that in a session you've got a username, you've got the user ID.
You've got the session idea and the cookie including the security level and ID information, in this case, I'll be showing you in a Python example. But it's important to understand that as a web client you logging on to check out your email or to a CRM, for example, you send an HTTP request it comes back with a setcookie, okay.
And that's the important information that an attacker would love to get a hold of. And then you send the HTTP request back plus the cookie and some additional information and then the response comes and you have a session. Well using Burp Suite it's possible to listen in on those kinds of communications.
Not necessarily to conduct a man-in-the-middle attack against a poor victim and the web server not necessarily. But you use it to understand how a web server talks if you're gonna attack one or if you are auditing one and analyzing how it works. You can listen in on how your browser connects to the web server and learn quite a bit about how it talks.
And then if you understand how it talks and communicates and if it has kind of a problem in securely talking back and forth, then you can go in and identify that problem as a security analyst. So Burp Suite is a way to inspect all of those web sessions.
And so it's a bit of a sniffer. It's kind of a proxy server. It acts as a proxy at any rate. I shouldn't say it's a proxy server but it acts as a proxy. Because what you'll do is you'll connect your browser to Burp Suite and then Burp Suite goes and connects to the web browser and then it intercepts those connections and listens carefully.
Example 04:08-07:20 Quick overview of attack types to think about cross-site scripting, watering hole, and SQL injection. The BeEF browser different than Burp Suite does a nice watering hole injection attack for example. And so we can look and see what kind of susceptibility a web session might have to cross-site scripting or SQL injection using Burp Suite.
Because what we can do here is take a look at the session ID as it's happening. So what I've done here in this screenshot is I've configured my web browser to talk to Burp Suite first and then Burp Suite then forwards the connection to the web server and then back again, and this way I was able to get the setcookie, okay.
And this is important information because what I've done is I've told Burp Suite to act as a proxy and intercept the connection. And as my web browser goes through Burp Suite and then through their this here is where I've connected. You can see I've configured my browser in a simple way to go through port 8080 into Burp Suite.
What I can do as an analyst is then I can identify the combination of username and password. I'm not trying to login or hack into the web server I'm simply trying to determine exactly the form of the login. Is it POST or GET? What protocol is being used?
What language? What is the referrer? And how the user name and the password are formatted back and forth that's what I'm trying to find. So once again, I'm going through the proxy and then I am able to capture this information. So notice they're using POST that first red underline there they're using POST.
Second, there's the referrer and how that login is working and that login.php is important. In this case, it's a PHP scripting that I'm looking at. And then notice the username and password there and the token. This tells me a few things. This tells me the sequence of how things work.
If I know that sequence I can use another application kind of pivot to another application. I can take this session information and I can take a look at it. Here's a command using slightly different credentials, but it gets the point across. Basically, what I'm doing here is I'm using THC Hydra and I'm logging in as admin, right?
That's cuz I grabbed that username, right? And then I can go in and I can see how that username and password is working. And I can grab that session cookie, From earlier and put that in there into the sequence. So I know the sequence that the web server application wants, so I fill it in and I'm now basically brute forcing this.
So here's an example of where I've gone in and with some simple brute forcing attacks I've been able to go in and crack that particular password for that web server and own it. So Burp Suite is very important simply as a way to investigate how web servers talk.
Once you know how they talk then maybe you can talk that web server into giving improper information or acting improperly. As a security analyst now you've identified an issue that you can flag and fix.
OWASP Zed Attack Proxy (ZAP)
The ZAP is a popular open-source web application testing tool and one of several flagship products produced and maintained by the Open Web Application Security Project (OWASP). ZAP parallels Burp Suite's features and functionality. It has many features to support automated scanning, input manipulation, and API testing. Some of the key features of the OWASP ZAP tool include:
- An intercepting proxy for intercepting and modifying requests and responses between the browser and web application.
- An active scanner that can identify vulnerabilities such as SQL injection and cross-site scripting (XSS).
- A plugin architecture to extend its capabilities, allowing users to create and share custom scripts and plugins.
- detailed reports and alerts to help quickly identify and prioritize security issues.
ZAP provides a browser preconfigured to send all data through the proxy. This screenshot shows captured content from traffic between the browser and web application.
