Section 3.3 Threat Hunting
As you study this section, answer the following questions:
What types of sources can be used for intelligence gathering?
What are zero-day threats, and why are they particularly dangerous?
Why do some organizations choose to keep their threat intelligence private?
What are the benefits of threat hunting?
Define threat hunting
Understand the process of threat profiling
Identify the indicators of different threat types
The key terms for this section include:
| Term | Definition |
|---|---|
| Indicators | Indicators are bits of information that can be used to identify or describe a known threat. Indicators could include unusual activity, a unique filename, attack methods, or malicious commands. |
| Threat hunting | A cybersecurity technique designed to detect the presence of threats that have not been discovered by normal security monitoring or required additional research. |
| Profiling | The process of determining who could be a threat, how they could access a system, and what actions they will take once inside. |
| Misconfiguration hunting | Searching for misconfigured systems, services, or applications that attackers could exploit. |
| Isolated network hunting | Searching for vulnerabilities in physical access points that could be used to gain access to the isolated network. |
| Business-critical asset hunting | Searching for vulnerabilities and threats that could impact business-critical assets. |
| Managed security service providers (MSSPs) | Providers that offer the necessary knowledge, skills, resources, and analytic tools to help organizations locate unusual activities and hidden threats efficiently. |
This section helps you prepare for the following certification exam objectives:
| Exam | Objective |
|---|---|
| CompTIA CySA+ CS0-003 | 1.2 Given a scenario, analyze indicators of potentially malicious activity
1.4 Compare and contrast threat-intelligence and threat-hunting concepts
1.5 Explain the importance of efficiency and process improvement in security operations
2.5 Explain concepts related to vulnerability response, handling, and management
3.1 Explain concepts related to attack methodology frameworks
3.2 Given a scenario, perform incident response activities
3.3 Explain the preparation and post-incident activity phases of the incident management life cycle
|
| TestOut CyberDefense Pro | 1.1 Monitor networks
1.2 Monitor software and systems
1.3 Implement Logging
2.1 Perform threat analysis
2.2 Detect threats using analytics and intelligence
4.1 Manage security incidents
4.3 Analyze Indicators of compromise
|
3.3.1 Threat Hunting Overview
Click one of the buttons to take you to that part of the video.
Threat Hunting Overview 00:00-01:43 In this video, we're going to discuss threat hunting. Whenever possible, security should be proactive instead of reactive. Reactive measures are taken only after an incidence response system identifies a problem. At this point, it's too late to prevent an attack. You're simply mitigating damage to your system. Threat hunting is a proactive approach that assumes attackers may have already accessed your system and gives you an opportunity to find and end threats before your incidence response system alerts you to malicious activity.
A hypothesis-based investigation typically begins because other organizations have shared information about a newly identified threat. First, you'll want to establish a hypothesis.
Before you start searching blindly, you'll want to determine which threat(s) are likely to occur. This hypothesis may be a result of recent attacks on similar organizations, or it could be the result of a recently discovered threat.
Similar to a criminal investigation, you'll want to build a profile. Who could be a threat, how could they access your systems, and what actions would they take once they got inside? The information gathered from intelligence sites and other sources during the profiling phase will help narrow down the scope of your search.
Threat hunting tactics combine manual work with common tools that are already used for security monitoring or incident response.
Because threat hunting assumes that your system could already be compromised, you'll operate under the assumption that your security systems are not effective. You'll need to review log files, registry files, captured packets, and other information from your monitoring software.
Benefits of Threat Hunting 01:43-02:39 Threat hunting can be time consuming, but if it's managed efficiently, it can provide several benefits.
Threat hunting can help to reduce the attack surface area by revealing entry points (or attack vectors), ineffective security controls, and other opportunities for improvement. As you begin to uncover attackers' strategies, you'll be better able to identify targeted assets. This gives you the opportunity to bundle critical assets so that additional security controls can be added.
Threat hunting integrates known intelligence by combining information gathered from external and internal sources. This method of investigation gives analysts an opportunity to enhance their skills and to improve their detection capabilities.
Reactive threat hunting can be stressful. Proactive hunting, on the other hand, can provide an opportunity to use your security skills without the pressure of an active incident.
Summary 02:39-02:48 That's it for this lesson. In this video, we reviewed threat hunting and its benefits.
3.3.2 Threat Hunting Facts
This lesson covers the following topics:
- Threat hunting
- Attack focus areas
- Threat hunting benefits
- Managed security service providers (MSSPs)
Threat Hunting
Threat hunting is a cybersecurity technique designed to detect the presence of threats that have not been discovered by normal security monitoring or required additional research. The purpose of threat hunting is to analyze routine activities and network traffic to identify potential anomalies indicative of malicious actions which may result in a complete breach. Threat hunting describes the methods used to identify malicious cyber activities within an organization's network in a systematic way.
Threat hunting subscribes to an "assume breach" mentality; a crucial strategy designed to help protect against advanced cyberattacks, mitigate any intrusion's impact, and develop a procedural approach to cyber resilience. Cyber threat hunting is a primarily manual process whereby a threat hunter (or security analyst) reviews various sources of information and uses their skills and experience to identify potential threats. They typically follow a hypothesis-based investigation process.
Establish a Hypothesis
Before you start searching, determine which threats are likely to occur. This hypothesis may be a result of recent attacks on similar organizations, or it could be the result of a recently discovered threat. Based on cyber threat intelligence, known attack techniques, and other information, threat hunters develop and validate assumptions about potential threats while gathering and analyzing data from various sources, both within the organization and externally. For example, after finding evidence that a threat actor has gained access to the environment, a threat hunter might look for evidence that the attacker also performed lateral movement.
