Chapter 5 – IT Service Management and Continuity
Objectives
- IT Service Management
- Business Continuity and Disaster Recovery
- SLA Management
- IT operations and exception handling
- Security Monitoring
- Data Management
- Types of Computers
- Network models
- Network Technologies and Toplologies
- IP addressing
- VPNs
IT Organizations and Operations Control
- IT Service Management (ITSM): IT Service Management (ITSM) is central to maintaining an organization's IT functionality.
- ITSM ensures IT services are managed efficiently, aligning with business objectives and supporting continuous operations, especially in scenarios that test resilience, such as disasters.
- IT departments function as service organizations within an enterprise, dedicated to supporting and enhancing business processes.
- Their main goal is to deliver reliable, consistent, and effective IT services that align with and support organizational objectives.
- Effective IT operations require stringent control mechanisms to maintain service reliability and quality.
- Digital Transformation and ITSM: The rapid advancement of digital transformation has heightened the need for robust ITSM practices.
Information Systems (IS) Operations
- Definition of IS Operations: Information Systems (IS) operations refer to the daily activities involved in managing information systems, applications, and infrastructure essential to achieving business objectives. The role of IS operations is to ensure that systems and services remain operational, supporting the overall functionality of the organization without interruption.
- Components of IS Operations: IS operations encompass various components that enable a well-rounded approach to IT service delivery. Key components include:
- IT Service Management: Ensures IT services are consistently delivered, meeting established standards.
- IT Operations and Exception Handling: Addresses routine operations and manages unexpected events that could impact service levels.
- End-User Computing: Manages the computing environment and support services available to end-users.
- Quality Assurance & Security: Enforces standards that uphold service quality and protect information integrity
Management and Control of Operations in IT
- The Importance of Management Oversight: In IT operations, management oversight is critical for ensuring that all activities are adequately controlled, documented, and consistent with organizational policies. Each action taken by operations personnel must align with established controls and procedures, providing a structured framework for daily operations and incident handling.
- Responsibilities:
- Process and Procedure Documentation: All operational activities that are repetitive should be documented as a process or procedure. This documentation allows for consistency, control, and transparency in operations, enabling any team member to follow standardized steps to perform a task.
- Development of Standards: Standards dictate the technology brands, practices, and methodologies used in operations, fostering consistency and quality across the organization.
- Resource Allocation: Management is responsible for aligning resources—including manpower, technology, and budget—to meet the demands of IS operations effectively.
- Process Measurement and Control: Regular measurement and management of IS processes ensure they are efficient and align with organizational goals, allowing management to track progress and make improvements.
IT Service Management (ITSM) Fundamentals
- Role of IT Service Management (ITSM): IT Service Management (ITSM) involves a structured approach to designing, delivering, managing, and improving IT services. It enables organizations to ensure that their IT services are aligned with business needs, facilitating reliable and cost-effective IT support.
- Activities in ITSM:
- Service Desk & Incident Management: Provides a centralized contact point for IT issues, handling incidents and ensuring timely resolution of disruptions.
- Problem and Change Management: Manages root causes of recurring issues and coordinates controlled changes to minimize service disruption.
- Configuration Management: Maintains an accurate record of IT configurations to support service delivery and help diagnose issues quickly.
- Release Management: Oversees the controlled rollout of new software and updates, ensuring that changes are properly tested before they reach production environments.
ITIL and ISO/IEC 20000: ITSM practices are structured within the IT Infrastructure Library (ITIL) framework, recognized globally as a standard, and can be audited against the ISO/IEC 20000 standard to ensure compliance with international ITSM best practices.
Service Desk Operations in ITSM
- Service Desk as a Single Point of Contact: The service desk, often known as the helpdesk, is the primary point of contact for IT users experiencing issues or requiring support. It serves as a centralized hub, managing incidents and service requests and ensuring efficient communication between IT and its internal customers.
- Responsibilities of the Service Desk:
- Incident Management: The service desk is responsible for managing incidents that affect IT services, coordinating resources to resolve issues as quickly as possible.
- Service Request Fulfillment: In addition to handling incidents, the service desk processes requests for routine services, such as password resets or software installations.
- Status Communication: The service desk also keeps users informed about the status of incidents and requests, managing expectations and ensuring transparency.
- Integration with Other ITSM Functions: The service desk works closely with other ITSM functions such as change management, configuration management, and availability management, ensuring all IT processes are interconnected and responsive to user needs.
Incident Management in ITSM
- Definition and Importance of Incident Management:
Incident management is the process of restoring IT services as quickly as possible following a disruption, with minimal impact on business operations.
According to ITIL, an incident is any unplanned interruption to an IT service or a reduction in service quality, making quick resolution essential. - Types of Incidents:
- Service Outage: A complete cessation of an IT service, preventing users from accessing required resources.
- Service Degradation: A decline in the quality or speed of an IT service, which may slow down productivity.
- Software Issues: Errors or bugs within applications that can disrupt workflows and user experiences.
- Efficient Resolution Strategies:
- Known Error Database: By maintaining a catalog of previously identified issues, the service desk can expedite problem resolution, reducing downtime for users.
- Escalation Protocols: If an incident cannot be resolved promptly, it may be escalated to a higher level of support to ensure a more thorough investigation and resolution.
- Benefits of Effective Incident Management:
An efficient incident management process helps reduce downtime, maintain productivity, and improve user satisfaction by minimizing service disruptions.
Problem Management in ITSM
- Role of Problem Management:
Problem management is the process of identifying and addressing the underlying causes of incidents, aiming to reduce the recurrence of service disruptions. ITIL defines a problem as a root cause behind one or more incidents, making it a key focus area in long-term IT stability. - Objectives of Problem Management:
- Root Cause Analysis: By identifying the underlying causes of recurring incidents, IT can implement solutions that prevent future disruptions, contributing to a more stable IT environment.
- Proactive System Monitoring: Problem management includes proactive measures such as system monitoring and capacity management to identify potential issues before they escalate into serviceaffecting incidents.
- Examples of Problems:
- Resource Constraints: Servers with insufficient resources may repeatedly fail, leading to multiple incidents until the issue is resolved at the root level.
- Persistent Software Bugs: Recurring issues caused by software bugs can disrupt operations for multiple users.
- Coordination with Change Management: Effective problem resolution often requires changes to system configurations or software, which must be coordinated through the change management process to avoid unintended consequences.
