Chapter 1: Introduction to Automotive Cybersecurity
OBJECTIVES
- Overview
- Introduction
- Security and Its Impact
- Cyber Security in Automotive Technology
- The Rising Threat
- Vehicular Ransomware Attack
HACKERS REMOTELY KILL A JEEP ON A HIGHWAY
https://www.youtube.com/watch?v=MK0SrxBC1xs&t=1s
AUTOMOTIVE HACKING: REMOTELY HACKING INTO A BRAND NEW CAR
https://www.youtube.com/watch?v=fPQIWawXSRI&t=3s
OVERVIEW
- The technological progress made in sensor and navigation systems, the Internet of Things, and different types of machine learning techniques would promote new, innovative, and accessible mobility that gives rise to intelligent and autonomous vehicles.
- However, security plays a vital role in intelligent and autonomous vehicles.
- We discuss in detail about the different levels of autonomous vehicles from Level 0 to Level 4, different types of cybersecurity issues in autonomous vehicles, and future trends and challenges in autonomous vehicles.
- Security must be thought as an important aspect during designing and implementation of the autonomous vehicles to prevent from numerous security threats and attacks.
INTRODUCTION
- The term security refers to the protection of critical assets of the system from malicious threats and mitigation of their impact on the system.
- The assets can be any valuable object or entity or an organization.
- These assets can have certain vulnerability, which can be exploited by malicious users or attackers for their own benefits.
- The malicious threats are generated by malicious users or intruders, which exploits the system’s vulnerability, and access or modify the critical assets of the system.
- These malicious users can be an individual person or group of people or software, whose aim is to find a vulnerability or weak points in the system and attack at that point to collapse, harm, or just to gain access to the system.
- The security assets are the resources of the system that need to be protected against malicious threats and attacks.
- The security assets with its environment refer to the security context.
- If the security environment responds friendly, then it adds for security assets and vice versa.
SECURITY AND ITS IMPACT
- The automotive industry is experiencing massive changes as well as gaining huge opportunities.
- The automotive industry is dealing with new technologies and autonomous vehicle concepts that have the potential to turn the vehicle itself into the autonomous computerized moving device.
- There can be various cyber security mechanisms to provide security, and each security mechanism can have single or multiple impacts on the assets to be protected.
- A security mechanism can level-up the security for various assets or for all assets in the system’s environment context.
- The security mechanism may be powerful for a limited period of time or impact in such a way that there is a trade-off among assets.
- The cybersecurity ensures safe access to hardware and protects damage to data during network access data injection and code injection.
CYBER SECURITY IN AUTOMOTIVE TECHNOLOGY
- Every year, there are huge developments of novel automotive applications and services that are leading the production in terms of cost and technology.
- More than 90% of automotive inventions lead to innovations in vehicle hardware and software.
- Hardware in the vehicles has control system, which directs the vehicles to perform various tasks on the roads while driving.
- Some basic tasks are listed below:
- Primary systems of the vehicles, e.g., the engine, driver assistance, driveline, electric system, brake system,dashboard, etc.
- Secondary vehicles systems, e.g., ignition, indicators, window control, wipers, lights
- Infotainment applications, e.g., navigation systems, telematics, rear seat entertainment, music and video entertainment, and GPS-based services.