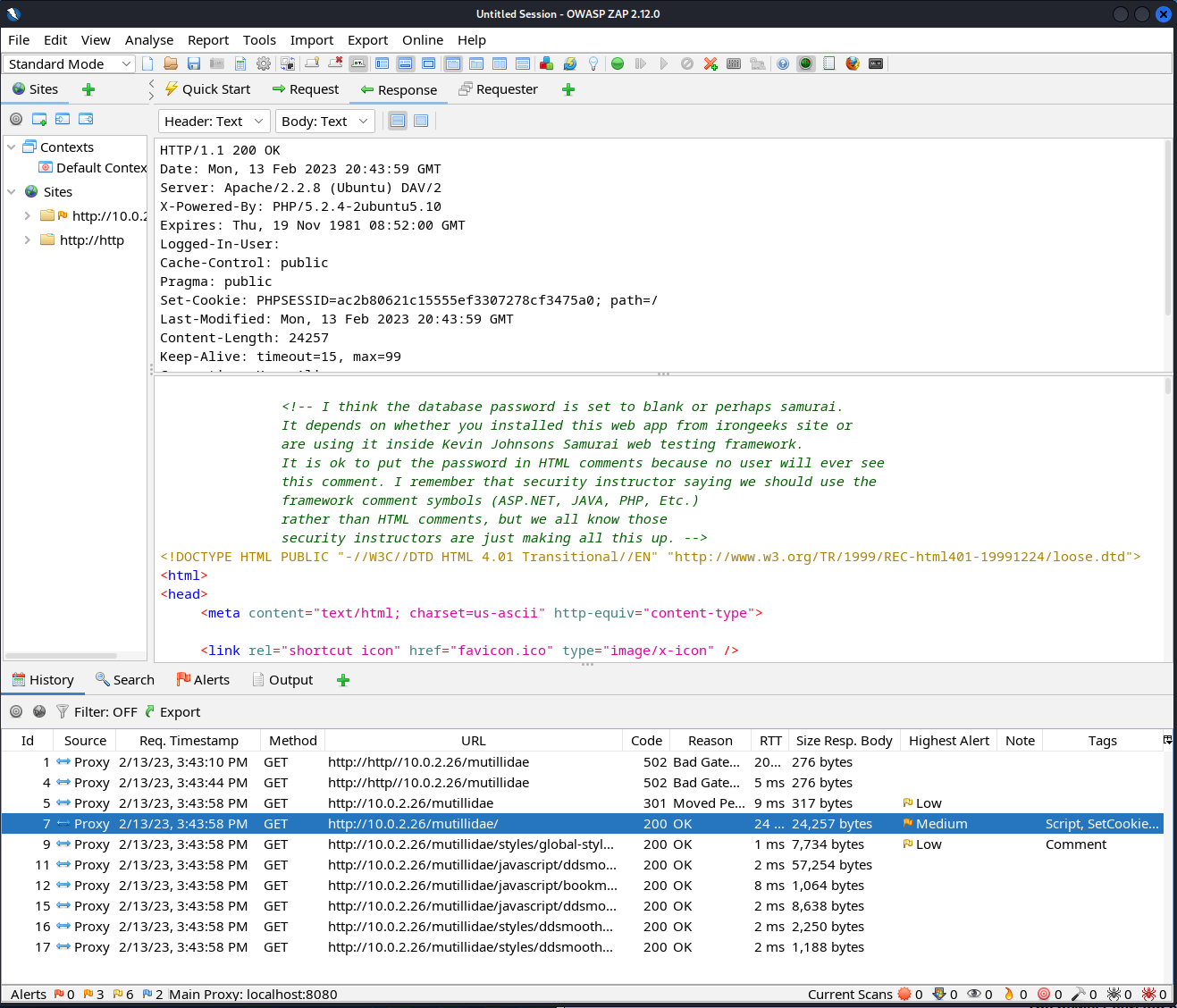
OWASP ZAP proxy displaying captured content. (Screenshot courtesy of OWASP Foundation, Inc.)
Like Burp Suite, ZAP includes scanners to automate the discovery of content and vulnerabilities within a web application.
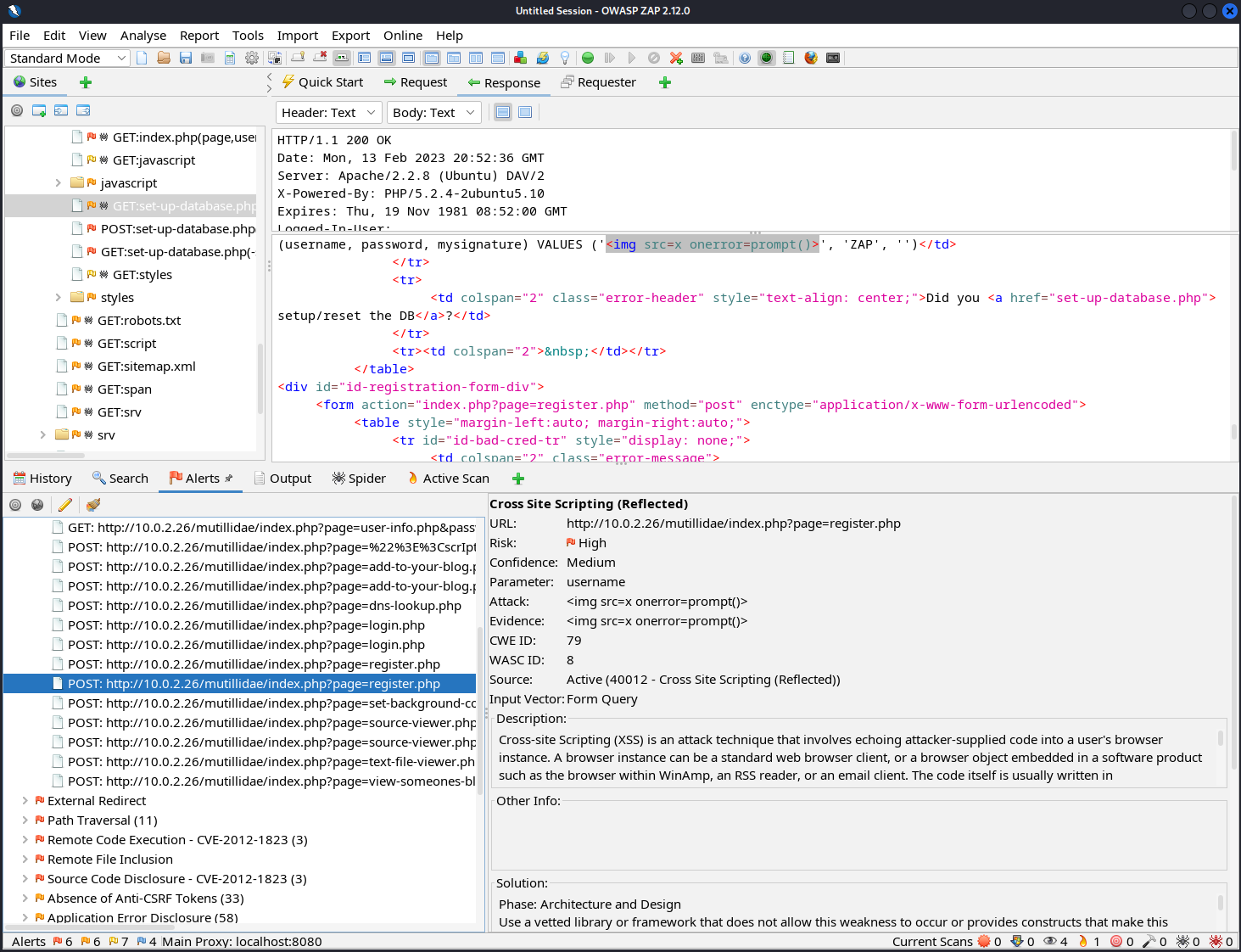
Using the scanner in OWASP ZAP to inspect a web application. (Screenshot courtesy of OWASP Foundation, Inc.)