Change Management in ITSM
- Definition: Change management is the structured approach to managing all changes within an IT environment to ensure consistent and controlled implementation.
- Objectives:
- Vetting Changes for Suitability and Risk: Change management assesses the suitability of proposed changes, identifying and mitigating potential risks to minimize service disruption.
- Stakeholder Involvement: Each proposed change is reviewed by relevant stakeholders, ensuring a well-rounded perspective and accountability in change decisions.
- Change Management Process:
- Proposal or Request: Change proposals include a full description, impact analysis, verification procedure, and back-out plan, allowing stakeholders to review and understand the change in detail.
- Review and Approval: Stakeholders discuss the proposed change, and if approved, the decision is documented for transparency. Deferred or denied changes require revisions.
- Implementation and Verification: Approved changes are implemented and verified for correctness, with evidence collected for future reference.
- Post-Change Review: A review assesses the effectiveness of changes, identifying lessons for improvement.
Emergency Changes in Change Management
- Definitoin: Emergency changes are unplanned but necessary adjustments made to IT systems to quickly restore or maintain critical services. While they follow a similar process to standard changes, emergency changes prioritize immediate approval and swift action.
- Process for Emergency Changes:
- Emergency Approval: Approval is granted urgently, often through verbal or written channels. Designated managers are pre-assigned to handle emergency change authorizations.
- Rapid Implementation and Verification: The change is implemented immediately, and verification follows to ensure the emergency action achieves the desired effect.
- Post-Implementation Review: Emergency changes undergo a formal review to assess effectiveness and document outcomes, often alongside non-emergency changes.
- Importance of Documentation: Proper documentation ensures that even emergency changes are recorded for future audits and analysis, supporting accountability and knowledge management within IT operations.
Configuration Management in ITSM
- Configuration management is the process of recording and maintaining information on IT systems’ configurations, often through a configuration management database (CMDB). Each configuration item (CI) includes details essential for system management and troubleshooting.
- Types of Configuration Items (CIs):
- Hardware Specifications: Details like CPU speed, memory, and adapters that describe each system’s physical components.
- Operating System and Software Configuration: Includes OS versions, patches, and application configurations that influence performance and functionality.
- Network Configurations: Network settings, including protocols and connection details, crucial for maintaining connectivity and security.
- Benefits of Configuration Management:
- Accurate configuration records help diagnose and resolve issues by revealing any conflicting configurations.
- Configuration management tools detect and validate changes, ensuring that any changes align with approved configurations in the CMDB.
Configuration Management in ITSM
- Configuration data enables rapid troubleshooting by helping identify whether incidents stem from specific configurations. This linkage allows for quicker resolution by cross-referencing incidents with known configuration issues.
- Configuration management tools can detect configuration changes and validate them against approved changes in the change management process. This integration helps track unauthorized changes and ensures alignment with the change management workflow.
- The CMDB is a centralized database that maintains configuration records, supporting seamless operations across ITSM. Automated tools can track and update configurations, ensuring consistency and compliance across all IT assets.
Release Management in ITSM
- Definition: Release management in ITSM refers to the controlled deployment of changes to applications, systems, or environments. It is the process through which updates, enhancements, and fixes are moved from development to production.
- Types of Releases:
- Incident and Problem Resolutions: Bug fixes that address issues reported by users or identified through problem management.
- Enhancements: New features and functionalities added to applications to improve user experience and performance.
- Subsystem Patches: Updates to underlying systems, such as operating systems or databases, often aimed at improving security or performance.
- Release Process Steps:
- Feasibility Study and Requirements Definition: Each release is evaluated for its potential impact and must have detailed requirements to guide development.
- Design and Development: Releases undergo design and coding phases where all changes are structured and created.
- Testing and Approval: Comprehensive testing, including regression testing, is performed to validate changes, followed by user acceptance testing (UAT) to ensure functionality.
- Deployment and Post-Implementation Review: Once changes are confirmed, they are deployed to production. A review follows to assess the success and identify any lessons learned.
Release Management in ITSM
- Preparation for Release Deployment: Once changes are approved, a release team prepares the system for implementation. This step includes aligning databases, network configurations, and user data as required for smooth deployment.
- Execution of Release Deployment: The release is systematically installed on target systems, following a structured procedure to apply changes accurately across all components.
- Verification of Deployment: After release deployment, a verification process ensures all system elements function as expected. Verification results are documented, confirming that the system operates correctly and meeting requirements.
- Post-Implementation Review: This review evaluates the release’s overall success, checking for performance issues and verifying the achievement of intended outcomes. This step is essential for continuous improvement in the release management process.
Gate Process in Release Management
- Definition: The gate process in release management is a structured method where each step of the release process undergoes a formal review and approval before proceeding to the next stage. This ensures that all aspects of the release meet quality standards at every stage.
- Review at Each Gate: The gate process typically includes a review by stakeholders at each critical point, including design, testing, and implementation stages. These reviews involve endusers, IT personnel, and management to confirm that each aspect aligns with requirements.
- Although agile methodologies often involve parallel processes, they also include gates for formal reviews and quality checks. Gates in agile environments ensure that even fast-paced development cycles maintain quality and consistency, supporting rapid but controlled releases.
Business Continuity and Disaster Recovery Planning
- Business continuity and disaster recovery (BCDR) planning are essential components of ITSM, as they prepare organizations to respond effectively to disruptions. BCDR plans ensure that critical IT functions can continue or be quickly restored after unexpected incidents.
- Components of BCDR:
- Risk Assessment: Identifies potential threats to IT operations, such as natural disasters or cyber-attacks.
- Business Impact Analysis (BIA): Assesses the effects of disruptions on business operations, helping prioritize recovery efforts.
- Components of BCDR:
Disaster recovery planning (DRP) focuses on restoring IT systems, while business continuity planning (BCP) aims to maintain essential functions. Together, they form a comprehensive strategy to ensure organizational resilience.
- IS auditors play a vital role in evaluating the effectiveness of ITSM processes, infrastructure, and business continuity plans. By auditing these areas, auditors ensure that IT services align with business needs, policies, and regulatory standards.
- Audit Objectives:
- Assess operational efficiency, control mechanisms, and compliance with established procedures.
- Review the adequacy of business continuity and disaster recovery plans, verifying their alignment with organizational risk profiles and industry standards.