Profile Threat Actors and Activities
Profiling involves determining who could be a threat, how they could access a system, and what actions they will take once inside. To improve their effectiveness, threat hunters focus on well-established tactics, techniques, and procedures (TTPs), indicators of compromise (IoCs), indicators of attack (IoAs), and confidence levels provided by threat information data to identify threats, understand exploits, and reveal an attacker's activities.
Entity-driven hunts look for external threat actors based on TTPs observed by the cyber defense community in recent attacks identified. Crowdsourced attack data is a valuable source of information as it exposes the TTPs of current, active cyberattacks. An effective threat hunt team can often detect a threat actor before they are in a position to damage the environment.
Threat Hunting Tactics
Threat hunting tactics combine manual work with automated tools. Tools that you use for security monitoring or incidence response can be used during the threat hunting process. Here are just a few considerations for threat hunting:
- You can review log files, scan Registry files, and review packets captured on your network.
- Run programs, such as Task Manager, to determine what processes are being used and may be taxing the CPU. This is known as executable process analysis.
- The information gathered during the profiling phase will help narrow down the scope of your search.
- Information gathered from intelligence sources can provide better insight into the tools and methods that are being used.
Attack Focus Areas
The following table includes three areas that are common attack focus areas that are important to include in threat hunting.
| Focus Area | Explanation |
|---|---|
| Misconfiguration hunting | Misconfigurations in IT systems can create vulnerabilities that attackers can exploit. Misconfiguration hunting involves searching for misconfigured systems, services, or applications that attackers could exploit, including searching for weak passwords, open ports, or unpatched software. |
| Isolated network hunting | Isolated networks, such as air-gapped networks or networks with limited connectivity to the internet, are often thought to be more secure. However, attackers can still target these networks by exploiting vulnerabilities in connected systems or through physical access. Isolated network hunting involves searching for vulnerabilities in physical access points that could be used to gain access to the isolated network. |
| Business-critical asset hunting | Attackers often target business-critical assets, such as databases, servers, or applications. Business-critical asset hunting involves searching for vulnerabilities and threats that could impact these assets by searching for unauthorized access attempts, unusual traffic patterns, or suspicious activity that could indicate an attack. An organization's processes used to manage critical assets can also be targeted, such as new user creation, money transfer, access permission approvals, and other similar high-risk functions. |
Threat Hunting Benefits
Threat hunting can be time-consuming. However if managed efficiently, threat hunting can provide several benefits:
| Benefit | Description |
|---|---|
| Reduce the attack surface area | Threat hunting can help to reduce the attack surface area by the discovery of:
|
| Bundle critical assets | As you begin to uncover the strategies used by attackers, you will be better able to identify targeted assets. This is an opportunity to bundle critical assets so that additional security controls can be added. |
| Integrated intelligence | Threat hunting combines information gathered from external intelligence with information gathered from internal systems. |
| Improve detection capabilities | Reactive threat hunting can be stressful. Proactive hunting, on the other hand, can provide an opportunity to use skills without the pressure of an active incident. Analysts can use this time to enhance skills and to improve detection capabilities. |
Dedicated threat-hunting teams are out of reach for most organizations, so managed security service providers (MSSPs) fill this gap by providing the necessary knowledge, skills, resources, and analytic tools to help organizations locate unusual activities and hidden threats efficiently.
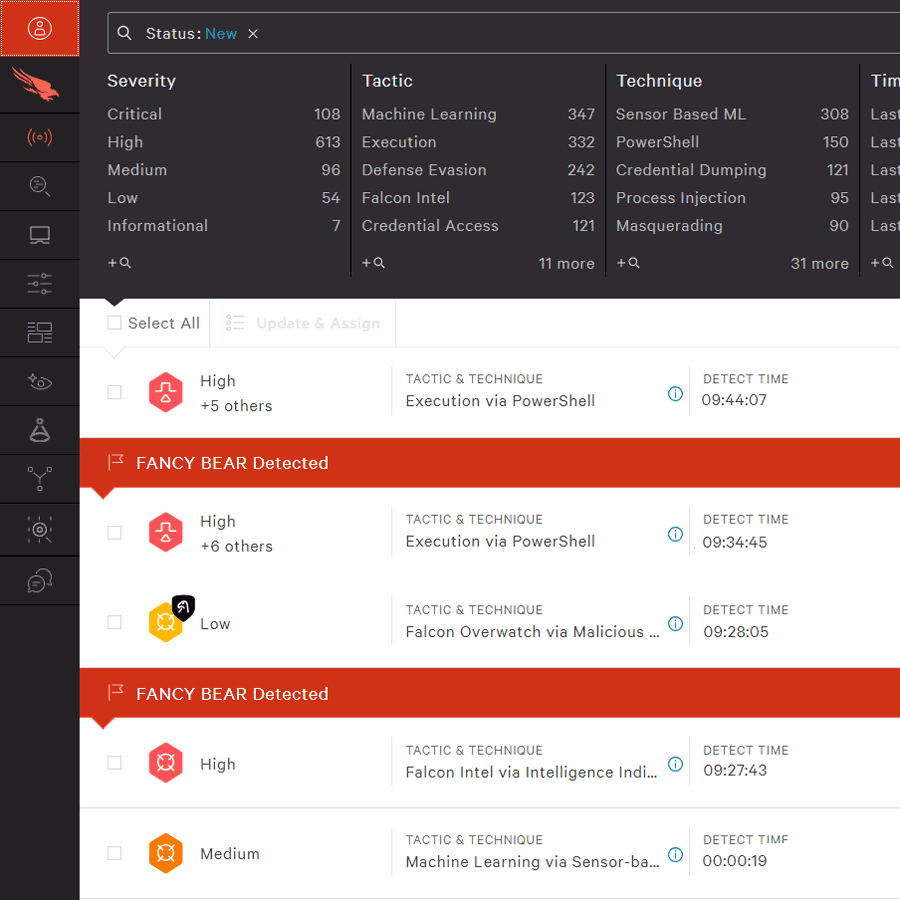
Description
The header at the top shows a search bar that represents the Status: New. The upper section has three compartments with different options for each of the following: Severity, Tactic, and Technique.