Scanner functionality can be modified and extended by installing add-ons ( zaproxy.org/addons ).
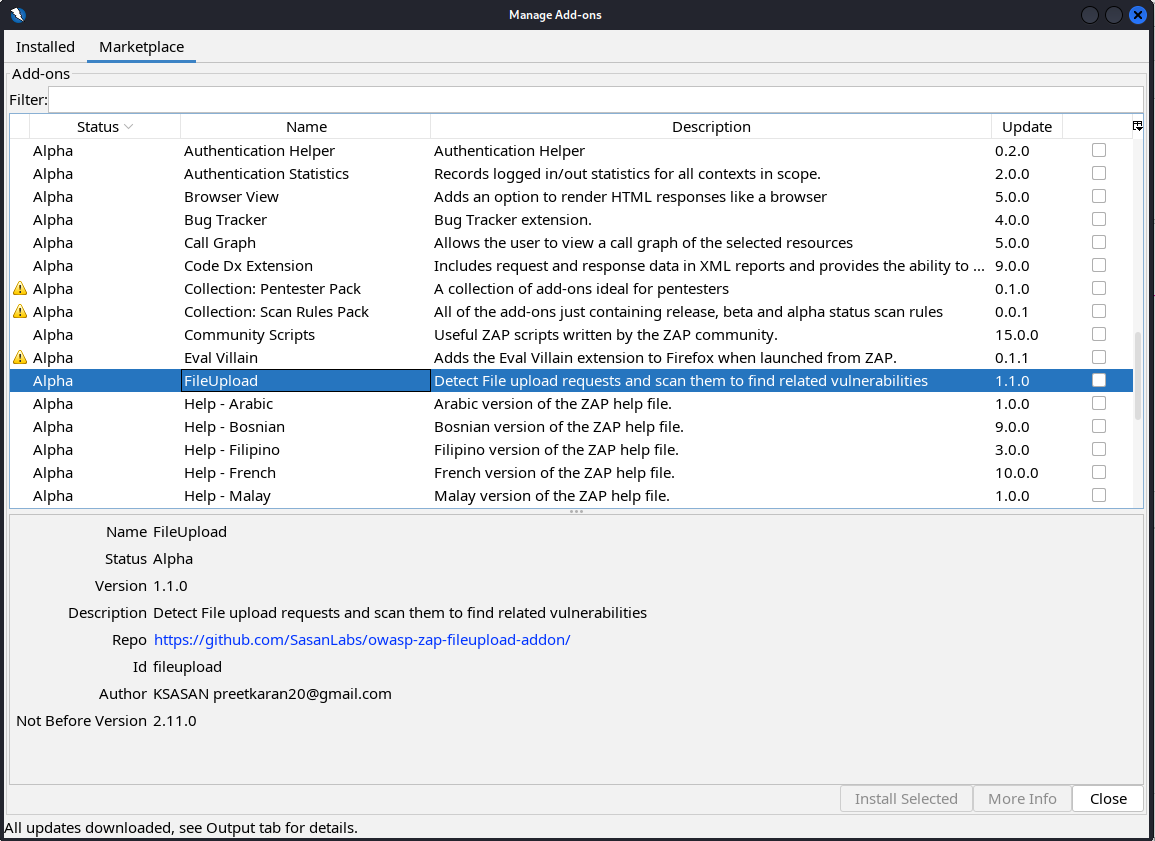
Detail
A tab at the top has two options, installed and marketplace. Marketplace is selected. A box is present below to enter the filter. Below that is a table with heads status, name, description, and update. A file is selected and the details of the file are listed in the bottom section.
Configuring ZAP add-ons to extend its functionality. (Screenshot courtesy of OWASP Foundation, Inc.)
Nikto
Nikto is another popular web application scanner that can be found at the project website https://www.cirt.net/nikto2 . Nikto can discover the type of HTTP server and web applications running on a host and expose vulnerabilities contained within them. Nikto:
- Tests more than 1250 outdated versions of web servers.
- Scans for more than 6,000 files and programs that can be exploited.
- Checks for version-specific problems on more than 270 servers.