- Auditing Standards and Frameworks: Audits are conducted using industry standards, including those from ISACA, NIST, and ISO. These frameworks provide auditors with guidelines for evaluating IT processes and controls, ensuring a thorough and standardized audit process.
Service-Level and Financial Management
- Service-Level Management: Service-level management (SLM) encompasses activities that assess whether IT operations are delivering adequate services to customers, based on agreed standards. This is achieved through constant monitoring and regular review of IT service delivery against defined service-level agreements (SLAs).
- IT departments often play dual roles in SLM, both as service providers for internal customers and as service coordinators with external providers.
- Financial Management: Financial management for IT services focuses on the financial planning and control aspects of IT, ensuring the cost-effectiveness of IT services aligned with organizational goals. Activities include managing budgets, overseeing expenses, and evaluating the return on investment (ROI) of IT projects.
- Budgeting allocates funds for IT operations and improvements, ensuring resource availability.
Service Continuity and Availability Management
- Definition: Service continuity management (SCM) encompasses activities focused on maintaining or quickly restoring IT services in the event of a disaster, ensuring business continuity.
- SCM works closely with BCP and DRP, forming a unified approach to protect IT infrastructure and ensure swift recovery. This integration ensures that critical services remain functional or are restored promptly after any adverse event.
- Availability Management: Availability management aims to maintain consistent IT service availability, aligning with organizational objectives and supporting uninterrupted business processes. Its primary focus is on ensuring systems are accessible to users as expected, with minimal unplanned downtime.
- Thorough testing and fault-tolerant architecture design enhance IT service resilience, allowing systems to withstand component failures. Resilient architectures are designed to maintain service availability even under adverse conditions.
- Availability is typically measured as a percentage of uptime or the number of unscheduled downtime minutes per month. These metrics allow IT to track performance and identify areas for improvement.
IT Operations and Exception Handling
- IT operations involve executing daily tasks according to established processes and procedures to ensure smooth functioning of IT services. This includes routine jobs, system monitoring, and maintenance, keeping IT systems operational and efficient.
- Job Scheduling and Monitoring: IT operations personnel run scheduled jobs, monitor them for errors, and allocate resources based on job priority. Failed jobs are restarted to maintain operational continuity.
- Backup and Maintenance Tasks: Backups are facilitated by loading or changing backup media, while maintenance tasks like equipment cleaning are performed to ensure system readiness. This ensures data availability and reliability across IT environments.
- Larger organizations utilize network operations centers (NOCs) and security operations centers (SOCs) to monitor networks, systems, and security incidents. These centers often operate around the clock, enhancing IT vigilance and responsiveness.
Monitoring in IT Operations
- Monitoring is essential for detecting any deviation from expected performance in IT systems, applications, and infrastructure. It allows IT staff to identify issues early, reducing the risk of larger disruptions.
- Types of Errors to Monitor: Monitoring tools detect system errors, program issues, communication errors, and operator mistakes. This proactive approach ensures a quick response to errors, preserving system integrity.
- Incident and Problem Management: Detected errors are addressed through incident and problem management processes, which ensure systematic identification and resolution. Documenting incidents provides valuable insights for future prevention and continuous improvement.
- Security monitoring protects IT assets from unauthorized access and detects potential security threats. It is a critical component in preventing and responding to security incidents, safeguarding organizational data.
- Types of Security Alerts:
- Firewall and IPS Alerts: Alerts generated by firewalls and intrusion prevention systems (IPS) help detect unauthorized access attempts.
- DLP and CASB Alerts: Data loss prevention (DLP) and cloud access security broker (CASB) systems monitor sensitive data and cloud environments for suspicious activities.
- Other Security Monitoring Tools: Organizations use endpoint management systems, network anomaly detection, and threat intelligence advisories to stay informed of potential vulnerabilities. These tools work in concert to create a layered security approach, enhancing overall IT security posture.
Media Control in IT Operations
- Media control involves the management, protection, and eventual disposal of digital media, ensuring that data is retained or destroyed as appropriate. This process is crucial for maintaining data security and complying with privacy laws.
- Data Retention and Purging: Media control policies include guidelines for retaining essential data and securely purging obsolete or redundant information. Retained data is protected with physical and logical security controls, while unneeded data is sanitized or destroyed.
- Types of Media: Digital media such as backup tapes, virtual libraries, optical media, hard drives, and solid-state drives fall under media control policies. The policies extend to storage within devices like printers, copiers, and mobile devices, as well as hard-copy documents.
- Media sanitization and destruction procedures are often stipulated in service contracts, ensuring that third-party providers comply with data security standards. Recordkeeping is maintained to track the secure destruction of media over time, supporting accountability
Data Management in IT Operations
- Definition: Data management includes all activities related to the acquisition, storage, processing, use, and disposal of data. Effective data management is essential for ensuring data integrity, security, and availability throughout its lifecycle.
- Planning is crucial to data management, encompassing the design of databases and information flows between systems. A well-structured data architecture facilitates efficient data access and enhances security.
- Data Life Cycle Stages:
- Planning: Define data structure, sensitivity, usage, and retention policies before data creation or acquisition.
- Design: Create database schemas and configure storage systems to securely store data.
- Build/Acquire: Data is either created or imported into the system, ready for operational use.
- Operations: Data is processed and shared according to organizational needs.
- Monitoring: Data quality and access are regularly checked to prevent misuse.
- Archival: Long-term storage of data for historical or legal purposes.
- Disposal: Securely erasing data when it is no longer needed.
DAMA International provides resources and standards for data management professionals, promoting best practices across the field.
Information Systems Hardware Overview
- Information systems hardware consists of physical components like circuit boards, processors, memory, and peripherals such as keyboards and network interfaces. Hardware serves as the foundation of IT systems, supporting software and applications essential for business functions.
- IS auditors must understand computer hardware concepts to assess the effectiveness of an organization’s infrastructure. This includes familiarity with hardware architecture, maintenance, and monitoring to ensure systems meet operational requirements.
- The transition to cloud infrastructure doesn’t eliminate the need for hardware knowledge. Virtual workloads still require configuration of hardware-like resources in the cloud, making hardware concepts relevant for both on-premises and cloud environments.
Types of Computers in IT Operations
- Classification by Size and Use: Computers can be categorized by capacity and intended use, including supercomputers, mainframes, midrange computers, and servers. Each type serves different purposes, from large-scale computations to specialized applications in various business sectors.
- Types:
- Supercomputer: Used for intensive scientific computations, such as weather forecasting.