Below the compartments, there are sections titled "Fancy Bear Detected," with items included in each section given a Severity, a Tactic and Technique, and a Detect Time.
CrowdStrike Falcon Complete managed services monitoring dashboard displaying observed TTPs. (Screenshot used with permission from CrowdStrike).
3.3.3 Analyzing Indicators of Compromise (IoC)
Click one of the buttons to take you to that part of the video.
Analyze Indicators of Compromise 00:00-01:13 There are many aspects to cybersecurity, and one of them is being watchful for any intrusion red flags on a network or host. We call these red flags indicators of compromise.
Indicators of compromise, or IOCs, are artifacts or forensic data that strongly suggest the presence of intrusion. You can look for these in all kinds of elements, like files, system logs, and network communications.
Just like a detective examines evidence and investigates to determine what took place, you as a cybersecurity specialist needs to do the same. So, what type of evidence should you look for?
First and foremost, you should try to notice any type of anomalous activity. In other words, look for anything that's out of the ordinary. To know what's out of place, though, you need to know what normal is first.
This is why we establish a baseline for things like resource consumption, network traffic, file system access, and which software programs should be running at a given time.
Once you have a baseline for how everything should look, you can then monitor for abnormal behavior. Let's go over some things to watch out for.
Processor Consumption 01:13-01:51 If you notice that your processor consumption is higher than usual, that's a great place to start. Dig deeper with a process analysis tool. For example, if you're working on a Windows machine, Task Manager lets you see all the processes running and how much the processor or CPU is being used. And you can kill—which just means stop—any unwanted processes.
Process names aren't always easy to identify. So having a baseline of which processes normally run on a host gives you a good starting point.
Then if you see a process you don't recognize, you can do some quick research to find out what it is.
And then there's memory consumption.
Memory Consumption 01:51-02:20 It's important to note that your operating system always tries to optimize memory usage, so high memory usage alone doesn't indicate a problem. But per-process use can provide helpful information when you're searching for potential intrusions. If you notice high usage on a process you don't recognize or on a process that should be much lower, you should investigate that. Excessive memory consumption is a major symptom of malware.
Drive and File System Consumption 02:20-03:28 Now let's talk about drive and file consumption. Malware's goal is often to steal data. So, although fileless malware does exist, most of it will interact with the file system in some way, leaving a trail of metadata that can lead you to the compromise.
File system viewers can help you analyze a file's metadata. These viewers can look through a file system for keywords and focus searches on common staging areas. File carving tools can recover file metadata that's been deleted.
If you do suspect malware, you'll want to check your file system for possible staging areas. Malware uses one location to stage data for exfiltration. These areas could include temp files, a user's profile folder, a log file, or the Recycle Bin. The data staged to these areas is typically compressed and encrypted, so it's easy to move and hard to detect.
You can use disk utilization tools to scan a file system and gather real-time disk usage information. These tools provide a visual mapping of storage space that includes all folders, files, sizes, and extensions.
Bandwidth Consumption 03:28-03:56 Along the same lines, excessive bandwidth consumption can also indicate an intrusion. For example, a denial-of-service attack is focused on consuming all available bandwidth, which causes services to be unavailable to users. There are natural ebbs and flows in your network traffic, but unusual traffic spikes or unavailable services due to bandwidth consumption are most definitely red flags.
Irregular Network Traffic 03:56-05:08 Beyond excessive bandwidth consumption, you should monitor network traffic for other irregularities. Here's just a short list of possible things to look for: unusual endpoint or traffic patterns, such as SSH or VPN tunnels in unusual geographic locations; HTTP requests to database-backed services; transfers using FTP, IM, or P2P; and HTTP or HTTPS transfers to easily created consumer storage accounts like OneDrive or Google Drive. Any of these can be indicators of data exfiltration.
Another irregularity to look for is non-standard port usage. The Internet Assigned Numbers Authority, or IANA, has established a list of TCP and UDP port mappings. Although you can configure applications to work on any port, legitimate application servers use these standard ports by default. Configuration documents should indicate which ports are allowed or blocked. You can use this information to create rules for non-standard port-usage detection.
Also, pay attention to traffic that connects to external IP addresses or unexpected outbound communication.
Unauthorized Privileges 05:08-05:50 Now, let's look at how access issues can be indicators of compromise. To gather data in the first place, an attacker has to gain access to the information they want. Common indicators of unauthorized privileges include: failed logins, unauthorized sessions, new accounts being created, after-hours access, and guest account usage.
Privilege escalation involves obtaining access to resources or permissions that a user normally wouldn't have. Ideally, an attacker would want to escalate to administrator or root-level privileges. This would allow him or her to access a role range of things, including sensitive files. Monitoring tools can help alert you to these anomalous access patterns.
Software and Service Irregularities 05:50-06:36 Unexpected pop-up windows and unusual error messages are tell-tale signs of compromise as well. This is especially true if a user is getting Windows UAC pop-ups. These prompts are typically only shown when you install new software, so if this window pops up out of the blue, that's definitely cause for concern.
If you notice this type of activity, look for unusual request patterns, scan for code injection strings in HTTP requests and, of course, check for malware on the host.
Services will often alert you to issues by their behavior. Any time you have services restarting, crashing, or stopping, you should investigate to determine whether there's been a security incident or if there's a maintenance issue that needs to be addressed.