Nikto has a large footprint because of the high volume of entries in the web server's log files. You can check auditing logs to determine if a hacker is using this tool against your web server.
Nikto is designed to use the command line, and can easily perform scans using the command nikto -h.
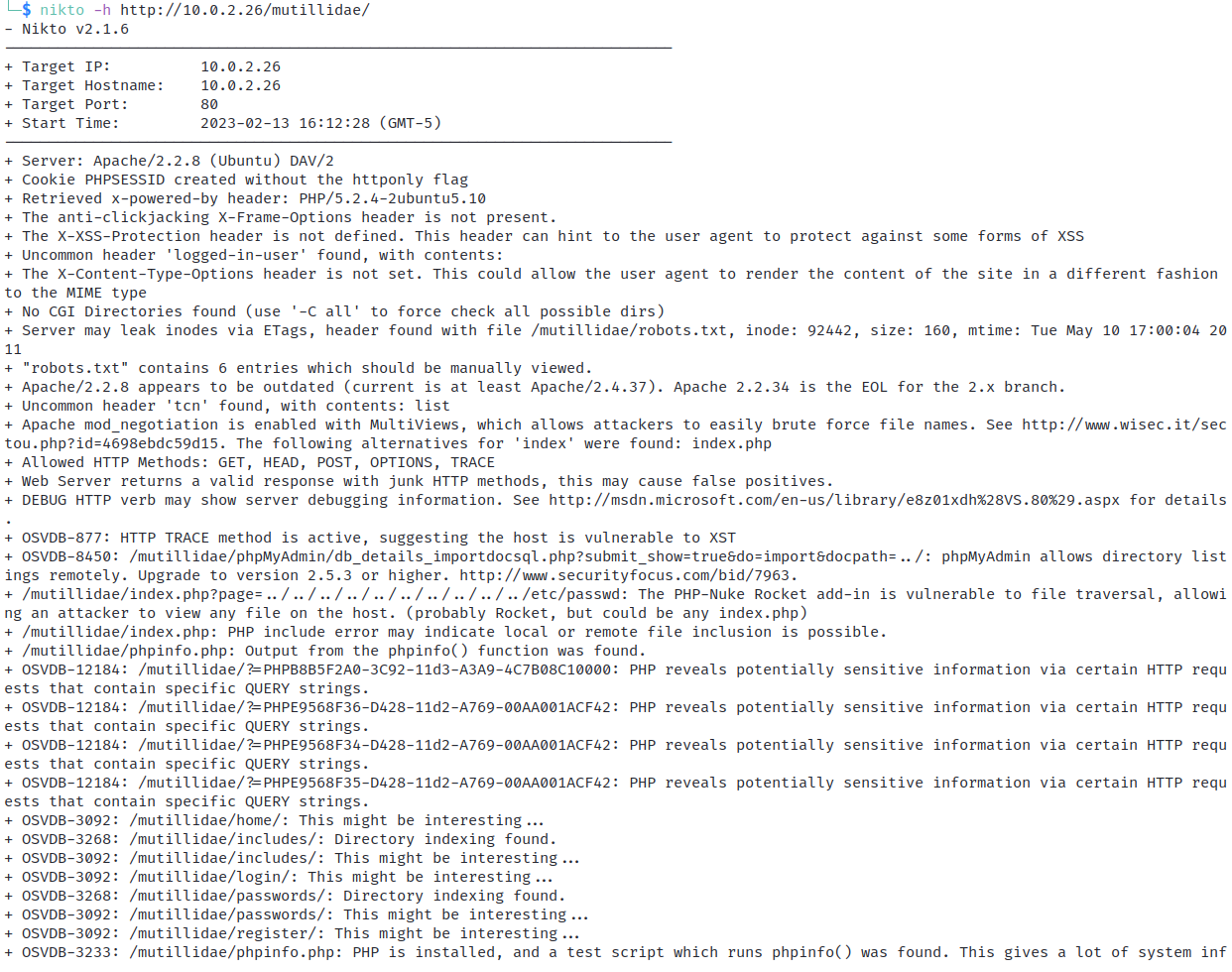
Output from a Nikto scan showing outdated software and configuration errors (permitted directory indexing and default files). (Screenshot Nikto running on Parrot Linux parrotlinux.org .)
Arachni
Arachni is another open-source web scanner application ( arachni-scanner.com ) available with both command line and web-based graphical interfaces. Arachni categorizes the severity of potential issues as high, medium, low, or informational. Arachni also:
- By default, audits:
- HTML & JavaScript forms
- JSON & XML input
- Links
- Orphan input elements
- Actively tests many different vulnerabilities, including:
- Code/SQL injection
- XSS
- CSRF
- Local and remote file inclusion
- Session fixation
- Directory traversal
- Backdoors
- Insecure policies
- Server information leakage
- Personal data exposure
- Provides a detailed description of each vulnerability, including:
- Specific information about how the scanner managed to exploit a vulnerability.
- Location in the web app where the vulnerability was exploited.
- What input was used to exploit it, including the specific HTTP request that triggered the issue and the server's response.
- What document object model (DOM) element was exploited.
- Sometimes will link to the Common Weakness Enumeration (CWE) entry for a more detailed description.
- Customizes each request to the technologies being used.
- Injects only pertinent payloads when performing its checks.
- Uses less bandwidth than other web application scanners.
- Causes less stress on the web application, resulting in faster and more accurate scans.
Arachni provides technical details as well as tabs for case management and issue timelines.