- Mainframe: Large-scale systems supporting financial transactions and database processing.
- Midrange and Server: Serve applications that require moderate capacity, commonly used in corporate settings.
- Desktop and Mobile: Individual devices supporting end-user tasks, such as productivity applications and communication.
- Appliances and Embedded Devices: Specialized systems with specific functions, like medical devices or industrial control.
Virtual servers provide flexibility, allowing IT departments to configure and deploy resources remotely. Cloudbased solutions enable scalable resource allocation without physical hardware, adapting to changing demands.
Computer Hardware Architecture
- Modern computers share common architectural elements, including a central processing unit (CPU), main memory, buses, and storage. These components work together to execute programs, store data, and communicate with external devices.
- CPU and Main Memory: The CPU, or central processing unit, executes instructions and performs calculations, supported by main memory for data storage. This combination enables computers to perform a range of tasks, from basic operations to complex computations.
- Storage and Communication: Secondary storage (such as hard drives) and communication interfaces facilitate data storage and transfer. Communication adapters allow data exchange with other computers and networks, supporting collaborative processes and connectivity.
- CPU Components: The CPU includes an arithmetic logic unit (ALU), a control unit, and registers for temporary data storage. The ALU performs arithmetic and logical operations, while the control unit directs data flow and manages instruction execution.
- In modern systems, the CPU is contained within a microprocessor on a motherboard, which connects it to other components. This design enables compact and efficient processing, essential for the high-speed computations in today's computers.

Figure 5-2 A CPU that is plugged into a computer circuit board
Figure 5-3 Typical RAM module for a laptop, workstation, or server

Figure 5-4 Typical computer hard disk drive
Introduction to Network Models
- Network models define how data is transferred across networks by standardizing processes, enabling compatibility among devices and applications. Models such as OSI and TCP/IP are fundamental in establishing a shared framework that allows devices from different manufacturers to work together.
- Network models help organize complex processes into layers, making it easier to troubleshoot, design, and upgrade networks. Each layer has specific tasks, such as addressing, error checking, and session control, ensuring a clear division of responsibilities.
Two Main Models: The OSI model and the TCP/IP model are two widely accepted frameworks. OSI provides a seven-layer approach, while TCP/IP follows a four-layer structure. These models serve as teaching tools, design standards, and protocols for effective data communication across global networks.
OSI Model
- The OSI model, created by ISO and ITU, was developed to provide a comprehensive standard for networking functions, facilitating communication across different systems.
- Comprising seven layers, the OSI model organizes functions into logical categories, from physical data transmission to application-level services.
- As data travels down the OSI layers, each layer adds its own header or information, encapsulating data before transmission. This encapsulation ensures that data reaches its destination in a structured format, maintaining integrity and allowing for error detection and correction.
Physical and Data Link Layer
- Physical Layer: Foundational layer of the OSI model, is responsible for the actual physical connection between devices, handling raw data bit. It includes physical elements such as cables, switches, and connectors that enable devices to transmit signals (e.g., electrical, light, or radio waves). Standards and Protocols: Standards at this layer ensure consistency in data transmission. Examples include Ethernet (10BASE-T, 100BASE-TX), Fiber Optics for light-based data transfer, and DSL (Digital Subscriber Line) for high-speed internet over telephone lines. Data Transmission: At this level, data is handled as bits—0s and 1s—without interpretation, focusing purely on transmitting binary data across media.
- Data Link Layer: This layer oversees data transfer between directly connected nodes, grouping raw bits into frames and ensuring that each frame reaches its destination within the local network.This layer includes error-checking mechanisms such as checksums to identify and possibly correct errors in transmitted data.
- Data Frames: Frames carry MAC addresses, which uniquely identify devices on the local network, making this layer essential for device-to-device communication within the same network.
- Examples of Layer 2 Protocols: Protocols include Ethernet, Token Ring for shared access networks, and PPP (Point-to-Point Protocol), commonly used for internet connections, each providing methods for framing, error control, and access methods.
Network and Transport Layer
- Network Layer: It handles the routing of data packets between devices across different networks, using logical addressing to locate devices globally. Routers operate at this layer, directing packets based on IP addresses and routing algorithms to find the most efficient path to the destination.
- Key Protocols: Internet Protocol (IP) is central at this layer, providing a method for addressing and delivering packets across networks. ICMP (Internet Control Message Protocol) supports diagnostic functions, while IGMP (Internet Group Management Protocol) manages group communications.
- Transport Layer: This layer is responsible for ensuring reliable data transfer between devices, managing packet sequencing, and error recovery. It introduces connections to manage ongoing data exchanges between sender and receiver, making communication stable and structured.
- TCP vs. UDP: TCP (Transmission Control Protocol) offers connection-oriented communication with guaranteed delivery and sequencing. UDP (User Datagram Protocol), in contrast, is a connectionless protocol with faster but less reliable communication, used for real-time applications.
Session, Presentation and Application Layer
- Session Layer: The Layer establishes, manages, and terminates sessions between applications. It maintains active communication sessions between devices, handling interruptions and ensuring data synchronization. This layer enables structured data exchanges, where applications on different systems interact.
- Examples: Protocols like NetBIOS and SIP (Session Initiation Protocol) manage different types of sessions, from file transfers to real-time communication such as VoIP calls.
- Presentation Layer: This layer formats or translates data from lower layers into a form suitable for the Application Layer, ensuring compatibility between communicating systems. It also provides security through encryption and improves efficiency through data compression. SSL/TLS encryption occurs at this layer to secure data during transmission.
- Codecs for Multimedia: Codecs, like MPEG, compress and decompress audio/video, making this layer crucial for multimedia data handling in real-time applications.
- Application Layer: The Application Layer is the user-facing layer, where software applications interact directly with end users or other applications. It provides network services like email, file transfers, and web browsing, using protocols such as HTTP, FTP, and SMTP
TCP/IP Model
- The TCP/IP Model, originally developed for the ARPANET, is widely used for Internet communications and forms the basis for modern networking.
- Unlike OSI, TCP/IP consists of four layers: Link, Internet, Transport, and Application. Each layer consolidates OSI functions for simplicity.
- Data moves from one layer to another, with each layer adding headers that allow data to be delivered effectively. Encapsulation helps maintain data integrity and security throughout transmission.