Application Logs 06:36-06:51 The last area we'll discuss is the use of logs in your search for compromise. Monitoring application logs—such as DNS event logs, HTTP access logs, FTP access logs, and SQL databases—can provide valuable insights for your search.
Summary 06:51-07:31 And that's all for this lesson. In this lesson, we explored indicators of compromise. First, we talked about creating baselines so that you're able to judge normal activity against abnormal activity. Then we reviewed excessive consumption of different resources. Next, we discussed irregularities in network traffic and access. Then we talked about indicators found in software and service anomalies. We finished this lesson by looking at how application logs can bring anomalies to light. Monitoring and analyzing these indicators are crucial for detecting and responding to cybersecurity threats effectively. Remember, vigilance and proactive monitoring are key to maintaining a secure digital environment.
3.3.4 Indicators of Compromise (IoC) Facts
Cybersecurity analysts and threat hunters collect indicators of compromise (IOCs) to identify, investigate, and mitigate threats.
This lesson covers the following topics:
- Indicators of compromise (IoCs)
- Indicators of compromise examples
- Role of digital forensics
- Analyzing indicators of compromise
Indicators of Compromise (IoCs)
As the name implies, indicators of compromise do not prove a successful attack or breach has occurred. Instead, an IoC points to a specific event, pattern, or sequence of events that may indicate trouble. After identifying an IoC, security analysts must validate it to more confidently determine if it is a false positive, warrants monitoring, or requires a full incident response. Indicators such as these help security analysts identify malicious actors early in the cyber kill chain, possibly before significant damage occurs. Attack indicators are similar to IoCs, but instead of focusing on the forensic analysis of an attack that has already happened, attack indicators focus on identifying the attacker's activities as an attack is occurring.
Indicators of compromise (IoCs) are artifacts or forensic data that strongly suggest the presence of an intrusion. These IoCs can be found in various elements such as files, system and application logs, network monitoring software, endpoint protection tools, and security information and event management (SIEM) platforms. Security teams can quickly identify and respond to security threats by collecting and analyzing these indicators. IoCs can help provide a summary of malicious actions, giving security professionals an easy way to identify the potential source of a security incident. The summary information also informs a response plan by identifying the systems and services to isolate or monitor and which users and accounts may need to be locked. Collecting and analyzing IoCs makes it possible to accurately and efficiently describe security issues, helping protect organizations from future threats.
Indicators of Compromise examples
Cybersecurity analysts are essentially looking for anomalous activity—for patterns or items that are not normal. A baseline must first be established to know what is anomalous. These should include things like resource consumption, network traffic, files, and knowing what software and programs are running on the system. Once established, monitoring for anomalous activity is possible. The following table contains several examples of indicators of compromise.
| Indicator | Explanation |
|---|---|
| Processor consumption | If your processor consumption is higher than its baseline, you can dig deeper using a process analysis tool. For example, if you are working on a Windows machine, the Task Manager lets you see all the processes running and how much the processor or CPU is being used. You can stop or kill any unwanted processes. |
| Memory consumption | Memory usage should be monitored. It is important to note that your operating system always tries to optimize memory usage, so high memory usage alone does not indicate a problem. However, the per-process use of memory can provide helpful information when searching for potential intrusions. If you notice a high usage on a process you do not recognize or on a process that should be much lower, you know you should investigate. |
| Drive and file system consumption | Most malware will interact with the file system in some way, leaving a trail of metadata that can help to indicate compromise. If you suspect malware, you will want to check your file system for possible staging areas. Malware uses one location to stage data for exfiltration. These areas could include temp files, a user's profile folder, a log file, or the recycle bin. The data staged to these areas is typically compressed and encrypted, so they are easy to move and hard to detect. |
| Bandwidth consumption | Excessive bandwidth consumption can also be an indication of intrusion. For example, a denial-of-service attack is focused on consuming all available bandwidth which causes services to be unavailable to users. Worm-type malware can consume bandwidth as it replicates across the network. There are natural ebbs and flows in your network traffic, but unusual traffic spikes or unavailable services due to bandwidth consumption are red flags to investigate. |
| Irregular network traffic | Some irregular network traffic or endpoint traffic pattern indicators include:
|
| Unauthorized privileges | Common indicators of unauthorized privileges include:
Privilege escalation involves obtaining access to resources and permissions that a user normally would not have. Ideally, an attacker would want to escalate to administrator or root-level privileges. This would allow them access to many things, including sensitive files. Monitoring tools can help alert you to these anomalous access patterns. |
| Software and service irregularities | Common indicators of software irregularities include:
Common indicators of service irregularities include:
|
In addition to host-based software applications, you should monitor, review, and investigate network-based software application logs as needed. You should also review DNS event logs, HTTP access logs, FTP access logs, and SQL event logs. The following table lists several types of logs you should monitor, and the type of information each contain.
| Log Type | Description |
|---|---|
| DNS event logs | DNS event logs include:
|
| HTTP access logs | HTTP access logs include:
|
| FTP access logs | FTP access logs include:
|
| SQL event logs | Structured Query Language (SQL) database logs can be customized to include many types of alerts and logging capabilities. A few key items are:
|
Role of Digital Forensics
Indicators of compromise (IoCs) can be identified using digital forensics techniques, which analyze digital artifacts left behind on a compromised system or network. These artifacts include log files, memory dumps, network traffic, and file system information. Once IoCs have been identified, they are used to generate threat intelligence data to detect and prevent future attacks of a similar nature. For example, IoCs can be input into security tools such as intrusion detection systems (IDS) or security information and event management (SIEM) systems to help detect and respond to similar events in real time. Additionally, digital forensic analysis may reveal specific details regarding vulnerabilities or misconfigurations that led to a breach. Overall, digital forensics plays a critical role in identifying and analyzing IoCs.