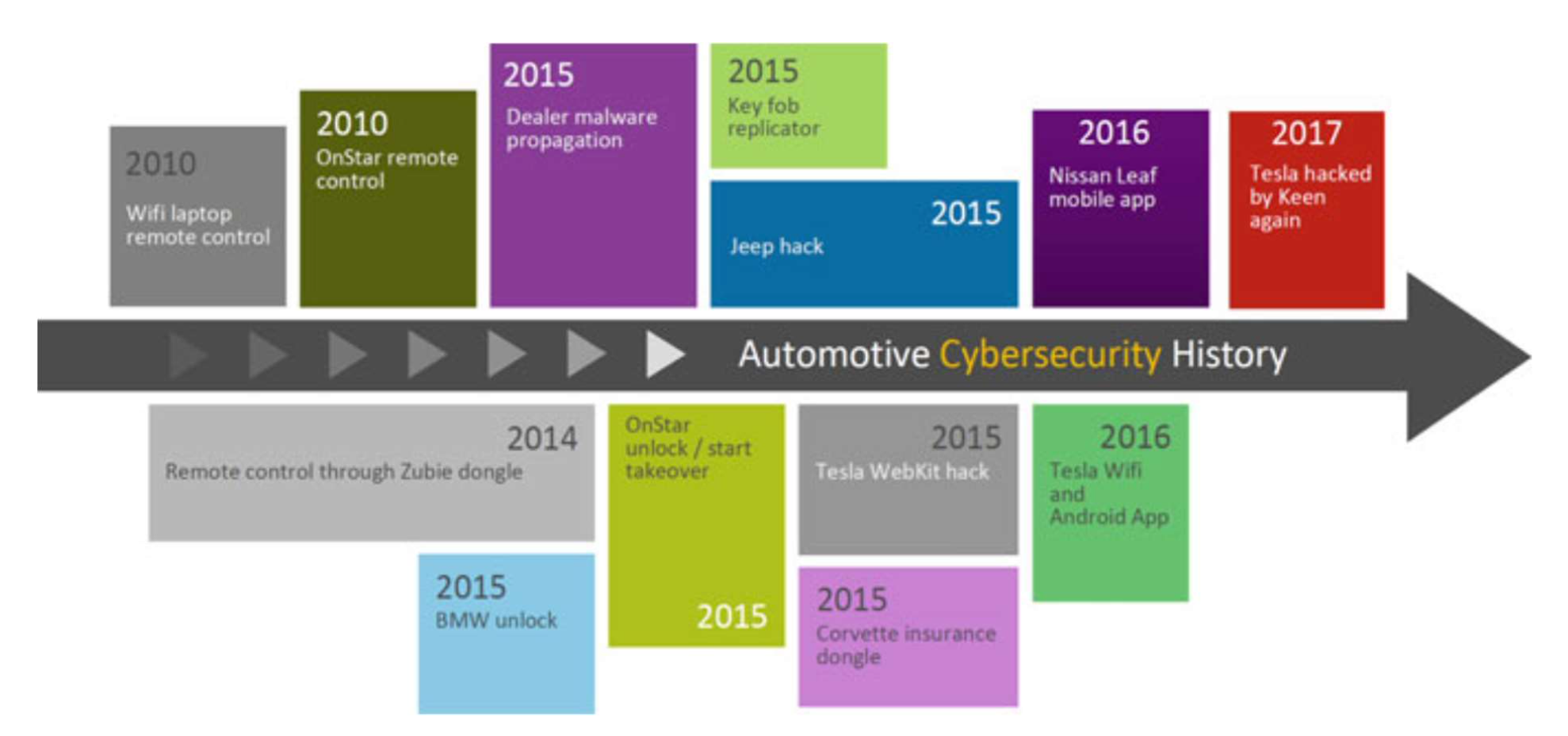
Fig. 1.1 Automotive cybersecurity history timeline
THE RISING THREAT
- As vehicles are getting more advanced, they use computers to control decisive operations such as brakes, stability control, and airbags functionality.
- Vehicles become safer on one hand, but on the other hand, the safety mechanisms are controlled by the ECUs (Electronic Control Units) , adding more complexity and potential attack vectors to the system.
- These ECUs are interconnected through a CAN (Controller Area Network) bus in an unsecured way.
- The notion of merely securing ECUs in individual systems is inadequate in the connected and autonomous vehicle situation.
- There are several forms of networking such as Ethernet, cellular, Internet, Wi-Fi, Bluetooth, and V2X connected in the vehicle and linking to various networks like CAN bus, Ethernet that are running applications on peripherals (USB, display, sensor, LiDAR, etc.).
- The vehicles may be remotely hacked or immobilized.
- Vehicles can be compromised through the wireless sensors in the vehicles, and person can be hurt physically if someone gets hold of the CAN bus and stops the vehicle suddenly through one of the external interfaces of the vehicle.
- Even luxury vehicles such as the Jaguar suffered from flaws, causing “blue screen of death” immobilizing them.
- The weakness in several vehicle assessments is seen as extremely vulnerable
- security architecture with a significant number of powerful computers with wireless
- access such as GPS, NFC, Bluetooth, cellular, IR, Wi-Fi, etc.
- The weakness in several vehicle assessments is seen as extremely vulnerable security architecture with a significant number of powerful computers with wireless access such as GPS, NFC, Bluetooth, cellular, IR, Wi-Fi, etc.