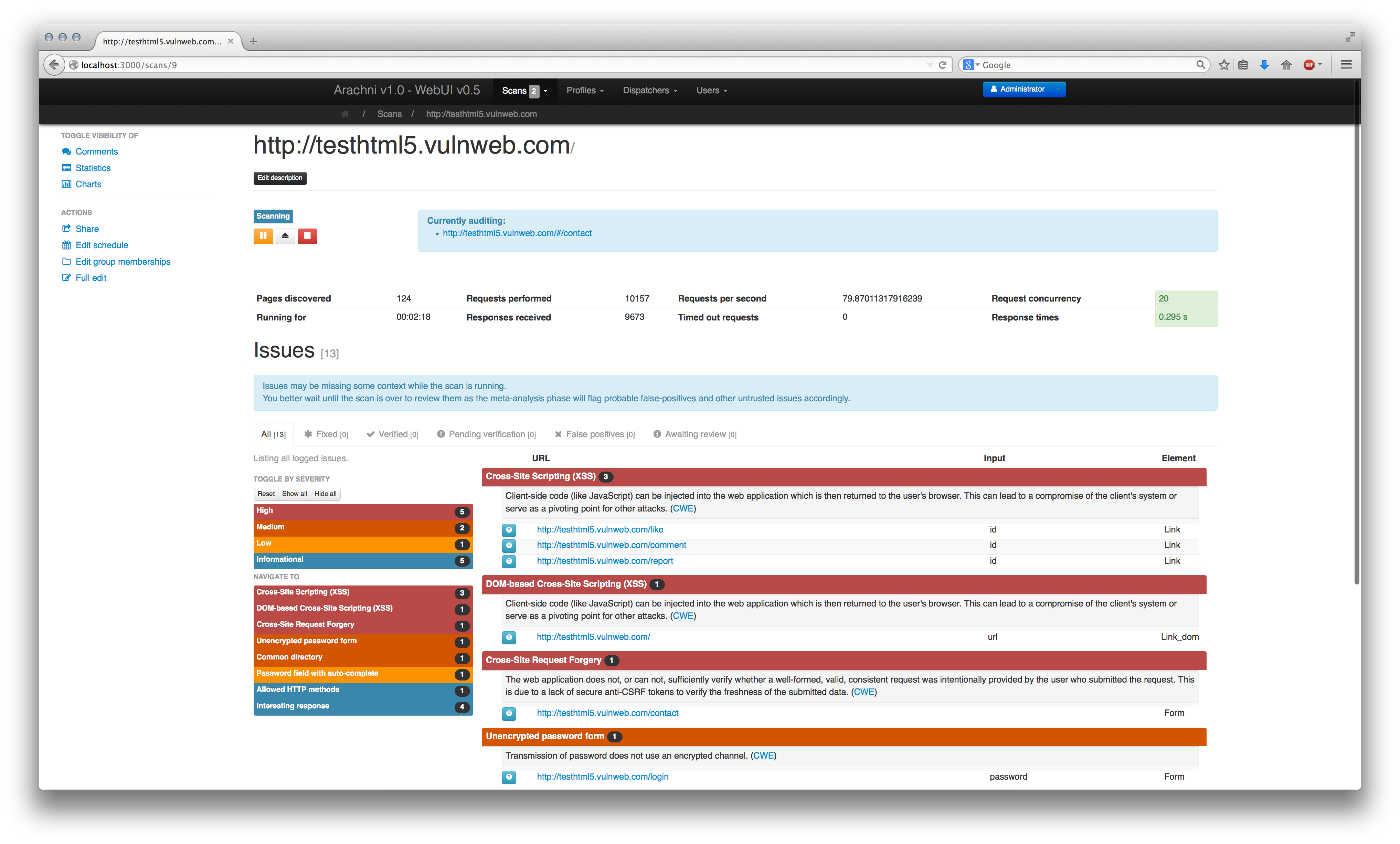
The Arachni web interface displaying the results of a vulnerability scan. (Screenshot courtesy of Arachni.)
Infrastructure Vulnerability Scanners
Security analysts use vulnerability scanners to determine if networks, systems, and applications have security weaknesses that make them vulnerable to attack. Vulnerability scanning is often mandated by industry standards and government regulations to improve the organization's security posture.
The following table describes three vulnerability scanners.
| Tool | Description |
|---|---|
| Nessus Professional | Nessus Professional is an assessment solution that resides on your network. This makes it more suitable for smaller organizations. Nessus Professional:
|
| OpenVAS | OpenVAS is a vulnerability scanner that has more than 50,000 vulnerability tests with daily updates. OpenVAS:
|
| Qualys Vulnerability Management | Qualys Vulnerability Management is a cloud-based service that keeps an organization's data in a private virtual database. Qualys:
|
5.4.8 Configure a Nessus Scan
Click one of the buttons to take you to that part of the video.
Scan a Network with Nessus 00:00-00:26 In this demonstration, we're going to work with the Nessus Vulnerability Scanner. Nessus is a very powerful security tool that you can use to scan for security vulnerabilities on your network.
Nessus is accessed via a web page on port 8834. I've installed Nessus on this machine, so I'm just connecting to localhost. For this demo, I'm running an evaluation copy of Nessus, but that's sufficient to show what it can do.
Create a Scan 00:26-01:28 Let's start by logging in. After I log in, we see the home page. Here, we can see the various scans that have already been created. There are many different features and options in Nessus, but for this demo, I'll stick to showing how to create and run a network scan.