Frequently, IoCs are provided to organizations through intelligence reports and electronic data feeds, which often update security products like Web Application Firewalls, EDR solutions, web proxies, and intrusion detection tools. As the community of defenders increase in size and capability, the information and details made available to others to help look for signs of trouble also increases. Some indicators are very apparent, such as ransomware infection of a desktop, while other indicators are far more subtle and non-obvious.
For most organizations, threat hunting is only possible with help from individuals and organizations working at the forefront of digital forensics. Applying threat-hunting techniques often requires using data provided by information-sharing platforms and "field notes" created by professional incident responders. For example, sites such as Uncoder.io provide "cookbook" information that can be translated into many different SIEM and EDR formats. Feeding this data into SIEM and EDR products helps quickly locate indicators of compromise. When an organization becomes aware of specific threat actor groups targeting particular products and industries, services like uncoder.io provide the precise search criteria threat hunters need to help them quickly and efficiently locate signs of trouble.
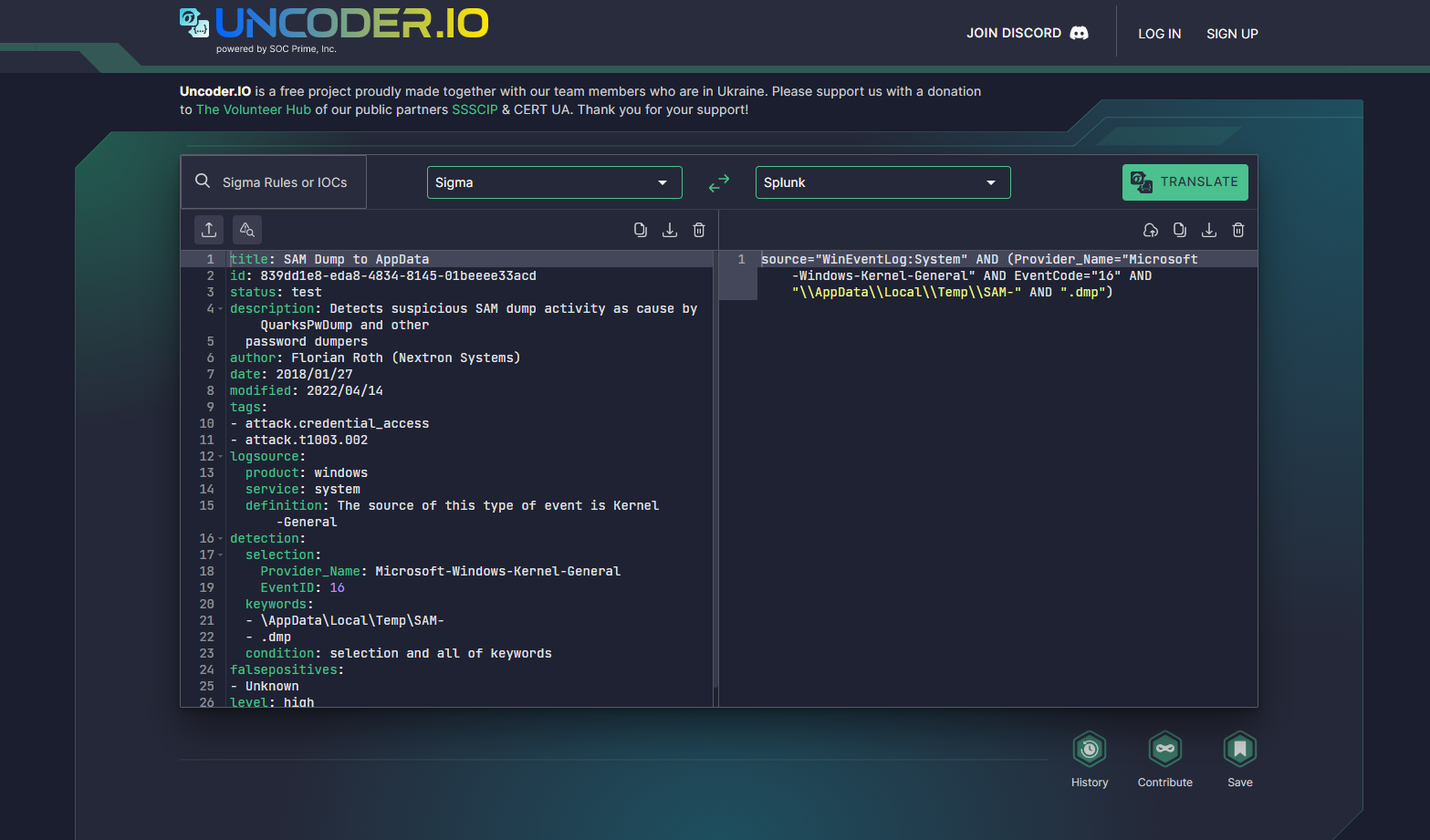
This diagram shows how uncoder.io provides details regarding an attacker copying the Windows SAM file to the AppData directory and translates the details into a search string that can be used with Splunk (or other 27+ SIEM, EDR, XDR platforms) to search for any matching events.
Analyzing Indicators of Compromise
The following video features a discussion of real-world experience with identifying, analyzing, and responding to indicators of compromise:
video
Click one of the buttons to take you to that part of the video.
Analyzing Indicators of Compromise 00:00-06:52 James Stranger: Well, let's talk indicators of compromise, finding those, looking at them, analyzing them and then formulating an appropriate response. To bring this home I've got Ian Trump. How you doing Ian?
Ian Thornton-Trump: I'm doing great James, thanks for having me.
James Stranger: You bet. It's good to have you here. You're calling in from London, is that right?
Ian Thornton-Trump: That's right. I'm the CISO here at Cyjax, threat hunting company and yeah, love to talk about this.
