Introduction
Purpose of this document
This document addresses the cybersecurity perspective in engineering of electrical and electronic (E/E) systems within road vehicles. By ensuring appropriate consideration of cybersecurity, this document aims to enable the engineering of E/E systems to keep up with state-of-the-art technology and evolving attack methods.
This document provides vocabulary, objectives, requirements and guidelines related to cybersecurity engineering as a foundation for common understanding throughout the supply chain. This enables organizations to:
- define cybersecurity policies and processes;
- manage cybersecurity risk; and
- foster a cybersecurity culture.
This document can be used to implement a cybersecurity management system including cybersecurity risk management.
Organization of this document
An overview of the document structure is given in Figure 1. The elements of Figure 1 do not prescribe an execution sequence of the individual topics.
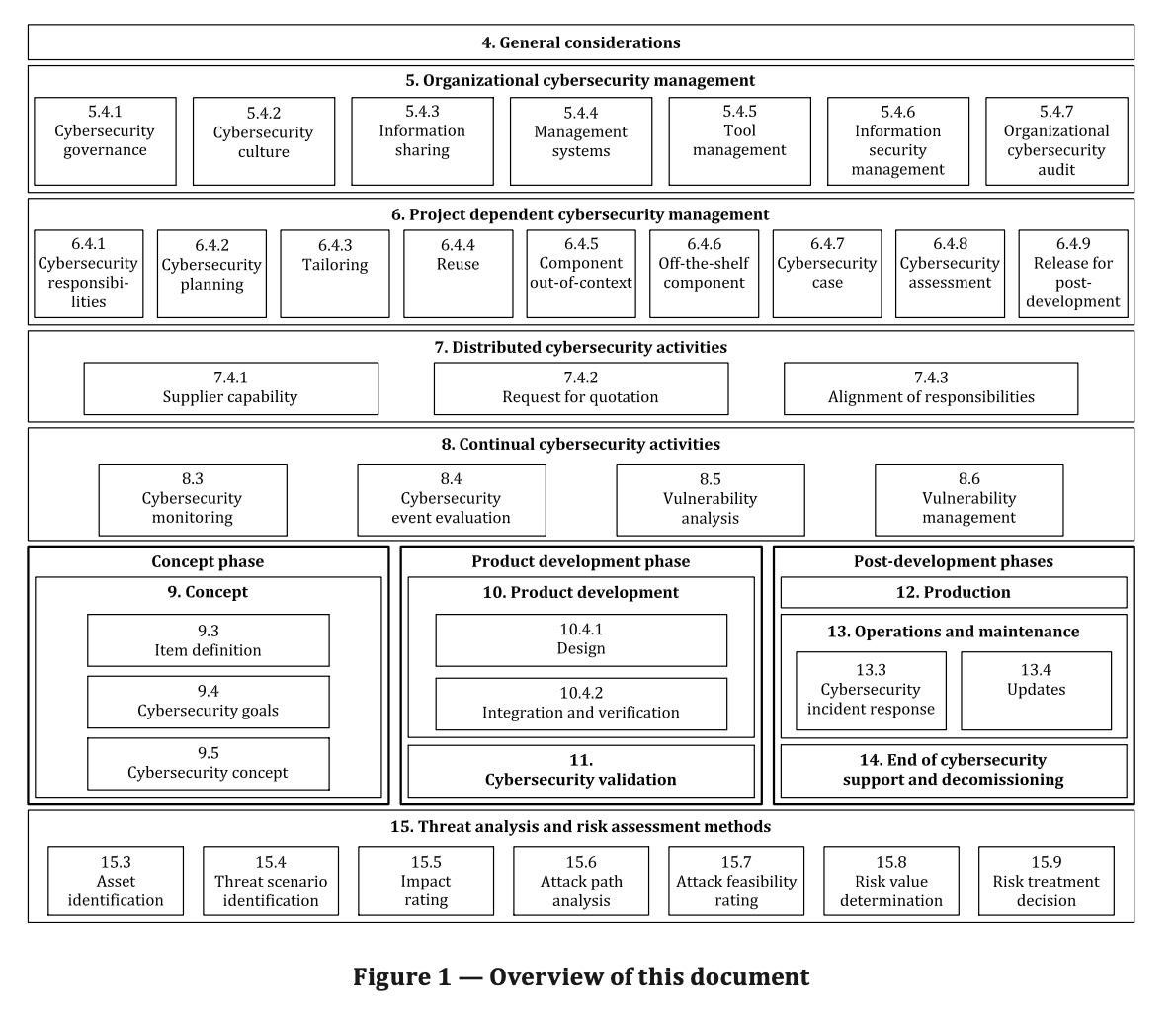
Clause 4 (General considerations) is informational and includes the context and perspective of the approach to road vehicle cybersecurity engineering taken in this document.
Clause 5 (Organizational cybersecurity management) includes the cybersecurity management and specification of the organizational cybersecurity policies, rules and processes.
ISO/SAE 21434:2021(E)
Figure 1 — Overview of this document
- Clause 6 (Project dependent cybersecurity management) includes the cybersecurity management and cybersecurity activities at the project level.
- Clause 7 (Distributed cybersecurity activities) includes requirements for assigning responsibilities for cybersecurity activities between customer and supplier.
- Clause 8 (Continual cybersecurity activities) includes activities that provide information for ongoing risk assessments and defines vulnerability management of E/E systems until end of cybersecurity support.
- Clause 9 (Concept) includes activities that determine cybersecurity risks, cybersecurity goals and cybersecurity requirements for an item.
- Clause 10 (Product development) includes activities that define the cybersecurity specifications, and implement and verify cybersecurity requirements.
- Clause 11 (Cybersecurity validation) includes the cybersecurity validation of an item at the vehicle level.
- Clause 12 (Production) includes the cybersecurity-related aspects of manufacturing and assembly of an item or component.
- Clause 13 (Operations and maintenance) includes activities related to cybersecurity incident response and updates to an item or component.
- Clause 14 (End of cybersecurity support and decommissioning) includes cybersecurity considerations for end of support and decommissioning of an item or component.
- Clause 15 (Threat analysis and risk assessment methods) includes modular methods for analysis and assessment to determine the extent of cybersecurity risk so that treatment can be pursued.
Clauses 5 through 15 have their own objectives, provisions (i.e. requirements, recommendations, permissions) and work products. Work products are the results of cybersecurity activities that fulfil one or more associated requirements.
“Prerequisites” are mandatory inputs consisting of work products from a previous phase. “Further supporting information” is information that can be considered, which can be made available by sources that are different from the persons responsible for the cybersecurity activities.
A summary of cybersecurity activities and work products can be found in Annex A.
Provisions and work products are assigned unique identifiers consisting of a two-letter abbreviation (“RQ” for a requirement, “RC” for a recommendation, “PM” for a permission and “WP” for a work product), followed by two numbers, separated by hyphens. The first number refers to the clause, and the second gives the order in the consecutive sequence of provisions or work products, respectively, of that clause. For example, [RQ-05-14] refers to the 14th provision in Clause 5, which is a requirement.