While I could create a custom scan profile, Nessus includes quite a few useful templates that can accomplish most of what I typically need. To create a scan, I'll start by selecting New Scan from the top right. Here, we can see some of the templates I mentioned. I'm going to run a basic network scan, so I'll select that template. This template scans a specified host or network range for known vulnerabilities.
To set up the scan, I'll need to provide a name for it, as well as a network address that I'd like to scan. I'm going to name this 'Home Gateway Scan' since I'll be scanning the computers at my house with it. My gateway is located at 10.0.0.1, so that's what I'll supply as the target. There are many other options that I could configure, including port discovery and authenticated scanning, but I just want to do a simple scan today. Since everything I need is configured, I'll click Save.
Scan 01:28-02:02 Now that I've returned to the home page, I can see that the new scan has been created, but isn't running yet. I can click Launch to start it.
The scan's title changes to bold, and a spinning green icon appears to show that the scan is active. I can watch the scan live by clicking on it. This screen shows information about the different hosts that are discovered and the vulnerabilities that are found. Nessus also keeps a historical log of all the times a scan has been run so that I can compare how vulnerabilities have improved on my network over time.
This scan is going to take a while, so I'll pause the demo until it's finished.
Scan Results 02:02-03:01 Now that the scan has finished, we can see that my gateway has quite a few vulnerabilities. Luckily, most of them are labelled as informational. This means that the tool found information that could be useful for a security administrator to know about a host, but that the information doesn't immediately indicate a problem. An example of the type of data that would be labelled as informational is a list of open network ports. Network ports have to be open on some machines for them to function properly, but opening unexpected ports can cause problems.
More serious vulnerabilities are color-coded from green to red. Low-severity vulnerabilities aren't as interesting as high or critical vulnerabilities, so I'll take a look at one of the worst issues Nessus found.
When I select a vulnerability, it shows me information about the issue. In many cases, software creators patch high and critical vulnerabilities, and a relevant CVE entry is listed. Nessus provide a description and a suggested solution for many issues, as well as relevant information related to the vulnerability.
Summary 03:01-03:16 And that's it for this demo. We discussed how to conduct a vulnerability scan with Nessus. We looked at what Nessus is and what it does. And we ran a vulnerability scan on my home network and explored the results.
5.4.9 Analyze Scan Results from a Nessus Report
Click one of the buttons to take you to that part of the video.
Analyze Scan Results from a Nessus Report 00:00-00:28 Nessus is a vulnerability scanner published by a company called Tenable. Nessus scans help security analysts determine what may be vulnerable on their network. Today, we're going to go over some scan results, but we should first view the different types of scans. As you can see, we can just scan for live and open ports and then all the way down to specific vulnerabilities. In this demo, we're just going to cover a basic network scan with and without credentials
Scan Results 00:28-01:05 We have two scans that we've already run. Let's take a look at the home gateway scan. There are four hosts that were scanned for vulnerabilities. We don't have any that are critical; that's a good thing.
Next, were going to click on Vulnerabilities. This shows a list of all the items the scan picked up. Since this is the only one marked as High, let's click on it and check it out. Nessus usually give a description like this to tell us why this was picked up in the scan. On this host, Apache is currently at version 2.4.43, which has several vulnerabilities. In order to correct this, the fixed version of 2.4.46 has to be installed.
Credential Scan 01:05-02:08 Our second scan is our credential scan. This one differs from the first one in that it has login credentials specified to connect to the hosts. It's good to run both types of scans so you can see what's detected with and without credentials. We can see this picked up a lot more information vs. the other scan. Let's check out this host at 192.168.0.75 since it has the most vulnerabilities. In this list, let's click the first severity level labeled Mixed that has a count of 327. We have several critical ones in here. But we're only going to check out this first one. Openssl is used on Linux nodes for SSL and TLS protocols. The attack listed is called a DROWN attack. In a nutshell, it makes it easier for remote hackers to decrypt TLS data. Let's go back a few pages. The real reason why there are so many vulnerabilities for this host is most likely due to the version of Redhat Enterprise Linux, or RHEL, running, which is version 7.2. At the time of this demo, version 7.9 is the latest version of RHEL 7 released.
Report 02:08-02:42 Exporting a report may be needed when presenting your results to your supervisor or when you want a way to preserve results in a file. Nessus gives us many ways to export this report. Today though, we're going to use PDF. We're just going to leave the default Executive Summary and click Generate Report. Let's take a look at the generated PDF.
This report only covers the credential gateway scan, which is the last scan we were looking at. It breaks out each scanned host and which vulnerabilities they have. You can see why this may be good for reference instead of logging into the console to obtain the information.
Summary 02:42-02:59 That's it for this demo. In this demo, we had an overview of the scan results of Nessus. We showed you the difference between a non-credential vs. credential scan. We wrapped up by viewing a PDF report of the network scan.
5.4.10 Inspect HTTP Requests with Tamper Data
Click one of the buttons to take you to that part of the video.
Intro 00:00-00:33 Using the Tamper Data extension for Firefox can be useful when testing the security of a website. This extension allows a tester to see each set of POST or GET data, even allowing for their modification. This is useful in verifying that changes made to the data that don't correspond with the expected values will be noticed and handled properly.
This is a very simple demonstration of a relatively simple tool. But there are many use cases and reasons to be familiar with Tamper Data.