James Stranger: Well let's talk about indicators of compromise because a couple of different ways that we traditionally and maybe in new ways, get a hold of them. Through packet capture right? You know the old snort way of doing things right? But also the via logs and feeds, from our cloud providers or from the network etc. Tell us a bit more about how we get a hold of these indicators of compromise.
Ian Thornton-Trump: Yeah, so I mean, it really starts with building an understanding of what's going on in your network and certainly what's talking to what and what shouldn't be talking to what, I think is one of the best ways to describe it. Then of course, once you have that data, you really wanna compare it to knowing bad stuff, right?
So this is what you know, companies will go out, they'll buy threat intelligence feed from the vendor and then they'll start looking at their own stuff and what they're capturing and see if there's anything suspicious that's going on. Anything that they can look at and go, "Huh, that looks like something we should maybe look a little bit closer at." And I think this is like an evolutionary step from like, the anti virus went off, you know?
James Stranger: Yeah, yeah.
Ian Thornton-Trump: Because what we're finding is, to go in the incident [UNSURE OF WORD], to go into a breach puts a lot of stress on the organization. I mean, the IT department's gonna be doing long nights.
And so if we can understand it, we're in the early stages of a potential data breach and that damage hasn't been done yet, we have an opportunity to stop you know, the bleeding before the patient really dies right?
And I think that's, when you want to describe what hunting is within an organization it's really around trying to interject a failure in your sort of perimeter security but at the same time, contain the situation, eradicate, you know, the malicious actor, you know, then step back and use it as lessons learned.
James Stranger: Right. Or is a failure in your zero trust approach or some sort of issue right, that allows you to take those network logs, those access logs or the information from your SIM and then do things about it. And then salt it with your CTI, with your intelligence right?
Ian Thornton-Trump: Yeah, so you know, one of the things that we talk about frequently is the miter attach framework. And you know, a couple of weeks ago I gave a presentation on mapping miter attack adversarial behavior to windows event logs, you know? So one of the examples I use to set in standard enterprise, it's a very unlikely, for an individual's work station to create a scheduled task, right?
James Stranger: That's right yeah. And that's how you speak to me.
Ian Thornton-Trump
A lot of adversaries are going to use the schedule task to maintain persistence and it'll be one of the steps that they're using once they're compromised the security of an end point.
So something like that to me is a smoking gun. The logs getting cleared on a server for instance, is another sign that something strange has happened. And when you're in an enterprise where you have changed management, where you have all of these procedures to do anything you would think there would at least be a service ticket to reference why that occurred.
So what's interesting about threat hunting is, not only are you correlating all of this machine data, so you know, the windows active directory to the network logs and drawing a time line--
James Stranger: Yeah you get alerts to stuff like that right?
Ian Thornton-Trump: Yeah, you have to think about what is the overall organization context around this. So, you know, as an example you might see a big data exfiltrationcoming out of your organization but you may not wanna clamp it down until you've had a chance to check with the marketing department or one of the other departments.
Because that might actually be a transfer that they've authorized, that they've set up and in some organizations the security team's the last to know about anything so you know, it's maybe not appropriate to turn the lights and sirens on if it looks like it could be a legitimate business activity.
James Stranger: Well let's talk about appropriate response then because we've talked about various types of alerts, we've talked about the logs etc. Types of response, you know, cos you can change the firewall rules or your intrusion detection etc. Do some data lose prevention work. Tell us more about the types of appropriate response.
Ian Thornton-Trump: Yeah, I mean, it depends of course on the risk of the information that might be you know, compromised. So you know, the response can be, we're turning off the internet, to prevent all of this, to isolation and containment.
And then the hunt starts for, was there lateral movement? What happened on this work station? Did they get to a server? If they got to a server, what were they looking at? What did they try and take? So this is where, you know, all of a sudden you're not just threat hunting, you're doing digital forensics. Because you're trying to determine, you know, was a large file with all of our precious data created and then, you know, [exfiltrated] out of the organization?
James Stranger: And you're also doing some segmentation. At least hopefully you've got that ready to go. So with your ACLs and etc. to kind of slow things down a bit.
Ian Thornton-Trump: Yeah, and I think that's one of the really important things is that if things like the fire wall is changing or there's information being put into the network architecture and it's those boundaries between segmentations is what the bad guys are gonna be attacking right?
It's always said, you know, the first thing to be compromised is the bastion host that leads to all of the other things that you thought were secure, right? And so when we look at these type of models the more sort of like, obstacles you can put in place within your own organization, the more likely you are to detect that advance persistent threat adversary because they need to get an account, you know, to the management system that you're using and then make a change and that change might set off alarm bells, depending on what type of controlling technology you have.
So you know, in a way it's always about looking for what is happening, what should be happening and if something strange, that has never happened, that's a problem that needs to be addressed.
James Stranger: You know Ian, thank you so much for all your insights about what it means to take a look at these indicators of compromise and formulate an appropriate response. Sure appreciated your wisdom man.
Ian Thornton-Trump: You're welcome James.
James Stranger: Take care.
3.5 Threat Research
Click one of the buttons to take you to that part of the video.
Threat Research 00:00-00:39 In this video, we're going to discuss threat research. In the past, malware signatures were the primary feature used to detect a threat. Malware signatures are unique and include a set of data or bits of code that allow malware to be identified. Antivirus software scans file signatures and compares them to a known list of malware signatures, identifying the malicious files. As the tools and skillsets of attackers improve, threat research must improve alongside it. Although malware signatures are still used to identify malicious files, additional research and analysis is required.
Reputational Threat Research 00:39-01:05 The first type of research is reputational threat research. To perform reputational threat research, first, you search your system logs and files for potential threat indicators. Then you compare these indicators with reputational data obtained from your sources. Threat research sources provide useful information such as indicators, IP addresses, and DNS names that can be used to identify and respond to threats.