VEHICULAR RANSOMWARE ATTACK
- Ransomware for vehicles can be developed and injected, indicating that this ransomware attack on vehicles is real and serious.
- As the cars are more interconnected and as digital technology begins to provide even more essential vehicle technologies and as vehicle digital technology becomes more standardized, the attack surfaces for ransomware will grow, and the value that ransomware may take hostage will increase.
- The community that can attack a single type of ransomware will increase.
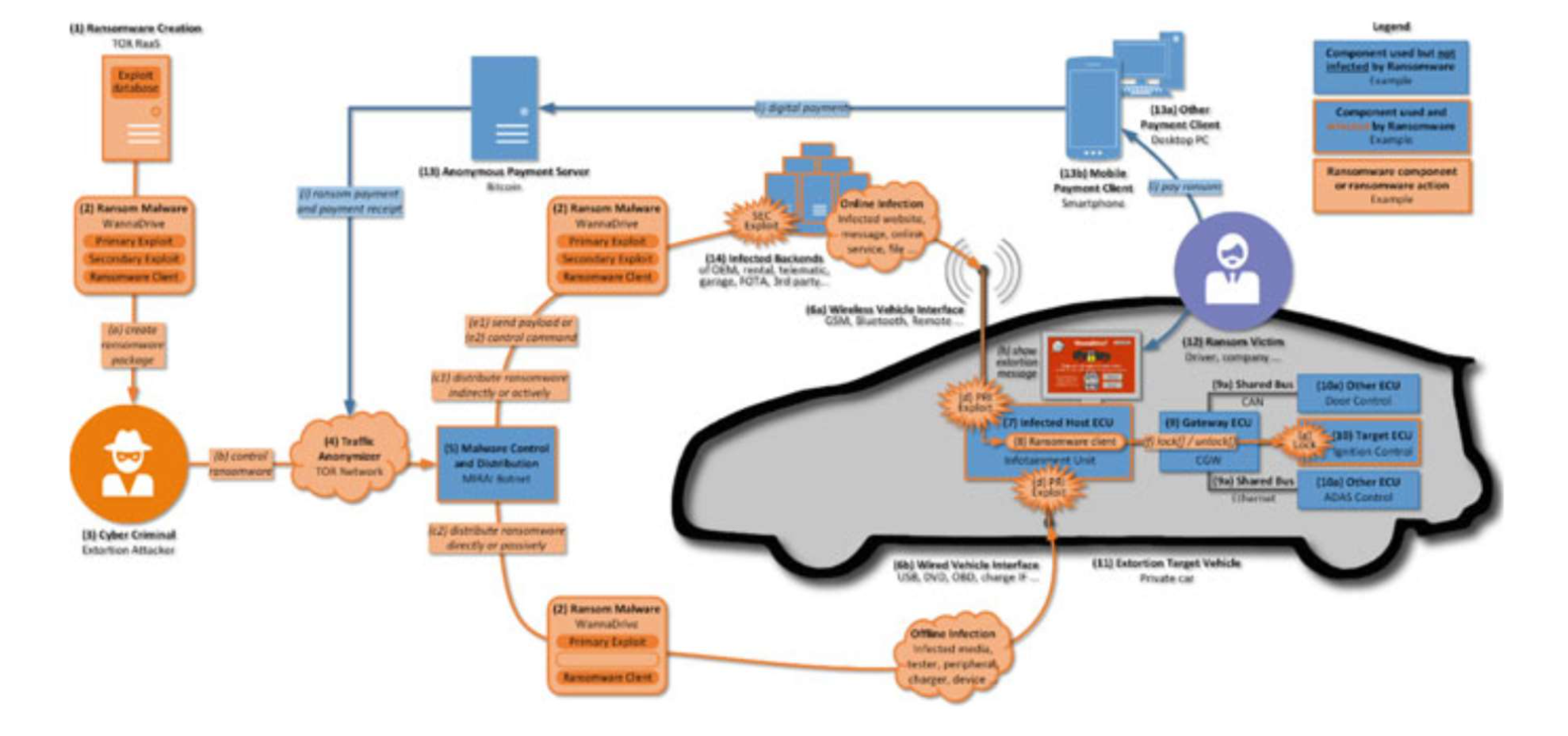
Fig. 1.2 Ransomware attack scheme in vehicles