Enable the Tamper Data Extension 00:33-01:13 On my Kali Linux box, I'm going to log into a website and watch as data is pushed from the browser to the server. I'm using a local website. After entering the address, I'm presented with the login screen. I haven't yet activated the Tamper Data extension, so no changes to the regular website interaction have happened. I'll complete the login, and then log out and start the extension. I'll activate Tamper Data now using the cloud icon in the upper-right corner. When I click that icon, I'm presented with a list of things that Tamper Data can listen for. I'm going to leave the default values checked and make no changes. I click Yes at the bottom to proceed.
View POST Data 01:13-01:56 Back at the login page, I log in. A pop-up is displayed with the URL, Method, and Type. In the body of the POST is the data that'll be presented to the server. Notice that the password is in cleartext and not the dots that represent it on the actual page. I'll click OK to proceed. Another pop-up is presented with additional data being provided to the server. I'll click OK again. And twice more. I'm then presented with the website I was trying to log into. Although this is a simple example, it does give you an idea of how much data is pushed to a web server and also gives you fields that you might need to test for? vulnerability to overflow, etc.
Modify Website Traffic Data 01:56-02:51 Let's click one more link and see what's presented. I'll click the SQL Injection link. Doing so displays more pop-ups. I'll click OK to all of them. At this point, I can put in a value to send to the server. I'll enter a ‘1' here and click Submit. After clicking OK on the pop-ups, data is returned showing the ID of 1 with the First name and Surname fields showing admin. I'll put a ‘2' in the input field and click Submit. This time I'll alter the URL to use the number ‘3' for the id. I'll click OK twice more and be presented with user ID of 3 instead of the 2 that was entered. Tamper Data has allowed us to change the results on the fly.
Summary 02:51-03:12 That's it for this demonstration. In this demo, I've shown you how Tamper Data can read website traffic between a browser and a server and how to change data during that web conversation. There are many possible uses for this extension and practice will bring proficiency.
5.4.11 Navigate the DVWA Website
Click one of the buttons to take you to that part of the video.
DVWA 00:00-00:25 DVWA is a tool that lets security professionals test their skills against some of the most common web vulnerabilities. Most organizations won't let you exploit their systems in order to gain knowledge, but DVWA is a safe place to learn and gain a competitive advantage. As you can see, I've installed this tool on Kali Linux since a LAMP stack is pre-installed.
Vulnerabilities 00:25-04:06 Now let's talk about some vulnerabilities DVWA offers. Brute force is a known method for obtaining username and passwords by logging in over and over until a match is obtained. This process can be very tedious, but there are tools that make it more efficient. For example, Hydra can perform this kind of attack using a password dictionary.
Command injection is another one. It's the ability to run a command through a website's application. Developers didn't design things to work this way, and data that's not sanitized properly can be really bad. Let's go head and ping our localhost ‘127.0.0.1'. We get a reply back. Let's try this again and add a Linux command to the end of the ping request, ‘127.0.0.1;whoami' . whoami should show the username active while running this application, which happens to be www-data. A second command attached to the ping ‘127.0.0.1; ls -l' shows us we can list the current directory. You can see how this can be a huge risk since it's like running any command in an SSH session.
CSRF Cross-Site Request Forgery is a process that forces users to execute an action on an authentication portal, such as a web login. This could involve the attacker setting up a fake website along with some social engineering links sent by email.
File inclusion can be accomplished by two different means, Remote File Inclusion or Local File inclusion. Both vulnerabilities allow a user to enter information into files or upload files to the web server. There are examples here, on DVWA, showing existing file uploads, such as this File 1.
File Upload is what it sounds like: it's uploading a file to a web server. However, the file in this case has malicious code. Even though certain file types may be restricted, attackers can often work around that.
Insecure CAPTCHA is a way to bypass CAPTCHA, a function that's normally used to separate robots from humans. If it's not secured properly, it could provide unauthorized access.
SQL Injection is an injection attack against the database for the website. For example, a simple WordPress website will use a MYSQL database to store information that's accessed on the published website. Attacks against the database could result in adding, deleting, or modifying data in the database. There are two types of SQL injection listed. The first one will display query results back to the attacker, while a blind injection will not display any information from a query.
Weak session ID shows you how an attack can be executed from a cookie. Every time the Generate button is selected, it creates a new value in the cookie. If enough of these cookies were captured, maybe from an on-path attack, an attacker could easily guess the next session ID.
XSS, or cross-site scripting, is a type of attack where malicious JavaScript is injected into a website. As you can see, there are three different types of XSS attacks in DVWA. The most dangerous of them all is the XSS stored attack. This one, specifically, can store data from an attacker, which modifies the website. An example would be a pop-up saying "you are hacked" every time you visit the infected website.
CSP Content Security Policy is a set of rules the browser sends to the web server. It is possible to bypass these rules and manipulate a website. Scripts could be run remotely with a specified web address.
JavaScript attacks are directly focused on manipulation of JavaScript by injecting HTML or JavaScript code into a website. This code can be executed in the web view of a browser by an attacker depending on the vulnerability that's trying to be exploited.
Security Level 04:06-04:18 Out of the box, DVWA is set to Impossible. Right now, I have it set to Low. It's recommended that you start on Low and work your way up as you obtain the skills needed to exploit the vulnerability.
Summary 04:18-04:32 That's it for this demo. In this demo, we reviewed the vulnerabilities inherit in DVWA. We also saw how these vulnerabilities could pose a danger to websites.