Indicator of Compromise 01:05-01:38 In the event of a successful attack on your network, there will often be residual signs. These signs are called indicators of compromise, or IoCs. Sometimes these indicators are clearly identifiable, like a malware signature. Other times the indicators are not as obvious, and an analyst must use their experience and knowledge to identify them as IoCs.
Indicators of compromise could include unusual emails, registry updates, file system changes, unauthorized software, files, hardware, or account access.
Behavioral Threat Research 01:38-02:37 Because IoCs are somewhat subjective, an analyst should use several indicators to establish a finding. Behavioral threat research combines IoCs to show patterns and techniques used in previous attacks. Analysts will often report their findings to research sites in hopes of helping other analysts who come across a similar attack. These findings usually include the tactics, techniques, and procedures—the TTPs--that are used in attacks.
Let's say an analyst suspects that a system has been infected with a virus. Indicators of compromise may include higher than usual memory usage or exceptionally high CPU usage.
Indicators of a denial-of-service attack could include increased traffic levels and IP addresses that originate from unusual geographic locations.
As you can see, threat research is all-encompassing. You're collecting data from your network, from external sources, and from your education and work experience.
Summary 02:37-02:50 That's it for this lesson. In this video, we reviewed reputational threat research, indicators of compromise, and behavioral threat research.
3.3.6 Threat Research Facts
Malware signatures are a primary method used for detecting threats. These signatures are unique and include data or bits of code that allow the malware to be identified. To identify malicious files, antivirus software scans file signatures and compares them to a known list of bad malware signatures.
In today's world, more advanced forms have emerged. As the tools and skill set of attackers have improved, threat research has also had to improve. Although malware signatures are still used to identify malicious files, additional research and analysis is also needed to identify new forms of malware.
This lesson covers the following topics:
- Reputational threat research
- Indicators of compromise (IoCs)
- Behavioral threat research
- Perform threat management activities
Reputational Threat Research
Reputational risk is a threat having to do with the perception of an organization's conformance to standards like quality, character, and stability. Social media plays an important role in the perception of an organization's reputation.
To perform reputational threat research, select one or more sources for indicators of reputational threats. Then search log files for potential threat indicators. Compare indicators from log files with data obtained from reputational threat research sources.
Threat research sources often identify DNS and IP address information associated with known attacks. Searching logs for the identified DNS and IP addresses is a good way to begin to identify a reputational attack.
Indicators of Compromise (IoCs)
In the event of a successful attack on your network, there will often be residual signs. These signs are called indicators of compromise (IoCs). Sometimes these indicators are clearly identifiable, such as a malware signature. Other times, the indicators are not as obvious, and an analyst must use experience and knowledge to identify a possible IoC.
Examples of IoCs are:
- Unusual emails
- Unusual Registry updates
- Unusual file system changes
- Unusual port usage
- Unauthorized software
- Unauthorized files
- Unauthorized account usage
- Unauthorized hardware
Behavioral Threat Research
Behavioral threat research combines IoCs to show patterns and techniques used in previous attacks. Because IoCs are somewhat subjective, an analyst should investigate them enough to decide whether to escalate or dismiss them as valid threats.
Analysts will often report their findings to research sites in hopes that it will help other analysts who come across similar attacks. These findings usually include the tactics, techniques, and procedures (TTP) used in attacks.
The following table provides potential attacks and indicators:
| Attack | Description |
|---|---|
| Virus | Indicators of a virus attack are:
|
| Denial-of-service attack | Indicators of a denial-of-service attack are:
|
| Advanced persistent threat (APT) | Indicators of an advanced persistent threat are:
|
Perform Threat Management Activities
Attack methodology frameworks assist in identifying malicious activity and provide a comprehensive and standardized approach to investigating and assessing potential threats. Attack methodology frameworks typically help describe different tactics for detection, analysis, containment, and resolution. When used appropriately, they help to define a process-centric approach to analyzing data, identifying suspicious trends, and implementing effective methods for preventing malicious activity.
Video script
Click one of the buttons to take you to that part of the video.
Performing Threat Management Activities 00:00-09:18 James Stanger: Well, let's talk about what it means to perform threat management activities and, to help us with that we've got Ian Trump. Ian, how you doing?
Ian Thornton-Trump: I'm doing great, James. Thanks for bringing me on.
James Stanger: Good to have you here, man, good to have you here. You're calling in from London, right, where you've been for a few years, right?
Ian Thornton-Trump: Yes, indeed.
James Stanger: Well, good to have you here. Tell us a bit about yourself and then let's start talking about what it means to perform threat management activities.
Ian Thornton-Trump: Sure. I'm the CISO for Cyjax. I work in the threat intelligence space, along with a team of dedicated professionals and really, what we're talking about is taking the risk models of the business, applying them to the various controls, detective, reactive and proactive and coming up with a plan to, essentially, stop data breach.
James Stanger: You know, when it comes to these intelligence types that we have available to us, you know, we could look at it from a perspective of cyber security threat intelligence. We've got all sorts of, I don't know, we've got threat hunting and all that. What are some of the intelligence types that you find useful, whether it be deep web or proprietory or what have you?
Ian Thornton-Trump: Yeah, I mean I think the battle right now is really centered around driving a vulnerability management program with accurate threat intelligence about what's being exploited, what's vulnerable. You know, if somebody drops proof of concept on Twitter, how long will I t take the bad guys to turn that into and weaponize it and have it show up? That's, I think, half of the battle. I mean, when we do the analysis and we see how a lot of businesses are falling prey, it really comes down to, you know, credentials being compromised, Office 365 being compromised, password reset capability being invoked by the bad guys and then, you know, they're off to the races.