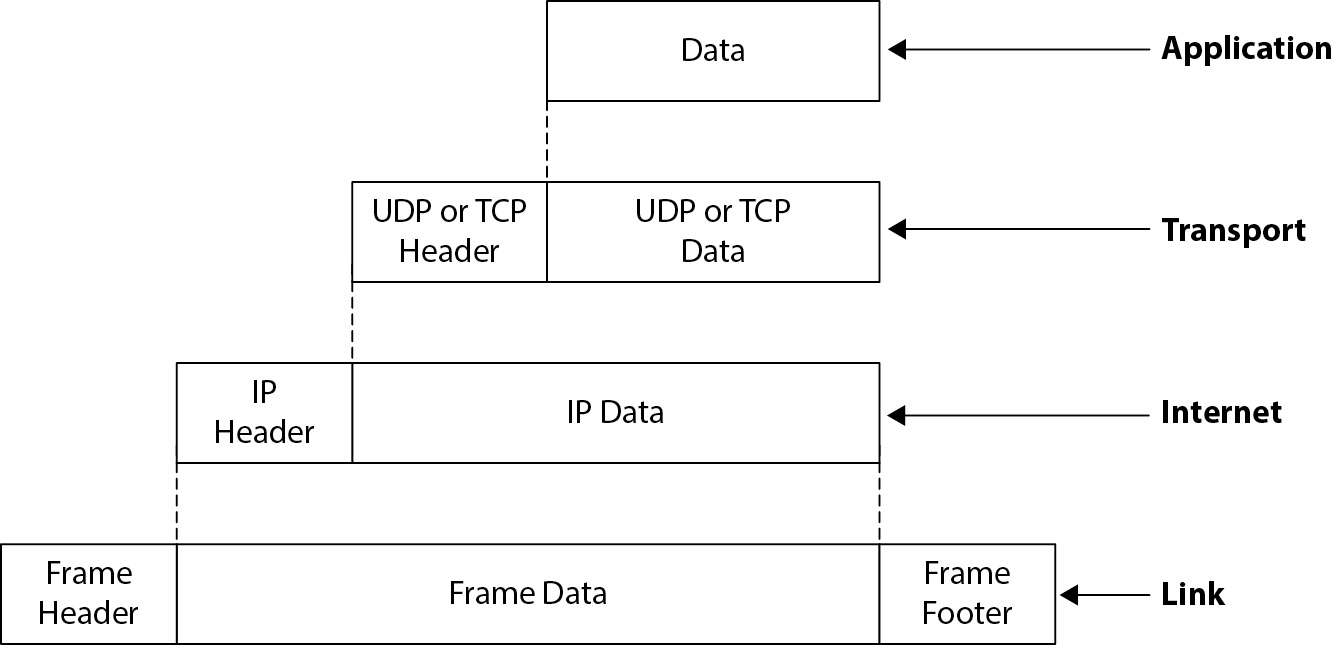
Figure 5-11 Encapsulation in the TCP/IP network model
Link and Internet Layer
- Link Layer: Link Layer manages data transmission within the local network, providing a direct connection between devices. This includes both physical connections (e.g., Ethernet cables) and hardware like NICs.
- In TCP/IP, the Link Layer combines OSI’s Physical and Data Link layers, handling both data framing and physical transmission.
- Internet Layer: The Internet Layer, also known as the Network Layer, manages logical addressing and routing across networks, ensuring data packets reach their intended IP destination.
- Protocols like IP and ICMP are core to this layer. IP provides logical addressing, while ICMP helps diagnose and troubleshoot network issues.
- Hosts create data packets, while routers forward these packets across networks, each working together to establish end-to-end communication across interconnected networks.
Transport and Application Layer
- The Transport Layer manages reliable data transmission through TCP and UDP, each offering unique properties.
- TCP provides error-checked, ordered delivery, ideal for web browsing and file transfers. UDP offers fast, connectionless communication, suitable for real-time applications like video streaming.
- Top Layer Functions: Like OSI’s Application, Presentation, and Session layers combined, this layer interacts with the end user, providing access to network services and applications.
- HTTP, FTP, and SMTP allow for web access, file transfers, and email services, while SNMP manages devices on IP networks.
- The Application Layer enables user actions, from sending emails to accessing websites, integrating with software applications to fulfill network requests.
Introduction to Network Technologies
- Network technologies provide essential protocols, architectures, and media that enable data communication within organizations and across the globe. From local setups (LAN) to large-scale networks (WAN), network technology is pivotal in facilitating secure and efficient data sharing.
- Understanding these technologies, architectures, and protocols is essential for IS auditors. They need to evaluate network infrastructures for compliance, security, and operational efficiency, which ensures alignment with industry standards and organizational needs.
- Categories: Network technologies can be broadly categorized into LANs, WANs, Wireless Networks, and protocols like TCP/IP. IS auditors benefit from familiarity with these to understand both the strengths and limitations of a network.