5.4.14 Test a Web Application with Burp Suite
Click one of the buttons to take you to that part of the video.
Use Burp Suite 00:00-00:32 Penetration testers and ethical hackers use many tools. It would be impossible to cover every tool and every feature in this course. But the tasks you perform are more important than the tools you use. If you're scanning a site, testing credentials, or spidering a web application, it doesn't matter which tool you choose as long as it meets your needs. In this demo, I want to introduce you to Burp Suite. As its name indicates, it isn't a single tool, but a suite of tools for testing the security of web applications.
Open Burp Suite and Set Proxy 00:32-01:55 We're using Kali Linux, a Linux distribution designed for penetration testing. To open Burp Suite, I can come down to Show Applications and search for it. You might also have it listed in your favorites. If you're in the terminal, you can just type 'Burp Suite', and it'll launch. We're using the free Community edition. It does the basic things we're interested in. Professional penetration testers might find that the paid version is better for their needs.
To start, I'll just leave this set to a Temporary project and click Next. I'll leave it set to Use Burp defaults, come down here, and select Start Burp.
Burp Suite sits between your browser and the web application by acting as a proxy. We'll use the built-in browser that's already configured to use Burp Suite as the proxy. If you're using another browser, say, Firefox or Chrome, you'll need to configure it to use Burp Suite as the proxy, which is set up to listen by default on 127.0.0.1 on port 8080.
If we select the Burp Suite Proxy tab, it puts us on the Intercept sub-tab by default. Before we can collect traffic in Burp Suite, we need to make some small changes to the proxy's settings. On the Proxy tab, select the Options sub-tab. Under the section labeled Intercept Client Requests, click on the unchecked boxes in the enabled field so all boxes are checked. Back on the Intercept sub-tab, verify that the button near the top says that Intercept is on.
Explore Burp Suite's Interface 01:55-06:24 Now let's verify. Open a browser--I'll just use the built-in one--and generate some traffic. I've entered the address where the web application is running, and I'll enter in my credentials. Click Log in. Okay. Now let's go look at Burp Suite to see what's going on.
Under Proxy, click the HTTP History tab. Notice all of the get and post traffic that Burp Suite has captured. Our Burp Suite proxy is working as expected.
We can find our login to the web application listed. If I click on the line where login.php was used with a POST method, I can see more information. At the bottom, I can see the username and password fields, which have been transferred to the web application in clear text.
Burp Suite can be used to fuzz test an SQL database. Fuzz testing is an automated software testing technique where lists of random characters or character strings are used as input to an application. On the website I've logged into, which was designed to help teach penetration testing, I can submit a string to the database looking for a response from the SQL back end. If I put in a single character and click Submit, it returns the ID, First Name, and Surname fields as stored in the SQL database. In Burp Suite, I can view the traffic that was generated and then use fuzzing to probe the database. If I right-click the GET request, I can send to the Burp Suite Intruder tab. On the Intruder tab, down on the Positions sub-tab there are several items highlighted as potential attack vectors for an intrusion. I want to clear them and then focus an attack on the field labeled ID. I highlight the value of the ID field and click the Add button, then click on the Payloads tab above. Under the Payload Options section, click the Load button. A text file with a list of character combinations and sequences is selected. The attack begins with the Start Attack button.
Since I'm using the community version of Burp Suite, we get a notification that this version has some limitations. I click OK, and the attack begins. Each character set, as shown in the Payloads field, is inserted where our ID field value of 1 was to see how the application will react. I'm looking for field lengths longer than normal, which is about 4,498 bytes. I'll wait for the full list of items to run and then sort the results by length. Highlighting the longest length item, I click on the Response sub-tab below, then click Render, which displays the html as a browser would display it. Note that although only a single ID is meant to be entered through the browser and only one ID with associated names is intended to be displayed, the fuzzing attack payload highlighted has induced the database to respond with all IDs and names. This is a vulnerability in the SQL database and web app.
There are a lot of things you can do to configure an attack using Burp Suite. It's advised that you practice this attack on non-production servers and web applications until you know how to use this feature very well.
The Burp Suite Repeater tab allows you to manually manipulate and reissue individual HTTP requests and then analyze the application's responses. The Sequencer tab contains a tool for analyzing the quality of randomness and unpredictability in an application's session tokens or other data that's deemed important. The Decoder tab has a tool for performing manual or intelligent decoding and encoding of application data. The Comparer tab is a utility for performing a visual difference between any two items of data, such as two similar HTTP messages. The Extender allows you to load Burp extensions to extend the functionality of Burp using your own code or third-party code. You have two options here: Project options and User options. The Target tab contains detailed information about your target applications and lets you drive the process of testing for vulnerabilities. As you can see, my sites are in a tree view. I can expand these out and go deeper into the site hierarchy.
Let's revisit the Proxy tab. Under HTTP history, we have our http headers. Each http request made by our browser is listed here. As we browse our web application, our proxy will keep a record of all the requests and all the responses. If you select one, you can see the results down here, in this lower pane.
Summary 06:24-07:06 All right, that's all for this demo. Burp Suite is a hands-on tool that gives the user control of the actions they want to perform. The program is user-driven; users have the ability to pass the http requests on to the different Burp tools to carry out particular tasks. This was a very high-level overview of the program and a few of the tasks it can perform. It would take an entire course to explain how to use the program and all the features it offers. Like all the tools covered in this course, the best way to become proficient with Burp Suite is to set up a test environment and practice on non-production servers and web applications.