The other big area that I'd say needs to be focused on, in terms of CTI and threat management, is around that external attacks or if it's what do I have? Is it exposed and, you know, can take action to fix it before it becomes a particular problem? This got really exacerbated when, all of a sudden, you know, we had a workforce that needed to work from home, so downtime on the systems to patch an update wasn't appreciated, you know, and you didn't really have the change windows that you used to have in an enterprise environment. So, in a lot of cases, if there was a requirement to update, you know, a client site VPN and a VPN concentrator, across hundreds of employees, it just wasn't done.
James Stanger: You know, when it comes to understanding the different types of threats that are out there, there are various frame works. Let's say if they are going after your VPN or whether they are going after your end points, there are various frameworks that are out there. There's the big three I suppose. MITRE ATT&CK, the Lockheed Martin, Cyber Kill Chain and the Diamond Model. Let's compare those a bit and talk about them and how they're used.
Ian Thornton-Trump: Sure. So, I mean the new kid on the block is the MITRE ATT&CK Kill Chain analysis, if you will, that really maps advance persistent threat and ransomware cyber criminal attacks to a particular set of things that happens, right. So, one of them is, of course, you know, some sort of of exploitation that gets inside the network. Then, a Trojan is invoked and then, you know, there might be a living off the land component, where the bad guys now do a reconnaissance, you know, find the crown jewels, zip up the crown jewels and exfiltrate all the data. That's kind of what both an APT style and a cyber criminal attack look like and, you know, the cyber criminal attack is I now drop a ransomware package on those end points. So, I think MITRE ATT&CK really works well when you start applying machine learning and AI models to it and try to detect stuff as early as possible.
In terms of the Diamond framework and Lockheed Martin, I think these are great teaching opportunities and frameworks for when you're dealing with a lot of more non technical people, right, and when you're just trying to explain adversarial activity and maybe the steps that you're taking to nip that off in the bud. So, if I was to say to a bunch of like threat hunters and blue team folks, you know, use MITRE ATT&CK and tell me how we're gonna detect all of these adversarial activities. That's a really common language amongst those types of people.
But if I'm trying to get a whole bunch of money for a cyber program, within an organization, when I'm going in front of the executives, the CFO, the CEO, the CIO and I'm trying to explain what type of adversary is coming at us, what they're trying to do, you know, the Lockheed Martin or the Diamond Model are really great teaching diagrams and the reason I like these teaching diagrams is because I can move left to right, or up to down, on one slide, as opposed to going through pages and MITRE is really deep and not really consumable. You know, I've seen people try to put MITRE ATT&CK into a PowerPoint slide and it didn't shift, right.
James Stanger: Yeah. You know, when it comes to understanding different types of threats, there are ways that you can go after a do some threat hunting, right, and then there's threat emulation. Let's talk about those two things, just to kind of finish up a little bit. What do those mean?
Ian Thornton-Trump: Well, there's sort of really two really valuable takeaways from that. So, one of the things is using threat intelligence to determine, you know, are we breached and looking actively at everything from the network layer to the end point and into your SIM, looking for those indications of compromise. That's threat hunting, right.
Now, when you're talking about like mapping adversarial activity, it's really interesting to do this in sort of more of a tabletop exercise or bring in, you know, and start training your folks in the ideas behind being a purple team member. So, understanding and practicing adversarial tactics on your own environment or maybe not a production environment but maybe a dev environment that looks a lot like the production environment.
This gives you two things. One, it gives you the opportunity understand maybe gaps in your own IR capabilities. But also, when you do those type of tabletop exercises and you share the results and the summaries of them with the organization, it should be part of your plan to either get funds to fill those gaps or really be able to inform the board about the level of governance and risk tolerance that is currently there, you know. IT believes, it says that they have backups for everything, but how long will it take to restore? How long will it take to get back to fully operational capability? Well, you don't know unless you test it or game it out.
James Stanger: So, that's where the threat emulation side of it comes and it's interesting that you see purple team as part of that and threat hunting as a more separate activity. I find that interesting.
Ian Thornton-Trump: Yeah, I mean I've really been talking about the evolution of the DevOp spaces to be intelligence led for specific activities like threat hunting and so I see these kind of emerging whereas business I think are struggling a bit for is, you know, they have a fire department called the IR team, right, and unless there is a fire, the fire department, you know, might be doing a bit of training but they're not really contributing to the business.
So, I think purple team is an opportunity for those red teamers to start working on the defensive side, in sort of supporting the business objectives. I mean it's super cool to go around getting into, you know, the business and finding all of the vulnerabilities, but unless you're prepared to start contributing to the defense and being fully transparent on what you found and why it's a problem and then making suggestions on how you should fix it, I think that's more constructive than continuing to demoralize the blue team inside your company.
James Stanger: No, it's a big thing because it includes the non technical folks and it basically starts getting a strategic IT approach going, rather than the old kind of separation of IT and the business unit as it were.
Ian Thornton-Trump: Yeah, and I mean when you, and god forbid you do, but, you know, it's an experience that many businesses have faced, when you have been breached, having people that can go back to an exercise and bringing in, you know, PR, bringing in counsel, bringing in the executives, the appropriate executives, and arming them with the right information, all of that becomes really valuable. I mean it's still gonna be a super stressful scenario but if you have already sort of gamed it out, I think you're gonna have a huge advantage on reducing your cost of data breach and knowing, you know, what your own team's limitations are and capabilities, that you can then augment with, you know, obviously what's gonna be high priced resources.
James Stanger: Fantastic. Thanks so much, Ian, for your insights about threat management activities and their relationship to the rest of the organization.
Ian Thornton-Trump: My pleasure, James.
James Stanger: Bye.