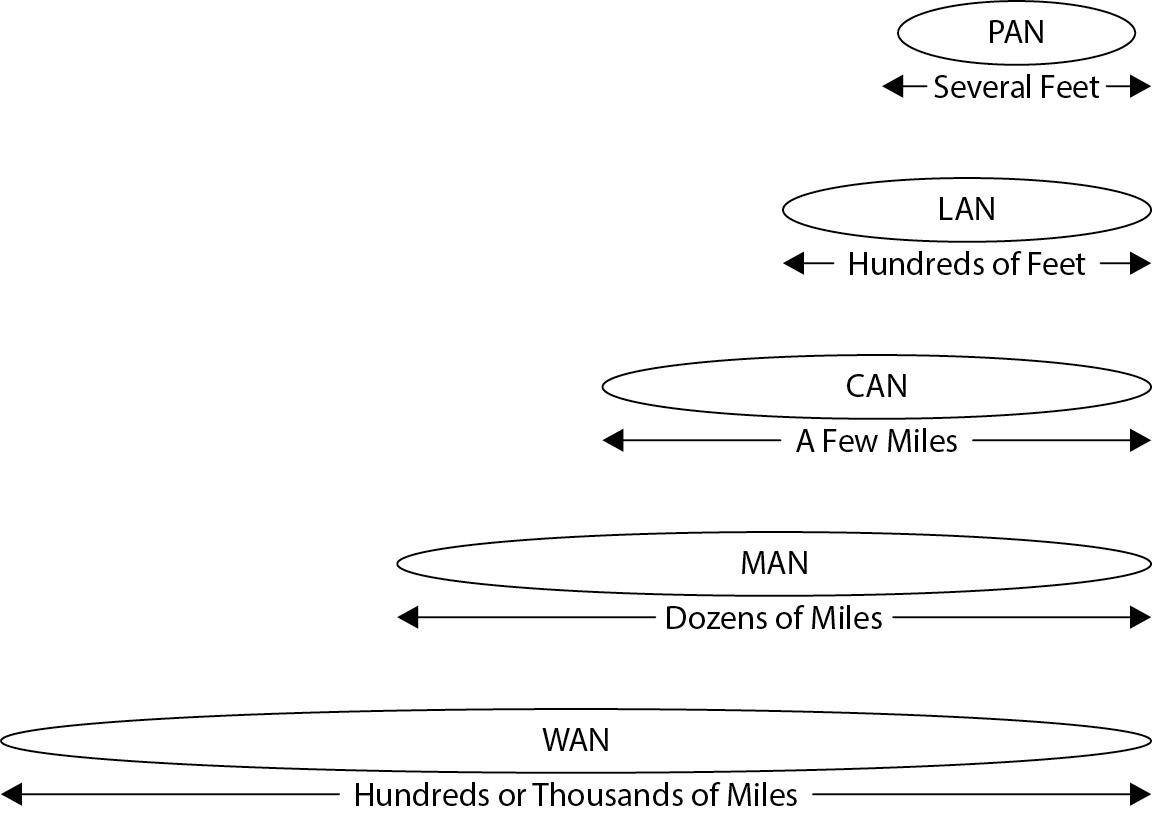
Figure 5-9 A comparison of network sizes
Local Area Networks (LANs) Overview
- Local Area Networks (LANs) connect devices within a restricted geographic area, typically within a building or office floor.
- LANs use short-range connections, providing high-speed data transfer between devices. LANs enable efficient data sharing and resource access among connected devices, such as printers, storage, and databases, within close proximity.
- LAN Physical Network Topologies:
- Star Topology
- Ring Toplology
- Bus Topology
- Cabling Types:
- Twisted-Pair
- Fibre Optic
- Category Rating
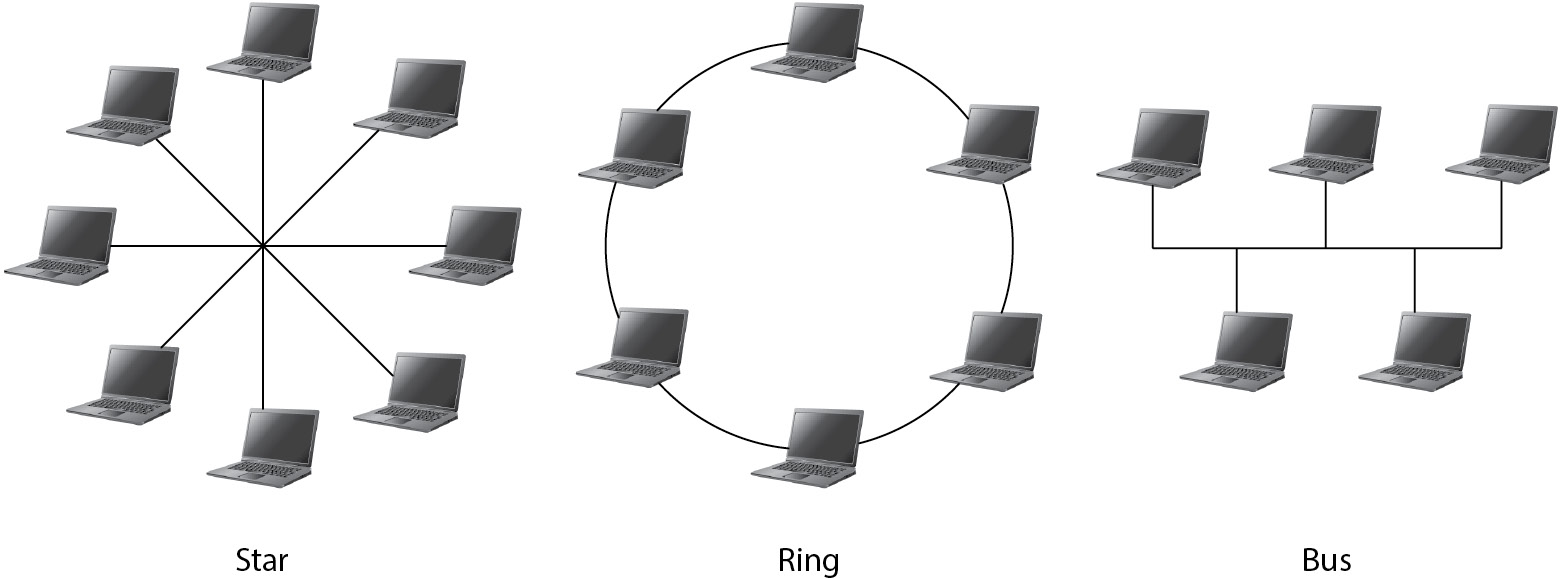
Figure 5-14 Network physical topologies: star, ring, and bus
Wide Area Networks (WANs) Overview
- Wide Area Networks (WANs) connect multiple LANs across extensive geographic areas, from cities to countries. WANs allow data transfer across large distances using various telecommunications links, making them essential for organizations with multiple branches.
- WAN technologies include T-Carrier (such as T1), SONET (Synchronous Optical Networking), Frame Relay, ISDN, and MPLS (Multiprotocol Label Switching). Each offers unique bandwidth, reliability, and cost-effectiveness suited to different organizational needs.
- Telecommunications providers often supply the physical connections and services necessary for WANs, supporting stable and continuous data flow between different locations.
- Auditors evaluate WAN setups for compliance with security standards, reliability, and operational costs. Ensuring that the WAN infrastructure meets performance requirements and secures data transfer over large distances is critical.
Cabling
Figure 5-15 Category 5 twisted-pair cable

Figure 5-16 Fiber optic cable with its connector removed to reveal its interior

Figure 5-17 Connectors link fiber optic cable to network equipment.

Figure 5-18 Coaxial cable
Wireless Networks Overview
- Wireless networks transmit data using radio frequencies, eliminating the need for physical cabling. They offer flexibility and mobility, making them ideal for both personal and organizational use.
- Wireless LAN (Wi-Fi) is the most popular form of wireless network, widely available in both homes and businesses. Other types include Bluetooth for short-range communication, Wireless USB, and NFC for close-proximity data transfer.
- Wireless networks adhere to specific standards, including 802.11 (Wi-Fi standards), Bluetooth, and IrDA (Infrared Data Association). Each standard determines speed, range, and reliability.
- Auditors assess wireless networks for security protocols, such as WPA3 and network encryption, to protect against unauthorized access and data breaches. They also examine compliance with data protection policies in wireless setups.
Network Management
- Network management encompasses monitoring, configuration, troubleshooting, and updating network devices to maintain optimal performance and security.
- Network management tools include SNMP (Simple Network Management Protocol) for monitoring, Syslog for logging, and NTP (Network Time Protocol) for time synchronization. These tools ensure consistency and operational efficiency across the network.
- Regular monitoring helps identify potential issues such as network congestion, device failures, or security breaches. Monitoring protocols enable real-time alerting and event logging.
- Auditors review network management practices to confirm the reliability of monitoring protocols and ensure that logging mechanisms are in place to detect unusual activities. Proper network management helps prevent security lapses and ensures smooth network operations.
Network Devices in Communication
- Network devices play a fundamental role in transmitting, receiving, and securing data across network infrastructures. They are categorized based on their functions, including data transmission, protocol conversion, and security facilitation.
- Network Devices:
- Network Adapter: Acts as the interface between a computer and the network, essential for connecting computers to LANs or wireless networks.
- Hub: A basic networking device that connects multiple computers in a local area network (LAN) but has limitations regarding efficiency and security due to its broadcasting nature.
- Gateway: Converts protocols to connect networks with different architectures, allowing seamless communication across distinct networks, such as LAN to WAN.
- Repeater and Bridge: Extends network range and bridges two network segments, helping maintain strong, reliable connectivity.
- Auditors focus on device configurations, access controls, and physical placement to ensure optimized performance and secure data handling within an organization’s network.
Switches and ATMs
- Switches connect devices in a LAN, selectively forwarding data packets to specific devices based on MAC addresses, thus minimizing unnecessary data traffic.
- Switches provide faster data transmission, better network performance, and improved security by not broadcasting data indiscriminately.
- Auditors evaluate switch configurations, focusing on VLAN (Virtual LAN) settings, access control lists, and MAC filtering to secure network communications and control data flow within sensitive segments.
- ATM is a telecommunications protocol used to support high-speed data transmission, notably in the core networks of telecommunication carriers.
- Communication in ATM occurs over virtual circuits, establishing a path before transmission to guarantee packet delivery.
- Auditors examine ATM configurations to ensure QoS settings align with business needs and that traffic prioritization does not inadvertently compromise security or performance across sensitive data streams.
IPsec - Security in IP Networks
- Introduction: IPsec, or Internet Protocol Security, secures IP-based communication by adding layers of encryption and authentication, essential for maintaining data integrity and confidentiality.
- Modes of Operation:
- Transport Mode: Encrypts only the data payload, leaving the IP header unchanged for routing purposes.
- Tunnel Mode: Encapsulates the entire IP packet, encrypting both the header and payload, making it suitable for secure virtual private networks (VPNs).
- IPsec establishes SAs to create secure channels, defined by authentication methods and encryption keys.
- Auditors examine IPsec configurations, focusing on VPNs, to ensure proper encryption and authentication for sensitive data transmissions, particularly over the internet.
IPv4 Addressing
- IP Addressing: IP addressing provides a unique identifier for each device on a network, ensuring that data reaches the correct destination.
- IP Structure:
- IPv4: A 32-bit address format, divided into four octets (e.g., 192.168.1.1). Each octet can range from 0 to 255, providing around 4.3 billion unique addresses.
- Subnet Mask: Used to distinguish network portions from device portions within an IP address, aiding in organizing devices within networks.
- Subnetting: Divides large networks into smaller subnetworks, improving traffic management and security.
- Auditors ensure IP addresses and subnet masks are assigned logically and comply with
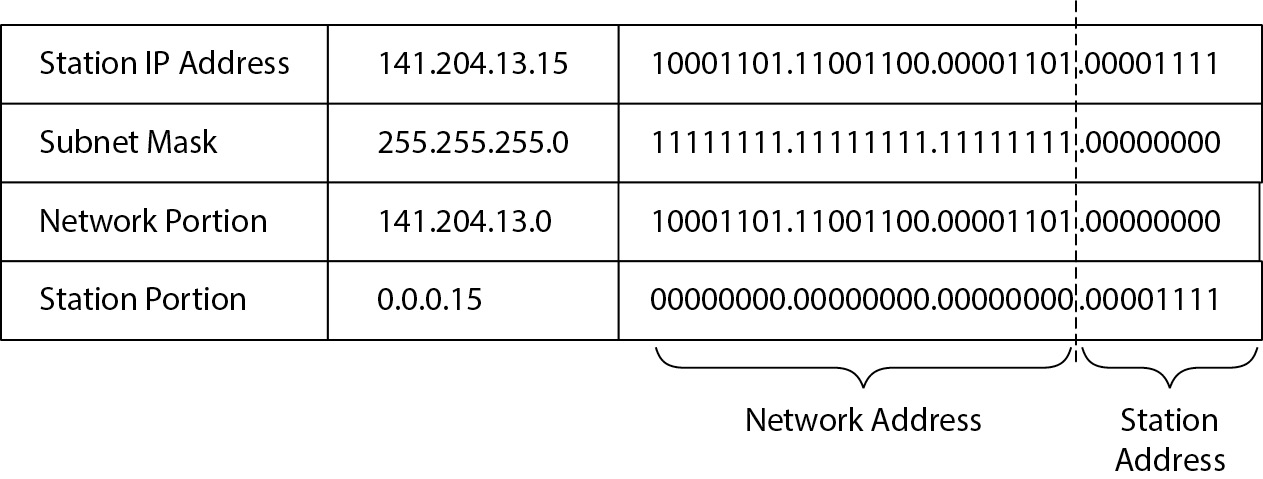
Figure 5-22 A subnet mask denotes which part of an IP address signifies a network and which part signifies a station on the network.
Classful and Classless Networks
- Classful Networks: Originally, IPv4 addresses were divided into classes (A, B, C) to allocate IP addresses efficiently.
- Class A: Large networks with over 16 million addresses.
- Class B: Medium-sized networks, up to 65,536 addresses.
- Class C: Small networks, allowing up to 256 addresses.
- Limitations: Classful addressing was wasteful, often leading to unused addresses.
- Classless Interdomain Routing (CIDR): Introduced to allow flexible allocation by using variable-length subnet masks.
- CIDR Notation: Uses a suffix to indicate subnet mask length (e.g., 192.168.1.0/24).
- CIDR minimizes IP waste and improves network efficiency. Auditors check for appropriate CIDR usage and IP allocation to align with organizational needs.
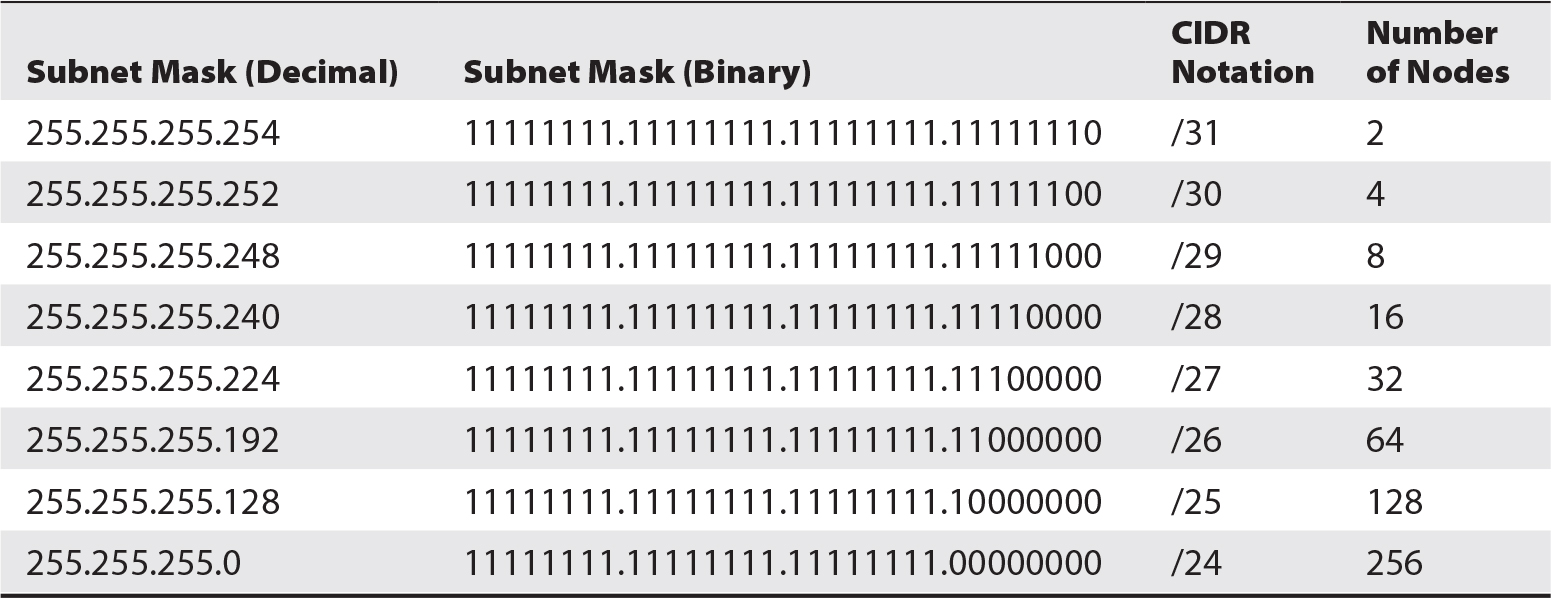
Table 5-9 Classless Network Subnet Masks
IPv6 Addressing - Overcoming IPv4 Limitations
- IPv6 was developed to address IPv4 limitations, primarily the shortage of available addresses, by expanding the address space to 128 bits.
- Address Format: Written as eight groups of four hexadecimal digits, separated by colons (e.g., 2001:0db8:85a3:0000:0000:8a2e:0370:7334).
- Enhanced Capacity: Supports 2^128 addresses, sufficient for global network expansion.
- IPv6 Subnetting:
- Fixed Prefix Length: Standard /64 subnet size simplifies network planning.
- Many devices now support both IPv4 and IPv6 (dual-stack), enabling gradual transition.
- Auditors assess IPv6 adoption, ensure compatibility, and check for secure configurations to prevent unauthorized access.
Protocol Data Units (PDUs) in Network Layers
- PDUs are the specific units of data transmitted at each OSI layer, essential for understanding data encapsulation.
- Layer-Specific Terms:
- Physical Layer: Bits
- Data Link Layer: Frames
- Network Layer: Packets
- Transport Layer: Segments (TCP) or Datagrams (UDP)
- Layer-Specific Terms:
Types of Protocols
- FTP (File Transfer Protocol): Allows batch transfer of files between systems; lacks encryption.
- FTPS and SFTP: Secure versions of FTP using SSL/TLS and SSH, respectively, to protect data integrity and confidentiality.
- SMTP (Simple Mail Transfer Protocol): Routes email over the internet; lacks native security.
- POP and IMAP: Email retrieval protocols; typically unsecured but can use SSL/TLS for encryption.
- Instant Messaging (IM): Real-time messaging over the internet; can be encrypted for security.
- DNS (Domain Name System): Translates domain names to IP addresses, essential for internet navigation. Resolves names like "example.com" to IP addresses, enabling users to access services without memorizing IP addresses.
- LDAP (Lightweight Directory Access Protocol): Used for managing and accessing directory information, often in enterprise environments. Centralized access to user information and computing resources; integrates with Microsoft Active Directory.
Virtual Private Networks (VPNs) - Secure Remote Connections
- VPNs create secure, encrypted tunnels over public networks, allowing private data exchange.
- Uses: Remote employee access, secure branch office connections.
- Types of VPNs:
- Site-to-Site VPNs: Connects two networks over the internet, typically used for branch offices.
- Remote Access VPNs: Allows individuals to access a network remotely.
- Encryption Standards: Ensure strong encryption methods like IPsec and SSL/TLS are used.
- Access Controls: Auditors assess VPN access policies to confirm that only authorized users can connect.
Summary
- IT Service Management
- Business Continuity and Disaster Recovery
- SLA Management
- IT operations and exception handling
- Security Monitoring
- Data Management
- Types of Computers
- Network models
- Network Technologies and Toplologies
- IP addressing
- VPNs
